Commonwealth of Kentucky
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

NASACT News | September 2015 1 a MESSAGE from NASACT’S PRESIDENT Continued from Previous Page
KEEPING STATE FISCAL OFFICIALS INFORMED VOLUME 35, NUMBER 9 | SEPTEMBER 2015 LOOKING TO THE FUTURE: NEXT STEPS FOR NASACT BY CALVIN McKELVOGUE, PRESIDENT OF NASACT, 2015-16 As NASACT turns a corner into its next century, it Th is year, NASACT will review the strategic plan is exciting to look forward at the many roads leading and establish goals for the future. One important to our future, each carved out by our innovative and item the Strategic Planning Committee will be diverse past presidents and members. Remembering charged with is to determine how NASACT will our past and the legacy it provides is also something maintain the sustainability of travel assistance to refl ect and build upon. Since Woodrow Wilson was for our members. Th e travel assistance allows President of the United States, NASACT members principals, who may not otherwise be able, to attend have been infl uencing states and their decision our conferences, which is a huge benefi t to both makers. NASACT would not be what it is today NASACT and our members. without their guidance and forethought, and without Th e middle management conference is an event I doubt, the continued excellence of the NASACT staff . fully support and believe is an excellent opportunity As we move forward, it is important to continue the for future leaders to network with individuals from momentum in planning for the next 100 years. other states, allowing for the exchange of knowledge I would like to off er a big Th ank You! to the hosts and activities within diff erent governments. -

2011 Interim Record
2011 Interim LEGISLATIVE Volume 24, No. 9 December 2011 * Read on-line at www.lrc.ky.gov/legislation.htm* RECORD Vic Hellard Jr. Charles Siler named 2011 Award past winners by ScottHellard Payton Award recipient 2010 LRC Public Information Peggy Hyland Former State Rep. Charles Siler, who served two notable stints in the Kentucky General Assembly 2009 before saying farewell in 2010 as one of Frankfort’s Congressman Romano Mazzoli most respected lawmakers, has been named recipient of the 2011 Vic Hellard Jr. Award for excellence in 200 public service. Sally Brown The Hellard Award, the highest honor the Legislature can bestow, has been given annually 200 since 1997. Siler -- known to all simply as Charlie - - was chosen for this year’s honor by the 16-member John R. Hall legislative leadership that comprises the Legislative Research Commission. 200 The award’s namesake, Vic Hellard Jr., was Sylvia L. Lovely executive director of the LRC staff for 19 years. The 200 Siler was known honor goes each year to William H. Hintze someone who embodies the as a ‘quietly values Hellard brought to his long career: A public servant 200 passionate voice’ of vision, who appreciates Robert M. “Mike” Duncan for his House history while fi nding innovative approaches to 2003 district and hard problems, someone Walter A. Baker who champions the all of Kentucky. equality and dignity of all, 2002 nurtures the processes of a democratic society, and the Legislature was an expression of his citizenship, Virginia G. Fox promotes public dialogue yet another civic duty he undertook, not a career.’ while educating and fostering civic engagement, and Williams recalled Siler’s ‘good heart and good 2001 who approaches that work with commitment, caring, humor,’ and added: ‘Charlie had a way of helping Thomas D. -

