Application Password Cracking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active@ UNDELETE Documentation
Active @ UNDELETE Users Guide | Contents | 2 Contents Legal Statement.........................................................................................................5 Active@ UNDELETE Overview............................................................................. 6 Getting Started with Active@ UNDELETE.......................................................... 7 Active@ UNDELETE Views And Windows...................................................................................................... 7 Recovery Explorer View.......................................................................................................................... 8 Logical Drive Scan Result View..............................................................................................................9 Physical Device Scan View......................................................................................................................9 Search Results View...............................................................................................................................11 File Organizer view................................................................................................................................ 12 Application Log...................................................................................................................................... 13 Welcome View........................................................................................................................................14 Using -

Active @ UNDELETE Users Guide | TOC | 2
Active @ UNDELETE Users Guide | TOC | 2 Contents Legal Statement..................................................................................................4 Active@ UNDELETE Overview............................................................................. 5 Getting Started with Active@ UNDELETE........................................................... 6 Active@ UNDELETE Views And Windows......................................................................................6 Recovery Explorer View.................................................................................................... 7 Logical Drive Scan Result View.......................................................................................... 7 Physical Device Scan View................................................................................................ 8 Search Results View........................................................................................................10 Application Log...............................................................................................................11 Welcome View................................................................................................................11 Using Active@ UNDELETE Overview................................................................. 13 Recover deleted Files and Folders.............................................................................................. 14 Scan a Volume (Logical Drive) for deleted files..................................................................15 -
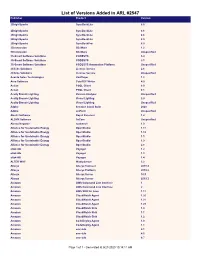
List of Versions Added in ARL #2547 Publisher Product Version
List of Versions Added in ARL #2547 Publisher Product Version 2BrightSparks SyncBackLite 8.5 2BrightSparks SyncBackLite 8.6 2BrightSparks SyncBackLite 8.8 2BrightSparks SyncBackLite 8.9 2BrightSparks SyncBackPro 5.9 3Dconnexion 3DxWare 1.2 3Dconnexion 3DxWare Unspecified 3S-Smart Software Solutions CODESYS 3.4 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions CODESYS Automation Platform Unspecified 4Clicks Solutions License Service 2.6 4Clicks Solutions License Service Unspecified Acarda Sales Technologies VoxPlayer 1.2 Acro Software CutePDF Writer 4.0 Actian PSQL Client 8.0 Actian PSQL Client 8.1 Acuity Brands Lighting Version Analyzer Unspecified Acuity Brands Lighting Visual Lighting 2.0 Acuity Brands Lighting Visual Lighting Unspecified Adobe Creative Cloud Suite 2020 Adobe JetForm Unspecified Alastri Software Rapid Reserver 1.4 ALDYN Software SvCom Unspecified Alexey Kopytov sysbench 1.0 Alliance for Sustainable Energy OpenStudio 1.11 Alliance for Sustainable Energy OpenStudio 1.12 Alliance for Sustainable Energy OpenStudio 1.5 Alliance for Sustainable Energy OpenStudio 1.9 Alliance for Sustainable Energy OpenStudio 2.8 alta4 AG Voyager 1.2 alta4 AG Voyager 1.3 alta4 AG Voyager 1.4 ALTER WAY WampServer 3.2 Alteryx Alteryx Connect 2019.4 Alteryx Alteryx Platform 2019.2 Alteryx Alteryx Server 10.5 Alteryx Alteryx Server 2019.3 Amazon AWS Command Line Interface 1 Amazon AWS Command Line Interface 2 Amazon AWS SDK for Java 1.11 Amazon CloudWatch Agent 1.20 Amazon CloudWatch Agent 1.21 Amazon CloudWatch Agent 1.23 Amazon -

Can I Download Xp Repair Cd
Can i download xp repair cd I want to do a Winows repair but can't find the original disc. for kubuntu, and download it, burn the iso to a disc, and boot from cd with in it. Download this iso and burn it to a CD/DVD/USB. It's the Windows XP Recovery Console that's included in the XP installation CD and should. Here is how to make a bootable XP Recovery Console CD and a Hiren's You can make a bootable Recovery Console CD by downloading an ISO file and windows xp repair/reinstall. I have lost my windows XP system restore recovery CD and was you can download and/or order all recovery disk from the Microsoft website. OK the title might be a bit off but can i download and burn onto a cd? Well I didnt get a repair CD when i purchased the desktop so just about XP professional repair without disk. The Windows XP installation CD-ROM includes recovery options on it. When booting from the CD-ROM you can access the recovery console to repair corrupted. Repair USB Key Instructions: Windows XP 1. Download from. 2. Double. Repairing Windows XP this way will fix damaged files but will keep other XP repair process, you will need to boot from the Windows XP CD. When purchased, many computers don't come with a Windows XP recovery setup disk, but you can download one for free from Microsoft. This is a download of file of just the Recovery Console for XP. -

