Mobile Censorship: What's Happening and What We Can Do About
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

La Quadrature Du Net Campaigning on Telecoms Package Pan-European Activism for Patching a “Pirated” Law
25th Chaos Communication Congress Nothing to hide Berlin, 2008-12-30 La Quadrature du Net Campaigning on Telecoms Package Pan-european activism for patching a \pirated" law by J´er´emieZimmermann <[email protected]> \Whatever you do will be insignificant, but it is very important that you do it." Mohandas Karamchand Gandhi Contents Prelude 3 Who are we ? 4 Who is La Quadrature du Net ...................................4 Why this name?..........................................4 They support La Quadrature du Net ...............................5 Campaign on Telecoms Package6 Squaring the net..........................................6 The debate is open.........................................7 European Parliament rejects graduated response........................8 Will France Introduce the Digital Guillotine in Europe?....................8 Privacy: Film industry pirates European law..........................9 MEPs want to torpedo the Free Internet on July 7th...................... 10 The \Telecoms Package": out of the shadows, into the light.................. 10 Telecoms Package: vote postponed................................ 11 Telecoms Package: the spectre of the graduated response hangs over Europe......... 12 Telecoms Package: protect the free and just society!...................... 12 Telecoms Package: European democracy's victory already threatened............. 13 Letter sent to all MEPs on september 23rd........................... 14 Graduated Response: The Lesson................................. 15 \Graduated response": Will France -

Press Release for JV Completion 01 04 10 2
press release April 1, 2010 Deutsche Telekom and France Telecom announce completion of UK merger London, Bonn, Paris. April, 1, 2010: Further to announcements of 8 th September 2009, and to the obtaining of all necessary approvals, Deutsche Telekom and France Telecom today announced the successful completion of the UK merger transaction and the formation of the new Joint Venture. The JV will be accounted for using the equity method as of April 2010 for both Deutsche Telekom and France Telecom. Tom Alexander, former CEO of Orange UK, is the Chief Executive of the new Joint Venture, and Richard Moat, the former CEO of T-Mobile UK, is Chief Financial Officer and Deputy CEO. A Board of Directors has also been formed, on which Tom Alexander and Richard Moat will serve as executive directors. Tim Höttges, CFO of Deutsche Telekom, will lead the board as non-executive chairman for two years. After this time, the leadership will rotate to Gervais Pellissier, Deputy CEO and CFO of France Telecom, for two years. Also joining the six-person Board as non-executive directors are Philipp Humm, Chief Regional Officer Europe for Deutsche Telekom and Olaf Swantee, Executive Vice President Europe at France Telecom. About Deutsche Telekom Deutsche Telekom is one of the leading integrated telecommunications companies worldwide with more than 151 million mobile customers, more than 38 million fixed-network lines and more than 15 million broadband lines (as at: December 31, 2009). As an international group of companies in around 50 countries throughout the world with almost 260,000 employees (as at: December 31, 2009), Deutsche Telekom generated more than half of its revenues of EUR 64.6 billion outside Germany in 2009. -
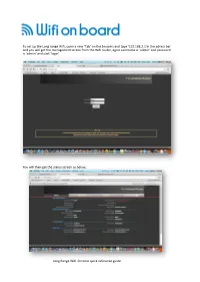
Long Range Wifi Tube Settings
To set up the Long range Wifi, open a new ‘Tab’ on the browers and type ‘192.168.2.1’in the adress bar and you will get the management screen from the Wifi router, again username is ‘admin’ and password is ‘admin’ and click ‘login’ You will then get the status screen as below, Long Range Wifi Chrome quick reference guide Click ‘Easy Setup and select the WAN connections and ‘Client Router Mode’ and click on ‘Next’ On the next screen click ‘Site Survey” Long Range Wifi Chrome quick reference guide This will bring up a screen with all the available WiFi hotspots in the area. Select the WiFi Hotspot you require, the system will connect to most Wifi access points with a signal greater than -80dB ie -79dB to 0dB. Select the Wifi you want in this case BT with FON and click ‘Select’ N o w If you have selected a known Wifi with and access code you will be asked to enter this as the ‘Passkey’ So if you have been to a Bar and have the code this is where you enter it. Set the power level to 24-27 if requires some units do not have this field.. Long Range Wifi Chrome quick reference guide Select Next on the following screens until you reach done and the unit will reboot. Open another tab on you browser and you shold be connected to the Internet, you can also log back into the Long ranage WiFi on 192.168.2.1 and check the status of the connection If you are connected as in this case to BT Openzone, enter your account details and connect to the internet, all other devices will not need to logon to BT or the Public Wifi provider. -