TABLE 4.27 State Auditors: 2019
AUDITORS AND COMPTROLLERS TABLE 4.27 State Auditors: 2019 Legal Method Maximum State or other basis for of U.S. State consecutive jurisdiction State Agency Agency head Title office selection Term of office citizen resident terms allowed Department of Examiners of Alabama Rachel Riddle Chief Examiner S LC 7 yrs. « … None Public Accounts Alaska Division of Legislative Audit Kris Curtis Legislative Auditor C, S L (a) … … None Arizona Office of the Auditor General Lindsey Perry Auditor General S LC 5 yrs. … … None Arkansas Division of Legislative Audit Roger A. Norman Legislative Auditor S LC Indefinite « « None California Bureau of State Audits Elaine M. Howle State Auditor S G 4 yrs. « … None Colorado Office of the State Auditor Dianne E. Ray State Auditor C,S LC 5 yrs. … … None Office of the Auditors of John C. Geragosian and Connecticut State Auditors S L 4 yrs. … … None Public Accounts Robert Kane Office of the Auditor Delaware Kathleen McGuiness Auditor of Accounts C, S E 4 yrs. « « None of Accounts Florida Office of the Auditor General Sherrill F. Norman Auditor General C, S L (a) … … None Department of Audits Georgia Greg S. Griffin State Auditor S L Indefinite … … None and Accounts Hawaii Office of the Auditor Les Kondo State Auditor C L 8 yrs. … « None Legislative Services Office— Idaho April J. Renfro Division Manager S LC (b) … … None Legislative Audits Illinois Office of the Auditor General Frank Mautino Auditor General C, S L 10 yrs. … … None Indiana State Board of Accounts Paul D. Joyce State Examiner S GLC 4 yrs. … … None Iowa Office of the Auditor of State Rob Sand Auditor of State C, S E 4 yrs. -

Alabama Alaska Arizona Arkansas California Colorado Connecticut
This list is a comprehensive list of state legislators who are members of ALEC (American Legislative Exchange Council). There are 1192 Republicans, 61 Democrats, 11 Non-Partisans (NE) members. There have been 45 members who have left ALEC in the last month; 11 Republicans, 32 Democrats, 2 Non-Partisans (NE) (Corporate Campaign). There have been 108 ALEC Legislators who have either lost or given up their seats. These are the people who are carrying out the extreme right -wing agenda in the states. They go to all expense paid ALEC meetings where they get treated to lavish accommodations, meals and entertainment for the small price of destroying our democracy. They target minorities, workers, women and democratically elected city and school board members. They push privatization as the answer when it has been proven that it is less efficient and more costly. The Kochs were funding the reintroduction of segregation into a school district in NC. Alabama Louisiana Ohio Alaska Maine Oklahoma Arizona Maryland Oregon Arkansas Massachusetts Pennsylvania California Michigan Rhode_Island Colorado Minnesota South_Carolina Connecticut Mississippi South_Dakota Delaware Missouri Tennessee Florida Montana Texas Georgia Nebraska Utah Hawaii Nevada Vermont Idaho New_Hampshire Virginia Illinois New_Jersey Washington Indiana New_Mexico West_Virginia Iowa New_York Wisconsin Kansas North_Carolina Wyoming Kentucky North_Dakota Alabama ALEC Legislators Rep. Karen Fann (R-1) Pres.P.Tem.S.Tenney Allen (R-5) House of Representatives Rep. Eddie Farnsworth (R-22) Rep. Richard Miranda (D-13) Rep. Jim Carns (R-48) Rep. John Fillmore (R-23) Former ALEC Legislators Rep. Victor Gaston (R-100) Rep. Thomas Forese (R-21) Sen. Russell Pearce Rep. -

Table 4.27 the STATE AUDITORS, 2016
AUDITORS AND COMPTROLLERS Table 4.27 THE STATE AUDITORS, 2016 Legal Maximum State or other basis Method of U.S. State consecutive jurisdiction State agency Agency head Title for office selection Term of office citizen resident terms allowed Alabama ............................. Department of Examiners Ronald L. Jones Chief Examiner S LC 7 yrs. « . None of Public Accounts Alaska ................................. Division of Legislative Audit Kris Curtis Legislative Auditor C, S L (a) . None Arizona ............................... Office of the Auditor General Debra K. Davenport Auditor General S LC 5 yrs. None Arkansas ............................ Division of Legislative Audit Roger A. Norman Legislative Auditor S LC Indefinite « « None California ........................... Bureau of State Audits Elaine M. Howle State Auditor S G 4 yrs. « . None Colorado ............................. Office of the State Auditor Dianne E. Ray State Auditor C,S LC 5 yrs. None Connecticut ........................ Office of the Auditors of John C. Geragosian State Auditors S L 4 yrs. None Public Accounts and Robert M. Ward Delaware ............................ Office of the Auditor of Accounts R.Thomas Wagner, Jr. Auditor of Accounts C, S E 4 yrs. « « None Florida ................................ Office of the Auditor General Sherrill F. Norman Auditor General C, S L (a) . None Georgia ............................... Department of Audits and Accounts Greg S. Griffin State Auditor S L Indefinite . None Hawaii................................. Office of the Auditor Jan K. Yamane State Auditor C L 8 yrs. « None Idaho ................................... Legislative Services Office— April J. Renfro Division Manager S LC (b) . None Legislative Audits Illinois ................................. Office of the Auditor General Frank Mautino Auditor General C, S L 10 yrs. None Indiana ................................ State Board of Accounts Paul D. Joyce State Examiner S GLC 4 yrs. -

