Other Still Image Compression Standards
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PDF/A for Scanned Documents
Webinar www.pdfa.org PDF/A for Scanned Documents Paper Becomes Digital Mark McKinney, LuraTech, Inc., President Armin Ortmann, LuraTech, CTO Mark McKinney President, LuraTech, Inc. © 2009 PDF/A Competence Center, www.pdfa.org Existing Solutions for Scanned Documents www.pdfa.org Black & White: TIFF G4 Color: Mostly JPEG, but sometimes PNG, BMP and other raster graphics formats Often special version formats like “JPEG in TIFF” Disadvantages: Several formats already for scanned documents Even more formats for born digital documents Loss of information, e.g. with TIFF G4 Bad image quality and huge file size, e.g. with JPEG No standardized metadata spread over all formats Not full text searchable (OCR) inside of files Black/White: Color: - TIFF FAX G4 - TIFF - TIFF LZW Mark McKinney - JPEG President, LuraTech, Inc. - PDF 2 Existing Solutions for Scanned Documents www.pdfa.org Bad image quality vs. file size TIFF/BMP JPEG TIFF G4 23.8 MB 180 kB 60 kB Mark McKinney President, LuraTech, Inc. 3 Alternative Solution: PDF www.pdfa.org PDF is already widely used to: Unify file formats Image à PDF “Office” Documents à PDF Other sources à PDF Create full-text searchable files Apply modern compression technology (e.g. the JPEG2000 file formats family) Harmonize metadata Conclusion: PDF avoids the disadvantages of the legacy formats “So if you are already using PDF as archival Mark McKinney format, why not use PDF/A with its many President, LuraTech, Inc. advantages?” 4 PDF/A www.pdfa.org What is PDF/A? • ISO 19005-1, Document Management • Electronic document file format for long-term preservation Goals of PDF/A: • Maintain static visual representation of documents • Consistent handing of Metadata • Option to maintain structure and semantic meaning of content • Transparency to guarantee access • Limit the number of restrictions Mark McKinney President, LuraTech, Inc. -

Chapter 9 Image Compression Standards
Fundamentals of Multimedia, Chapter 9 Chapter 9 Image Compression Standards 9.1 The JPEG Standard 9.2 The JPEG2000 Standard 9.3 The JPEG-LS Standard 9.4 Bi-level Image Compression Standards 9.5 Further Exploration 1 Li & Drew c Prentice Hall 2003 ! Fundamentals of Multimedia, Chapter 9 9.1 The JPEG Standard JPEG is an image compression standard that was developed • by the “Joint Photographic Experts Group”. JPEG was for- mally accepted as an international standard in 1992. JPEG is a lossy image compression method. It employs a • transform coding method using the DCT (Discrete Cosine Transform). An image is a function of i and j (or conventionally x and y) • in the spatial domain. The 2D DCT is used as one step in JPEG in order to yield a frequency response which is a function F (u, v) in the spatial frequency domain, indexed by two integers u and v. 2 Li & Drew c Prentice Hall 2003 ! Fundamentals of Multimedia, Chapter 9 Observations for JPEG Image Compression The effectiveness of the DCT transform coding method in • JPEG relies on 3 major observations: Observation 1: Useful image contents change relatively slowly across the image, i.e., it is unusual for intensity values to vary widely several times in a small area, for example, within an 8 8 × image block. much of the information in an image is repeated, hence “spa- • tial redundancy”. 3 Li & Drew c Prentice Hall 2003 ! Fundamentals of Multimedia, Chapter 9 Observations for JPEG Image Compression (cont’d) Observation 2: Psychophysical experiments suggest that hu- mans are much less likely to notice the loss of very high spatial frequency components than the loss of lower frequency compo- nents. -

Electronics Engineering
