Providing Security and Privacy in Cloud Computing Using Distributed Firewall and VPN
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adaptive Distributed Firewall Using Intrusion Detection Lars Strand
UNIVERSITY OF OSLO Department of Informatics Adaptive distributed firewall using intrusion detection Lars Strand UniK University Graduate Center University of Oslo lars (at) unik no 1. November 2004 ABSTRACT Conventional firewalls rely on a strict outside/inside topology where the gateway(s) enforce some sort of traffic filtering. Some claims that with the evolving connectivity of the Internet, the tradi- tional firewall has been obsolete. High speed links, dynamic topology, end-to-end encryption, threat from internal users are all issues that must be addressed. Steven M. Bellovin was the first to propose a “distributed firewall” that addresses these shortcomings. In this master thesis, the design and implementation of a “distributed firewall” with an intrusion detection mechanism is presented using Python and a scriptable firewall (IPTables, IPFW, netsh). PREFACE This thesis is written as a part of my master degree in Computer Science at the University of Oslo, Department of Informatics. The thesis is written at the Norwegian Defence Research Establishment (FFI). Scripting has been one of my favourite activities since I first learned it. Combined with the art of Computer Security, which I find fascinating and non-exhaustive, it had to be an explosive combina- tion. My problem next was to find someone to supervise me. This is where Professor Hans Petter Langtangen at Simula Research Laboratory and Geir Hallingstad, researcher at FFI, stepped in. Hans Petter Langtangen is a masterful scripting guru and truly deserves the title “Hacker”. Geir Hallingstad is expert in the field of computer/network security and gave valuable input and support when designing this prototype. -

DISTRIBUTED FIREWALL: a WAY of DATA SECURITY in LOCAL AREA NETWORK Satinder1, Vinay2 1Assistant Professor (Extn.), Department of Computer Science, Govt
International Journal of Advance Research In Science And Engineering http://www.ijarse.com IJARSE, Vol. No.4, Special Issue (01), April 2015 ISSN-2319-8354(E) DISTRIBUTED FIREWALL: A WAY OF DATA SECURITY IN LOCAL AREA NETWORK Satinder1, Vinay2 1Assistant Professor (Extn.), Department of Computer Science, Govt. College For Women, Hisar, Haryana, INDIA 2Computer Programmer, Computer Section, College of Basic Sciences & Humanities, CCS HAU, Hisar, Haryana, INDIA ABSTRACT Today, Computer and Internet network are essential part of our life. A number of personal transaction occur every second and computer network are mostly used only for transmission of information rather than processing. So, network security is essentialfor avert hacking of our confidential or important information. Network security can be attained by firewall. Firewall is a system or a group of system that implement a set of security rules to apply access control between two networks to protect inside network from outside network. In Short, we can say that, Firewall is a set of software programming and hardware device to secure host computer. A firewall is typically placed at the extremity of a system and act as filter for an illegitimate traffic. But, Conventional firewalls trust on the notions of restricted topology restriction and controlled entry points to apply traffic filtering.There are some problems for restricting the network topology i.e. End-to-End encryption problems, filtering of some protocols.Distributed firewallprotect from hackers attacks that originate from both the Internet and the internal network.Italso protect the client'scomputer and network's serversfrom unwanted hackers and intrusion.In this paper, we introduce the concept of distributed firewall. -

Data Security Based on Lan Using Distributed Firewall
Jayshri V.Gaud et al, International Journal of Computer Science and Mobile Computing, Vol.3 Issue.3, March- 2014, pg. 386-391 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320–088X IJCSMC, Vol. 3, Issue. 3, March 2014, pg.386 – 391 RESEARCH ARTICLE DATA SECURITY BASED ON LAN USING DISTRIBUTED FIREWALL Jayshri V.Gaud1, Mahip M.Bartere2 ¹Department of Computer Science & Amravati University, India ²Department of Computer Science & Amravati University, India 1 [email protected]; 2 [email protected] Abstract— Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. In most of the systems, the network security is achieved by firewall and acts as a filter for unauthorized traffic. But there are some problems with these traditional firewalls like they rely on the notation of restricted topology and controlled entry points to function. Restricting the network topology, difficulty in filtering of certain protocols, end-to-end encryption problem and few more problems lead to the evolution of Distributed Firewalls. It secures the network by protecting critical network endpoints, exactly where hackers want to penetrate. This paper is a survey paper, dealing with the general concepts such distributed firewalls, its requirements and implications and introduce, its suitability to common threats on the Internet, as well as give a short discussion on contemporary implementations. A distributed firewall gives complete security to the network. -