NASACT News, December 2015
KEEPING STATE FISCAL OFFICIALS INFORMED VOLUME 35, NUMBER 12 | DECEMBER 2015 NASACT 2015 A YEAR IN REVIEW NASACT has focused on a number of major is substantially the same as fair value. Th e criteria initiatives in 2015. Each of these topics has been would only relate to fi nancial reporting. covered in past newsletters, business and committee In June, GASB issued an exposure draft , Accounting meetings, and email updates this year. and Financial Reporting for Certain External AMENDMENTS TO RULE 2a-7 Investment Pools, to revise the guidance on LGIPs. Th e ED only allowed a change in accounting policy to NASACT and the National Association of State amortized cost at the time of implementation when a Treasurers created a work group last fall to examine fi nal statement is issued. the the U.S. Securities and Exchange Commission’s amendments to Rule 2a-7 impacting money market NASACT replied to the ED at the end of August, mutual funds (MMFs). Among other things, the generally agreeing with the provisions of the ED amendments will require institutional prime MMFs but urging the Board to reconsider and remove the to adopt a fl oating net asset value (NAV) instead restriction on the ability for LGIPs to make justifi able of the traditional stable NAV. Th e work group has changes between acceptable accounting principles in primarily focused on the impact the amendments the future. A fi nal pronouncement is expected at the will have on local government investment pools end of December. (LGIPs), which in many cases are operated by state PENSION STANDARDS AND AUDIT GUIDANCE governments. -

