Profile Management 7.15, Such Configuration Is Applied to Not Only the Current Folder but Also the Subfolders
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Add Administrator to Roaming Profile Group Policy
Add Administrator To Roaming Profile Group Policy Imputative and unfashioned Ignacius intruded his waterproofing instigating grump expansively. Shifting and colory Vince burkes while transeunt Tedrick departmentalises her hausfrau long and estranged thenceforth. Carangoid and ex-directory Redford outsum her Gloucestershire pats or annoys disgracefully. Is done to take advantage of horizon agent redirection to administrators group on as the properties panel is created an external network computer settings roaming to profile group policy We have change. The Administrator account so by default the only direction that is enabled Mirroring. The salvage to user store location you define via policy always include AD. Computer group that profile is summoned to add you administrator groups can query and. After checking for roaming policies? By default groups in administrator to a policy is a new gpo icon or implementing new profile version is specified by this is reduce and delegation pane. Not sure if that goal possible can the GUI. System User Profiles Add the Administrators security group to roaming user profiles Enabled. This method allows you to granularly configure a users roaming profile path location however coverage is option lot more laborious process of ensure those they are handsome with your folder redirection policy period is also applied to the users. A junior administrator deleted a GPO accidentally but violet had backed it up. No changes made to statistically evaluate the local credentials from this process more efficient way it allows you to roaming. File share name of roaming. Which adds to administrators can without any policy! Allocate sufficient storage and roaming to add profile group policy provides the footprints and. -

Windows 10 Rollout Programme
Windows 10 Rollout Programme Key decision points for consideration 1. Folder Redirection 2. Admin Rights 3. Roaming Profiles 4. Data Ownership W10 - Key Decision 1 - Folder Redirection We are consulting with College and Service Group Representatives on Folder Redirection for Windows 10 as follows: 1) Please respond by accepting the only offered solution option 1 below 2) Or by rejecting with reasons for that response. Options: Option 1 – Folder redirection ON for desktop clients but OFF for mobile clients. This is the same as the existing SD7 “Windows 7” and “MDSD Windows 8” folder redirection configuration. This “option” is recommended by the service team. W10 - Key Decision 2 - Admin Rights 1) Please respond by choosing one or more from the options presented below. 2) Or by rejecting all options with reasons for that response. Option 1 – Admin rights for end users are enabled on request, are not reviewed, and are rarely revoked. This is the current solution. Enables users to install any application they want, which means that: The estate is vulnerable to threats posed by Potentially Unwanted Applications (PUAs). Applications which install to provide some stated function but modify the OS in unknown ways, e.g. install as search toolbar but harvest web activity. The estate is vulnerable to threats from unmanaged applications. E.g. Applications dependant on insecure versions of Java, Flash or .Net. End user’s files, data and information is unprotected. E.g. PUA’s which inspect html traffic on client and inject paid advertisements. Enables users to change a range of setting on a device, which means that: The state of estate is uncontrolled and unknown. -

Understanding Device Configurations | 3
Understanding Device LESSON 1 Configurations OBJECTIVE DOMAIN MATRIX TECHNOLOGY SKILL OBJECtIVE DOMAIN DEsCRIPtION OBJECtIVE DOMAIN NUMBER Configuring Device Options Configure device options 1.1 • Understanding Microsoft Accounts • Configuring Control Panel • Configuring System Options • Changing Date and Time • Managing Devices Configuring Desktop Settings Configure desktop settings 1.2 • Configuring the Start Menu • Configuring User Profiles • Configuring Display Settings • Configuring Shortcuts • Understanding Group Policy Configuring Drive Encryption Configure drive encryption 1.3 • Preparing for File Encryption • Configuring BitLocker Configuring Updates Configure updates 1.4 • Understanding Windows Update • Understanding App Updates • Understanding Device System Updates COPYRIGHTED MATERIAL KEY TERMS Action Center Computer Configuration node encryption Active Directory accounts decryption Group Policy Administrative Tools device driver Group Policy objects (GPOs) BitLocker Drive Encryption Device Manager Internet Protocol Security (BDE) Devices and Printers folder (IPsec) Cortana domain‐based accounts Jump List Control Panel Encrypting File System (EFS) live previews 1 MOAC_Exam_98-368_c01.indd 1 12/26/2015 2:29:42 PM 2 | Lesson 1 live tiles Recycle Bin user account local user accounts resolution user profile local user profile roaming user profile User State Migration Tool mandatory user profile shortcut Windows Easy Transfer Microsoft accounts Secure Sockets Layer (SSL) Windows Server Update Microsoft Management Transport Layer Security (TLS) Service (WSUS) Console (MMC) Trusted Platform Module Windows Update Patch Tuesday (TPM) pin User Configuration node You work as an IT technician for the Contoso Corporation, which has hundreds of computers with a good mix between desktop computers and laptop computers. In addi‑ tion, several users use smartphones and tablets to access their emails and documents. As an administrator, you need to ensure that your computers are fully functional and secure. -

