Mac Security Report 2019
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 0X9: Dynamic Monitoring (Tools)
The Art of Mac Malware: Analysis p. wardle Chapter 0x9: Dynamic Monitoring (Tools) Note: This book is a work in progress. You are encouraged to directly comment on these pages ...suggesting edits, corrections, and/or additional content! To comment, simply highlight any content, then click the icon which appears (to the right on the document’s border). 1 The Art of Mac Malware: Analysis p. wardle Note: As dynamic analysis involves executing the malware (to observe its actions), always perform such analysis in a virtual machine (VM) or on a dedicated malware analysis machine. ...in other words, don’t perform dynamic analysis on your main (base) system! In this chapter, we’ll focus on various dynamic analysis monitoring tools. Specifically, we’ll illustrate how process, file, and network monitors can efficiently provide invaluable insight into the capabilities and functionality of malware specimens. Process Monitoring Malware often spawns or executes child processes. If observed via a process monitor, such processes may quickly provide insight into the behavior and capabilities of the malware. Often such processes are built-in (system) command line utilities that the malware executes in order to (lazily) delegate required actions. For example: ■ A malicious installer might invoke the move (/bin/mv) or copy (/bin/cp) utilities to persistently install the malware. ■ To survey the system, the malware might invoke the process status (/bin/ps) utility to get a list of running processes, or the /usr/bin/whoami utility to determine the current user’s permissions. ■ The results of this survey may then be exfiltrated to a remote command and control server via /usr/bin/curl. -

AV-TEST Security Report for 2016/2017
FACTS AND FIGURES SECURITY REPORT The AV-TEST Security Report 2 WINDOWS Security Status 5 macOS Security Status 10 ANDROID Security Status 13 INTERNET THREATS Security Status 16 IoT Security Status 19 2016/17 Test Statistics 22 FACTS AND FIGURES Declining malware statistics It remains positive to note that the declining malware trend in 2016 The AV-TEST provided some relief, at least quantitatively. Thus, compared to 2015, detection systems were required to seek out and defend against 14% fewer Security Report malware samples. In total, this amounted to precisely 11,725,292 fewer newly developed malware programs than in the previous year. It should not be The best news right off the bat: forgotten, however, that the volume of newly developed malware in 2016 still represented the second-highest since the beginning of measurements by Compared to the previous year, the AV-TEST systems. In addition, 2015 saw skyrocketing growth in malware the detection systems of AV-TEST showed programs and in comparison to 2014, practically a doubling of the sample statistics. The overall number of malware programs for all operating systems a slight decline in the development currently exceeds 640 million. of malware programs for the year 2016. Without wanting to belittle the positive trend for 2016, the fact remains that Overall, that is a pleasing trend, however there have been several short-term downward trends since the beginning of by no means any reason to celebrate, measurements in 1984, a total of six times, without seriously influencing the clear, long-term trend – towards more malware. Despite declining numbers, as evidenced by the AV-TEST Institute‘s in 2016, the AV-TEST analysis systems still recorded an average of 350,000 statistics of this year‘s Security Report. -
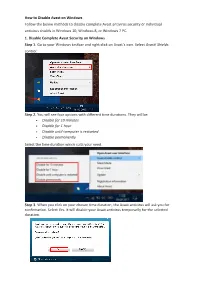
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet -

Secureworks Corp. (Exact Name of Registrant As Specified in Its Charter)
UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 FORM 10-K (Mark One) ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES þ EXCHANGE ACT OF 1934 For the fiscal year ended February 3, 2017 or TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES o EXCHANGE ACT OF 1934 For the transition period from to Commission file number: 001-37748 SecureWorks Corp. (Exact name of registrant as specified in its charter) Delaware 56-2015395 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) One Concourse Parkway NE Suite 500, Atlanta, Georgia 30328 (Address of principal executive offices) (Zip Code) Registrant’s telephone number, including area code: (404)327-6339 Securities registered pursuant to Section 12(b) of the Act: Title of each class Name of each exchange on which registered Class A Common Stock, par value $0.01 per share The NASDAQ Stock Market LLC (NASDAQ Global Select Market) Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes o No R Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes o No R Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