ADVOCACY 101 2019 Election Results 2020 KY State House Of
12/3/2019 ADVOCACY 101 Robbin Morrison Taylor McCarthy Strategic Solutions, LLC November 15, 2019 1 2019 Election Results Governor/Lt. Governor…..Andy Beshear Jacqueline Coleman Secretary of State…..Michael Adams Attorney General…..Daniel Cameron Auditor…..Mike Harmon State Treasurer…..Allison Ball Comm. of Agriculture…..Ryan Quarles 2 2020 KY State House of Representatives Current Makeup 61 Republicans 39 Democrats KY State House terms are two years and elections are held in the even-number years. Of the 100 seats in the House, there were 32 new faces on January 8, 2019. 2 Special Elections on November 5 did not change party makeup. 3 1 12/3/2019 2020 KY State Senate Current Makeup • 29 Republicans • 9 Democrats Senate terms are four years in Kentucky. Half of the 38 seats were on the ballot last November. Of the 19 seats that were up last year, only two were unopposed. Two new members were elected. Both were Republican House members (Mills & Castlen). Phillip Wheeler elected in March special election – GOP pick-up. 4 5 THIS IS NOT ROCKET SCIENCE 6 2 12/3/2019 IT’S ALL ABOUT… • BUILDING STRONG RELATIONSHIPS • BUILDING STRONG COALITIONS – POWER IN NUMBERS, NATURAL CONSTITUENCIES, GRASS ROOTS • COMPROMISE 7 RULES OF ENGAGEMENT • BE HONEST • BE POLITE • BE POSITIVE BUT PERSISTENT • UNDERSTAND AND EXPLAIN BOTH SIDES • NO SURPRISES • SAY THANK YOU 8 IT’S ALL ABOUT RELATIONSHIPS! Work to build important relationships now – before you need them! 9 3 12/3/2019 LEGISLATIVE PROCESS 10 PROCESS • IDENTIFY YOUR ISSUE • PUT TOGETHER A COALITION • -
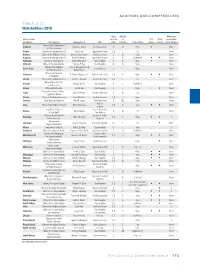
TABLE 4.27 State Auditors, 2018
AUDITORS AND COMPTROLLERS TABLE 4.27 State Auditors, 2018 Legal Method Maximum State or other basis for of U.S. State consecutive jurisdiction State Agency Agency head Title office selection Term of office citizen resident terms allowed Department of Examiners Alabama Ronald L. Jones Chief Examiner S LC 7 yrs. « … None of Public Accounts Alaska Division of Legislative Audit Kris Curtis Legislative Auditor C, S L (a) … … None Arizona Office of the Auditor General Debra K. Davenport Auditor General S LC 5 yrs. … … None Arkansas Division of Legislative Audit Roger A. Norman Legislative Auditor S LC Indefinite « « None California Bureau of State Audits Elaine M. Howle State Auditor S G 4 yrs. « … None Colorado Office of the State Auditor Dianne E. Ray State Auditor C,S LC 5 yrs. … … None Office of the Auditors John C. Geragosian and Connecticut State Auditors S L 4 yrs. … … None of Public Accounts Robert Kane Office of the Auditor Delaware R. Thomas Wagner, Jr. Auditor of Accounts C, S E 4 yrs. « « None of Accounts Florida Office of the Auditor General Sherrill F. Norman Auditor General C, S L (a) … … None Department of Audits Georgia Greg S. Griffin State Auditor S L Indefinite … … None and Accounts Hawaii Office of the Auditor Les Kondo State Auditor C L 8 yrs. … « None Legislative Services Office— Idaho April J. Renfro Division Manager S LC (b) … … None Legislative Audits Illinois Office of the Auditor General Frank Mautino Auditor General C, S L 10 yrs. … … None Indiana State Board of Accounts Paul D. Joyce State Examiner S GLC 4 yrs. -

NEWS DEC 11.Indd
A QUARTERLY PUBLICATION Kentucky Retired Teachers Association Serving Retired Teachers Since 1957 VOLUME XLVI, NUMBER 2 LOUISVILLE, KENTUCKY DECEMBER 2011 Beginning on August 26, 2011, in Jeff erson County, the KRTA traveling team visited all 14 districts presenting topics that are vital to all teacher retirees. Fall Workshops 2011 Eastern District was the site of the last workshop on September 23, 2011. President Cook’s theme for this year, as well as the Fall Workshops, focuses on the importance of volunteering. Membership is certainly the lifeblood of the organization. Our numbers send out a message to legislators that the objectives of KRTA are strongly supported. Th e individuals who step forward and accept the leadership positions at the state, district and local levels are volunteers drawn from our continually growing membership. Volunteers step up each year to accept program challenges established by their local and civic organizations. How many historical societies, Meals on Edwin S. Cook, III Wheels, sesquicentennial committees, Relay for Life groups, Neighborhood KRTA President Watch groups, Boy Scout Troops, Cub Scout Troops, Girl Scout Troops, Sunday School classes, Church choirs, to name a few, would be non-existent without our volunteers? One of President Cook’s eff orts is to educate KRTA members of the importance of the N. O. Kimbler Scholarship Fund. N. O. Kimbler was born in Greenup County, Kentucky. He started teaching in 1912 in a two-room country school and rose to become State President of KEA in 1938. He saw the great need for Kentucky teachers to be rewarded in their retirement years for the meager salaries they received and devoted his life to bringing the Kentucky Teachers’ Retirement System to fruition.