Protecting Net Neutrality in the Telecoms Package
September 24th, 2009 Protecting Net Neutrality In the Telecoms Package Network Neutrality is a constitutional principle of the Internet's architecture. It was conceived as an efficient decentralized network and was designed according to an axiom that technological neutrality is the foundation of freedom in communications infrastructure. Built into the network was also an idea about equality, that society as a whole benefits when we defend against discrimination and unfair advantage. Moreover, Net neutrality stimulates the virtuous circle of a development model based on the growth of a common communication network that enables new uses and tools, as opposed to one relying on investments in filtering and controlling, that would lead to a fragmentation of the Internet. Network Neutrality is the safeguard of civil and human rights, and of fair competition for innovation. It is now that the principle of network neutrality is being challenged in the current version of the Telecom Package that it has become a matter of public policy debate in Europe. The shape of our future networks and the rights and freedoms of citizens on the Internet is what is being voted on in this major reform of the European framework for telecommunications regulation. This memorandum lays out the public interest issues at stake in the Telecoms Package. It explains what Network Neutrality is and why openness is important to telecommunications infrastructure. It outlines the social and economic benefits of a regulatory regime that preserves network neutrality. It identifies the specific language in the key provisions that risk fundamental rights and freedoms. It concludes with a guide to making Network Neutrality a fundamental regulatory principle in the European telecommunications market. -

Everything Everywhere, Telefónica UK and Vodafone UK to Form Mobile Marketing and Payments Joint Venture
Everything Everywhere, Telefónica UK and Vodafone UK to form mobile marketing and payments joint venture Ground breaking venture promises to accelerate the development of innovative mobile services for consumers and business customers • Creation of a single ecosystem for m-commerce helping advertisers, retailers and banks to reach consumers through their mobile phones • Consumers will be able to replace their physical wallet with a secure mobile wallet using Near Field Communications (NFC) technology to pay for goods and services • Consumers will also benefit from relevant offers and coupons, delivered direct to their phone • Everything Everywhere, Telefónica UK and Vodafone UK to provide start-up investment London. 16 June 2011. Everything Everywhere, Telefónica UK and Vodafone UK today announce plans to create a standalone m-commerce joint venture (JV). The new entity, the first of its kind in the UK, will bring together the expertise and technology of the UK’s leading mobile operators, enabling the rapid development and delivery of new mobile marketing and payment services. The JV will provide a single contact for advertisers, marketing partners, retailers and banks making it far easier to create m-commerce products and services. The JV will be open and available to all industry participants, maximising benefits to consumers. The JV is subject to competition clearance and is aiming to launch before the end of the year. Enabling mobile payments The JV will deliver the technology required for the speedy adoption of mobile wallet and payments. This will enable consumers to transfer their entire physical wallet into a new secure, SIM-based wallet regardless of which NFC enabled mobile device, or mobile network they are using. -

Case No COMP/M.6314 – Telefónica UK/ Vodafone UK/ Everything Everywhere/ JV
EN This text is made available for information purposes only. A summary of this decision is published in all EU languages in the Official Journal of the European Union. Case No COMP/M.6314 – Telefónica UK/ Vodafone UK/ Everything Everywhere/ JV Only the EN text is authentic. REGULATION (EC) No 139/2004 MERGER PROCEDURE Article 8 (1) Date: 4/09/2012 EUROPEAN COMMISSION Brussels, 4.9.2012 C(2012) 6063 final PUBLIC VERSION COMMISSION DECISION of 4.9.2012 addressed to: - Telefónica UK - Vodafone Group - Everything Everywhere declaring a concentration to be compatible with the internal market and the functioning of the EEA Agreement (Case No COMP/M.6314 – Telefónica UK / Vodafone UK / Everything Everywhere / JV) (Only the EN version is authentic) TABLE OF CONTENTS COMMISSION DECISION addressed to: - Telefónica UK - Vodafone Group - Everything Everywhere declaring a concentration to be compatible with the internal market and the functioning of the EEA Agreement (Case No COMP/M.6314 – Telefónica UK / Vodafone UK / Everything Everywhere / JV) ............................................................................................ 7 1. NOTIFICATION.......................................................................................................... 7 2. THE NOTIFYING PARTIES ...................................................................................... 8 3. THE OPERATION AND THE CONCENTRATION ............................................... 10 4. UNION DIMENSION .............................................................................................. -