Fortios 6.2 Data Sheet
DATA SHEET FortiOS™ 6.2 Fortinet’s Security Operating System FortiOS enables the Fortinet Security Fabric, allowing organizations to readily achieve a security-driven network with one intuitive operating system. FortiOS 6.2, the latest version of Fortinet’s security operating system, powers the entire Security Fabric, helping customers reduce and manage the attack surface, prevent advanced threats, and reduce complexity from Internet of Things (IoT) devices to the cloud. Broad Visibility Highlights — What’s New Achieve full visibility across multi-cloud and branch § Spilt-task VDOM environments with SD-WAN, native cloud and virtual connectors, and intent-based segmentation. § Expanding product Integration with Security Fabric § New SDN and Threat Feed Connectors Integrated AI-driven Breach Prevention § SD-WAN Rule Definition and VPN Stop threats quickly and detect active intrusions and Setup Enhancements bad actors across the entire Security Fabric with § Extending Public Cloud Support integrated AI-driven intelligence capabilities combined § Additional Triggers and Actions with advanced, leading-edge technologies. § Flow-based security profile Improvements § MAC Address Objects § Consolidated risk View on Automated Operations, Orchestration, Topology Map and Response § FortiSandbox Cloud Region Reduce complexity and costs with rapid orchestrated Selection threat response, automated workflows, and § Policy Setup and Visibility automated auditing and compliance. Upgrades DATA SHEET | FortiOS™ 6.2 Overview Introducing FortiOS 6.2 increasing digital connectedness of organizations is driving the requirement for a security transformation, where security is integrated into applications, devices, and cloud networks to protect business data spread across these complex environments. FortiOS™ 6.2 delivers hundreds of new features and capabilities that were designed to provide the broad visibility, integrated threat intelligence, and automated response required for digital business. -

Antivirus Downloads Free the Best Antivirus Software 2021: Free and Paid Options Compared
antivirus downloads free The best antivirus software 2021: free and paid options compared. Having one of the best antivirus software packages in your device is as important as it has ever been. Yup, it's an incredibly boring and dry thing to think about - particularly as many of us won't have been affected by a virus for years and years, if ever - but that's not meant to say you shouldn't have one of the best antivirus packs anyway. It's definitely still a case of 'rather have it and not need than need it and not have it', for sure. We can guarantee that there are baddies still out there and want to get your personal details, even if it might not be in the traditional sense of a virus anymore. So, whether you have a premium machine like one of the best gaming PCs or one of the best gaming laptops, or just a cheap one for work, having one of the best antivirus will protect you while you work or play. If you're looking to beef up security on an Apple Mac or MacBook though, you might want to consider checking out our antivirus for Macs guide. However, in the year 2021, it is a very saturated market. There are free versions that we remember from years ago still around - though now refined - and also some newer or much-revamped paid-for programs that are more comprehensive than ever. As a result, it can be a confusing market to work your way through. But fear not, we’ve looked at a range of options available, from premium to free, from some of the biggest players in online security, to help you make a safe and informed decision on the best antivirus software for you. -

