Mobile Context-Aware Game for the Next Generation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mypal A600A600A600A600
MyPal MyPalMyPalMyPal A600A600A600A600 ® MyPal A600 User’s Manual MyPal A600 Microsoft MS ActiveSync Windows Microsoft Intel Intel ©2002 Mypal A600 1.00 T1054 2002 7 2 MyPal A600 Pocket PC MyPal A600 ASUSTeK COMPUTER INC.( ) 150 886-2-2894-3447 [email protected] 0800-093-456 ... / / / / 886-2-2890-7113 ... 886-2-2890-7114 ... 886-2-2890-7698 [email protected] cscnews.asus.com.tw www.asus.com ASUS COMPUTER INTERNATIONAL ( ) 6737 Mowry Avenue, Mowry Business Center, Building 2 Newark, CA 94560, USA +1-510-608-4555 [email protected] ASUS Technology Service Inc. +1-502-995-0883 +1-502-933-8713 [email protected] 7100 Intermodal Dr.Suite - A Louisville Ky,40258 USA ASUS Holland BV. ( ) +31-(0)591-668190 ... +31-(0)591-666852 [email protected] [email protected] [email protected] [email protected] www.asus.com.tw FTP ftp.asus.com.tw/pub/ASUS MyPal A600 Pocket PC 3 MyPal A600 1. ( http:// www.asus.com.tw) 2. - 1. http://www.asusmall.com.tw/accounts/member/ Chinese (TWN) Registration ( ) Join Membership ( ) 2. http://www.asus.com.tw/ ASUS Membership Asus Member's Area Chinese(TWN) Join Membership ( ) "*" ( ) Agree and continue( ) 1. " " ( ) 2. 0800-093-456 Flash ROM A600T---------- IIIIIIIIIIIIIIIIIIIIIIIII xxAPxxxxxx---------------- 4 MyPal A600 Pocket PC MyPal A600 1. 2. 3. (1) (2) (3) LCD LCD 1. 2. 3. 4. 5. 6. 7. 8. 9. 1. 0800-093-456 2. 48 48 3. 0800-093- 456 4. 5. !!! MyPal A600 Pocket PC 5 MyPal A600 MyPal A600 6 MyPal A600 Pocket PC MyPal A600 0 30 50 122 20~30 - - - MyPal A600 Pocket PC 7 MyPal A600 ..................................................................... -

Pocket PC Backup/Restore Made Easy
Pocket PC backup/restore made easy Last year in the September 2005 issue of the First Responder we had an article on backing up the PEAC-WMD software application to either a PC or to the flash memory on the PDA. This is still a problem customers are encountering and I thought that revisiting the problem and the solutions would be of assistance to our customers and others that encounter this problem with Pocket PCs. Background Before getting into the mechanics of the backup and restore processes a short discussion about the problem may help Pocket PC users understand the problem. The Pocket PC processor draws power regardless of whether the unit is turned ON or OFF. The ON/OFF button simply turns the display ON/OFF, and since the display is one of the primary power consumers on the PDA, shutting off the display will extend the useful life of the battery on a single charge. Most of the batteries on the Pocket PCs are Lithium-Hydride (LiH) units and typically have a pretty reasonable performance. But like any battery, over time they will degrade and may have to be replaced. The primary thing to remember – periodically charge the PDA! Well that’s easy for me to say, but in the real world that’s not always easy to do. Many fire departments like to mount the PDA in the cab of a vehicle so it’s ready when rolling out to a Hazmat incident. Great plan and the right idea, but sometimes the charger isn’t connected to power and before long the unit is dead. -

