SECURE ELECTRONIC TRANSACTION Dr
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Alumni Association of MS Ramaiah University of Applied Sciences
Alumni Association of M.S. Ramaiah University of Applied Sciences (SAMPARK), Bangalore M.S. Ramaiah University of Applied Sciences Department of Automotive & Aeronautical Engineering Program Year of Name Contact Address Photograph E-mail & Mobile Sl NO Completed Admiss ion # 25 Biligiri, 13th cross, 10th A Main, 2nd M T Layout, [email protected] M. Sc. (Automotive 574 2013 Pramod M Malleshwaram, Bangalore- 9916040325 Engineering) 560003 S/o L. Srinivas Rao, Sai [email protected] Dham, D-No -B-43, Near M. Sc. (Automotive m 573 2013 Lanka Vinay Rao Torwapool, Bilaspur (C.G)- Engineering) 9424148279 495001 9406114609 3-17-16, Ravikunj, Parwana Nagar, [email protected] Upendra M. Sc. (Automotive Khandeshwari road, Bank m 572 2013 Padmakar Engineering) colony, 7411330707 Kulkarni Dist - BEED, State – 8149705281 Maharastra No.33, 9th Cross street, Dr. Radha Krishna Nagar, [email protected] M. Sc. (Automotive Venkata Krishna Teachers colony, 571 2013 0413-2292660 Engineering) S Moolakulam, Puducherry-605010 # 134, 1st Main, Ist A cross central Excise Layout [email protected] M. Sc. (Automotive Bhoopasandra RMV Iind 570 2013 Anudeep K N om Engineering) stage, 9686183918 Bengaluru-560094 58/F, 60/2,Municipal BLDG, G. D> Ambekar RD. Parel [email protected] M. Sc. (Automotive Tekavde Nitin 569 2013 Bhoiwada Mumbai, om Engineering) Shivaji Maharashtra-400012 9821184489 Thiyyakkandiyil (H), [email protected] M. Sc. (Automotive Nanminda (P.O), Kozhikode / 568 2013 Sreedeep T K m Engineering) Kerala – 673613 4952855366 #108/1, 9th Cross, themightyone.lohith@ M. Sc. (Automotive Lakshmipuram, Halasuru, 567 2013 Lohith N gmail.com Engineering) Bangalore-560008 9008022712 / 23712 5-8-128, K P Reddy Estates,Flat No.A4, indu.vanamala@gmail. -

Cinema of the Social: Stars, Fans and the Standardization of Genre in Tamil Cinema
Western University Scholarship@Western Digitized Theses Digitized Special Collections 2011 CINEMA OF THE SOCIAL: STARS, FANS AND THE STANDARDIZATION OF GENRE IN TAMIL CINEMA Ganga Rudraiah Follow this and additional works at: https://ir.lib.uwo.ca/digitizedtheses Recommended Citation Rudraiah, Ganga, "CINEMA OF THE SOCIAL: STARS, FANS AND THE STANDARDIZATION OF GENRE IN TAMIL CINEMA" (2011). Digitized Theses. 3315. https://ir.lib.uwo.ca/digitizedtheses/3315 This Thesis is brought to you for free and open access by the Digitized Special Collections at Scholarship@Western. It has been accepted for inclusion in Digitized Theses by an authorized administrator of Scholarship@Western. For more information, please contact [email protected]. CINEMA OF THE SOCIAL: STARS, FANS AND THE STANDARDIZATION OF GENRE IN TAMIL CINEMA r , ' (Spine title: CINEMA OF THE SOCIAL) (Thesis Format: Monograph) by : Ganga Rudraiah Graduate Program in Film Studies A thesis submitted in partial fulfillment of the requirements for the degree of Master of Arts The School of Graduate and Postdoctoral Studies The University