IDOL Keyview Filter SDK 12.8 C++ Programming Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Differential Fuzzing the Webassembly
Master’s Programme in Security and Cloud Computing Differential Fuzzing the WebAssembly Master’s Thesis Gilang Mentari Hamidy MASTER’S THESIS Aalto University - EURECOM MASTER’STHESIS 2020 Differential Fuzzing the WebAssembly Fuzzing Différentiel le WebAssembly Gilang Mentari Hamidy This thesis is a public document and does not contain any confidential information. Cette thèse est un document public et ne contient aucun information confidentielle. Thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Technology. Antibes, 27 July 2020 Supervisor: Prof. Davide Balzarotti, EURECOM Co-Supervisor: Prof. Jan-Erik Ekberg, Aalto University Copyright © 2020 Gilang Mentari Hamidy Aalto University - School of Science EURECOM Master’s Programme in Security and Cloud Computing Abstract Author Gilang Mentari Hamidy Title Differential Fuzzing the WebAssembly School School of Science Degree programme Master of Science Major Security and Cloud Computing (SECCLO) Code SCI3084 Supervisor Prof. Davide Balzarotti, EURECOM Prof. Jan-Erik Ekberg, Aalto University Level Master’s thesis Date 27 July 2020 Pages 133 Language English Abstract WebAssembly, colloquially known as Wasm, is a specification for an intermediate representation that is suitable for the web environment, particularly in the client-side. It provides a machine abstraction and hardware-agnostic instruction sets, where a high-level programming language can target the compilation to the Wasm instead of specific hardware architecture. The JavaScript engine implements the Wasm specification and recompiles the Wasm instruction to the target machine instruction where the program is executed. Technically, Wasm is similar to a popular virtual machine bytecode, such as Java Virtual Machine (JVM) or Microsoft Intermediate Language (MSIL). -

Why ODF?” - the Importance of Opendocument Format for Governments
“Why ODF?” - The Importance of OpenDocument Format for Governments Documents are the life blood of modern governments and their citizens. Governments use documents to capture knowledge, store critical information, coordinate activities, measure results, and communicate across departments and with businesses and citizens. Increasingly documents are moving from paper to electronic form. To adapt to ever-changing technology and business processes, governments need assurance that they can access, retrieve and use critical records, now and in the future. OpenDocument Format (ODF) addresses these issues by standardizing file formats to give governments true control over their documents. Governments using applications that support ODF gain increased efficiencies, more flexibility and greater technology choice, leading to enhanced capability to communicate with and serve the public. ODF is the ISO Approved International Open Standard for File Formats ODF is the only open standard for office applications, and it is completely vendor neutral. Developed through a transparent, multi-vendor/multi-stakeholder process at OASIS (Organization for the Advancement of Structured Information Standards), it is an open, XML- based document file format for displaying, storing and editing office documents, such as spreadsheets, charts, and presentations. It is available for implementation and use free from any licensing, royalty payments, or other restrictions. In May 2006, it was approved unanimously as an International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) standard. Governments and Businesses are Embracing ODF The promotion and usage of ODF is growing rapidly, demonstrating the global need for control and choice in document applications. For example, many enlightened governments across the globe are making policy decisions to move to ODF. -
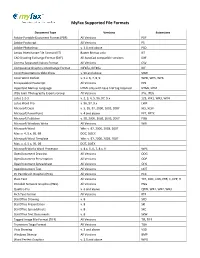
Supported File Types
MyFax Supported File Formats Document Type Versions Extensions Adobe Portable Document Format (PDF) All Versions PDF Adobe Postscript All Versions PS Adobe Photoshop v. 3.0 and above PSD Amiga Interchange File Format (IFF) Raster Bitmap only IFF CAD Drawing Exchange Format (DXF) All AutoCad compatible versions DXF Comma Separated Values Format All Versions CSV Compuserve Graphics Interchange Format GIF87a, GIF89a GIF Corel Presentations Slide Show v. 96 and above SHW Corel Word Perfect v. 5.x. 6, 7, 8, 9 WPD, WP5, WP6 Encapsulated Postscript All Versions EPS Hypertext Markup Language HTML only with base href tag required HTML, HTM JPEG Joint Photography Experts Group All Versions JPG, JPEG Lotus 1-2-3 v. 2, 3, 4, 5, 96, 97, 9.x 123, WK1, WK3, WK4 Lotus Word Pro v. 96, 97, 9.x LWP Microsoft Excel v. 5, 95, 97, 2000, 2003, 2007 XLS, XLSX Microsoft PowerPoint v. 4 and above PPT, PPTX Microsoft Publisher v. 98, 2000, 2002, 2003, 2007 PUB Microsoft Windows Write All Versions WRI Microsoft Word Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOC, DOCX Microsoft Word Template Win: v. 97, 2000, 2003, 2007 Mac: v. 4, 5.x, 95, 98 DOT, DOTX Microsoft Works Word Processor v. 4.x, 5, 6, 7, 8.x, 9 WPS OpenDocument Drawing All Versions ODG OpenDocument Presentation All Versions ODP OpenDocument Spreadsheet All Versions ODS OpenDocument Text All Versions ODT PC Paintbrush Graphics (PCX) All Versions PCX Plain Text All Versions TXT, DOC, LOG, ERR, C, CPP, H Portable Network Graphics (PNG) All Versions PNG Quattro Pro v. -

