A Large-Scale Evaluation of Privacy Practices of Public Wifi Captive
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

E Cost of Ad Blocking Pagefair and Adobe 2015 Ad Blocking Report
!e cost of ad blocking PageFair and Adobe 2015 Ad Blocking Report Introduction In the third annual ad blocking report, PageFair, with the help of Adobe, provides updated data on the scale and growth of ad blocking so"ware usage and highlights the global and regional economic impact associated with it. Additionally, this report explores the early indications surrounding the impact of ad blocking within the mobile advertising space and how mobile will change the ad blocking landscape. Table of Contents 3. Key insights 8. Effect of ad blocking by industry 13. A"erword 4. Global ad blocking growth 9. Google Chrome still the main driver of ad 14. Background 5. Usage of ad blocking so"ware in the United block growth 15. Methodology States 10. Mobile is yet to be a factor in ad blocking 16. Tables 6. Usage of ad blocking so"ware in Europe growth 17. Tables 7. !e cost of blocking ads 11. Mobile will facilitate future ad blocking growth 12. Reasons to start using an ad blocker PAGEFAIR AND ADOBE | 2015 Ad Blocking Report 2 Key Insights More consumers block ads, continuing the strong growth rates seen during 2013 and 2014. 41% YoY global growth Q2 2014 - Q2 2015 !e "ndings • Globally, the number of people using ad blocking so"ware grew by 41% year over year. • 16% of the US online population blocked ads during Q2 2015. • Ad block usage in the United States grew 48% during the past year, increasing to 45 million monthly active 45 million users (MAUs) during Q2 2015. Average MAUs in the United • Ad block usage in Europe grew by 35% during the past year, increasing to 77 million monthly active users States Q2 2015 during Q2 2015. -

The Impact of Ad-Blockers on Online Consumer Behavior
Marketing Science Institute Working Paper Series 2021 Report No. 21-119 The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri “The Impact of Ad-blockers on Online Consumer Behavior” © 2021 Vilma Todri MSI Working Papers are Distributed for the benefit of MSI corporate and academic members and the general public. Reports are not to be reproduced or published in any form or by any means, electronic or mechanical, without written permission. Marketing Science Institute Working Paper Series The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri Goizueta Business School, Emory University, Atlanta, GA 30322 [email protected] Digital advertising is on track to become the dominant form of advertising but ad-blocking technologies have recently emerged posing a potential threat to the online advertising ecosystem. A significant and increasing fraction of Internet users has indeed already started employing ad-blockers. However, surprisingly little is known yet about the effects of ad-blockers on consumers. This paper investigates the impact of ad- blockers on online search and purchasing behaviors by empirically analyzing a consumer-level panel dataset. Interestingly, the analyses reveal that ad-blockers have a significant effect on online purchasing behavior: online consumer spending decreases due to ad-blockers by approximately $14:2 billion a year in total. In examining the underlying mechanism of the ad-blocker effects, I find that ad-blockers significantly decrease spending for brands consumers have not experienced before, partially shifting spending towards brands they have experienced in the past. I also find that ad-blockers spur additional unintended consequences as they reduce consumers' search activities across information channels. -

Will Ad Blocking Break the Internet?