of Western Ontario London, Ontario, Canada © Ganga Rudraiah 2011 THE UNIVERSITY OF WESTERN ONTARIO SCHOOL OF GRADUATE AND POSTDOCTORAL STUDIES CERTIFICATE OF EXAMINATION r Supervisor Examiners Dr. Christopher E. Glttings Dr. James Prakash Younger Supervisory Committee Dr. Constanza Burucúa Dr. Chris Holmlund The thesis by Ganga Rudraiah entitled: Cinema of the Social: Stars, Fans and the Standardization of Genre in Tamil Cinema is accepted in partial fulfillment of the requirements for the degree of Master of Arts Date Chair of the Thesis Examination Board Abstract The star machinery of Tamil cinema presents itself as a nearly unfathomable system that produces stars and politicians out of actors and fans out of audiences in an organized fashion. -

Psyphil Celebrity Blog Covering All Uncovered Things..!! Vijay Tamil Movies List New Films List Latest Tamil Movie List Filmography
Psyphil Celebrity Blog covering all uncovered things..!! Vijay Tamil Movies list new films list latest Tamil movie list filmography Name: Vijay Date of Birth: June 22, 1974 Height: 5’7″ First movie: Naalaya Theerpu, 1992 Vijay all Tamil Movies list Movie Y Movie Name Movie Director Movies Cast e ar Naalaya 1992 S.A.Chandrasekar Vijay, Sridevi, Keerthana Theerpu Vijay, Vijaykanth, 1993 Sendhoorapandi S.A.Chandrasekar Manorama, Yuvarani Vijay, Swathi, Sivakumar, 1994 Deva S. A. Chandrasekhar Manivannan, Manorama Vijay, Vijayakumar, - Rasigan S.A.Chandrasekhar Sanghavi Rajavin 1995 Janaki Soundar Vijay, Ajith, Indraja Parvaiyile - Vishnu S.A.Chandrasekar Vijay, Sanghavi - Chandralekha Nambirajan Vijay, Vanitha Vijaykumar Coimbatore 1996 C.Ranganathan Vijay, Sanghavi Maaple Poove - Vikraman Vijay, Sangeetha Unakkaga - Vasantha Vaasal M.R Vijay, Swathi Maanbumigu - S.A.Chandrasekar Vijay, Keerthana Maanavan - Selva A. Venkatesan Vijay, Swathi Kaalamellam Vijay, Dimple, R. 1997 R. Sundarrajan Kaathiruppen Sundarrajan Vijay, Raghuvaran, - Love Today Balasekaran Suvalakshmi, Manthra Joseph Vijay, Sivaji - Once More S. A. Chandrasekhar Ganesan,Simran Bagga, Manivannan Vijay, Simran, Surya, Kausalya, - Nerrukku Ner Vasanth Raghuvaran, Vivek, Prakash Raj Kadhalukku Vijay, Shalini, Sivakumar, - Fazil Mariyadhai Manivannan, Dhamu Ninaithen Vijay, Devayani, Rambha, 1998 K.Selva Bharathy Vandhai Manivannan, Charlie - Priyamudan - Vijay, Kausalya - Nilaave Vaa A.Venkatesan Vijay, Suvalakshmi Thulladha Vijay 1999 Manamum Ezhil Simran Thullum Endrendrum - Manoj Bhatnagar Vijay, Rambha Kadhal - Nenjinile S.A.Chandrasekaran Vijay, Ishaa Koppikar Vijay, Rambha, Monicka, - Minsara Kanna K.S. Ravikumar Khushboo Vijay, Dhamu, Charlie, Kannukkul 2000 Fazil Raghuvaran, Shalini, Nilavu Srividhya Vijay, Jyothika, Nizhalgal - Khushi SJ Suryah Ravi, Vivek - Priyamaanavale K.Selvabharathy Vijay, Simran Vijay, Devayani, Surya, 2001 Friends Siddique Abhinyashree, Ramesh Khanna Vijay, Bhumika Chawla, - Badri P.A. -

COMMON ELIGIBILITY TEST 2020 (For M