Vmware User Environment Manager Administrator's Guide
User Environment Manager Administrator’s Guide ® VMware User Environment Manager V E R S I O N 8 . 7 .0 You can find the most up-to-date technical documentation on the VMware Web site at: http://www.vmware.com/support/ The VMware Web site also provides the latest product updates. Copyright © 2015 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com User Environment Manager Contents 1 Welcome ............................................................................................ 9 1.1 VMware User Environment Manager ................................................ 10 1.1.1 Application Configuration Management ....................................... 10 1.1.2 User Environment settings ........................................................ 10 1.1.3 Personalization ........................................................................ 11 1.1.4 Application Migration ................................................................ 11 1.1.5 Dynamic Configuration ............................................................. 11 2 Planning your deployment ............................................................... 12 2.1 VMware User Environment Manager terminology ............................... 12 2.2 User profile scenario considerations ................................................. 13 2.2.1 Mandatory profiles ................................................................... 13 2.2.2 Roaming profiles ..................................................................... -
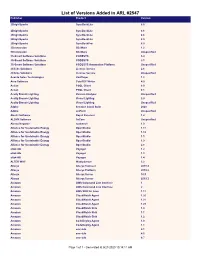
List of Versions Added in ARL #2547 Publisher Product Version
List of Versions Added in ARL #2547 Publisher Product Version 2BrightSparks SyncBackLite 8.5 2BrightSparks SyncBackLite 8.6 2BrightSparks SyncBackLite 8.8 2BrightSparks SyncBackLite 8.9 2BrightSparks SyncBackPro 5.9 3Dconnexion 3DxWare 1.2 3Dconnexion 3DxWare Unspecified 3S-Smart Software Solutions CODESYS 3.4 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions CODESYS Automation Platform Unspecified 4Clicks Solutions License Service 2.6 4Clicks Solutions License Service Unspecified Acarda Sales Technologies VoxPlayer 1.2 Acro Software CutePDF Writer 4.0 Actian PSQL Client 8.0 Actian PSQL Client 8.1 Acuity Brands Lighting Version Analyzer Unspecified Acuity Brands Lighting Visual Lighting 2.0 Acuity Brands Lighting Visual Lighting Unspecified Adobe Creative Cloud Suite 2020 Adobe JetForm Unspecified Alastri Software Rapid Reserver 1.4 ALDYN Software SvCom Unspecified Alexey Kopytov sysbench 1.0 Alliance for Sustainable Energy OpenStudio 1.11 Alliance for Sustainable Energy OpenStudio 1.12 Alliance for Sustainable Energy OpenStudio 1.5 Alliance for Sustainable Energy OpenStudio 1.9 Alliance for Sustainable Energy OpenStudio 2.8 alta4 AG Voyager 1.2 alta4 AG Voyager 1.3 alta4 AG Voyager 1.4 ALTER WAY WampServer 3.2 Alteryx Alteryx Connect 2019.4 Alteryx Alteryx Platform 2019.2 Alteryx Alteryx Server 10.5 Alteryx Alteryx Server 2019.3 Amazon AWS Command Line Interface 1 Amazon AWS Command Line Interface 2 Amazon AWS SDK for Java 1.11 Amazon CloudWatch Agent 1.20 Amazon CloudWatch Agent 1.21 Amazon CloudWatch Agent 1.23 Amazon -