INTERNATIONAL JOURNAL OF ELECTRONICS ENGINEERING ISSN : 0973-7383 Volume 11 • Number 1 • 2019 Study of Different Image File formats for Raster images Prof. S. S. Thakare1, Prof. Dr. S. N. Kale2 1Assistant professor, GCOEA, Amravati, India, [email protected] 2Assistant professor, SGBAU,Amaravti,India, [email protected] Abstract: In the current digital world, the usage of images are very high. The development of multimedia and digital imaging requires very large disk space for storage and very long bandwidth of network for transmission. As these two are relatively expensive, Image compression is required to represent a digital image yielding compact representation of image without affecting its essential information with reducing transmission time. This paper attempts compression in some of the image representation formats and the experimental results for some image file format are also shown. Keywords: ImageFileFormats, JPEG, PNG, TIFF, BITMAP, GIF,CompressionTechniques,Compressed image processing. 1. INTRODUCTION Digital images generally occupy a large amount of storage space and therefore take longer time to transmit and download (Sayood 2012;Salomonetal 2010;Miano 1999). To reduce this time image compression is necessary. Image compression is a technique used to identify internal data redundancy and then develop a compact representation that takes up less storage space than the original image size and the reverse process is called decompression (Javed 2016; Kia 1997). There are two types of image compression (Gonzalez and Woods 2009). 1. Lossy image compression 2. Lossless image compression In case of lossy compression techniques, it removes some part of data, so it is used when a perfect consistency with the original data is not necessary after decompression. -

JPEG and JPEG 2000
JPEG and JPEG 2000 Past, present, and future Richard Clark Elysium Ltd, Crowborough, UK [email protected] Planned presentation Brief introduction JPEG – 25 years of standards… Shortfalls and issues Why JPEG 2000? JPEG 2000 – imaging architecture JPEG 2000 – what it is (should be!) Current activities New and continuing work… +44 1892 667411 - [email protected] Introductions Richard Clark – Working in technical standardisation since early 70’s – Fax, email, character coding (8859-1 is basis of HTML), image coding, multimedia – Elysium, set up in ’91 as SME innovator on the Web – Currently looks after JPEG web site, historical archive, some PR, some standards as editor (extensions to JPEG, JPEG-LS, MIME type RFC and software reference for JPEG 2000), HD Photo in JPEG, and the UK MPEG and JPEG committees – Plus some work that is actually funded……. +44 1892 667411 - [email protected] Elysium in Europe ACTS project – SPEAR – advanced JPEG tools ESPRIT project – Eurostill – consensus building on JPEG 2000 IST – Migrator 2000 – tool migration and feature exploitation of JPEG 2000 – 2KAN – JPEG 2000 advanced networking Plus some other involvement through CEN in cultural heritage and medical imaging, Interreg and others +44 1892 667411 - [email protected] 25 years of standards JPEG – Joint Photographic Experts Group, joint venture between ISO and CCITT (now ITU-T) Evolved from photo-videotex, character coding First meeting March 83 – JPEG proper started in July 86. 42nd meeting in Lausanne, next week… Attendance through national -
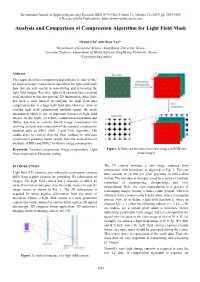
Analysis and Comparison of Compression Algorithm for Light Field Mask
International Journal of Applied Engineering Research ISSN 0973-4562 Volume 12, Number 12 (2017) pp. 3553-3556 © Research India Publications. http://www.ripublication.com Analysis and Comparison of Compression Algorithm for Light Field Mask Hyunji Cho1 and Hoon Yoo2* 1Department of Computer Science, SangMyung University, Korea. 