Distributed Firewall with Dynamic Intrusion Detection Module
International Journal of Advanced Research in Engineering and Technology (IJARET) Volume 12, Issue 4, April 2021, pp. 484-491, Article ID: IJARET_12_04_046 Available online at https://iaeme.com/Home/issue/IJARET?Volume=12&Issue=4 ISSN Print: 0976-6480 and ISSN Online: 0976-6499 DOI: 10.34218/IJARET.12.4.2021.046 © IAEME Publication Scopus Indexed DISTRIBUTED FIREWALL WITH DYNAMIC INTRUSION DETECTION MODULE Dr. Zalte S.S. Department of Computer Science, Shivaji University, Kolhapur, India Patil P.N Department of Computer Science, Vishwakarma College of Arts, Commerce and Science, Pune, India Deshmukh S.N. Department of Computer Science, Vishwakarma College of Arts, Commerce and Science, Pune, India ABSTRACT Computers and Internet, both are becoming an essential part of life. With computer networks we are sharing resources, exchanging information, and number of personal transactions which must be secured from unauthorized access, with Network Security we can prevent and detect unauthorized access. So, we can maintain integrity, confidentiality and accessibility of computer networks. One way to achieve Network Security is FIREWALL. A firewall is a system which monitors and filters traffic and gives entry/ blocks data packets based on a set of security rules. Distributed firewall is introduced to eliminate the problems which are difficult to solved in conventional firewalls. Distributed firewall is not restricted by topology and entry point as conventional firewall. Distributed firewall secure critical network endpoints, it provides unlimited Scalability and overcomes single point of failure problems. In this paper, we have proposed Distributed Firewall with Dynamic Intrusion Detection Module to achieve elevated security to the network. Key words: Network Security, Distributed Firewall, computer networks, Policy, Threats, Intrusion Detection. -

DATA SECURITY in LAN USING DISTRIBUTED FIREWALL Dr.T.Pandikumar1, Mekonnen Gidey2
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395 -0056 Volume: 04 Issue: 05 | May -2017 www.irjet.net p-ISSN: 2395-0072 DATA SECURITY IN LAN USING DISTRIBUTED FIREWALL Dr.T.Pandikumar1, Mekonnen Gidey2 1Associate Professor, Department of Computer & IT, Defence University, Ethiopia 2M.Tech, Department of Computer & IT, Defence University, Ethiopia ---------------------------------------------------------------------***--------------------------------------------------------------------- Abstract - Computers and Networking have become outside world through wide area networks and the inseparable by now. A number of confidential transactions internet. occur every second and today computers are used mostly Traditional firewalls ( Conventional firewalls ) are for transmission rather than processing of data. So devices often placed on the edge of the network that act Network Security is needed to prevent hacking of data and as a bouncer allowing only certain types of traffic in and to provide authenticated data transfer. Distributed out of the network which often called perimeter firewalls secure the network by protecting critical firewalls. They divide the network into two parts; network endpoints, exactly where hackers want to trusted on one side and un-trusted on the other side. penetrate. It filters traffic from both the Internet and the For this reason they depend heavily on the topology of internal network because the most destructive and costly the network. Moreover, firewalls are a mechanism for hacking attacks still originate from within the policy control and permit a site administrator to set a organization. They provide virtually unlimited scalability. policy on external access. Just as file permissions In addition, they overcome the single point-of-failure enforces an internal security policy and can enforces an problem presented by the perimeter firewall. -