JETIR Research Journal
© 2018 JETIR October 2018, Volume 5, Issue 10 www.jetir.org (ISSN-2349-5162) QUALITATIVE COMPARISON OF KEY-VALUE BIG DATA DATABASES 1Ahmad Zia Atal, 2Anita Ganpati 1M.Tech Student, 2Professor, 1Department of computer Science, 1Himachal Pradesh University, Shimla, India Abstract: Companies are progressively looking to big data to convey valuable business insights that cannot be taken care by the traditional Relational Database Management System (RDBMS). As a result, a variety of big data databases options have developed. From past 30 years traditional Relational Database Management System (RDBMS) were being used in companies but now they are replaced by the big data. All big bata technologies are intended to conquer the limitations of RDBMS by enabling organizations to extract value from their data. In this paper, three key-value databases are discussed and compared on the basis of some general databases features and system performance features. Keywords: Big data, NoSQL, RDBMS, Riak, Redis, Hibari. I. INTRODUCTION Systems that are designed to store big data are often called NoSQL databases since they do not necessarily depend on the SQL query language used by RDBMS. NoSQL today is the term used to address the class of databases that do not follow Relational Database Management System (RDBMS) principles and are specifically designed to handle the speed and scale of the likes of Google, Facebook, Yahoo, Twitter and many more [1]. Many types of NoSQL database are designed for different use cases. The major categories of NoSQL databases consist of Key-Values store, Column family stores, Document databaseand graph database. Each of these technologies has their own benefits individually but generally Big data use cases are benefited by these technologies. -

04 ISC 228-TESIS.Pdf
UTN –FICA Análisis y Estudio de Tecnología Ruby on Rails con bases de datos Postgresql para Aplicaciones Web 2.0 UNIVERSIDAD TÉCNICA DEL NORTE Facultad de Ingeniería en Ciencias Aplicadas Carrera de Ingeniería en Sistemas Computacionales TESIS PREVIA OBTENCIÓN DEL TITULO DE INGENIERO EN SISTEMAS COMPUTACIONALES Tema: “Análisis y Estudio de Tecnología Ruby on Rails con bases de datos Postgres para Aplicaciones Web 2.0” Aplicativo: Implementación del Portal Web 2.0 para la Mancomunidad de la Cuenca del Río Mira AUTOR : CHRISTIAN FERNANDO REALPE ROSERO. DIRECTOR : ING. MARCO PUSDÁ. IBARRA – ECUADOR, 2012 Christian Fernando Realpe Rosero Implementación del Portal Web 2.0 para la Mancomunidad de la Cuenca del Río Mira Print to PDF without this message by purchasing novaPDF (http://www.novapdf.com/) UTN –FICA Análisis y Estudio de Tecnología Ruby on Rails con bases de datos Postgresql para Aplicaciones Web 2.0 Certifico: Que la Tesis previa a la obtención del título de Ingeniería en Sistemas Computacionales con el tema “Análisis y Estudio de Tecnología Ruby on Rails con bases de datos Postgres para Aplicaciones Web 2.0”con el aplicativo “Implementación del Portal Web 2.0 para la Mancomunidad de la Cuenca del Río Mira” ha sido desarrollada y terminada en su totalidad por el Sr. Christian Fernando Realpe Rosero con C.C. 100251109-3 bajo mi supervisión para lo cual firmo en constancia. Atentamente, Ing. Marco Pusdá DIRECTOR DE TESIS Christian Fernando Realpe Rosero Implementación del Portal Web 2.0 para la Mancomunidad de la Cuenca del Río Mira Print to PDF without this message by purchasing novaPDF (http://www.novapdf.com/) UTN –FICA Análisis y Estudio de Tecnología Ruby on Rails con bases de datos Postgresql para Aplicaciones Web 2.0 UNIVERSIDAD TÉCNICA DEL NORTE CESIÓN DE DERECHOS DE AUTOR DEL TRABAJO DE INVESTIGACIÓN A FAVOR DE LA UNIVERSIDAD TÉCNICA DEL NORTE Yo, CHRISTIAN FERNANDO REALPE ROSERO, con cedula de identidad Nro. -