COMMON ELIGIBILITY TEST 2020 (For M. Phil. And Ph.D. Programs 2020-2021) Eligible Applicant List (Updated) S. No Application No Appearing Subject Name Father/Guardian Name Email Id 1 CET/2020-21/00001 Commerce DEVICHANDRIKA S B.SIVASUBRAMANIAN [email protected] 2 CET/2020-21/00002 English SINDUJA B BUPATHY G [email protected] 3 CET/2020-21/00003 Computer Science Vishali priya. O T.OOMATHURAI [email protected] 4 CET/2020-21/00004 Journalism And Mass Comm. Melwin Samuel Rajamani [email protected] 5 CET/2020-21/00005 Computer Applications Megala V Vanaja [email protected] 6 CET/2020-21/00006 Commerce PRAKASH D K R DHANABALAN [email protected] 7 CET/2020-21/00007 English PADHMAVATHI Alagarsamy ALAGARSAMY [email protected] 8 CET/2020-21/00008 Costume Design & Fashion K.SATHYA SATHYA M KRISHNASAMY [email protected] 9 CET/2020-21/00009 Mathematics GIFTEENA HINGIS Y M YESUDHASAN C [email protected] 10 CET/2020-21/00010 Chemistry SWATHI THARANI.D Dharmalingam.R [email protected] 11 CET/2020-21/00011 Computer Applications Nandhakumar SubramaniamSubbulakshmi [email protected] 12 CET/2020-21/00012 English Priyadharsini R D Rajagopal [email protected] 13 CET/2020-21/00013 Psychology KANCHANA D M DHANALAKSHMI M [email protected] 14 CET/2020-21/00014 Computer Science JINCY JOY JOY SAMUEL [email protected] 15 CET/2020-21/00015 English B. Dheepthi P C Balamohan [email protected] 16 CET/2020-21/00016 Education Dany K J Jose [email protected] 17 CET/2020-21/00017 -

Science Toppers
SKCH COMPOSITE PU COLLEGE II PU BOARD EXAMS MARCH 2020 SCIENCE TOPPERS ENG 91 ENG 90 SAN 100 SAN 99 PHY 99 PHY 99 CHE 99 CHE 98 MAT 100 MAT 100 ELE 96 BIO 99 TOT 585 TOT 585 RAKSHA K SWAMY SAAKSHI ADIGA S ENG 87 ENG 90 FRE 99 SAN 99 PHY 98 PHY 99 CHE 100 CHE 98 MAT 100 MAT 100 ELE 100 CS 99 TOT 584 TOT 585 SUDERSHAN K S RACHITHA S ENG 90 ENG 94 HIN 95 SAN 98 PHY 98 PHY 98 CHE 100 CHE 95 MAT 100 MAT 97 ELE 100 CS 98 TOT 583 TOT 580 SUBRAMANYA H SOUJANYA S COMMERCE TOPPERS ENG 93 ENG 90 SAN 99 SAN 98 BS 99 BS 97 ACC 98 ACC 99 STAT 99 STAT 100 BM 100 BM 100 TOT 588 TOT 584 S TANMAYI ROSHNI S S ENG 92 ENG 90 SAN 99 KAN 94 BS 99 BS 99 ACC 98 ACC 100 STAT 95 STAT 100 BM 100 BM 100 TOT 583 TOT 583 NADHIYA S SUPREETH K ENG 90 SAN 100 BS 96 ACC 97 STAT 100 BM 99 TOT 582 SHARANYA L NUMBER OF CENTUMS NO. OF SNO SUBJECT CENTUMS 1 KANNADA 1 2 SANSKRIT 12 3 HINDI 2 4 PHYSICS 5 5 CHEMISTRY 4 6 MATHEMATICS 83 7 BIOLOGY 2 8 COMPUTER SCIENCE 6 9 ELECTRONICS 11 10 BUSINESS STUDIES 9 11 ACCOUNTANCY 2 12 STATISTICS 22 13 BASIC MATHS 26 185 NO. OF DISTINCTIONS 445 NO. OF FIRST CLASS 305 NO. OF CENTUMS 185 RESULT ANALYSIS TOTAL STREAM PASS %AGE STRENGTH SCIENCE 649 640 98.61 COMMERCE 117 117 100 OVERALL 766 757 98.83 SCIENCE TOPPERS FOR THE YEAR 2019-2020 SNO NAME TOTAL %AGE RANK 1 RAKSHA K SWAMY 585 97.5 1 2 SAAKSHI ADIGA S 585 97.5 1 3 SUDERSHAN K S 585 97.5 1 4 RACHITHA S 584 97.3 2 5 SUBRAMANYA H 583 97.2 3 6 SOUJANYA S 580 96.7 4 7 HITHASHRI C M 579 96.5 5 8 TEJAS P V 579 96.5 5 9 DEEPTHI T L 578 96.3 6 10 NAMRATA B HAKARI 577 96.2 7 11 SOOJAL S 577 96.2 -

PERI Institute of Technology Department of Civil Engineering Academic Year 2015-2016 (Even Semester)