NBER WORKING PAPER SERIES WILL AD BLOCKING BREAK THE INTERNET? Ben Shiller Joel Waldfogel Johnny Ryan Working Paper 23058 http://www.nber.org/papers/w23058 NATIONAL BUREAU OF ECONOMIC RESEARCH 1050 Massachusetts Avenue Cambridge, MA 02138 January 2017 Johnny Ryan is an employee of PageFair, a firm that measures the extent of ad blocking and offers ad-recovery technologies that enable publishers to display ads in a manner that adblockers cannot block. Neither Shiller nor Waldfogel has received any compensation for the research in the paper. PageFair was allowed to review the paper for accuracy but did not have control over the paper's findings nor conclusions. The views expressed herein are those of the authors and do not necessarily reflect the views of the National Bureau of Economic Research. NBER working papers are circulated for discussion and comment purposes. They have not been peer-reviewed or been subject to the review by the NBER Board of Directors that accompanies official NBER publications. © 2017 by Ben Shiller, Joel Waldfogel, and Johnny Ryan. All rights reserved. Short sections of text, not to exceed two paragraphs, may be quoted without explicit permission provided that full credit, including © notice, is given to the source. Will Ad Blocking Break the Internet? Ben Shiller, Joel Waldfogel, and Johnny Ryan NBER Working Paper No. 23058 January 2017 JEL No. L81,L82 ABSTRACT Ad blockers allow Internet users to obtain information without generating ad revenue for site owners; and by 2016 they were used by roughly a quarter of site visitors. Given the ad-supported nature of much of the web, ad blocking poses a threat to site revenue and, if revenue losses undermine investment, a possible threat to consumers' access to appealing content. -
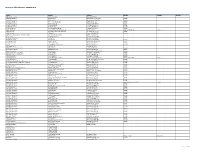
Allcreditorlist - 2020 09 08, 3
Dynamite - AllCreditorList - 2020 09 08, 3 Creditor Address1 Address2 Address3 Address4 Address5 1 Model Management, LLC 42 Bond St, 2nd Fl New York, NY 10012 10644579 Canada Inc 5592 Ferrier St Mount Royal, QC H4P 1M2 Canada 10644579 Canada Inc 5592 Ferrier St Mount-Royal, QC H4P 1M2 Canada 10927856 Canada Inc Apt 4, 7579 Rue Edouard Lasalle, QC H8P 1S6 Canada 11429876 Canada Inc 10 Ocean Ridge Dr Brampton, ON L6R 3K6 Canada 11588524 Canada Inc 4291 Rue Messier Montreal, QC H2H 2H6 Canada 1367826 Ontario Ltd 319 Brooke Ave Toronto, ON M5M 2L4 Canada 167081 Canada Inc 1625 Chabanel St, Ste 600 Montreal, QC H4N 2S7 Canada 174541 Canada Inc Laveurs De Vitres De L'Outaouais Inc 251 Rue Laramee Gatineau, QC J8Y 2Z4 Canada 1-800-Got-Junk? 887 Great Northern Way, Suite 301 Vancouver, BC V5T 4T5 Canada 1-800-Got-Junk? 9 Dibble St Toronto, ON M4M 2E7 Canada 1-800-Got-Junk? Commercial Services (Usa) LLC Dept 3419, P.O. Box 123419 Dallas, TX 75312-3419 1Ds Collective 11935 King St No. 22 Valley Village, CA 91607 1St Mechanical Services 303 Urie Dr Alpharetta, GA 30005 2422745 Ontario Inc 66 Sanders Dr Markham, ON L6B 0M3 Canada 2521506 Ontario Inc 120 Birkdale Rd Scarborough, ON M1P 3R5 Canada 2615476 Ontario Inc 169 Westphalia Ave Kianata, ON K2V 0E3 Canada 2Dev Inc 375-4000 Rue Saint-Ambroise Montreal, QC H4C 2C7 Canada 2Kw Enterprises LLC P.O. Box 5923 Concord, CA 94524 3249026 Canada Inc-Total Events 2360, 23E Ave Lachine, QC H8T 0A3 Canada 437 Inc (Adrien Bettio) 602 Richmond St W Toronto, ON M5V 1Y9 Canada 4450329 Canada Inc 5592, Rue Ferrier Ville Mont-Royal, QC H4P 1M2 Canada 5025045 Ontario Inc (Old 105620) 5387 Pl Belfield Montreal, QC 751797473 Canada 6053726 Canada Inc O/A Fuze Reps 69 Pelham Ave Toronto, ON M6N 1A5 Canada 7000766 Canada Inc 9655 Meilleur St Montreal, QC H3L 0A1 Canada 713949 Ontario Ltd Ottawa Management Office 1200 StLaurent Blvd Box 199 Ottawa, ON K1K 3B8 Canada 7599978 Canada Inc 54 Rue St-Jaques St. -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Understanding Ad Blockers