2Associate Professor, Department of Media Software SangMyung University, Korea. *Corresponding author Abstract This paper describes comparison and analysis of state-of-the- art lossless image compression algorithms for light field mask data that are very useful in transmitting and refocusing the light field images. Recently, light field cameras have received wide attention in that they provide 3D information. Also, there has been a wide interest in studying the light field data compression due to a huge light field data. However, most of existing light field compression methods ignore the mask information which is one of important features of light field images. In this paper, we reports compression algorithms and further use this to achieve binary image compression by realizing analysis and comparison of the standard compression methods such as JBIG, JBIG 2 and PNG algorithm. The results seem to confirm that the PNG method for text data compression provides better results than the state-of-the-art methods of JBIG and JBIG2 for binary image compression. Keywords: Lossless compression, Image compression, Light Figure. 2. Basic architecture from raw images to RGB and filed compression, Plenoptic coding mask images INTRODUCTION The LF camera provides a raw image captured from photosensor with microlens, as depicted in Fig. 1. The raw Light field (LF) cameras, also referred to as plenoptic cameras, data consists of 10 bits per pixel precision in little-endian differ from regular cameras by providing 3D information of format. -

PDF Image JBIG2 Compression and Decompression with JBIG2 Encoding and Decoding SDK Library | 1
PDF image JBIG2 compression and decompression with JBIG2 encoding and decoding SDK library | 1 JBIG2 is an image compression standard for bi-level images developed by the Joint bi-level Image Expert Group. It is suitable for lossless compression and lossy compression. According to the group’s press release, in its lossless mode, JBIG2 usually generates files that are one- third to one-fifth the size of the fax group 4 and twice the size of JBIG, which was previously released by the group. The double-layer compression standard. JBIG2 was released as an international standard ITU in 2000. JBIG2 compression JBIG2 is an international standard for bi-level image compression. By segmenting the image into overlapping and/or non-overlapping areas of text, halftones and general content, compression techniques optimized for each content type are used: *Text area: The text area is composed of characters that are well suited for symbol-based encoding methods. Usually, each symbol will correspond to a character bitmap, and a sub-image represents a character or text. For each uppercase and lowercase character used on the front face, there is usually only one character bitmap (or sub-image) in the symbol dictionary. For example, the dictionary will have an “a” bitmap, an “A” bitmap, a “b” bitmap, and so on. VeryUtils.com PDF image JBIG2 compression and decompression with JBIG2 encoding and decoding SDK library | 1 PDF image JBIG2 compression and decompression with JBIG2 encoding and decoding SDK library | 2 *Halftone area: Halftone areas are similar to text areas because they consist of patterns arranged in a regular grid. -
Lossless Image Compression
Lossless Image Compression C.M. Liu Perceptual Signal Processing Lab College of Computer Science National Chiao-Tung University http://www.csie.nctu.edu.tw/~cmliu/Courses/Compression/ Office: EC538 (03)5731877 [email protected] Lossless JPEG (1992) 2 ITU Recommendation T.81 (09/92) Compression based on 8 predictive modes ( “selection values): 0 P(x) = x (no prediction) 1 P(x) = W 2 P(x) = N 3 P(x) = NW NW N 4 P(x) = W + N - NW 5 P(x) = W + ⎣(N-NW)/2⎦ W x 6 P(x) = N + ⎣(W-NW)/2⎦ 7 P(x) = ⎣(W + N)/2⎦ Sequence is then entropy-coded (Huffman/AC) Lossless JPEG (2) 3 Value 0 used for differential coding only in hierarchical mode Values 1, 2, 3 One-dimensional predictors Values 4, 5, 6, 7 Two-dimensional Value 1 (W) Used in the first line of samples At the beginning of each restart Selected predictor used for the other lines Value 2 (N) Used at the start of each line, except first P-1 Default predictor value: 2 At the start of first line Beginning of each restart Lossless JPEG Performance 4 JPEG prediction mode comparisons JPEG vs. GIF vs. PNG Context-Adaptive Lossless Image Compression [Wu 95/96] 5 Two modes: gray-scale & bi-level We are skipping the lossy scheme for now Basic ideas find the best context from the info available to encoder/decoder estimate the presence/lack of horizontal/vertical features CALIC: Initial Prediction 6 if dh−dv > 80 // sharp horizontal edge X* = N else if dv−dh > 80 // sharp vertical edge X* = W else { // assume smoothness first X* = (N+W)/2 +(NE−NW)/4 if dh−dv > 32 // horizontal edge X* = (X*+N)/2 -