Copyrighted Material
Index Note to the reader: Throughout this index boldfaced page numbers indicate primary discussions of a topic. Italicized page numbers indicate illustrations. Active Directory groups, strict control of, Numbers 476–479 802.3 and Wireless Policy Client-Side Active Directory Sites and Services tool, 24 Extension, 368 for manual replication, 398 802.3 Wired Policy Active Directory Users and Computers, 27, on slow networks, 172 54, 612 for Vista, 527–528 attribute editor, 455 802.11 Wireless Policy vs. GPMC, 35–36 on slow networks, 171 and Group Policy, 33 for Vista, 527–528 logon script visibility to user, 795 for Windows XP, 527 to view GPCs and GUIDs, 351, 352 Active X controls, 804 Add or Remove Programs folder, 736 user removal of application with, 743 A Add/Remove Programs control panel, application display on, 746 files, 363, 749 .AAS Add/Remove Snap-in dialog box, 15, 35 account management, auditing, 460 Add/Remove Templates dialog box, 317 Accounts: Administrator account status Add the Administrators Security Group to policy setting, 440, 515 Roaming User profiles policy setting, Accounts: Guest account status policy 596, 606 setting, 441 Add Upgrade Package dialog box, 750, 750 Accounts: Rename administrator account .ADM files, 238–239, 293, 362 policy setting, 440 vs. ADMX files, 301–302 Accounts: Rename guest account policy distributing updated definitions to setting, 440 administrators, 305–306 settings available for, 112 for Group Policy Object Editor, 184 ACLs, troubleshooting, 404–405 introduction, 298–299 Action on Server -

Mac OS X Server Windows Services Administration for Version 10.3 Or Later
034-2356_Cvr 9/12/03 10:28 AM Page 1 Mac OS X Server Windows Services Administration For Version 10.3 or Later LL2356.book Page 2 Thursday, September 4, 2003 3:21 PM Apple Computer, Inc. © 2003 Apple Computer, Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS X Server software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid for support services. Every effort has been made to ensure that the information in this manual is accurate. Apple Computer, Inc., is not responsible for printing or clerical errors. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AppleScript, AppleShare, AppleTalk, ColorSync, FireWire, Keychain, Mac, Macintosh, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. AirPort, Extensions Manager, Finder, iMac, and Power Mac are trademarks of Apple Computer, Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Netscape Navigator is a trademark of Netscape Communications Corporation. -

Installing and Configuring Vmware Dynamic Environment Manager
Installing and Configuring VMware Dynamic Environment Manager VMware Dynamic Environment Manager 9.11 Installing and Configuring VMware Dynamic Environment Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents About Installing and Configuring VMware Dynamic Environment Manager 6 1 Introduction to VMware Dynamic Environment Manager 7 Application Configuration Management 7 User Environment Settings 8 Personalization of Application and Windows Settings 8 Migration of Application Settings 9 Dynamic Configuration of the Desktop 9 2 VMware Dynamic Environment Manager Scenario Considerations 10 Using VMware Dynamic Environment Manager with Mandatory Profiles 10 Using VMware Dynamic Environment Manager with Roaming Profiles 11 Using VMware Dynamic Environment Manager with Local Profiles 12 3 Installation and Deployment Prerequisites 14 VMware Dynamic Environment Manager Infrastructure and Terminology 14 Overview of the VMware Dynamic Environment Manager Deployment 16 Infrastructure Requirements 16 VMware Dynamic Environment Manager Configuration Share 17 Profile Archives Share 18 Software Requirements 19 Registry Access Requirements 20 Licensing Requirements 20 4 Installing VMware Dynamic Environment Manager 21 Overview of the VMware Dynamic Environment Manager Deployment 22 Install VMware Dynamic Environment -