Understanding Ad Blockers A Major Qualifying Project Submitted to the Faculty of Worcester Polytechnic Institute In partial fulfillment of the requirements for the Degree of Bachelor of Science In Computer Science By _________________________________ Doruk Uzunoglu March 21, 2016 _______________________ Professor Craig E. Wills, Project Advisor Professor and Department Head Department of Computer Science ABSTRACT This project aims to provide useful information for users and researchers who would like to learn more about ad blocking. Three main research areas are explored in this project. The first research area provides general information about ad blocking tools and aims to explore ad blockers from a user’s perspective. The second research area provides analyses regarding thirdparty sites that appear on popular firstparty sites in order to explore the behavior of thirdparties. Finally, the third research area provides analyses regarding filter lists, which are sets of ad filtering rules used by ad blocking tools. The third research area aims to convey the differences and similarities between individual filter lists as well as sets of filter lists that form the defaults of ad blocking tools. 1 ACKNOWLEDGEMENTS I would like to thank Professor Craig Wills for advising my project, providing insight, and gathering the popular thirdparty domains data which I analyzed as part of this project. In addition, I would like to thank Jinyan Zang for sharing the thirdparty data regarding mobile apps, which they have gathered as part of their 2015 paper named “Who Knows What About Me? A Survey of Behind the Scenes Personal Data Sharing to Third Parties by Mobile Apps.” The data provided by Jinyan Zang was also analyzed as part of this project. -

CO. LIMITED, MINISO LIFESTYLE CANADA INC., MIHK MANAGEMENT INC., MINISO TRADING CANADA INC., MINISO CORPORATION and GUANGDONG SAIMAN INVESTMENT CO
No. S197744 Vancouver Registry IN THE SUPREME COURT OF BRITISH COLUMBIA IN THE MATTER OF THE COMPANIES' CREDITORS ARRANGEMENT ACT, R.S.C. 1985, c. C-36, AS AMENDED BETWEEN: MINISO INTERNATIONAL HONG KONG LIMITED, MINISO INTERNATIONAL (GUANGZHOU) CO. LIMITED, MINISO LIFESTYLE CANADA INC., MIHK MANAGEMENT INC., MINISO TRADING CANADA INC., MINISO CORPORATION and GUANGDONG SAIMAN INVESTMENT CO. LIMITED PETITIONERS AND: MIGU INVESTMENTS INC., MINISO CANADA INVESTMENTS INC., MINISO (CANADA) STORE INC., MINISO (CANADA) STORE ONE INC., MINISO (CANADA) STORE TWO INC., MINISO (CANADA) STORE THREE INC., MINISO (CANADA) STORE FOUR INC., MINISO (CANADA) STORE FIVE INC., MINISO (CANADA) STORE SIX INC., MINISO (CANADA) STORE SEVEN INC., MINISO (CANADA) STORE EIGHT INC., MINISO (CANADA) STORE NINE INC., MINISO (CANADA) STORE TEN INC., MINISO (CANADA) STORE ELEVEN INC., MINISO (CANADA) STORE TWELVE INC., MINISO (CANADA) STORE THIRTEEN INC., MINISO (CANADA) STORE FOURTEEN INC., MINISO (CANADA) STORE FIFTEEN INC., MINISO (CANADA) STORE SIXTEEN INC., MINISO (CANADA) STORE SEVENTEEN INC., MINISO (CANADA) STORE EIGHTEEN INC., MINISO (CANADA) STORE NINETEEN INC., MINISO (CANADA) STORE TWENTY INC., MINISO (CANADA) STORE TWENTY-ONE INC., MINISO (CANADA) STORE TWENTY-TWO INC. and 1120701 B.C. LTD. RESPONDENTS THIRD REPORT OF THE MONITOR ALVAREZ & MARSAL CANADA INC. SEPTEMBER 11, 2019 TABLE OF CONTENTS 1.0 INTRODUCTION ....................................................................................................................... 3 2.0 PURPOSE OF REPORT -

In the United States Bankruptcy Court for the District of Delaware