Developing Applications for Pocket PC and GPRS/EDGE Devcentral White Paper
Developing Applications for Pocket PC and GPRS/EDGE devCentral White Paper Document Number 12588 Revision 2.0 Revision Date 10/15/03 AT&T Wireless Developer Program © 2003 AT&T Wireless. All rights reserved. Legal Disclaimer This document and the information contained herein (collectively, the "Information") is provided to you (both the individual receiving this document and any legal entity on behalf of which such individual is acting) ("You" and "Your") by AT&T Wireless Services, Inc. ("AWS") for informational purposes only. AWS is providing the Information to You because AWS believes the Information may be useful to You. The Information is provided to You solely on the basis that You will be responsible for making Your own assessments of the Information and are advised to verify all representations, statements and information before using or relying upon any of the Information. Although AWS has exercised reasonable care in providing the Information to You, AWS does not warrant the accuracy of the Information and is not responsible for any damages arising from Your use of or reliance upon the Information. You further understand and agree that AWS in no way represents, and You in no way rely on a belief, that AWS is providing the Information in accordance with any standard or service (routine, customary or otherwise) related to the consulting, services, hardware or software industries. AWS DOES NOT WARRANT THAT THE INFORMATION IS ERROR-FREE. AWS IS PROVIDING THE INFORMATION TO YOU "AS IS" AND "WITH ALL FAULTS." AWS DOES NOT WARRANT, -
Windows Embedded Compact | Microsoft Wiki | Fandom Windows Embedded Compact
8/24/2020 Windows Embedded Compact | Microsoft Wiki | Fandom Windows Embedded Compact Windows Embedded Compact,[1] formerly Windows Embedded CE Windows Embedded Compact and Windows CE, is an operating system subfamily developed by Microsoft as part of its Windows Embedded family of products.* Unlike Windows Embedded Standard, which is based on Windows NT, Windows Embedded Compact uses a different hybrid kernel.[2] Microsoft licenses Windows CE to original equipment manufacturers (OEMs), who can modify and create their own user interfaces and experiences, with Windows CE providing the technical foundation to do so. The current version of Windows Embedded Compact supports x86 and ARM processors with board support package (BSP) directly.[3] The MIPS and SHx architectures had support prior to version 7.0. On every version, changing the view options like showing hidden stuff in the Windows folder will lead you a bunch of stuff. Most of them are just images, while those files are a bunch of system files. The "homelogo" file is used in Internet Explorer Mobile, it can be seen on the home page (it Developer Microsoft probably appears on 6.0 and lower) and on these versions, it haves the old CE logo that can be customized on the desktop to make it look like a OS family Windows old version. Working state Supported Contents [show] Source model Closed Source Released November 16, 1996 Features as Windows CE 1.0 Windows CE is optimized for devices that have minimal memory; a Windows CE kernel may run with one megabyte of memory.[4] Devices Final release 8.0 (Embedded Compact 2013) are often configured without disk storage, and may be configured as a June 13, 2013 "closed" system that does not allow for end-user extension (for instance, it can be burned into ROM). -

Acer N10 Handheld COPYRIGHT
Manual for Acer n10 Handheld COPYRIGHT Copyright © 2003 Acer Inc. or its subsidiaries All Rights Reserved. Printed in Taiwan. Acer n10 Handheld Manual Original issue: August 2003 Acer and the Acer logo are registered trademarks of Acer Inc. Microsoft, ActiveSync, Outlook, Pocket Outlook, Windows, Windows NT, and the Windows logo are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Microsoft products are licensed to OEMs by Microsoft Licensing, Inc., a wholly owned subsidiary of Microsoft Corporation. Other company’s product names or trademarks are used herein for identification purpose only and belong to their respective companies. Changes may be made periodically to the information in this publication without obligation to notify any person of such revision or changes. Such changes will be incorporated in new editions of this Manual or supplementary documents and publications. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopy, recording, or otherwise, without the prior written permission of Acer Inc. DISCLAIMER AND LIMITATION OF LIABILITY Acer and its subsidiaries makes no representations or warranties, either expressed or implied, with respect to the contents hereof and specifically disclaims the implied warranties of merchantability or fitness for a particular purpose. Acer and its subsidiaries assume no responsibility for any damage or loss resulting from the use of this Acer n10 Handheld Manual. NOTES Record the serial number, purchase date, and place of purchase information in the space provided below. The serial number is recorded on the label affixed to your Acer n10. -