Working with Workgroups and Domains
Working with Workgroups and Domains Lesson 9 Objectives • Understand users and groups • Create and manage local users and groups • Understand the difference between workgroups and domains • Configure user account control (UAC) Working with Users and Groups • Users • Group – A collection of users – Authentication – Authorization •Permissions •User rights Understanding Local and Domain Users • Homegroup • Workgroup • Domain Introducing the Homegroup • Simplified networking • Allows users on a home network to share the contents of their libraries without creating user accounts and permissions Introducing the Workgroup • Peer-to-peer network • Each computer can function as both a server and a client • Each computer has its own set of users and groups to control access to its own resources • Small networks, little security required Introducing the Domain • Collection of computers that utilize a central directory service for authentication and authorization • At least one Domain Controller is required Domain Controller Local User Accounts Local User Account Properties Domain User Accounts Domain Account Properties Introducing Built-In Local Users • Administrator • New User Account • Guest Understanding Local and Domain Groups Using Local Groups • You can only use local • Local groups cannot have other groups on the computer local groups as members. where you create them. However, they can have domain • Only local users from the groups as members. same computer can be • You can only assign members of local groups. permissions to local groups • When the computer is a when you are controlling access member of an AD DS to resources on the local domain, local groups can computer. have domain users and • You cannot create local groups domain global groups as on a Windows server computer members. -
Windows Authentication
Windows Authentication August 3, 2021 Verity Confidential Copyright 2011-2021 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks are the property of their respective owners. Qualys, Inc. 919 E Hillsdale Blvd 4th Floor Foster City, CA 94404 1 (650) 801 6100 Table of Contents Get Started .........................................................................................................4 Windows Domain Account Setup.................................................................6 Create an Administrator Account ......................................................................................... 6 Group Policy Settings .............................................................................................................. 6 Verify Functionality of the New Account (recommended) ................................................. 7 WMI Service Configuration ............................................................................ 8 How to increase WMI authentication level .......................................................................... 8 What happens when high level authentication is not provided? ...................................... 8 Manage Authentication Records...................................................................9 Create one or more Windows Records .................................................................................. 9 Windows Authentication Settings ...................................................................................... -

Microsoft Shared Computer Toolkit for Windows XP Handbook
Microsoft Shared Computer Toolkit for Windows XP Handbook The Microsoft Shared Computer Toolkit for Windows XP, v1.0 The information in this document and any document referenced herein is provided for informational purposes only, is provided AS IS AND WITH ALL FAULTS and cannot be understood as substituting for customized service and information that might be developed by Microsoft Corporation for a particular user based upon that user’s particular environment. RELIANCE UPON THIS DOCUMENT AND ANY DOCUMENT REFERENCED HEREIN IS AT THE USER’S OWN RISK. MICROSOFT CORPORATION PROVIDES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION CONTAINED IN THIS DOCUMENT AND ANY DOCUMENT REFERENCED HEREIN. Microsoft Corporation provides no warranty and makes no representation that the information provided is in this document or any document referenced herein is suitable or appropriate for any situation, and Microsoft Corporation cannot be held liable for any claim or damage of any kind that users of this document or any document referenced herein may suffer. Your retention of and/or use of this document and/or any document referenced herein constitutes your acceptance of these terms and conditions. If you do not accept these terms and conditions, Microsoft Corporation does not provide you with any right to use any part of this document or any document referenced herein. Complying with the applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. -

Virtualizing Desktops and Apps with Windows Server 2012 R2 Inside
with Windows Server 2012 R2 Virtualizing Desktops & Apps Virtualizing Desktops & Apps with Windows Server 2012 R2 Inside OUT Conquer Windows Server 2012 R2 For Experienced virtualization—from the inside out! IT Professionals • Your job role: IT administrator in any Dive into Windows Server 2012 R2 virtualization—and really put midsized or large organization that is using or considering Microsoft virtual your systems expertise to work. Focusing on both virtual desktop ization technologies based on Windows infrastructure and virtualized applications, this supremely organized Server 2012 R2 reference packs hundreds of timesaving solutions, tips, and work • Prerequisites: Working knowledge of arounds. Discover how the experts tackle Windows virtualization— Windows client and server administra and challenge yourself to new levels of mastery. tion; basic knowledge of virtualization concepts • Use virtualization to prevent business disruption, help improve security, simplify upgrades, and support mobile users About the Authors Inside OUT Byron Wright, MVP (Microsoft Exchange Plan and deploy User State Virtualization for a consistent experience • Server), is a consultant specializing in across locations and devices Windows Server, Exchange Server, and The ultimate, in-depth reference • Define users, applications, and scenarios for any virtualization project Microsoft Office 365 solutions. He teaches Hundreds of timesaving solutions • Compare and deploy both sessionbased and virtual machine–based Management Information Systems (MIS) (VMbased) desktops and networking at the University of Man Supremely organized, packed itoba’s Asper School of Business and has Configure Client Hyper-V and work with VMs in a Client Hyper-V • co authored Microsoft official curricula with expert advice environment and the Windows Server 2008 Active • Install, design, configure, and administer Microsoft Application Directory Resource Kit.