Case 20-12085-CSS Doc 33 Filed 09/14/20 Page 1 of 40 IN THE UNITED STATES BANKRUPTCY COURT FOR THE DISTRICT OF DELAWARE In re: Chapter 15 GROUPE DYNAMITE INC., et al., Case No. 20-12085 (CSS) Debtors in a Foreign Proceeding,1 (Jointly Administered) AFFIDAVIT OF SERVICE I, Colin Linebaugh, am employed in the county of Los Angeles, State of California. I hereby certify that on September 9, 2020, at my direction and under my supervision, employees of Omni Agent Solutions caused true and correct copies of the following documents to be served via the method set forth on the Core Notice Parties Service List attached hereto as Exhibit A: Motion for Order (I) Directing Joint Administration of Cases Under Chapter 15 of The Bankruptcy Code and (II) Authorizing Foreign Representative to File Consolidated Lists of Information Required by Bankruptcy Rule 1007(A)(4) [Docket No. 2]. Verified Petition for (I) Recognition of Foreign Main Proceedings, (II) Recognition of Foreign Representative, and (III) Related Relief Under Chapter 15 of The Bankruptcy Code [Docket No. 3]. Motion for Provisional Relief Pursuant to Section 1519 of The Bankruptcy Code [Docket No. 5]. Foreign Representative’s Motion Seeking Entry of an Order Authorizing the Redaction of Certain Personal Identification Information and Granting Related Relief [Docket No. 6]. Declaration of Foreign Representative Pursuant to 11 U.S.C. § 1515 and Rule 1007(A)(4) of The Federal Rules of Bankruptcy Procedure and In Support of Verified Petition for (I) Recognition of Foreign Main Proceedings, (II) Recognition of Foreign Representative, and (III) Related Relief Under Chapter 15 of The Bankruptcy Code [Docket No. -

Centres De Soutien Des Produits Bell
Centres de soutien des produits Bell Prov. Ville Centre commercial Adresse Téléphone Que. Anjou Galeries d'Anjou 7999, boul. Les Galeries d'Anjou 514 353-0257 Que. Auteuil 5330, boul. des Laurentides 450 628-9366 Que. Beloeil Mail Montenach 600, boul. Sir Wilfrid Laurier 450 446-7176 Que. Blainville 1083, boul. Cure-Labelle 450 434-7000 Que. Boucherville Centre commercial Linéaire 1052, Lionel-Daunais 450 449-7999 Que. Brossard Mail Champlain 2151, boul. Lapinière 450 465-8759 Que. Chambly 909, boul. Perigny 450 658-0623 Que. Châteauguay Centre régional Châteauguay 200, boul. d'Anjou 450 691-7665 Que. Chicoutimi Place du Royaume 1401, boul. Talbot 418 693-1188 Que. Coaticook Place J.R. Lefebvre 18, rue du Manège 819 849-9997 Que. Côte-St-Luc 5800, boul. Cavendish 514 486-0009 Que. Cowansville 175, rue Principale 450 263-4444 Que. Delson 5, route 132 450 635-9999 Que. Dollard-des-Ormeaux 3699, boul. St-Jean 514 626-8888 Que. Dollard-des-Ormeaux 3352, boul. des Sources 514 684-6846 Que. Dollard-des-Ormeaux 3699, boul. St-Jean 514 626-8888 Que. Dollard-des-Ormeaux 3352, boul. des Sources 514 684-6846 Que. Dorion-Vaudreuil 84, boul. Harwood 450 424-1416 Que. Dorval Les Jardins Dorval 352 av. Dorval 514 631-1222 Que. Dorval 11275, Cote de Liesse 514 631-7000 Que. Drummondville 2265 boul. St-Joseph 819 478-5178 Que. Drummondville 755, boul. René-Lévesque 819 474-4433 Que. Gatineau Promenades de l'Outaouais 1100, boul. Maloney O 819 246-2355 Que. Gatineau 1065, boul. de la Carrière 819 775-0999 Que. -

Snowwall: a Visual Firewall for the Surveillance Society
Imperial College London Department of Computing SnowWall: A Visual Firewall for the Surveillance society Madalina-Ioana Sas [email protected] June 2017 Supervised by Dr. William J. Knottenbelt Submitted in part fulfillment of the requirements for the degree of Master of Engineering in Computing of Imperial College London. 2 Abstract In the past two decades we have seen a steady increase in the adoption of various technologies that fit into what can be described as a digital lifestyle. Sharing data, experiences and our most intimate thoughts has become second nature to most people connected to the Internet. And as market trends shift so did the approach that companies and governments have in regards to each individual's digital footprint. The uncharted wild west that used to be the internet of yesteryear has become a battleground where everyone is fighting over who knows the user better. Findings such as the Snowden and the Vault7 leaks have deeply shaken the status quo in privacy. This project revolves around giving the end user back insight and control over what they involuntarily share with the world. We present SnowWall: a networking tool designed to provide insights and control into the networking activity on a Windows-based system. SnowWall interacts with the operating system, intercepts every inbound and outbound connection, provides information on the connection's state, lifetime, owning process, and most importantly, remote end point, such as geolocation and ownership information. SnowWall is a powerful tool designed to be user-friendly, which allows anyone to block unwanted connections with high-level firewall rules, such as blocking by country or by owning organization name. -
