Deploy:Manage OS X Edited-JCS-Jwajc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Getting Started on a Mac with Macgamut Download
Getting started on a Macintosh computer with MacGAMUT 6 (Download) These step-by-step instructions will get you started on any Macintosh OS X computer, when you make a Download purchase of MacGAMUT 6 from the MacGAMUT website. Getting started with MacGAMUT 6 is EASY, but it's still a good idea to follow these printed instructions as you proceed step by step, marking off each step as you complete it. Follow these steps to install MacGAMUT 6 as a download: 1. First, download and install the MacGAMUT 6 software. Yes, you can complete the download and installation even before you make your online purchase. You just won’t be able to use the installed program until you’ve paid for it! a. From the Home page at www.macgamut.com, follow the links from the Installers link on the left-hand side of the screen to go to the MacGAMUT Web Installers page. b. Read the “How-to” Videos paragraph before scrolling down to click the appropriate installer for your computer and system. c. You’ll find the downloaded Installer in your Macintosh’s Downloads folder. (If you are not working on your own computer, you can copy the Installer to a flash drive so you can install it later on your computer.) d. The Installer will start automatically when you open the Installer package. Just follow the instructions to complete your installation. e. If you are installing MacGAMUT 6 for the first time, you will need to restart your computer after the installation process is finished. f. The program installs in a folder labeled MacGAMUT 6 in your computer’s Applications folder. -

How to Set up IP Camera by Using a Macintosh Computer
EDIMAX COMPUTER INC. Edimax IP Camera series How to set up IP Camera by using a Macintosh computer 2011 Edimax Computer 3350 Scott Blvd., Building #15 Santa Clara, California 95054, USA Phone 408-496-1105 • Fax 408-980-1530 www.edimax.us How to setup Edimax IP Camera by a Macintosh computer Introduction The most important thing to setup IP Camera is to assign a static IP address so the camera can work with your network. So far the Edimax IP Cam Admin utility is Windows based only and the program can not work for Macintosh computers. Macintosh users can follow this guide to set up Edimax IP camera. Step 1. Understand the IP address used in your network. Have your Macintosh computer operate as usual. Go into System Preferences. In System Preferences, Go to Network. Select the adapter you are using. It could be an Airport card, a third- party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We have a usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses used in the network are 10.0.1.x. All the devices in the network have the first three octets the same, but the last octet number must be different. We decide to give our new camera an IP address 10.0.1.100 because no other computer device use 10.0.1.100. We temporarily disconnect the wireless adapter. You can turn off your Airport adapter if you use it to get on Internet. -

Initial Setup of Your IOS Device
1. When you first turn on your iOS device, you'll see a screen displaying Hello in different languages. Slide from left to right anywhere on this screen. 2. Select the language you want your iOS device to use, and then the region in which you'll be using your iOS device. This will affect things such as date, time, and contact formatting. 3. Your iOS device requires an Internet connection to set up. Tap the name of your desired Wi-Fi network to begin device activation. § If you're activating an iPhone or iPad (Wi-Fi + Cellular) with active cellular service, you can instead choose cellular activation. 4. Choose whether to enable Location Services. 5. Set up your iPhone as a new device, from an iCloud backup, or from an iTunes backup. § If restoring from backup, you can learn how to restore your content. 6. Sign in with your Apple ID, which you've created previously, or create a free Apple ID. § Alternatively, you can tap Skip This Step to sign in or create an Apple ID later. § If necessary, learn how to create a free Apple ID: 1. Select your birthday, then tap Next: 2. Enter your first and last name, then tap Next: 3. You can then use either your current email address, or choose to get a free iCloud email address. Select the option you'd like, then tap Next. 4. Enter your current email address, or what you'd like for your iCloud email, then tap Next. 5. Enter what you'd like for your password and tap Next. -