Jotti Report
Online malware scan Page 1 of 2 Jotti's malware scan 2.99-TRANSITION_TO_3.00-R1 File to upload & scan: Browse... Submit Service Service load: 0% 100% File: iehv.zip Status: OK MD5: 7e1297c4bc4fc8d972b65396f27e3216 Packers detected: PE_PATCH.UPX, UPX Virus and Trojan Remover Download Free Trojan & Virus Scan Recommended and Used By The Experts www.pctools.com Scanner results Scan taken on 28 Feb 2009 16:48:40 (GMT) A-Squared Found nothing AntiVir Found nothing ArcaVir Found nothing Avast Found nothing AVG Antivirus Found nothing BitDefender Found nothing ClamAV Found nothing CPsecure Found nothing Dr.Web Found nothing F-Prot Antivirus Found nothing F-Secure Anti-Virus Found nothing Ikarus Found nothing Kaspersky Anti-Virus Found nothing NOD32 Found nothing Norman Virus Control Found nothing Panda Antivirus Found nothing Sophos Antivirus Found nothing VirusBuster Found nothing VBA32 Found nothing Powered by Disclaimer This service is by no means 100% safe. If this scanner says 'OK', it does not necessarily mean the file is clean. There could be a whole new virus on the loose. NEVER rely on one single product only, not even this service, even though it utilizes several products. Therefore, We cannot and will not be held responsible for any damage caused by results presented by this non-profit online service. Scanning can take a while, since several scanners are being used, plus the fact some scanners use very high levels of (time consuming) heuristics. Scanners used are Linux versions, differences with Windows scanners may or may not occur. Some scanners will only report one virus when scanning archives with multiple pieces of malware. -

EXABEAM SECURITY MANAGEMENT PLATFORM INTEGRATIONS Inbound Data Sources for Log Ingestion and Service Integrations for Incident Response
EXABEAM SECURITY MANAGEMENT PLATFORM INTEGRATIONS Inbound Data Sources for Log Ingestion and Service Integrations for Incident Response The more data sources you have in your security incident and event management (SIEM), the better equipped you are to detect attacks. And the more security orchestration and automation response (SOAR) connections you have between your SIEM and your IT and security systems the quicker LIMITLESS SCALE WITH FLAT, PREDICTABLE PRICING you can respond. Every log and every security event matters. Not retaining your log data can create security blinds spots that prevent Exabeam Security Management Platform (SMP) has compliance or leave your organization vulnerable to attack. approximately 350 integrations with IT and security products Exabeam is designed to scale without penalizing you for the to help your analysts work smarter - providing inbound amount of data you ingest. Our flat pricing model is based integrations with data sources from vendors to easily on the number of users and devices in your environment, allow you to ingest as much data as possible; and SOAR not data volume. integrations with 3rd party vendors to help you automate and orchestrate your security response. CENTRALIZED SECURITY AUTOMATION AND ORCHESTRATION WITH 3RD PARTY INTEGRATIONS EXTENSIVE DATA SOURCES Exabeam Incident Responder integrates with approximately Exabeam ingests data from approximately 300 different 70 third party IT and security products. These integrations IT and security products to provide security analysts with help your analysts to gather evidence and attach them as the full scope of events. Exabeam Data Lake, Exabeam artifacts to incidents or quarantine affected users and assets Advanced Analytics and Exabeam Entity Analytics ingest logs until incidents are mitigated. -

Fortigate 100F Series Data Sheet
DATA SHEET ® FortiGate 100F Series Next Generation Firewall Secure SD-WAN FG-100F and FG-101F Secure Web Gateway The FortiGate 100F series provides an application-centric, scalable, and secure SD-WAN solution with Next Generation Firewall (NGFW) capabilities for mid-sized to large enterprises deployed at the campus or branch level. Protects against cyber threats with system-on-a-chip acceleration and industry-leading secure SD-WAN in a simple, affordable, and easy to deploy solution. Fortinet’s Security-Driven Networking approach provides tight integration of the network to the new generation of security. Security Networking n Identifies thousands of applications inside network traffic n Delivers advanced networking capabilities that seamlessly for deep inspection and granular policy enforcement integrate with advanced layer 7 security and virtual n Protects against malware, exploits, and malicious domains (VDOMs) to offer extensive deployment websites in both encrypted and non-encrypted traffic flexibility, multi-tenancy and effective utilization of resources n Prevent and detect against known and unknown attacks using continuous threat intelligence from AI-powered n Delivers high-density, flexible combination of various FortiGuard Labs security services high-speed interfaces to enable best TCO for customers for data center and WAN deployments Performance n Delivers industry’s best threat protection performance and Management ultra-low latency using purpose-built security processor n Includes a management console that is effective, simple