Embedded DOS-ROM User's Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Better Performance Through a Disk/Persistent-RAM Hybrid Design
The Conquest File System: Better Performance Through a Disk/Persistent-RAM Hybrid Design AN-I ANDY WANG Florida State University GEOFF KUENNING Harvey Mudd College PETER REIHER, GERALD POPEK University of California, Los Angeles ________________________________________________________________________ Modern file systems assume the use of disk, a system-wide performance bottleneck for over a decade. Current disk caching and RAM file systems either impose high overhead to access memory content or fail to provide mechanisms to achieve data persistence across reboots. The Conquest file system is based on the observation that memory is becoming inexpensive, which enables all file system services to be delivered from memory, except providing large storage capacity. Unlike caching, Conquest uses memory with battery backup as persistent storage, and provides specialized and separate data paths to memory and disk. Therefore, the memory data path contains no disk-related complexity. The disk data path consists of only optimizations for the specialized disk usage pattern. Compared to a memory-based file system, Conquest incurs little performance overhead. Compared to several disk-based file systems, Conquest achieves 1.3x to 19x faster memory performance, and 1.4x to 2.0x faster performance when exercising both memory and disk. Conquest realizes most of the benefits of persistent RAM at a fraction of the cost of a RAM-only solution. Conquest also demonstrates that disk-related optimizations impose high overheads for accessing memory content in a memory-rich environment. Categories and Subject Descriptors: D.4.2 [Operating Systems]: Storage Management—Storage Hierarchies; D.4.3 [Operating Systems]: File System Management—Access Methods and Directory Structures; D.4.8 [Operating Systems]: Performance—Measurements General Terms: Design, Experimentation, Measurement, and Performance Additional Key Words and Phrases: Persistent RAM, File Systems, Storage Management, and Performance Measurement ________________________________________________________________________ 1. -

System Calls System Calls
System calls We will investigate several issues related to system calls. Read chapter 12 of the book Linux system call categories file management process management error handling note that these categories are loosely defined and much is behind included, e.g. communication. Why? 1 System calls File management system call hierarchy you may not see some topics as part of “file management”, e.g., sockets 2 System calls Process management system call hierarchy 3 System calls Error handling hierarchy 4 Error Handling Anything can fail! System calls are no exception Try to read a file that does not exist! Error number: errno every process contains a global variable errno errno is set to 0 when process is created when error occurs errno is set to a specific code associated with the error cause trying to open file that does not exist sets errno to 2 5 Error Handling error constants are defined in errno.h here are the first few of errno.h on OS X 10.6.4 #define EPERM 1 /* Operation not permitted */ #define ENOENT 2 /* No such file or directory */ #define ESRCH 3 /* No such process */ #define EINTR 4 /* Interrupted system call */ #define EIO 5 /* Input/output error */ #define ENXIO 6 /* Device not configured */ #define E2BIG 7 /* Argument list too long */ #define ENOEXEC 8 /* Exec format error */ #define EBADF 9 /* Bad file descriptor */ #define ECHILD 10 /* No child processes */ #define EDEADLK 11 /* Resource deadlock avoided */ 6 Error Handling common mistake for displaying errno from Linux errno man page: 7 Error Handling Description of the perror () system call. -

OS 386 Multiuser/Multitasking Operating System
OS 386 Multiuser/Multitasking Operating System REFERENCE GUIDE [Q] DIGITAL RESEARCH@ os REFERENCE GUIDE [jill DIGITAL RESEARCH~ COPYRIGHT Copyright © 1987 Digital Research Inc. All rights reserved. No part of this publication may be reproduced, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise without the prior written permission of Digital Research Inc, 60 Garden Court, Box DRI, Monterey, California 93942 DISCLAIMER DIGITAL RESEARCH MAKES NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE CONTENTS HEREOF AND SPECIFICALLY DISCLAIMS ANY IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE. Further Digital Research Inc. reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Digital Research Inc to notify any person of such revision or changes. NOTICE TO USER This manual should not be construed as any representation or warranty with respect to the software named herein. Occasionally changes or variations exist in the software that are not reflected in the manual. Generally, if such changes or variations are known to exist and to affect the product significantly, a release note or READ.ME file accompanies the manual and the distribution disks. In that event, be sure to read the release note or READ.ME file before using the product. ii TRADEMARKS Digital Research and its logo, CP/M, and CP/M-86 are registered trademarks of Digital Research Inc. Cardfile, Concurrent, Concurrent DOS 386, Concurrent DOS XM, DR EDIX, DOS Plus and MP/M-86 are trademarks of Digital Research Inc. -