Kompresja Statycznego Obrazu 138
Damian Karwowski Zrozumieć Kompresję Obrazu Podstawy Technik Kodowania Stratnego oraz Bezstratnego Obrazów Wydanie Pierwsze, wersja 1.2 Poznań 2019r. ISBN 978-83-953420-0-4 9 788395 342004 © Damian Karwowski – „Zrozumieć Kompresję Obrazu” © Copyright by DAMIAN KARWOWSKI. All rights reserved. Książka jest chroniona prawem autorskim i prawami pokrewnymi. Egzemplarz książki został zdeponowany w Kancelarii Notarialnej. Książka jest dostępna pod adresem: www.zrozumieckompresje.pl ISBN 978-83-953420-0-4 Projekt okładki książki oraz strona internetowa zostały wykonane przez Marka Piskulskiego. Serdecznie dziękuję za profesjonalną pracę Obraz „Miś Panda”, który jest częścią okładki, namalowała na płótnie Natalka Karwowska. Natalko, dziękuję Ci za Twój wysiłek Autor książki dołożył ogromnych starań, żeby zamieszczone w niej informacje były prawdziwe i rzetelnie przedstawione. Korzystając z książki Czytelnik robi to jednak wyłącznie na własną odpowiedzialność. Tym samym autor nie odpowiada za jakiekolwiek szkody, będące następstwem wykorzystania zawartej w książce wiedzy. Autor książki Dr inż. Damian Karwowski. Absolwent Politechniki Poznańskiej. Uzyskał tytuł zawodowy magistra inżyniera oraz stopień doktora nauk technicznych na Politechnice Poznańskiej, odpowiednio w latach 2003 i 2008. Obecnie pracownik naukowo-dydaktyczny na wyżej wymienionej uczelni. Od roku 2003 zawodowo zajmuje się kompresją obrazu. Autor ponad 50 publikacji naukowych o tematyce kompresji i przetwarzania obrazów. Brał udział w licznych projektach naukowych dotyczących wydajnej reprezentacji multimedialnych danych. Dodatkowo członek wielu zespołów badawczych, które w tematyce kompresji obrazu i dźwięku realizowały prace badawczo-wdrożeniowe dla przemysłu. Jego zainteresowania obejmują kompresję danych, techniki kodowania entropijnego danych oraz realizację kodeków obrazu i dźwięku na procesorach x86 oraz DSP. 4 | S t r o n a © Damian Karwowski – „Zrozumieć Kompresję Obrazu” Spis treści Spis treści 5 “Słowo” wstępu 11 Rozdział 1 15 Obraz i jego reprezentacja przestrzenna 15 1.1. -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata -

Enterprise Imaging E-Course Atalasoft's 5 Day Introduction To
ENTERPRISE IMAGING E-COURSE Atalasoft’s 5 Day Introduction to Enterprise Imaging Atalasoft’s Five-Day Imaging e-Course This is part one of five of Atalasoft’s introduction to Enterprise Imaging. This five day course will cover the following topics: 1. Understanding Image Formats 2. Enterprise Imaging on the Web 3. Scanning from the Web 4. Extracting Information from Images 5. Performance Tuning Chapter 1: Understanding Image Formats We’re all somewhat familiar with the common image formats such as JPEG, PNG, and GIF, but there are over a hundred image formats. Many are legacy, but there are still reasons to choose among a dozen or so of the most common ones, depending on your application. There are trade-offs between the various formats and understanding them will allow you to optimize your storage require- ments while still maintaining the highest quality images possible. When trying to figure out which format to pick for a given use, ask the following questions: 1. How are the images originally captured from the imaging device (e.g. scanner, digital camera, medical device)? 2. Are the images in color? If so, is the color important to maintain? 3. Is the image photographic content with rich color, graphic art with few colors, or a black & white text document? 4. What is the DPI and the number of pixels in the image? 5. Do I need a format that can hold multiple images (a multi-page or multi-frame format), such as for a scanned document that I want to keep in a single file? 6. -