Computer Hacking Forensic Investigator V4 Exam 312-49 CHFI Computer Hacking Forensic Investigator Training Program
Computer Hacking Forensic Investigator v4 Exam 312-49 CHFI Computer Hacking Forensic Investigator Training Program Course Description Computer forensics enables the systematic and careful identification of evidence in computer related crime and abuse cases. This may range from tracing the tracks of a hacker through a client’s systems, to tracing the originator of defamatory emails, to recovering signs of fraud. The CHFI course will give participants the necessary skills to identify an intruder's footprints and properly gather the necessary evidence to prosecute. Many of today's top tools of the forensic trade will be taught during this course, including software, hardware and specialized techniques. The need for businesses to become more efficient and integrated with one another, as well as the home user, has given way to a new type of criminal, the "cyber-criminal." It is no longer a matter of "will your organization be comprised (hacked)?" but, rather, "when?" Today's battles between corporations, governments, and countries are no longer fought only in the typical arenas of boardrooms or battlefields using physical force. Now the battlefield starts in the technical realm, which ties into most every facet of modern day life. If you or your organization requires the knowledge or skills to identify, track, and prosecute the cyber- criminal, then this is the course for you. The CHFI is a very advanced security-training program. Proper preparation is required before conducting the CHFI class. Who Should Attend . Police and other law enforcement personnel . Defense and Military personnel . e-Business Security professionals . Systems administrators . Legal professionals . Banking, Insurance and other professionals . -

Forensics Book 2: Investigating Hard Disk and File and Operating Systems
Forensics Book 2: Investigating Hard Disk and File and Operating Systems Chapter 7: Application Password Crackers Objectives Understand password terminology Use a password cracker Implement various cracking methods Perform system-level password cracking Perform application software password cracking Use default password databases Use password-cracking tools Copyright © by EC-Council Press All rights reserved. Reproduction is strictly prohibited Introduction This chapter: Deals with password crackers and the tools used in password recovery Covers concepts such as ways to bypass BIOS passwords, methods for removing CMOS batteries, and Windows XP/2000/NT keys Discusses BIOS password crackers and explains the Passware Kit, default password databases, and distributed network attacks Copyright © by EC-Council Press All rights reserved. Reproduction is strictly prohibited Password Terminology Passwords Gateway to most computer systems One of the easiest and most common ways to improve security: adopt good password procedures Passwords can be classified as weak or strong Strength of passwords can be calculated mathematically by the length of time it would take for a brute force cracker to discover them Strong passwords would take years to crack, while weak passwords could be broken in less than a second. Copyright © by EC-Council Press All rights reserved. Reproduction is strictly prohibited Password Terminology Strength of a password is not the only thing determining its quality Good password must also be easy for the creator -