Towards Scalable Multiprocessor Virtual Machines
USENIX Association Proceedings of the Third Virtual Machine Research and Technology Symposium San Jose, CA, USA May 6–7, 2004 © 2004 by The USENIX Association All Rights Reserved For more information about the USENIX Association: Phone: 1 510 528 8649 FAX: 1 510 548 5738 Email: [email protected] WWW: http://www.usenix.org Rights to individual papers remain with the author or the author's employer. Permission is granted for noncommercial reproduction of the work for educational or research purposes. This copyright notice must be included in the reproduced paper. USENIX acknowledges all trademarks herein. Towards Scalable Multiprocessor Virtual Machines Volkmar Uhlig Joshua LeVasseur Espen Skoglund Uwe Dannowski System Architecture Group Universitat¨ Karlsruhe [email protected] Abstract of guests, such that they only ever access a fraction of the physical processors, or alternatively time-multiplex A multiprocessor virtual machine benefits its guest guests across a set of physical processors to, e.g., ac- operating system in supporting scalable job throughput commodate for spikes in guest OS workloads. It can and request latency—useful properties in server consol- also map guest operating systems to virtual processors idation where servers require several of the system pro- (which can exceed the number of physical processors), cessors for steady state or to handle load bursts. and migrate between physical processors without no- Typical operating systems, optimized for multipro- tifying the guest operating systems. This allows for, cessor systems in their use of spin-locks for critical sec- e.g., migration to other machine configurations or hot- tions, can defeat flexible virtual machine scheduling due swapping of CPUs without adequate support from the to lock-holder preemption and misbalanced load. -

Life in the Fast Lane: Optimisation for Interactive and Batch Jobs Nikola Marković, Boemska T.S
Paper 11825-2016 Life in the Fast Lane: Optimisation for Interactive and Batch Jobs Nikola Marković, Boemska T.S. Ltd.; Greg Nelson, ThotWave Technologies LLC. ABSTRACT We spend so much time talking about GRID environments, distributed jobs, and huge data volumes that we ignore the thousands of relatively tiny programs scheduled to run every night, which produce only a few small data sets, but make all the difference to the users who depend on them. Individually, these jobs might place a negligible load on the system, but by their sheer number they can often account for a substantial share of overall resources, sometimes even impacting the performance of the bigger, more important jobs. SAS® programs, by their varied nature, use available resources in a varied way. Depending on whether a SAS® procedure is CPU-, disk- or memory-intensive, chunks of memory or CPU can sometimes remain unused for quite a while. Bigger jobs leave bigger chunks, and this is where being small and able to effectively exploit those leftovers can be a great advantage. We call our main optimization technique the Fast Lane, which is a queue configuration dedicated to jobs with consistently small SASWORK directories, that, when available, lets them use unused RAM in place of their SASWORK disk. The approach improves overall CPU saturation considerably while taking loads off the I/O subsystem, and without failure results in improved runtimes for big jobs and small jobs alike, without requiring any changes to deployed code. This paper explores the practical aspects of implementing the Fast Lane on your environment. -

Winreporter Documentation
WinReporter documentation Table Of Contents 1.1 WinReporter overview ............................................................................................... 1 1.1.1.................................................................................................................................... 1 1.1.2 Web site support................................................................................................. 1 1.2 Requirements.............................................................................................................. 1 1.3 License ....................................................................................................................... 1 2.1 Welcome to WinReporter........................................................................................... 2 2.2 Scan requirements ...................................................................................................... 2 2.3 Simplified Wizard ...................................................................................................... 3 2.3.1 Simplified Wizard .............................................................................................. 3 2.3.2 Computer selection............................................................................................. 3 2.3.3 Validate .............................................................................................................. 4 2.4 Advanced Wizard....................................................................................................... 5 2.4.1 -
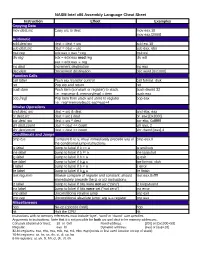
NASM Intel X86 Assembly Language Cheat Sheet
NASM Intel x86 Assembly Language Cheat Sheet Instruction Effect Examples Copying Data mov dest,src Copy src to dest mov eax,10 mov eax,[2000] Arithmetic add dest,src dest = dest + src add esi,10 sub dest,src dest = dest – src sub eax, ebx mul reg edx:eax = eax * reg mul esi div reg edx = edx:eax mod reg div edi eax = edx:eax reg inc dest Increment destination inc eax dec dest Decrement destination dec word [0x1000] Function Calls call label Push eip, transfer control call format_disk ret Pop eip and return ret push item Push item (constant or register) to stack. push dword 32 I.e.: esp=esp-4; memory[esp] = item push eax pop [reg] Pop item from stack and store to register pop eax I.e.: reg=memory[esp]; esp=esp+4 Bitwise Operations and dest, src dest = src & dest and ebx, eax or dest,src dest = src | dest or eax,[0x2000] xor dest, src dest = src ^ dest xor ebx, 0xfffffff shl dest,count dest = dest << count shl eax, 2 shr dest,count dest = dest >> count shr dword [eax],4 Conditionals and Jumps cmp b,a Compare b to a; must immediately precede any of cmp eax,0 the conditional jump instructions je label Jump to label if b == a je endloop jne label Jump to label if b != a jne loopstart jg label Jump to label if b > a jg exit jge label Jump to label if b > a jge format_disk jl label Jump to label if b < a jl error jle label Jump to label if b < a jle finish test reg,imm Bitwise compare of register and constant; should test eax,0xffff immediately precede the jz or jnz instructions jz label Jump to label if bits were not set (“zero”) jz looparound jnz label Jump to label if bits were set (“not zero”) jnz error jmp label Unconditional relative jump jmp exit jmp reg Unconditional absolute jump; arg is a register jmp eax Miscellaneous nop No-op (opcode 0x90) nop hlt Halt the CPU hlt Instructions with no memory references must include ‘byte’, ‘word’ or ‘dword’ size specifier. -