An Overview of the JPEG 2000 Still Image Compression
Signal Processing: Image Communication 17 (2002) 3–48 An overview of the JPEG2000 still image compression standard Majid Rabbani*, Rajan Joshi Eastman Kodak Company, Rochester, NY 14650, USA Abstract In 1996, the JPEGcommittee began to investigate possibilities for a new still image compression standard to serve current and future applications. This initiative, which was named JPEG2000, has resulted in a comprehensive standard (ISO 154447ITU-T Recommendation T.800) that is being issued in six parts. Part 1, in the same vein as the JPEG baseline system, is aimed at minimal complexity and maximal interchange and was issued as an International Standard at the end of 2000. Parts 2–6 define extensions to both the compression technology and the file format and are currently in various stages of development. In this paper, a technical description of Part 1 of the JPEG2000 standard is provided, and the rationale behind the selected technologies is explained. Although the JPEG2000 standard only specifies the decoder and the codesteam syntax, the discussion will span both encoder and decoder issues to provide a better understanding of the standard in various applications. r 2002 Elsevier Science B.V. All rights reserved. Keywords: JPEG2000; Image compression; Image coding; Wavelet compression 1. Introduction and background select various elements to satisfy particular re- quirements. This toolkit includes the following The Joint Photographic Experts Group (JPEG) components: (i) the JPEGbaseline system, which committee was formed in 1986 under the joint is a simple and efficient discrete cosine transform auspices of ISO and ITU-T1 and was chartered (DCT)-based lossy compression algorithm that with the ‘‘digital compression and coding of uses Huffman coding, operates only in sequential continuous-tone still images’’. -

Still Image Compression Standards
Still Image Compression Standards Michael W. Hoffman and Khalid Sayood Presented by: Jafar Ajdari Content 5.1 Introduction 5.2 Lossy compression 5.2.1 JPEG 5.2.1.1 DCT-Bsed Image Compression 5.2.1.2 Progressive Transmission 5.2.1.3 General Syntax and Data Ordering 5.2.1.3 Entropy Coding 5.2.2 JPEG2000 5.3 lossless Compression 5.3.1 JPEG 5.3.2 JPEG-LS 5.4 Bilevel Image Compression 5.4.1 JBIG 5.4.2 JBIG2 Definitions of some key terms DCT: Discrete Cosine Transform. JPEG: Joint Photographic Expert Group. JPEG200: the current standard that emphasizes lossy compression of images. JPEG-LS: An upcoming standard that focuses on lossless and near-lossless compression of still images JBIG: Joint Bilevel Image Group. Wavelets: A time-scale decomposition that allow very efficient energy compaction in images. INTRODUCTION What is image compression? Image data can be compressed without significant degradation of the visual (perceptual) quality b/c image contain a high degree of: • Spatial redundancy • Spectral redundancyPsycho-visual redundancy Why Standardization? Compression is one of the technologies that enable the multimedia revolution to occur. However for technology to be effective there has to be some degree of standardization so that the equipment designed by different vendors can talk to each other. Type of still image compression standards: • (JPEG) Joint Photographic Experts Group a- Lossy copression of still images b- Lossless compression of still images • (JBIG) Joint Bilevel Image Group • (GIF) Graphics Interchange Format. de facto • (PNG) Portable Network Graphics. De facto Compression scheme In any compression scheme there are: Step 1- Removal of redundancy based on implicit assumption about the structure in the data Step 2- Assignment of binary codewords to the information deemed nonredundant.