PERI Institute of Technology Department of Civil Engineering Academic Year 2016 – 2017 (Even Semester) Subject Code / Name: CE 6811 Project Work Semester: 08 S. Batch Name of the Reg. No. Name of the Student Topic No No. Guide 1. 411513103002 Abinaya M Strength properties of concrete using Mrs. Namitha 2. 411513103007 Anandheswaran B 1 crumb rubber with partial Jacob replacement of fine aggregate 3. 411513103302 Arunkumar M 4. 411513103008 Anish Kumar P Mrs. Namitha An Experimental study of bacterial 5. 411513103015 Divya B 2 Jacob self-Healing Concrete 6. 411513103311 Shanmugasundaram C 7. 411513103031 Phidawansha R Sohliya Comparison on Strength of Concrete 8. 411513103021 Jenifer Raj M 3 Mr. M.Vignesh cementatious using Glass Powder and Polythene bag as additive 9. 411513103055 Vinayagam P 10. 411513103001 Aarthi V R Seismic Behaviour of Brick and 11. 411513103004 Aishwarya S P 4 Mr. M.Vignesh Hollow Block Masonry Walls with fibre composites 12. 411513103017 Gayathri P 13. 411513103012 Charan Tej R Experimental Study on static 14. 411513103033 Pravin A Mathew 5 Dr. Rajesh Guna behaviour of high Volume class C Fly ash RCC Beam. 15. 411513103048 Sudharsan R 16. 411513103036 Rajkumar R An Experimental study of Strated 17. 411513103037 Rajpandi V 6 Dr. Rajesh Guna Fibre Concrete.[SIFCON] 18. 411513103057 Yuvaraj R 19. 411513103005 Ajithkumar M Experimental Investigation of Mrs. 20. 411513103029 Narendhar S 7 Pervious Concrete for Improving the S.Rajalakshmi performance In Rigid Pavements. 21. 411513103053 Viknesh V 22. 411513103014 Devanathan S Mrs. Flyash based cellular light weight 23. 411513103047 Sudha V 8 S.Rajalakshmi concrete 24. 411513103306 Pandiyarajan D 25. -

NAMITHA PRASTHEENA JOSEPH Address: Thachuthara House, Kotheri Road, Vaduthala P
NAMITHA PRASTHEENA JOSEPH Address: Thachuthara House, Kotheri Road, Vaduthala P. O., Kochi-682023 Email: [email protected] Contact Number: 8281756189 CAREER OBJECTIVE To obtain a position that challenges me and provides me the opportunity to reach my full potential professionally and personally. My ultimate goal is to inspire students by sharing my knowledge, skills and experience on the subject and guide them toward the path of excellence. EDUCATIONAL QUALIFICATION 2020 : Completed Post Graduation in Food Science and Nutrition from St. Teresa’s College (Autonomous), Ernakulam. 2019 : Qualified UGC-NET for eligibility for Assistant Professor in the subject Home Science. 2018 : Completed Graduation in Home Science from St. Teresa’s College (Autonomous) Ernakulam. 2015 : Completed Senior secondary from Assisi Vidyaniketan Public School, Chembumukku, Kakkanad, Kochi. 2013 : Completed higher secondary from Assisi Vidyaniketan Public School, Chembumukku, Kakkanad, Kochi. PERSONAL QUALITES I am hard working person who can handle all tasks with full potential and with utmost perfection. ACADEMIC PROFILE Examination Year of University/ Name of Course Marks Passing Board Institution Obtained X 2013 CBSE Assisi English 8.2 Vidyaniketan Hindi (CGPA) Public School, Science Chembumukku, Social Science Kakkanad, Mathematics Kochi. XII 2015 CBSE Assisi Science with 80.4% Vidyaniketan Home Science Public School, Chembumukku, Kakkanad, Kochi. Graduation 2018 MG St. Teresa’s B. Sc. Home 8.4 University College Science (CGPA) (Autonomous), Ernakulam Post- 2018- 2020 MG St. Teresa’s M. Sc. Food 8.72 Graduation University College Science and (CGPA) (Autonomous), Nutrition Ernakulam INTERNSHIP • Completed one month Internship Programme at Department of Dietetics, Christian Medical College Vellore from 1st May 2019 to 30th May, 2019. -