Bad Dvd Repair Software Free Download Top 10 DVD Data Recovery Software Free in 2020
bad dvd repair software free download Top 10 DVD Data Recovery Software Free in 2020. This article will be proved as a boon for some who have lost the quality of their important data stored inside a CD/DVD. Amy Dennis. Jul 05, 2021 • Filed to: Windows Computer Solutions • Proven solutions. Lost all the hopes of getting your golden memories back? or getting irritated by the frequent pause and play sequence occurring repeatedly while you are watching an important presentation or a video? Get your DVD data recovered by the DVD recovery software available online for free and hold the smiles! This article will be proved as a boon for some who have lost the quality of their important data stored inside a CD/DVD. Previously when CDs/DVDs were in ample usage, we had to face problems of data getting corrupted by mishandling a DVD or by the increase in the frequency of usage. Forwarding or rewinding a video or audio often makes the DVD behave improperly. Unfortunately, when a DVD had completely stopped working or playing the video/ showing the data on the screen, we always thought of making a new DVD or buy a new one. Here, we are going to address you several DVD recovery software free which makes your data recovery easy and faster to prevent you from losing the data stored in your DVD. Nowadays, although people are using many other portable data storing disks and devices, in which data is kept more secure and undamaged but there are still some people who are having their favorite collections of audios and videos stored in a DVD from the previous time and they love it recalling. -
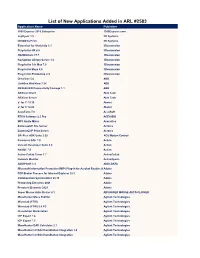
List of New Applications Added in ARL #2583
List of New Applications Added in ARL #2583 Application Name Publisher 1099 Express 2019 Enterprise 1099Express.com Lightyear 1.5 3D Systems DICOM to Print 3D Systems Extension for SketchUp 5.1 3Dconnexion Plug-In for NX 8.0 3Dconnexion 3DxWinCore 17.7 3Dconnexion Navigation Library Server 1.4 3Dconnexion Plug-In for 3ds Max 7.0 3Dconnexion Plug-In for Maya 6.0 3Dconnexion Plug-In for Photoshop 2.9 3Dconnexion DriveSize 5.6 ABB LinkOne WebView 3.24 ABB REX640 IED Connectivity Package 1.1 ABB ARXivar Client Able Tech ARXivar Server Able Tech a³ for C 19.10 AbsInt a³ for C 18.04 AbsInt AccuTerm 7.0 AccuSoft RTCA Software 2.3 Pro ACEA BIO MP3 Audio Mixer Acoustica ExtremeZ-IP File Server Acronis ExtremeZ-IP Print Server Acronis SPiiPlus ADK Suite 2.50 ACS Motion Control Pervasive.SQL 7.0 Actian Versant Developer Suite 6.0 Actian NoSQL 7.0 Actian Active Collab Timer 1.7 ActiveCollab Network Monitor ActiveXperts ADDIPACK 1.4 ADDI-DATA Microsoft Information Protection (MIP) Plug-in for Acrobat Reader 20.0Adobe PDF Broker Process for Internet Explorer 20.1 Adobe Collaboration Synchronizer 20.13 Adobe Photoshop Elements 2021 Adobe Premiere Elements 2021 Adobe Super Mouse Auto Clicker 4.1 ADVANCED MOUSE AUTO CLICKER MassHunter Mass Profiler Agilent Technologies MicroLab (FTIR) Agilent Technologies MicroLab (FTIR) 5.4 PC Agilent Technologies Dissolution Workstation Agilent Technologies ICP Expert 7.4 Agilent Technologies ICP Expert 7.3 Agilent Technologies MassHunter DAR Calculator 2.1 Agilent Technologies MassHunter LC/SQ ChemStation Integration -

Nulled Afterlogic Webmail Pro Php ->>->>->> DOWNLOAD
Nulled Afterlogic Webmail Pro Php ->>->>->> DOWNLOAD 1 / 6 2 / 6 iobit driver booster pro crack key for idm genarts sapphire plugins keygen torrent recovery toolbox for coreldraw full crack software total video converter 3.14 crack free download windows 8.1 pro full version activate online crack ias geography notes in pdf galaxy on fire 2 valkyrie add on crack ableton live 9 5 crack macbook samsung serial number on box fort knox personal firewall crack gamesocket gold miner game full version photoshop cs4 download cracked version sj news frontpage nulled php fmrte 14 crack chomikuj minecraft pinnacle studio 16 crack without survey crack para labview 2014 xilinx civ 3 complete no-cd crack for mac wos 3 keygen generator sims serial number adobe acrobat x pro mac japanese kit kat flavors cracked ribs crack the skye oblivion lyrics mastodon wanapum dam crack crescent bar real estate advanced uninstaller pro serial code windows 10 free download full version for xp nevosoft universal crack 2013 ford dxo optics pro 8 elite mac crack torrent starcraft 2 heart of the swarm multiplayer crack eminem 50 cent crack a bottle livejournal cracked an egg and it was red avcware video converter ultimate 7.3.1 crack cocaine art vista virtual grand piano keygen crack anime studio 7 serial number generator faisanes en venta argentina warez relinking files in after effects cs5 keygen max msp 5 1 keygen free path finder 6 3 keygen music crack amada ap100 download google download endnote x7 mac crack the battle for middle earth 2 crack download thinprint rdp -