Don't Pay with Itunes Gift Card Consumer Alert
DON’T PAY WITH iTUNES GIFT CARDS Consumer Alert In the news: SPOT IT: You are asked to pay with iTunes Demands for you to pay right away Someone calls instilling panic and urgency—your for taxes, hospital or utility bills, grandchild is going to jail; you will be arrested for bail money, or to settle a debt are past due taxes; or your utilities will be turned off common. Criminals make up all in hours—unless you immediately buy iTunes gift kinds of reasons for why you owe cards then share the 16-digit code with the caller urbanbuzz Shutterstock.com money. The goal is the same: to to make your payment. steal from you. You apply for a loan and to prove your credit Con artists using this ploy will ask for an untraceable worthiness, you are asked for an advance fee to form of payment, like wiring money, sending cash, or a be paid right away with iTunes gift cards. pre-loaded money or gift card. The iTunes gift card is the payment method of choice right now for many criminals. A caller tells you that an iTunes gift card is the way you use Apple Pay. What you need to know: When someone catches you off guard and hits your panic button, it is hard to think straight. Criminals know STOP IT: Don’t pay anyone with a gift card this, and hope you will focus on the worse-case scenario they are painting and not on your common sense. If you’re not shopping at the iTunes store, you should not be paying with an iTunes gift card. -

Filenet Image Services Installation and Configuration Procedures
IBM FileNet Image Services 4.1.2 Installation and Configuration Procedures SC19-2680-01 IBM FileNet Image Services 4.1.2 Installation and Configuration Procedures SC19-2680-01 Note Before using this information and the product it supports, read the information in .“Notices” on page 273 This edition applies to version 4.1.2 of IBM FileNet Image Services (product number 5724-R95) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 1984, 2008. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Table of Contents About this document. 15 Revision Log . 15 Typographical Conventions. 16 Accessing IBM FileNet documentation . 16 Feedback . 17 Documentation feedback . 17 Product consumability feedback. 17 Installation Checklists and Required Skills. 18 Installation Checklist for AIX Servers . 18 Installation Checklist for HP-UX Servers. 20 Installation Checklist for Solaris Servers. 21 Installation Checklist for Windows Servers. 22 Required Skills . 23 Installation Planning Considerations. 24 Hardware Requirements . 24 Server Memory . 24 Total Swap Space . 24 Total Disk Space . 25 Multicultural support . 25 Additional Requirements for AIX . 26 Additional Requirements for HP-UX . 26 Additional Requirements for Solaris . 28 Additional Requirements for Windows Server . 28 Software Requirements. 29 Server Naming Convention . 29 Object Name . 29 Domain Name . 29 Organization Name . 29 Image Services software image . 29 RDBMS software . 30 IBM DB2 RDBMS Software . 30 Oracle RDBMS Software (FileNet-controlled) . 30 Oracle RDBMS Software (Site-controlled) . 30 MS-SQL RDBMS Software . 30 Debugging Software . 30 Debugger - AIX . 30 Debugger - HP-UX . -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Apple Business Manager Overview Overview
Getting Started Guide Apple Business Manager Overview Overview Contents Apple Business Manager is a web-based portal for IT administrators to deploy Overview iPhone, iPad, iPod touch, Apple TV, and Mac all from one place. Working Getting Started seamlessly with your mobile device management (MDM) solution, Apple Configuration Resources Business Manager makes it easy to automate device deployment, purchase apps and distribute content, and create Managed Apple IDs for employees. The Device Enrollment Program (DEP) and the Volume Purchase Program (VPP) are now completely integrated into Apple Business Manager, so organizations can bring together everything needed to deploy Apple devices. These programs will no longer be available starting December 1, 2019. Devices Apple Business Manager enables automated device enrollment, giving organizations a fast, streamlined way to deploy corporate-owned Apple devices and enroll in MDM without having to physically touch or prepare each device. • Simplify the setup process for users by streamlining steps in Setup Assistant, ensuring that employees receive the right configurations immediately upon activation. IT teams can now further customize this experience by providing consent text, corporate branding or modern authentication to employees. • Enable a higher level of control for corporate-owned devices by using supervision, which provides additional device management controls that are not available for other deployment models, including non-removable MDM. • More easily manage default MDM servers by setting a default server that’s based on device type. And you can now manually enroll iPhone, iPad, and Apple TV using Apple Configurator 2, regardless of how you acquired them. Content Apple Business Manager enables organizations to easily buy content in volume. -