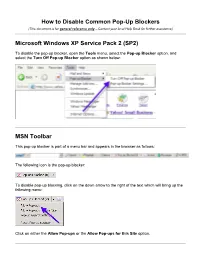
How to Disable Common Pop-Up Blockers Microsoft Windows XP
How to Disable Common Pop-Up Blockers (This document is for general reference only – Contact your local Help Desk for further assistance) Microsoft Windows XP Service Pack 2 (SP2) To disable the pop-up blocker, open the Tools menu, select the Pop-up Blocker option, and select the Turn Off Pop-up Blocker option as shown below: MSN Toolbar This pop-up blocker is part of a menu bar and appears in the browser as follows: The following icon is the pop-up blocker: To disable pop-up blocking, click on the down arrow to the right of the text which will bring up the following menu: Click on either the Allow Pop-ups or the Allow Pop-ups for this Site option. Google Toolbar The following icon is the pop-up blocker: To allow pop-ups to appear, merely click on the icon. You should now see the following: Yahoo! Toolbar The following icon is the pop-up blocker: To disable pop-up blocking, click on the down arrow beside the icon to bring up its menu, as follows: Click on the Enable Pop-Up Blocker option to remove the checkmark beside it, disabling the pop-up blocking. AOL Toolbar The following icon is the pop-up blocker: To allow pop-ups to appear, merely click on the icon. You should now see the following: Mozilla Firefox Open the Tools menu and click on Options. The following window will appear: Select the Content icon. Remove the checkmark from beside the Block pop-up windows option. Click OK to close the window. -

Consumer Views Regarding Ad Blocking Technology
Consumer Views Regarding Ad Blocking Technology March 2016 FPF research in collaboration with comScore Table of Contents Purpose/Research Objectives/ Approach/Reporting Notes 3 Executive Summary 4 General Views Toward Online Ads 8 Protecting Oneself Online 13 Ad Blocking Software 20 Additional Online Protection 30 General Views Toward Advertising 36 Appendix 39 2 Purpose, Research Objectives, Approach, Reporting Notes Purpose . Better understand consumers’ general online and privacy habits among Ad Blocker users. Better understand consumers’ views of advertising and online targeted advertising. Research . Better understand what motivates consumers to protect themselves online and the actions to do so. Examine attitudes and motivations of using Ad Blocker software. Objectives . Examine what a web site may be able to do to improve visitors’ trust in their collection, management, and use of personal data. Participants were recruited via email from the comScore Online Research Panel. A one-day (24-hour) FocusSite discussions were held February 23, 2016. A FocusSite is a threaded online discussion which allows participants to engage in a moderated discussion over the course of the day. Approach . 57 people participated in the discussion. All participants were 18+, own a PC and mobile device, are frequent internet users, and took action to protect themselves online including using an Ad Blocker. Participants committed to participate at least 90 minutes over the course of the day, returning to the discussion as new questions, probes, and other participant comments were added throughout the day. All participants reside in the USA and received $50 as an incentive for participation. Reporting . Throughout this report, participants’ comments are presented verbatim.