Personal Digital Assistants: Which One Is Right for Your Practice?
Vol. 01, No. 12 / December 2002 Personal digital assistants: Which one is right for your practice? PDAs come in many models and offer a range of features and extras. Here’s help sorting through the options. John Luo, MD Assistant clinical professor and director of psychiatric informatics Department of psychiatry University of California-Davis, Sacramento Personal digital assistants (PDAs) are becoming more commonplace in practice because they immediately provide critical information at the point of care. If you’re in the market for a handheld computer, chances are you’re fazed by the multitude of available models, upgrades, and extras. Choosing a PDA is not that difficult, however, if you take the time to assess your needs and do a little homework. Start by answering these four questions: 1. Why do I need a PDA? Look at your work patterns and see how a PDA would fit in. Do you frequently look up DSM-IV criteria and other reference information? Are you constantly writing prescriptions, giving presentations, or assessing drug-drug interactions? Do you find yourself regularly checking your schedule? Also try to envision: z where you would carry the device z where, when, and how you would charge it when needed z what connections to computers for data exchange are available z with whom you would share data z and from whom you could get technical support. You may have trouble thinking that far ahead, but doing so will help you narrow your PDA choices. 2. Which operating system should I use? A PDA operates on one of four main operating systems: z Palm OS, the most popular world wide z EPOC OS, which is more popular in Europe z Pocket PC, which is rapidly gaining popularity z and Linux OS, which recently entered the PDA market. -

Porting Unicon to Windows Mobile 2003
Porting Unicon to Windows Mobile 2003 David Price November 4, 2005 Abstract This report summarizes the port of Unicon to an operating system intended for mobile computing, Windows Mobile 2003. It describes the features available, unavailable and possible on Windows Mobile 2003 for the Unicon programming language. It also covers building Unicon for use on Windows Mobile 2003 and running Unicon on Windows Mobile 2003. 1 1.0 Introduction Handheld computing devices on the market range in capability from simple calculators to processors whose power exceeds desktop computers from recent memory. Handheld processing devices are usually coupled with other familiar devices, such as: cell phones, drawing tablets, input scanners, cameras and Global Positioning Systems. Mid to higher end devices feature operating systems, processors capable of several hundred megahertz, storage on the order of 32 to 64 megabytes, graphics displays with resolutions of 240x320 to 640x480 pixels at 16 bit color (some may even feature 3D graphics) and have networking allowing them to communicate with the internet, desktop computers and other handheld devices. Typically, these devices include software for web browsing, emailing, mp3 and other multimedia playback, simplified word processors, spreadsheets and instant messagers of various types. Two of the largest operating systems makers, in terms of devices and users, for handheld computing devices are from Microsoft, with its Windows CE derived operating systems, and Palm, with several versions of PalmOS. Many different versions of these operating systems are available on a wide variety of devices from both companies. Currently, Microsoft provides OSes including: Windows Mobile 2003, Windows Mobile 2003 Second Edition, Windows Mobile 2003 Phone Edition and Second Edition Phone and Smart Phone 2003, all based off of Windows CE.net 4.20. -