Privacy International, Human and Digital Rights Organizations, and International Legal Scholars As Amici Curiae in Support of Respondent
No. 17-2 IN THE Supreme Court of the United States IN THE MdATTER OF A WARRANT TO SEARCH A CERTAIN EMAIL ACCOUNT CONTROLLED AND MAINTAINED BY MICROSOFT CORPORATION UNITED STATES OF AMERICA, Petitioner, —v.— MICROSOFT CORPORATION, Respondent. ON WRIT OF CERTIORARI TO THE UNITED STATES COURT OF APPEALS FOR THE SECOND CIRCUIT BRIEF OF PRIVACY INTERNATIONAL, HUMAN AND DIGITAL RIGHTS ORGANIZATIONS, AND INTERNATIONAL LEGAL SCHOLARS AS AMICI CURIAE IN SUPPORT OF RESPONDENT LAUREN GALLO WHITE BRIAN M. WILLEN RYAN T. O’HOLLAREN Counsel of Record WILSON, SONSINI, GOODRICH BASTIAAN G. SUURMOND & ROSATI, P.C. WILSON, SONSINI, GOODRICH One Market Plaza Spear Tower, & ROSATI, P.C. Suite 3300 1301 Avenue of the Americas, San Francisco, California 94105 40th Floor (415) 947-2000 New York, New York 10019 [email protected] (212) 999-5800 [email protected] [email protected] [email protected] Attorneys for Amici Curiae (Counsel continued on inside cover) CAROLINE WILSON PALOW SCARLET KIM PRIVACY INTERNATIONAL 62 Britton Street London, EC1M 5UY United Kingdom [email protected] [email protected] i QUESTION PRESENTED Whether construing the Stored Communications Act (“SCA”) to authorize the seizure of data stored outside the United States would conflict with foreign data-protection laws, including those of Ireland and the European Union, and whether these conflicts should be avoided by applying established canons of construction, including presumptions against extra- territoriality and in favor of international comity, which direct U.S. courts to construe statutes as applying only domestically and consistently with foreign laws, absent clear Congressional intent. ii TABLE OF CONTENTS PAGE QUESTION PRESENTED .......................... -

Piracy Versus Privacy: an Analysis of Values Encoded in the Piratebrowser
International Journal of Communication 9(2015), 818–838 1932–8036/20150005 Piracy Versus Privacy: An Analysis of Values Encoded in the PirateBrowser BALÁZS BODÓ University of Amsterdam, Institute for Information Law The Netherlands The PirateBrowser is a Web browser that uses Tor privacy-enhancing technology to circumvent nationally implemented Internet filters blocking access to The Pirate Bay. This article analyzes the possible consequences of a mass influx of copyright pirates into the privacy domain. The article addresses the effects of the uptake of strong privacy technologies by pirates on copyright enforcement and on free speech and privacy technology domains. Also discussed are the norms and values reflected in the specific design choices taken by the developers of the PirateBrowser. Keywords: piracy, privacy, Tor, privacy-enhancing technologies, policy Introduction Tor (The Onion Router), “endorsed by Egyptian activists, WikiLeaks, NSA, GCHQ, Chelsea Manning, Snowden” (Dingledine & Appelbaum, 2013), is a volunteer network of computers that relays Web traffic through itself to provide anonymous, unobserved, and uncensored access to the Internet. It has about 4,000 relays and about 1,000 exit nodes. Tor users connect to the network, and their Web traffic is channeled through the internal relays to reach its final destination through one of the exit nodes. This arrangement makes the identification and surveillance of Tor users difficult. Anonymity is promised by the difficulty of tracing the Web traffic that appears on the exit node back to the individual who initiated the traffic, as long as there is a sufficient number of internal hops in between. Protection from surveillance is granted by the fact that each link in the communication chain is encrypted. -

The World Tomorrow, Episode 8 Cyberpunks #1
Air date 5 Jun 2012 Episode 8 – Cyberpunks #1 Jacob Applebaum is a staff research scientist at the University of Washington, and a developer and advocate for the Tor Project, which is an online anonymity system for everyday people to fight against surveillance and against internet censorship. Jacob believes that everybody has the right to read, without restriction, and the right to speak freely, with no exception. In 2010, when Julian Assange couldn’t deliver a talk in New York, Jacob gave the talk instead. Since then, he has been harrassed by the U.S. government: interrogated at airports, subjected to invasive pat-downs while being threatened with prison rape by law enforcement officials, had his equipment confiscated and his online services subject to secret subpoena. Jacob is uncowed by these measures, and remains an outspoken advocate of freedom of expression, and a vocal supporter of WikiLeaks. Andy Mueller-Maguhn is a long time member of the Chaos Computer Club in Germany, and a former spokesman. He is a specialist on surveillance, working in a journalistic capacity on the surveillance industry with his project wiki, buggedplanet.info. Andy works in cryptographic communications, and runs a company called Cryptophone, which markets secure voice communication devices to commercial clients. From worldtomorrow.wikileaks.org/episode-8.html 1 30 October 2013 Jeremie Zimmermann is the co-founder and spokesperson for the citizen advocacy group La Quadrature du Net, the most prominent European organization defending anonymity rights online and promoting awareness of regulatory attacks on online freedoms. Jeremie works to build tools for the public to use to take part in public debate and to try to change things. -