Well Known TCP and UDP Ports Used by Apple Software Products
Well known TCP and UDP ports used by Apple Languages English software products Symptoms Learn more about TCP and UDP ports used by Apple products, such as OS X, OS X Server, Apple Remote Desktop, and iCloud. Many of these are referred to as "well known" industry standard ports. Resolution About this table The Service or Protocol Name column lists services registered with the Internet Assigned Numbers Authority (http://www.iana.org/), except where noted as "unregistered use." The names of Apple products that use these services or protocols appear in the Used By/Additional Information column. The RFC column lists the number of the Request For Comment document that defines the particular service or protocol, which may be used for reference. RFC documents are maintained by RFC Editor (http://www.rfc- editor.org/). If multiple RFCs define a protocol, there may only be one listed here. This article is updated periodically and contains information that is available at time of publication. This document is intended as a quick reference and should not be regarded as comprehensive. Apple products listed in the table are the most commonly used examples, not a comprehensive list. For more information, review the Notes below the table. Tip: Some services may use two or more ports. It is recommend that once you've found an instance of a product in this list, search on the name (Command-F) and then repeat (Command-G) to locate all occurrences of the product. For example, VPN service may use up to four diferent ports: 500, 1701, 1723, and 4500. -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -
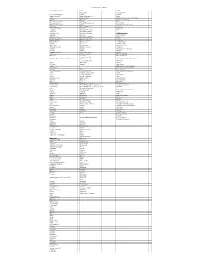
Software List (1-3-2017)
Software List (1-3-2017) Information Commons BU 104 LLCD Adobe Flash Academic online JVC Pro HD Manager Chrome Acrobat Adobe Reader DC Adobe Photoshop CS6 Adobe Itunes Adobe Reader XI Comprehensive Medical Terminology Maple 16 Drive M:\ Glencoe Keyboarding Microsoft Office 2016 Firefox Itunes Microsoft Publisher Irwin/GDP Keyboarding Kurzeil 3000 MS visual studio 2015 Itunes Microsoft Office Suite 2007 Quicktime Kurzweil 3000 v.12 Quick time SPSS for Windows Maple 16 Skills bank real player Microsoft Office 2016 Vista 3-Scanners MS platform installer Windows 7 & 10 Microsoft Visio 2016 Wellington Center sharepoint MS SQL Internet Explorer XPS viewer MS Visual Studio 2015 ITunes Express for desktop Quicken deluxe 2014 McAfee Express for Web VLC Media Player Quicktime MS silverlight Windows 10 " " Media Player Statdisk Scanner Mozilla Firefox Skype 2016 MS silverlight Adobe Reader XI windows dvd maker wolfram cdf player Windows 8 Onedrive Filezilla Microsoft Office Suite 2013 notepad++ Gimp 2 Maple 16 respounds/lockdown opera mobile emulator Statdisk 3D builder VM ware/ vsphere Wolfram CDF Player MS Azure wire shark VLC Media Player cisco packet tracker MACS Software (Information Commons) 3D builder Brunswick Front Desk Computers java development kit Windows 7 System project 2016 Adobe 9 Developer notepad++ Apple Itunes Utilities IBM Iseries access for windows Time Machine Intel Management and Security TextEdit UC 222 Iseries navigator System Preferences Acrobat Reader XI Malware Bytes Anti Malware Stickies Adult Clinical Simulation Mcaffe -

Network Boot and Exotic Root HOWTO
Network Boot and Exotic Root HOWTO Brieuc Jeunhomme frtest [email protected] Logilab S.A. Revision History Revision 0.3 2002−04−28 Revised by: bej Many feedback inclusions, added links to several projects Revision 0.2.2 2001−12−08 Revised by: dcm Licensed GFDL Revision 0.2.1 2001−05−21 Revised by: logilab Fixed bibliography and artheader Revision 0.2 2001−05−19 Revised by: bej Many improvements and included Ken Yap's feedback. Revision 0.1.1 2001−04−09 Revised by: logilab First public draft. Revision 0.1 2000−12−09 Revised by: bej Initial draft. This document explains how to quickly setup a linux server to provide what diskless linux clients require to get up and running, using an IP network. It includes data and partly rewritten text from the Diskless−HOWTO, the Diskless−root−NFS−HOWTO, the linux kernel documentation, the etherboot project's documentation, the linux terminal server project's homepage, and the author's personal experience, acquired when working for Logilab. Eventually this document may end up deprecating the Diskless−HOWTO and Diskless−root−NFS−HOWTO. Please note that you'll also find useful information in the From−PowerUp−to−bash−prompt−HOWTO and the Thin−Client−HOWTO, and the Claus−Justus Heine's page about NFS swapping. Network Boot and Exotic Root HOWTO Table of Contents 1. Introduction.....................................................................................................................................................1 1.1. What is this all about?.......................................................................................................................1 1.2. Thanks...............................................................................................................................................1 1.3. Diskless booting advocacy................................................................................................................1 1.3.1. Buying is cheaper than building.......................................................................................1 1.3.2.