Authentication in the Mesh with Webassembly
Authentication in the mesh with WebAssembly Sondre Halvorsen Master’s Thesis, Spring 2021 Thesis submitted for the degree of Master in Informatics: programming and system architecture 30 credits Department of Informatics Faculty of mathematics and natural sciences UNIVERSITY OF OSLO Spring 2021 © 2021 Sondre Halvorsen Master Thesis http://www.duo.uio.no/ Printed: Reprosentralen, University of Oslo Abstract At the start of the last decade Marc Andreessen stated in his now famous blog entry; ‘Software is eating the world’ [173], and as software is eating the world, problems stemming from its security, or lack thereof, is eating it as well. Or- ganisations are increasingly moving to the cloud and adopting new architecture patterns in this new environment, such as cloud native and microservice ar- chitecture. While moving to the cloud generally results in better security for organisations, due to large professional platforms, microservice architectures in- troduce some new problems in regards to cross-cutting concerns like security, robustness and observabiltity. Service mesh is a technology that aims to provide cloud native and application agnostic solution to many of the challenges with micro service architectures. In parallel with the cloud native revolution there has been innovations in areas like security as well. Authentication, authoriza- tion, and access control have changed drastically, with new requirements for how users want to manage and use their identity. Zero Trust Architectures is an example of this drawn to its logical conclusion where no connection is trusted by default. Unfortunately security breaches stemming from poor implementation of security protocols and frameworks rank among the highest still. -

Ragel State Machine Compiler User Guide
Ragel State Machine Compiler User Guide by Adrian Thurston License Ragel version 6.3, August 2008 Copyright c 2003-2007 Adrian Thurston This document is part of Ragel, and as such, this document is released under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version. Ragel is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PUR- POSE. See the GNU General Public License for more details. You should have received a copy of the GNU General Public License along with Ragel; if not, write to the Free Software Foundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111-1307 USA i Contents 1 Introduction 1 1.1 Abstract...........................................1 1.2 Motivation.........................................1 1.3 Overview..........................................2 1.4 Related Work........................................4 1.5 Development Status....................................5 2 Constructing State Machines6 2.1 Ragel State Machine Specifications............................6 2.1.1 Naming Ragel Blocks...............................7 2.1.2 Machine Definition.................................7 2.1.3 Machine Instantiation...............................7 2.1.4 Including Ragel Code...............................7 2.1.5 Importing Definitions...............................7 2.2 Lexical Analysis of a Ragel Block.............................8 -

Server Administration Manual Release Latest
Nextcloud Server Administration Manual Release latest The Nextcloud developers Oct 01, 2021 CONTENTS 1 Introduction 1 1.1 Videos and blogs.............................................1 1.2 Target audience..............................................1 2 Release notes 3 3 Maintenance and release schedule5 3.1 Major releases..............................................5 3.2 Maintenance releases...........................................5 3.3 Older versions..............................................6 4 Installation and server configuration7 4.1 System requirements...........................................7 4.2 Deployment recommendations......................................9 4.3 Installation on Linux...........................................9 4.4 Installation wizard............................................ 17 4.5 Installing from command line...................................... 21 4.6 Supported apps.............................................. 22 4.7 SELinux configuration.......................................... 24 4.8 NGINX configuration.......................................... 27 4.9 Hardening and security guidance.................................... 36 4.10 Server tuning............................................... 40 4.11 Example installation on Ubuntu 20.04 LTS............................... 42 4.12 Example installation on CentOS 8.................................... 44 4.13 Example installation on OpenBSD.................................... 48 5 Nextcloud configuration 53 5.1 Warnings on admin page........................................ -