Thank You for Purchasing the Elder Scrolls: Arena. Dedicated Rpgers
The Elder Scrolls ARENA hank you for purchasing The Elder Scrolls: Arena. Dedicated RPGers have invested an incredible amount of effort into creating this detailed simulation. If you enjoy the game, please pass the word! There is no better advertising than a satisfied customer. TYou can also purchase the second chapter of The Elder Scrolls, entitled Daggerfall, in Fall 1996. TES: Daggerfall will feature the same open-endedness and breadth as Arena, but will feature increased NPC (Non-Player-Character) interaction, a faster, more sophisticated 3-D engine, and a more extensive storyline. With all the planned enhancements, Daggerfall will give you even more of an opportunity to role-play your character as you choose. We are very excited about Daggerfall and what it will mean to the role-playing community. On our part, we promise to keep bringing you the best in computer simulation software and welcome any suggestions you may have for how we can serve you better. Journey well, and peace be with you. —The Bethesda Team Installing the Game Place the CD into your computer’s CD-ROM drive. Type the drive letter followed by a colon (Ex: D: for most CD-ROM drives) and hit <ENTER>. Next type INSTALL and hit <ENTER>. If you are installing Arena from floppy disks, select ‘Install Game’ and follow the prompts. Because you are installing from the CDROM, 5 megabytes of data will be copied to your hard drive when you select ‘Exit’. The next step is to configure your game (see below). Configuring Arena to your System To configure any Sound FX and Music drivers once Arena has successfully installed (if you wish to play the game with sound and/or music), choose the ‘Configure Game’ option. -

XICE Lnstallationguide for Motorola 68000, 68HCOOO, 68ECOOO and 68302 Development Systems for DOS and UNIX Hosts
1mmm Applied Microsystems Corporation XICE lnstallationGuide for Motorola 68000, 68HCOOO, 68ECOOO and 68302 Development Systems for DOS and UNIX Hosts May 1993 PIN 922-17140-03 Copyright© 1993 Applied Microsystems Corporation All rights reserved. \' '\'9~t\B<\', nnt:iubmv ~'9\nt . ,:~ s no gnilis' IBM XT and IBM AT are trademarks of IBM Corporation Microsoft and MS-DOS™ are trademarks of Microsoft Corporation. Microtec is a registered trademarks of Microtec Research, Inc. SP ARC, SPARCstation, Sun, Sun-3, Sun-4, NFS, and PC-NFS are trademarks o Microsystems, Inc. UNIX is a registered trademark of AT&T. VALIDATE is a registered tradmark of Applied Microsystems Corporation I Contents Chapter 1 Introduction Organization of the documentation................................... 1-2 Overview of the toolchain................................................... 1-4 XICE ............................................................................. 1-4 XRAY............................................................................ 1-4 C Cross Compiler......................................................... 1-4 C++ Compiler............................................................... 1-4 Chapter2 Installing on a Sun Workstation Step 1: Check minimum requirements ................ ............. 2-2 Requirements for Sun 4 (SPARC) workstations........ 2-2 Step 2: Set up the directory structure............................... 2-3 · Step 3: Copy the software from the tape........................... 2-4 Step 4: Define individual user's setup.............................. -