Econnect User Guide
eConnect™ User Guide 110 Lake Avenue South, Suite 35 Nesconset, NY 11767 Phone (631) 360-3400 Fax (631) 360-3268 Website: http://www.invisionsoft.com eConnect User Guide Document Information Document Version: Version 1.6 As of: March 31, 2004 Classification: Proprietary Release Date: March 31, 2004 Document ID: eConnectUserGuide.doc ABOUT THIS USER GUIDE This document describes how to install and configure eConnect on handheld terminals with Microsoft® Windows® Pocket PC 2002, Windows Mobile™ 2003 for Pocket PC, and Microsoft® Windows® CE .NET platforms. For specific information on setting up and using connections, refer to the documentation for your terminal. REVISION HISTORY Document Identifier Date Description eConnectUserManual.doc 5/15/2001 Original eConnectUG.doc 10/19/2001 Initial Release, Version 1.0 eConnectUserManual.doc 6/20/2002 Version 1.1 eConnectUserManual.doc 4/03/2003 Version 1.2 eConnectUserGuide.doc 9/23/2003 Version 1.3 eConnectUserGuide.doc 12/8/2003 Version 1.4 eConnectUserGuide.doc 2/6/2004 Version 1.5 eConnectUserGuide.doc 3/2/2004 Version 1.6 NEW IN THIS VERSION • Version 1.6 – Figure 8 updated to show version 3.2.1 display. Small typographical errors corrected. • Version 1.5 - Revised download URL and procedure. • Version 1.4 – Configuration instructions updated. • Version 1.3 – User Guide revised and updated. Version 1.6, 3/31/2004 InVision Software, Inc. - Proprietary i eConnect User Guide Notice Copyright © 2004 InVision Software, Inc. All rights reserved. All rights reserved. This document in full or in part may not be copied, photocopied, reproduced, translated, or reduced to any electronic medium or machine-readable form without the prior written consent of InVision Software, Inc. -
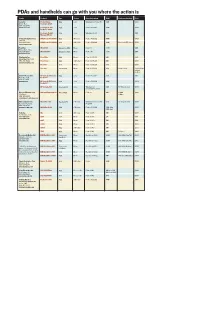
Pdas and Handhelds Can Go with You Where the Action Is
PDAs and handhelds can go with you where the action is Vendor Producct Type Screen Operating system RAM Built-in networking Price Casio Inc. Product Name PDA Color Windows for Pocket PC 32M $299 Dover, N.J. Cassiopeia E-125 888-932-2746 www.casio.com Cassiopeia E-200 PDA Color Pocket PC 2002 64M $599 Pocket PC 2002 Cassiopeia Pocket PDA Color Windows CE 3.0 16M $199 Manager BE-300 Compaq Computer Corp. iPAQ Pocket PC H3760 PDA 4K color Pocket PC 2002 64M $499 Houston 800-888-0220 iPAQ Pocket PC H3850 PDA 64K color Pocket PC 2002 64M Bluetooth $50 extra $599 www.compaq.com Fossil Inc. Wrist PDA Wristwatch PDA Mono Palm OS 190K $145 Richardson, Texas 972-234-2525 Wrist PDA/PC Wristwatch PDA Mono Pocket PC 190K $145 www.fossil.com Handspring Inc. Visor Edge PDA Mono Palm OS 3.5.2H 8M $249 Mountain View, Calif. 650-230-5000 Visor Prism PDA 64K color Palm OS 3.5.2H1 8M $299 www.handspring.com Visor Pro PDA Mono Palm OS 3.5.2H1 16M $249 Treo 180 Phone/PDA Mono Palm OS 3.5.2H 16M GSM cellular $399 ($549 without service) Hewlett-Packard Co. HP Jornada 547 Color PDA Color Pocket PC 2002 32M $416 Palo Alto, Calif. Pocket PC 650-857-1501 www.hp.com HP Jornada 567 Color PDA Color Pocket PC 2002 64M $608 Pocket PC HP Jornada 720 Handheld PC Color Windows for 32M 56-Kbps modem $899 Hand-held PC 2000 Kyocera Wireless Corp. QCP 6035 Smartphone Phone/PDA Mono Palm OS 8M CDMA $400 San Diego cellular 858-882-2000 www.kyocera-wireless.com NEC Computers Inc. -