Jipmer Md/Ms Entrance Examination Overall Rank List - January 2020 Session Total Rank Slno Roll No
JIPMER MD/MS ENTRANCE EXAMINATION OVERALL RANK LIST - JANUARY 2020 SESSION TOTAL RANK SLNO ROLL NO. NAME OF THE CANDIDATE DOB Percentile MARKS UR OBC SC ST INST OPHSponsoredForeignEligibility 1 2001122317 AJAY NARAYAN M S 692 30/10/1995 99.9931783 1 Yes 2 2001171139 VAIBHAV AGGARWAL 648 11/12/1995 99.9863565 2 Yes 3 2001171907 VASUDHA KOHLI 646 19/08/1995 99.9795348 3 Yes 4 2001172538 RAHUL MIDDHA 639 14/11/1994 99.9727130 4 Yes 5 2001140268 SANJANA S 633 26/10/1995 99.9658913 5 Yes 6 2001141655 PREM VENKATT T 629 13/09/1994 99.9590695 6 Yes 7 2001142873 S.PRASANNA ETHIRAJ 625 20/10/1995 99.9386043 7 Yes 8 2001121854 NAVANEETH B 625 29/02/1996 99.9386043 8 Yes 9 2001191433 MOHITH GEORGE VARAMPATHU 625 18/11/1994 99.9386043 9 Yes 10 2001140132 NAVEEDH AHMED A R 624 09/04/1996 99.9317825 10 1 Yes 11 2001190174 AKSHAY 623 14/04/1996 99.9249608 11 Yes 12 2001120636 CHAITHRA R 622 03/02/1996 99.9181390 12 1 Yes 13 2001142386 S M MOHANA SUNDARAM 621 05/09/1994 99.9044955 13 2 Yes 14 2001201477 YARLAGADDA YASHWANTH KUMAR 621 14/02/1996 99.9044955 14 Yes 15 2001144338 G.MAHATHI 619 01/06/1996 99.8976738 15 Yes 16 2001120437 DANESHWARI KALAGE 617 11/08/1995 99.8908520 16 Yes 17 2001170637 SWARNA SAXENA 616 25/09/1994 99.8840303 17 Yes 18 2001110288 PATEL MARGIKKUMAR LALLUBHAI 615 15/02/1995 99.8772085 18 Yes 19 2001143057 SARANYA.N 614 08/07/1996 99.8703868 19 1 Yes 20 2001200017 VUTUKURI SAI SASHANK 613 29/03/1996 99.8567433 20 2 Yes 21 2001140035 SARANKUMAR B 613 18/12/1994 99.8567433 21 3 Yes 22 2001190725 JOHN V ALEXANDER 611 22/10/1992 99.8499215 -
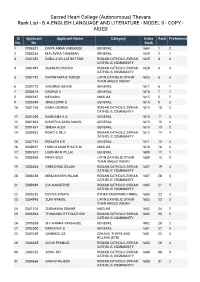
Sacred Heart College (Autonomous) Thevara Rank List - B a ENGLISH LANGUAGE and LITERATURE - MODEL II - COPY - AIDED
Sacred Heart College (Autonomous) Thevara Rank List - B A ENGLISH LANGUAGE AND LITERATURE - MODEL II - COPY - AIDED Sl Applicant Applicant Name Category Index Rank Preference No. No Mark 1 2008321 DIVYA ANNA VARGHESE GENERAL 1665 1 2 2 2004236 MALAVIKA THAMBAN GENERAL 1639 2 1 3 2001052 DONA J VELLATHOTTAM ROMAN CATHOLIC SYRIAN 1635 3 3 CATHOLIC COMMUNITY 4 2001491 AUGNUS CHACKO ROMAN CATHOLIC SYRIAN 1629 4 4 CATHOLIC COMMUNITY 5 2007142 NAYANTARA B TERESE LATIN CATHOLIC OTHER 1623 5 3 THAN ANGLO INDIAN 6 2005718 ANUSREE ASHOK GENERAL 1617 6 1 7 2004415 DRUPAD C GENERAL 1616 7 1 8 2003547 NEHARIN MUSLIM 1615 8 5 9 2005549 SREEGOWRI S GENERAL 1615 9 3 10 2001756 DONA GEORGE ROMAN CATHOLIC SYRIAN 1615 10 3 CATHOLIC COMMUNITY 11 2001029 NANDANA K A GENERAL 1615 11 3 12 2007304 NIKHITHA SARA