Distributed Perimeter Firewall Policy Management Framework
DISTRIBUTED PERIMETER FIREWALL POLICY MANAGEMENT FRAMEWORK A DISSERTATION IN Computer Science and Telecommunications and Computer Networking Presented to the Faculty of the University of Missouri-Kansas City in partial fulfillment of the requirements for the degree DOCTOR OF PHILOSOPHY by MAHESH NATH MADDUMALA M.Tech., Andhra University, India, 2007 B.Tech., M.L.Engineering College, India, 2004 Kansas City, Missouri 2017 © 2017 MAHESH NATH MADDUMALA ALL RIGHTS RESERVED DISTRIBUTED PERIMETER FIREWALL POLICY MANAGEMENT FRAMEWORK Mahesh Nath Maddumala, Candidate for the Doctor of Philosophy Degree University of Missouri-Kansas City, 2017 ABSTRACT A perimeter firewall is the first line of defense that stops unwanted packets (based on defined firewall policies) entering the organization that deploys it. In the real world, every organization maintains a perimeter firewall between internet (which could be untrusted) and its own network (private network). In addition, organizations maintain internal firewalls to safeguard individual departments and data center servers based on various security and privacy requirements. In general, if we consider firewall setup in multinational organization's network environment, every branch has perimeter firewall and a set of internal firewalls. Every branch has its own security policies defined based on its specific security requirements, type of information, information processing systems, location-based compliance requirements, etc. As the branches of the multinational organizations span across the globe, managing the policies at every branch and ensuring the compliance and consistency of security policies are quite complex. Any misconfiguration of firewall policies even at a single branch may pose risk to the overall organization in terms of financial loss and reputation. -

A Stateful CSG-Based Distributed Firewall Architecture for Robust Distributed Security
A Stateful CSG-based Distributed Firewall Architecture for Robust Distributed Security V. Ramsurrun, and K. M. S. Soyjaudah Electrical & Electronic Engineering Department University of Mauritius (UoM) Réduit, Mauritius [email protected], [email protected] Abstract —Distributed firewalls have been developed in order to is provided at the very cluster level, the whole of the network provide networks with a higher level of protection than will become more secure as we can reduce the occurrence of traditional firewalling mechanisms like gateway and host-based both insider & external attacks, and limit their spread & effects firewalls. Although distributed firewalls provide higher security, more readily. A 2-active-node stateful CSG is used for they too have limitations. This work presents the design & protecting each end-user cluster in our working prototype. implementation of a new distributed firewall model, based on In this paper, we perform the following: stateful Cluster Security Gateway (CSG) architecture, which addresses those shortcomings. This distributed security model 1. Review of the strengths & limitations of distributed adopts a bottom-up approach such that each cluster of end-user firewalls. hosts is first secured using the CSG architecture. These different 2. Use of the stateful CSG to implement a new robust CSGs are then centrally managed by the Network Administrator. distributed firewall model. A file-based firewall update mechanism is used for dynamic real- time security. IPsec is used to secure the firewall policy update 3. Qualitative comparison of its strengths & weaknesses distribution while X.509 certificates cater for sender/receiver with other major software-based & hardware-based authentication. The major benefits of this approach to distributed distributed firewall architectures available. -
Network Firewalls (Pdf)
Network Firewalls Kenneth Ingham Stephanie Forrest [email protected] [email protected] University of New Mexico University of New Mexico Santa Fe Institute Department of Computer Science Department of Computer Science 1399 Hyde Park Road MSC01 1130 MSC01 1130 Santa Fe, NM 87501 1 University of New Mexico 1 University of New Mexico Albuquerque, NM 87131-0001 Albuquerque, NM 87131-0001 Contents 1 Introduction 3 2 The Need for Firewalls 7 3 Firewall architectures 9 3.1 Packet filtering . 10 3.1.1 Packet Filtering with State . 11 3.1.2 Improving Packet Filter Specification . 12 3.2 Proxies . 15 4 Firewalls at various ISO network levels 17 4.1 Physical layer . 17 4.2 Data link layer . 18 4.2.1 Filtering on MAC address . 18 4.2.2 Bridging firewalls . 19 4.3 Network . 19 1 4.4 Network- and host-based filtering . 20 4.4.1 Multicast . 20 4.4.2 Network Address Translation . 22 4.5 Transport . 23 4.6 Presentation . 23 4.7 Application . 24 5 Other approaches 24 5.1 Distributed Firewalls . 25 5.2 Dynamic firewalls . 26 5.3 Normalization . 26 5.4 Signature-based Firewalls . 27 5.5 Transient Addressing . 27 6 Firewall Testing 28 7 What firewalls do not protect against 29 7.1 Data Which Passes Through the Firewall . 29 7.2 Servers on the DMZ . 31 7.3 Insider Attacks . 31 8 Future Challenges for Firewalls 32 8.1 VPNs . 32 8.2 Peer-to-peer Networking . 32 8.3 HTTP as a “universal transport protocol” . 33 9 Conclusion 33 2 Abstract Firewalls are network devices that enforce an organization’s security policy. -