Narciso Martí Oliet Universidad Complutense De Madrid, 2018 Resumen
BF y el asombroso mundo de los lenguajes esotéricos Narciso Martí Oliet Universidad Complutense de Madrid, 2018 Resumen Entre los miles de lenguajes de programación que existen, hay una especie que se ha hecho más visible en los últimos años, la de los lenguajes esotéricos. Se trata de lenguajes que no pretenden facilitarle la vida al programador o al menos facilitar la programación de ciertos sistemas, sino precisamente todo lo contrario; en la creación de muchos de ellos ha primado la diversión sobre la utilidad. En esta presentación veremos un panorama general de esta especie de lenguajes, prestando un poco más de atención a BF, uno de los lenguajes más famosos entre ellos. GitHub’s most popular PLs Ruby C++ C PHP Shell scripts Python TypeScript Java C# JavaScript PL Explorations (textbook) JavaScript Java CoffeeScript Clojure Lua Elm Python Erlang Ruby Go Julia Swift PL Explorations (more langs) Fortran C++ ML TypeScript COBOL Rust OCaml Dart Lisp CLU Haskell APL Algol Ada F# Prolog Simula C# Elixir K Smalltalk Scala PHP Io C Perl Hack Factor Lenguajes esotéricos Naturaleza ofuscada Utilidad dudosa Características poco comunes Prueba de concepto Según algunos APL, Lisp, Haskell, Oz (multiparadigma), JavaScript son buenos ejemplos. Lenguajes esotéricos Lenguaje de programación minimalista Sintaxis muy básica Alfabeto restringido Desafío para la creación e implementación Desafío para la programación Lenguajes esotéricos Cercanos a conceptos esenciales en computación Máquinas de Turing y máquinas de registros Turing computabilidad y -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Mda13:Hpg-Variant-Developers.Pdf
Overview Global schema: Binaries HPG Variant VCF Tools HPG Variant Effect HPG Variant GWAS Describing the architecture by example: GWAS Main workflow Reading configuration files and command-line options Parsing input files Parallelization schema How to compile: Dependencies and application Hacking HPG Variant Let's talk about... Global schema: Binaries HPG Variant VCF Tools HPG Variant Effect HPG Variant GWAS Describing the architecture by example: GWAS Main workflow Reading configuration files and command-line options Parsing input files Parallelization schema How to compile: Dependencies and application Hacking HPG Variant Binaries: HPG Variant VCF Tools HPG Variant VCF Tools preprocesses VCF files I Filtering I Merging I Splitting I Retrieving statistics Binaries: HPG Variant Effect HPG Variant Effect retrieves information about the effect of mutations I Querying a web service I Uses libcurl (client side) and JAX-RS/Jersey (server side) I Information stored in CellBase DB Binaries: HPG Variant GWAS HPG Variant GWAS conducts genome-wide association studies I Population-based: Chi-square, Fisher's exact test I Family-based: TDT I Read genotypes from VCF files I Read phenotypes and familial information from PED files Let's talk about... Global schema: Binaries HPG Variant VCF Tools HPG Variant Effect HPG Variant GWAS Describing the architecture by example: GWAS Main workflow Reading configuration files and command-line options Parsing input files Parallelization schema How to compile: Dependencies and application Hacking HPG Variant Architecture: Main workflow -

Implementation of the BOLARE Programming Language
Implementation of the BOLARE Programming Language Viktor Pavlu ([email protected]) Institute of Computer Languages, Vienna University of Technology, Argentinierstrasse 8/E185, 1040 "ien, Austria ABSTRACT REBOL is a very flexible, dynamic, reflective programming language that clearly differs from the dynamic languages currently in popular use! The idea behind REBOL is that different problems should be attacked with different languages that have varying levels of granularity, each specifi- cally tailored to its problem domain. These domain-specific languages should give the program- mer the power to #rite programs that are closer to the problem and more expressive, thus shorter and easier to read, maintain and extend than would be possible in today’s dynamic programming languages. Despite its promising features, REBOL has not gained wide acceptance. Above all, this is due to the following: )*+ The language is merely defined by means o its only implementation, ),+ this implementation is closed-source and has many flaws, and )-+ the flaws are here to stay! .e therefore started project BOLARE. Aim o this project is to build an interpreter for a lan- guage that very closely resembles REBOL but leaves out all unintentional behavior that only stems from artifacts of the original implementation. After an introduction to REBOL/BOLARE in general, the three areas currently being #orked on are presented: Parser Generator: REBOL has a large set o built-in datatypes that have their own literal form making it easy to embed dates, times, email-addresses, tag structures, coordinates, binary data, etc. in scripts. The BOLARE parser is dynamically generated from a declarative de- scription of literal forms.