De Filippi & Tréguer
May 2014 Expanding the Internet Commons : The Subversive Potential of Wireless Community Networks by Primavera De Filippi1 and Félix Tréguer2 “Freedom is fostered when the means of communication are dispersed, decentralized, and easily available, as are printing presses and microcomputers. Central control is more likely when the means of communication are concentrated, monopolized, and scarce, as are great networks,” wrote professor Ithiel de Sola Pool (1984), an American political scientist and legal analyst of communications technologies. Beyond highlighting historical and technical trends in technology, Sola Pool also understood that there was nothing deterministic about how technologies evolve. While control over printing presses and microcomputers can, as it turns out, be highly centralized, the deployment and management of telecommunication networks can, eventually, undergo a process of decentralization. The outcome ultimately depends on political, technical, economic, institutional and legal arrangements shaping both the development of communications tools and their use. Often, when it comes to politics – and Internet policy is obviously no exception – the antagonism between freedom and control essentially comes down to the trade-off between centralization or decentralization. In the past year, the ongoing controversy regarding the massive surveillance undertaken by the US National Security Agency (NSA) and its allied organizations has encouraged a growing number of technology activists to deploy decentralized and free software3 alternatives to the centralized online services known to collaborate with the NSA. This trend can be likened to what happened repeatedly in the history of the Internet. The rise of the personal computer and the widespread adoption of the Internet network came out of a need to democratize computing technologies by taking them out of the hands of technocracy – decentralizing both the use of computers and the control of communication technologies. -

Presentation Contains Forward-Looking Statements That Reflect the Current Views of Deutsche Telekom Management with Respect to Future Events
Combination of Orange UK & T-Mobile UK: Creating a new mobile champion 8 September 2009 Deutsche Telekom Disclaimer This presentation contains forward-looking statements that reflect the current views of Deutsche Telekom management with respect to future events. They include, among others, statements as to market potential and financial guidance statements, as well as our dividend outlook. They are generally identified by the words “expect,” “anticipate,” “believe,” “intend,” “estimate,” “aim,” “goal,” “plan,” “will,” “seek,” “outlook” or similar expressions and include generally any information that relates to expectations or targets for revenue, adjusted EBITDA, earnings, operating profitability or other performance measures, as well as personnel related measures and reductions. Forward-looking statements are based on current plans, estimates and projections. You should consider them with caution. Such statements are subject to risks and uncertainties, most of which are difficult to predict and are generally beyond Deutsche Telekom’s control, including those described in the sections “Forward-Looking Statements” and “Risk Factors” of the Company’s Annual Report on Form 20-F filed with the U.S. Securities and Exchange Commission. Among the relevant factors are the progress of Deutsche Telekom’s work-force reduction initiative, restructuring of its German operations and the impact of other significant strategic or business initiatives, including acquisitions, dispositions and business combinations and cost-saving initiatives. In addition, -

British Telecommunications Plc Annual Report and Form 20-F 2011 1 02 U10648 Report of the Directors.Qxp:BT PLC 02 19/5/11 17:39 Page 2 Bleed: 0 Mm Scale: 100%
Bringing it all together Annual BRITISH TELECOMMUNICATIONS plc BRITISH TELECOMMUNICATIONS Report & Form 20-F 201 1 British Telecommunications plc Registered offi ce: 81 Newgate Street, London EC1A 7AJ Registered in England No. 1800000 Produced by BT Group Designed by Greentarget, London Typeset by RR Donnelley Printed in England by Leycol Printers Ltd Printed on elemental chlorine-free paper Sourced from sustainably managed forests www.bt.com As a wholly-owned subsidiary of BT Group plc, British Telecommunications plc meets the PHME 59915 conditions set forth in General Instruction (I)(1)(a) and (b) of Form 10-K as applied to reports on Form 20-F and is therefore fi ling this Form 20-F with the reduced disclosure format. U10648_CoverSpread.indd 1 19/5/11 22:32:16 01_U10648_Contents.qxp:BT PLC 01 19/5/11 17:39 Page 1 Bleed: 0mm Scale: 100% BT is one of the world’s leading communications services companies, serving the needs of customers in the UK and in more than 170 countries worldwide. CONTENTS 2 Report of the Directors 2 Business review 19 Financial review 28 Statutory information 30 Statement of directors’ responsibilities 31 Report of the independent auditors – consolidated financial statements 33 Consolidated financial statements 90 Report of the independent auditors – parent company financial statements 91 Financial statements of British Telecommunications plc 108 Subsidiary undertakings and associate 109 Additional information for shareholders 114 Cross reference to Form 20-F This is the Annual Report for the year ended 31 March 2011. It complies with UK regulations and comprises part of the Annual Report on Form 20-F for the US Securities and Exchange Commission to meet US regulations.