Secure Virtual Network Configuration for Virtual Machine (VM) Protection
NIST Special Publication 800-125B Secure Virtual Network Configuration for Virtual Machine (VM) Protection Ramaswamy Chandramouli This publication is available free of charge from: http://dx.doi.org/10.6028/NIST.SP.800-125B C O M P U T E R S E C U R I T Y NIST Special Publication 800-125B Secure Virtual Network Configuration for Virtual Machine (VM) Protection Ramaswamy Chandramouli Computer Security Division Information Technology Laboratory This publication is available free of charge from: http://dx.doi.org/10.6028/NIST.SP.800-125B March 2016 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Willie May, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3541 et seq., Public Law (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on federal agencies by the Secretary of Commerce under statutory authority. Nor should these guidelines be interpreted as altering or superseding the existing authorities of the Secretary of Commerce, Director of the OMB, or any other federal official. -

Security and Compliance Configuration for Vmware Cloud Foundation
Security and Compliance Configuration for VMware Cloud Foundation Modified on 11 MAY 2021 VMware Cloud Foundation 4.2 Security and Compliance Configuration for VMware Cloud Foundation You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2021 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents About Security and Compliance Configuration for VMware Cloud Foundation 4 1 Software Requirements 6 2 Securing ESXi Hosts 8 Security Best Practices for Securing ESXi Hosts 8 Configure Multiple Security Settings on the ESXi Hosts by Using PowerCLI 9 Configure Multiple Security Settings on the ESXi Hosts by Using an SSH Client 11 Enable Normal Lockdown Mode on the ESXi Hosts 12 3 Securing vCenter Server 14 Security Best Practices for Securing vCenter Server 14 Configure Security Settings for vCenter Server from the vSphere Client 15 Configure Security Settings for vCenter Server by Using PowerCLI 19 Configure Security Settings for vCenter Server by Using an SSH Client 19 Configure Security Settings on the vCenter Server Appliance 20 4 Securing SDDC Manager 22 5 Securing Management Virtual Machines 24 6 Securing vSAN 27 Security Best practices for Securing vSAN 27 Configure a Proxy Server for vSAN from the vSphere Client 27 Configure vSAN Data-At-Rest Encryption from the vSphere Client 28 7 Securing NSX-T Data Center 29 Security Best Practices for Securing NSX-T Data Center 29 Configure Security Settings for NSX-T Data Center from User Interfaces 35 Configure Security Settings for NSX-T Data Center by Using CLI Commands 36 8 Security Configurations Not Applicable or Not Compatible with VMware Cloud Foundation 38 VMware, Inc. -
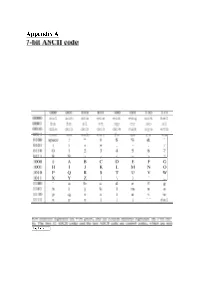