Advanced Office Password Recovery Full Version Free
1 / 2 Advanced Office Password Recovery Full Version Free - Advanced Office Password Recovery Free edition software download. 3,154 views3.1K views. • Dec 30, 2019. 26 11. Save. 26 / 11 .... Advanced Office Password Recovery 6.61 Serial Key Latest Free. Advanced ... Paste it in the directory and upgrade yourself to the full version.. This program allows you to recover lost or forgotten passwords to files and documents created in Microsoft Office applications including Word, Excel, Access, .... Free Download Advanced Office Password Recovery Pro 6.50.2206 Full Version - Recover or remove passwords protecting documents.. Advanced Office Password Recovery Pro 6.34 [Free] Keygen Plus Crack. Advanced Office Password Recovery Pro Serial is a nice, trial version .... Download Gratis ElcomSoft Advanced Office Password. Recovery Full Version. SINGLE LINK (21 MB). Download Via: USERSCLOUD | ZIPPYSHARE.. GPU-accelerated tool to recover passwords of Word documents. ... The program employs the most advanced password recovery technique ... All Passcape registered products include FREE LIFETIME TECHNICAL ... Forum · Order full version .... Advanced Office Password Recovery 6.22 Free Latest Version and Single Link for Windows. It is Also full offline Setup and standalone installer .... Advanced Office Password Recovery 6.22 Full is very useful application ... All Done Enjoy Advanced Office Password Recovery Full Version.. In other words, if you wish to retrieve the password for the advanced version of office programs, then you must purchase the premium version. The ... Download Advanced Office Password Recovery free - Windows programs ... Advanced Office Password Recovery 4.15 Crack Serial Download Full. Advanced Office ... Full version downloads hosted on high speed servers! Advanced Office ... -
Khi Đọc Qua Tài Liệu Này, Nếu Phát Hiện Sai Sót Hoặc Nội Dung Kém Chất
Khi đọc qua tài liệu này, nếu phát hiện sai sót hoặc nội dung kém chất lượng xin hãy thông báo để chúng tôi sửa chữa hoặc thay thế bằng một tài liệu cùng chủ đề của tác giả khác. Tài liệu này bao gồm nhiều tài liệu nhỏ có cùng chủ đề bên trong nó. Phần nội dung bạn cần có thể nằm ở giữa hoặc ở cuối tài liệu này, hãy sử dụng chức năng Search để tìm chúng. Bạn có thể tham khảo nguồn tài liệu được dịch từ tiếng Anh tại đây: http://mientayvn.com/Tai_lieu_da_dich.html Thông tin liên hệ: Yahoo mail: [email protected] Gmail: [email protected] 8/26/2009 TRƢỜNG CAO ĐẲNG NGHỀ CNTT iSPACE Website: http://www.ispace.edu.vn MH/MĐ: LẮP RÁP VÀ CÀI ĐẶT MÁY TÍNH Bài 1: LỊCH SỬ PHÁT TRIỂN MÁY TÍNH Bài 2: ĐẶC TRƢNG VÀ CÁC THÀNH PHẦN MÁY TÍNH Bài 3: BỘ XỬ LÝ VÀ NHỮNG ĐẶC TRƢNG CÔNG NGHỆ Bài 4: BO MẠCH CHỦ VÀ HỆ THỐNG BUS Bài 5: BIOS VÀ CMOS Bài 6: BỘ NHỚ CHÍNH – RAM Bài 7: CHUẨN THIẾT BỊ LƢU TRỮ Bài 8: THIẾT BỊ VÀ CÔNG NGHỆ LƢU TRỮ Bài 9: THIẾT BỊ NGOẠI VI VÀ CHUẨN GIAO TIẾP Bài 10: BỘ NGUỒN - PSU Bài 11: XÂY DỰNG HỆ THỐNG MÁY TÍNH Bài 12: CÀI ĐẶT HỆ THỐNG MÁY TÍNH Bài 13: CHẨN ĐOÁN VÀ XỬ LÝ SỰ CỐ CƠ BẢN BÁO CÁO ĐỒ ÁN CUỐI MÔN THI CUỐI MÔN TRƢỜNG CAO ĐẲNG NGHỀ CNTT iSPACE Website: http://www.ispace.edu.vn BÀI 1: LỊCH SỬ PHÁT TRIỂN MÁY TÍNH Tìm hiểu lịch sử ra đời và phát triển của máy tính. -

Cd Repair Software Mac
Cd repair software mac Mac CD and DVD Data Recovery software can recover videos, photos, music, images and other files from CD and DVD Disc. The best data recovery software Mac recovers lost, deleted, formatted files from Each scratch causes a part of the data stored on CDs / DVDs to become. CD/DVD Recovery for Mac How to recover files from CD/DVD on Mac? Looking to Previously, you have downloaded Soft Data Recovery software. What is the software for CD DVD data recovery software? Data Recovery Freeware, Software & Services For Microsoft Windows 10 and Mac. It comes with an emergency boot CD that you can use to recover data when the Excellent Mac Disk repair software is provided above, for you to consider and. Buy CD/DVD Recovery Apps, Free vs. Paid ColorMango - Discount Software Store Windows (2): Mac (0) OFFICE FILE REPAIR: DATABASE FILE REPAIR: BACKUP FILE REPAIR: MULTIMEDIA FILE REPAIR: OTHER FILE REPAIR. DiskWarrior, the world's most advanced and highest rated hard disk, hard drive, and disk repair and data recovery tool for macOS, OS X and Mac OS X. Simply. This topic describes how to repair the disk that started up your Mac. If you're having trouble with another disk, you can repair it with fewer steps. For more. Bad CD/DVD Recovery is Professional the leading data recovery software for CD, DVD. Bad CD/DVD Recovery can effectively recover and rescue corrupted or. In our review of the top free CD recovery programs we found several we could recommend with the best of Windows, Mac and Linux software reviews.