A620 Pocket PC Microsoft MS Activesync Windows Microsoft Intel Intel
A620 Pocket PC Microsoft MS ActiveSync Windows Microsoft Intel Intel ©2003 Mypal A620 V1 T1249 2003 4 2 ASUSTeK COMPUTER INC.( ) 150 886-2-2894-3447 [email protected] 0800-093-456 AM 9:00 PM 9:00 AM 9:00 PM 6:00 [email protected] www.asus.com.tw ASUS COMPUTER INTERNATIONAL ( ) 44370 Nobel Drive, Fremont ,CA 94538, USA +1-510-608-4555 [email protected] ASUS Technology Service Inc. +1-502-995-0883 +1-502-933-8713 [email protected] 7100 Intermodal Dr.Suite - A Louisville Ky,40258 USA ASUS Holland BV. ( ) +31-(0)591-668190 ... +31-(0)591-666852 [email protected] [email protected] [email protected] [email protected] www.asus.com.tw FTP ftp.asus.com.tw/pub/ASUS MyPal A620 Pocket PC 3 1. ( http://www.asus.com.tw/register.htm) 2. - http://www.asus.com.tw/register. htm 1. " " ( ) 2. 0800-093-456 Flash ROM A620T---------- IIIIIIIIIIIIIIIIIIIIIIIII xxAPxxxxxx---------------- 4 1. 2. 3. (1) (2) (3) LCD LCD 1. 2. 3. 4. 5. 6. 7. 8. 9. 1. 0800-093-456 2. 48 48 3. 0800-093- 456 4. 5. !!! MyPal A620 Pocket PC 5 MyPal A620 6 0 30 45 113 20~30 - - - MyPal A620 Pocket PC 7 ...................................................................... 2 ...................................................................... 3 .................................................................. 4 .......................................................................... 6 1 ...................................... 13 1.1 .................................................................. 15 1.2 ......................................................................... 16 1.2.1 MyPal -

Compaq Ipaq Pocket PC H3950
iPAQ Pocket PC H3950 » Product » Model Information Specification The most expandable Pocket PC is now brighter and even more versatile. The iPAQ Pocket PC H3950 has the same sleek, elegant design as the H3800 series without compromising size, and offers more versatility and functionality for your business or personal entertainment. The dazzling transflective display offers higher contrast, and better colour saturation. The iPAQ H3950 features the fastest processor available, the 400MHz Intel® X-Scale processor, which focuses on accelerating multimedia and security. Other features include an integrated universal remote control, image viewer with slide show, up to 18 hours battery life and secure digital expansion slot for future SDIO options. Compaq iPAQ H3950 features: Benefits Fastest processor available: Runs applications quickly Intel® 400MHz X-Scale without any delays. Improved security and multimedia capabilities Increased battery life: 50% improvement over H3800 series More battery life to keep you more productive Integrated SD Slot: SDIO Ready Expand your memory capacity without increasing the size or weight of the Ultrabright transflective TFT screen iPAQ. SDIO ready for future SDIO with 65K colours products for more functionality Microsoft® Pocket PC 2002 Easy to read screen even in daylight and operating system high contrast ratios 64MB RAM Memory 32MB ROM Memory Large memory for applications, with 5.9MB iPAQ File Store files, music, photos and more USB + Serial connector iPAQ file store protects critical data in non-volatile storage area to protect data A great number of options available No matter what operating system you have, you will be able to connect to your PC Amazing flexibility and functionality to maximise your investment. -

Mobile Device Survery
Mobile Device Surveyrvey DRAFT NIST Interagency Report June 2002 Tom Karygiannis Wayne Jansen Vlad Korolev Serban Gavrila 1 Table of Contents 1. Introduction ........................................................................................................... 1 2. PDA Platform Families ......................................................................................... 1 2.1 Palm PDA........................................................................................................ 2 2.2 Pocket PC........................................................................................................ 3 2.3 Linux PDA ...................................................................................................... 4 3. Development Tools ................................................................................................ 8 3.1 Palm OS Development Tools........................................................................... 8 3.2 Pocket PC Development Tools......................................................................... 8 3.3 Linux PDA Development Tools....................................................................... 9 4. Commercial Security Solutions........................................................................... 11 4.1 Palm OS Security Mechanisms ...................................................................... 11 4.2 Pocket PC Security Mechanisms.................................................................... 15 4.3 Linux PDA Security Mechanisms .................................................................