DANIEL GENERAL 1615 12 4 13 2001431 SNEHA ALEX GENERAL 1613 13 2 14 2005932 ROHIT C REJI ROMAN CATHOLIC SYRIAN 1612 14 4 CATHOLIC COMMUNITY 15 2007751 RENJITH K R GENERAL 1611 15 3 16 2009057 HANIYA MUMTHAZ K M MUSLIM 1610 16 3 17 2007672 LEKSHMI R PILLAI GENERAL 1609 17 1 18 2000530 PRIYA SOLY LATIN CATHOLIC OTHER 1609 18 2 THAN ANGLO INDIAN 19 2008434 GREESHMA SOJAN ROMAN CATHOLIC SYRIAN 1607 19 4 CATHOLIC COMMUNITY 20 2003328 MINU MARIYA RAJAN ROMAN CATHOLIC SYRIAN 1607 20 5 CATHOLIC COMMUNITY 21 2003489 IDA AUGUSTINE ROMAN CATHOLIC SYRIAN 1605 21 5 CATHOLIC COMMUNITY 22 2005252 DEVIKA S NATH OTHER BACKWARD HINDU 1603 22 2 23 2004998 SUNFIYAMOL LATIN CATHOLIC OTHER 1603 23 3 THAN ANGLO INDIAN 24 2001310 SUBAHANA SUBAIR MUSLIM 1602 24 2 25 2003594 THOMASKUTTY MATHEW ROMAN CATHOLIC SYRIAN 1602 25 3 CATHOLIC COMMUNITY 26 2005206 SIJI HANNA VARGHESE GENERAL 1602 26 2 27 2002300 PARVATHY S GENERAL 1601 27 4 28 2005769 UNNIMOL CS EZHAVA, THIYYA AND 1601 28 3 BILLAVA (ETB) 29 2008385 ALINA FRANCIS ROMAN CATHOLIC SYRIAN 1600 29 4 CATHOLIC COMMUNITY 30 2003252 JONA JOY ROMAN CATHOLIC SYRIAN 1600 30 3 CATHOLIC COMMUNITY 31 2004666 ANAND RAJESH ROMAN CATHOLIC SYRIAN 1600 31 2 CATHOLIC COMMUNITY Sl Applicant Applicant Name Category Index Rank Preference No. -

Muthurangam Government Arts College (Autonomous), Vellore - 632 0022| English Rank Report Provisional Rank List - B.A
Muthurangam Government Arts College (Autonomous), Vellore - 632 0022| English Rank Report Provisional Rank List - B.A. English SNo. App No. Name Gender Community Subject Cut off 1 375508 GOWTHAM V Male SC English 96.8 2 416866 GOPIKA S Female MBC (V) English 95.7 3 457917 BALAGURU S Male SC English 95.6 4 495649 HARINI S Female SC English 95.1 5 467828 VARSHINI G Female BC English 95 6 494370 HARSHINNI S Female SC English 94.7 7 228928 KOKILA D Female BC English 94.4 8 322863 KISHORE G C Male BC English 94 9 326341 PRAKASH A Male SC English 92.7 10 458210 SURIYAPRAKASH M Male SC English 92.6 11 277162 DHARSHAN D Male BC English 92.6 12 357091 PRITHI V Female BC English 92.3 13 456910 PRIYADHARSHINI N Female MBC (V) English 92.2 14 456642 GOKUL S Male SCA English 92.1 15 245884 NANDHINI S Female SC English 92 16 413478 SATHIYAMOORTHI G Male ST English 91.9 17 469141 ANNAMALAI A Male BC English 91.9 18 386861 SINDHU B Female MBC (V) English 91.9 19 336215 SNEHA M Female MBC (V) English 91.7 20 330642 GAYATHRI Female BC English 91.6 21 426694 GAYATHRI G S Female MBC (V) English 91.4 22 490496 KALAISELVI Female BC English 91.3 23 348279 GAYATHRI G S Female MBC (V) English 91.3 24 496761 HEMASRI P Female BC English 91 25 211514 MALLESH J Male BC English 91 26 212183 E ARTHI ANANTHI Female BC English 90.8 27 389397 POORNIMA S Female MBC (V) English 90.8 28 302437 SWETHA B Female SC English 90.6 29 349358 DHIVIYA U Female BC English 90.6 30 490449 SHERLY D Female SC English 90.6 31 472180 SUBHANU S Female MBC (V) English 90.2 32 234094 UDHAYASURIYAN -
Cfd Annual Report 2011