Computing :: Operatingsystems :: DOS Beyond 640K 2Nd
DOS® Beyond 640K 2nd Edition DOS® Beyond 640K 2nd Edition James S. Forney Windcrest®/McGraw-Hill SECOND EDITION FIRST PRINTING © 1992 by James S. Forney. First Edition © 1989 by James S. Forney. Published by Windcrest Books, an imprint of TAB Books. TAB Books is a division of McGraw-Hill, Inc. The name "Windcrest" is a registered trademark of TAB Books. Printed in the United States of America. All rights reserved. The publisher takes no responsibility for the use of any of the materials or methods described in this book, nor for the products thereof. Library of Congress Cataloging-in-Publication Data Forney, James. DOS beyond 640K / by James S. Forney. - 2nd ed. p. cm. Rev. ed. of: MS-DOS beyond 640K. Includes index. ISBN 0-8306-9717-9 ISBN 0-8306-3744-3 (pbk.) 1. Operating systems (Computers) 2. MS-DOS (Computer file) 3. PC -DOS (Computer file) 4. Random access memory. I. Forney, James. MS-DOS beyond 640K. II. Title. QA76.76.063F644 1991 0058.4'3--dc20 91-24629 CIP TAB Books offers software for sale. For information and a catalog, please contact TAB Software Department, Blue Ridge Summit, PA 17294-0850. Acquisitions Editor: Stephen Moore Production: Katherine G. Brown Book Design: Jaclyn J. Boone Cover: Sandra Blair Design, Harrisburg, PA WTl To Sheila Contents Preface Xlll Acknowledgments xv Introduction xvii Chapter 1. The unexpanded system 1 Physical limits of the system 2 The physical machine 5 Life beyond 640K 7 The operating system 10 Evolution: a two-way street 12 What else is in there? 13 Out of hiding 13 Chapter 2. -

Optimizing HLT Code for Run-Time Efficiency
Optimizing HLT code for run-time efficiency Public Note Issue: 1 Revision: 0 Reference: LHCb-PUB-2010-017 Created: September 6, 2010 Last modified: November 4, 2010 LHCb-PUB-2010-017 04/11/2010 Prepared by: Axel Thuressona, Niko Neufeldb aLund,Sweden bCERN, PH Optimizing HLT code for run-time efficiency Ref: LHCb-PUB-2010-017 Public Note Issue: 1 Date: November 4, 2010 Abstract An upgrade of the High level trigger (HLT) farm at LHCb will be inevitable due to the increase in luminosity at the LHC. The upgrade will be done in two main ways. The first way is to make the software more efficient and faster. The second way is to increase the number of servers in the farm. This paper will concern both of these two ways divided into three parts. The first part is about NUMA, modern servers are all built with NUMA so an upgrade of the HLT farm will consist of this new architecture. The present HLT farm servers consists of the architecture UMA. After several tests it turned out that the Intel-servers that was used for testing (having 2 nodes) had very little penalty when comparing the worst-case the optimal-case. The conclusions for Intel-servers are that the NUMA architecture doesn’t affect the existing software negative. Several tests was done on an AMD-server having 8 nodes, and hence a more complicated structure. Non-optimal effects could be observed for this server and when comparing the worst-case with the optimal-case a big difference was found. So for the AMD-server the NUMA architecture can affect the existing software negative under certain circumstances. -

Open WATCOM Programmer's Guide
this document downloaded from... Use of this document the wings of subject to the terms and conditions as flight in an age stated on the website. of adventure for more downloads visit our other sites Positive Infinity and vulcanhammer.net chet-aero.com Watcom FORTRAN 77 Programmer's Guide Version 1.8 Notice of Copyright Copyright 2002-2008 the Open Watcom Contributors. Portions Copyright 1984-2002 Sybase, Inc. and its subsidiaries. All rights reserved. Any part of this publication may be reproduced, transmitted, or translated in any form or by any means, electronic, mechanical, manual, optical, or otherwise, without the prior written permission of anyone. For more information please visit http://www.openwatcom.org/ Portions of this manual are reprinted with permission from Tenberry Software, Inc. ii Preface The Watcom FORTRAN 77 Programmer's Guide includes the following major components: · DOS Programming Guide · The DOS/4GW DOS Extender · Windows 3.x Programming Guide · Windows NT Programming Guide · OS/2 Programming Guide · Novell NLM Programming Guide · Mixed Language Programming · Common Problems Acknowledgements This book was produced with the Watcom GML electronic publishing system, a software tool developed by WATCOM. In this system, writers use an ASCII text editor to create source files containing text annotated with tags. These tags label the structural elements of the document, such as chapters, sections, paragraphs, and lists. The Watcom GML software, which runs on a variety of operating systems, interprets the tags to format the text into a form such as you see here. Writers can produce output for a variety of printers, including laser printers, using separately specified layout directives for such things as font selection, column width and height, number of columns, etc.