Center for Detectors Annual Report 2011 Table of Contents Director’s Comments .......................................................................................................................................... 1 Highlights ................................................................................................................................................................ 2 Executive Summary ............................................................................................................................................ 3 Research Research Projects ................................................................................................................................................ 7 The Future Photon Initiative: A National Center Proposal ............................................................. 31 Student Vignettes .............................................................................................................................................. 33 External Funding and Collaborating Partners ..................................................................................... 43 Communications Detector Virtual Workshop .......................................................................................................................... 51 Distinguished Speaker Series ...................................................................................................................... 53 Quantum-Limited Imaging Detector Symposium .............................................................................. -

List of Candidates Provisionally Admitted-2018
UNIVERSITY OF HYDERABAD List of Candidates Provisionally Admitted - 2018 Course: M.Sc.(5 yr Integrated) Page No: 1 Subject: Mathematical Sciences 14-Aug-2018 S.No Reg.No Name Remarks Left 1 18IMMM01 ADLURI ABHINAY SHARMA 2 18IMMM02 SANDIPAN PAUL 3 18IMMM04 SASI KUMAR MEESALA 4 18IMMM05 ANIL KUMAR EJJADA 5 18IMMM06 BETHA L G R MANJUNATH RAJ 6 18IMMM07 TANVI SAROJ 7 18IMMM08 PANYALA RAJESHWAR REDDY 8 18IMMM09 BONAGIRI PRANAY 9 18IMMM10 MARIA GEORGE 10 18IMMM11 METHRI KALYANI 11 18IMMM12 SHAMNA V 12 18IMMM13 V ACHARYA SAMUDRA 13 18IMMM14 CHINDAM NAGARAJU 14 18IMMM15 RATHOD PRANEETH 15 18IMMM16 CHALLA MANICHANDANA 16 18IMMM17 KATKURI KAVYA 17 18IMMM18 SYED SAFIUDDIN 18 18IMMM19 MUHAMMED SAJJAD C K UNIVERSITY OF HYDERABAD List of Candidates Provisionally Admitted - 2018 Course: M.Sc.(5 yr Integrated) Page No: 1 Subject: Physics 14-Aug-2018 S.No Reg.No Name Remarks 1 18IPMP01 APOORVA K 2 18IPMP02 GURIJALA SAI KEDAR REDDY 3 18IPMP03 KRUPA ANNA JOSE 4 18IPMP04 DARSANDEV T 5 18IPMP05 RAKESH GIRI 6 18IPMP06 ABHISHEK DAS 7 18IPMP07 MALAVIKA THILAK 8 18IPMP08 MUHAMMED SHAMEEM P 9 18IPMP09 PAVITHRA S Left 10 18IPMP10 UJWAL REDDY PARVATHA REDDY 11 18IPMP11 VASUNDHARA G S 12 18IPMP12 DIYA GOVIND 13 18IPMP13 SANIN SUHAIL M 14 18IPMP14 SURABHI YADAV 15 18IPMP15 MAHIMA ANN PAUL 16 18IPMP16 BANOTH SRIRAM CHINTU 17 18IPMP17 GUDALA VINAY 18 18IPMP18 MRUTYUNJAYA RATH 19 18IPMP19 SARTHAK MISHRA UNIVERSITY OF HYDERABAD List of Candidates Provisionally Admitted - 2018 Course: M.Sc.(5 yr Integrated) Page No: 1 Subject: Chemical Sciences 14-Aug-2018 S.No Reg.No