7-Bit ASCII Code
Appendix A 7-bit ASCII code 000 001 010 011 100 101 110 111 0000 nul soh stx etx eat enq ack bel 0001 bs ht nl vt np cr so si 0010 dIe del de2 dc3 dc4 nak syn etb VVll can em SUD esc LS gs rs us , 0100 space ! " # $ % & 0101 () * + , - / 0110 0 1 2 3 4 5 6 7 0111 8 9 : ; < = > ? 1000 @ A B C 0 E F G 1001 HI J KLM N 0 1010 P Q R S T U V W A - 1011 XYZ [ \ ] , -- 1100 a b c d e f g 1101 h i j k 1 ill n 0 1110 P q r s t u v w -- 1111 x y z { I ) del Row numbers represent the 4-bit prefix, and the column numbers represent the 3-bit suf fix. The first 32 ASCII codes and the last ASCII code are control codes, whIch are not displayable. Appendix B SMA-512 Constants (in hexadecimal) i Ki i Ki i Ki 0 428a2f98d728ae22 1 7137449123ef65cd 2 b5cOfbcfec4d3b2f ':l ,~Q1 o o--u-a-, A -v rv c v- _0C r-'~Qh~-'Q r:; ~Qf'11 f'1hhn~r1n1Q 6 923f82a4afl94f9b 7 ablc5ed5da6d8118 8 d807aa98a3030242 9 12835b0145706fbe 10 243185be4ee4b28c 11 550c7dc3d5ffb4e2 12 72be5d74f27b896f 13 80deblfe3b1696bl 14 9bdc06a725c71235 15 c19bfl74cf692694 16 e49b69c1gef14ad2 17 efbe4786384f25e3 18 Ofc19dc68b8cd5b5 19 240calcc77ac9c65 20 2de92c6f592b0275 21 4a7484aa6ea6e483 22 5cbOa9dcbd41fbd4 23 76f988da831153b5 24 983e5152ee66dfab 25 a831c66d2db43210 26 b00327c898fb213f 27 bf597fc7beefOee4 28 c6eOObf33da88fc2 29 d5a7914793 Oaa 725 30 06ca6351e003826f 31 142929670aOe6e70 32 27b70a8546d22ffc 33 2elb21385c26c926 34 4d2c6dfc5ac42aed 35 53380d139d95b3df 36 650a73548baf63de 37 766aOabb3c77b2a8 38 81c2c92e47edaee6 39 92 722c851482353b 40 a2bfe8a14cfl 0364 41 a81a664bbc423001 42 c24b8b70dOf89791 -

Data Security in Local Network Using Distributed Firewall
DATA SECURITY IN LOCAL NETWORK USING DISTRIBUTED FIREWALL A SEMINAR REPORT Submitted by ANAND KUMAR in partial fulfillment of requirement of the Degree of Bachelor of Technology (B.Tech) IN COMPUTER SCIENCE AND ENGINEERING SCHOOL OF ENGINEERING COCHIN UNIVERSITY OF SCIENCE AND TECHNOLOGY KOCHI- 682022 AUGUST 2008 DIVISION OF COMPUTER SCIENCE AND ENGINEERING SCHOOL OF ENGINEERING COCHIN UNIVERSITY OF SCIENCE AND TECHNOLOGY KOCHI-682022 Certificat e Certified that this is a bonafide record of the seminar entitled “DATA SECURITY IN LOCAL NETWORK USING DISTRIBUTED FIREWALL ” presented by the following student ANAND KUMAR of the VII semester, Computer Science and Engineering in the year 2008 in partial fulfillment of the requirements in the award of Degree of Bachelor of Technology in Computer Science and Engineering of Cochin University of Science and Technology. Ms. Latha R. Nair. Dr. David Peter S. Seminar Guide Head of Division Date : Acknowledgement Many people have contributed to the success of this. Although a single sentence hardly suffices, I would like to thank Almighty God for blessing us with His grace. I extend my sincere and heart felt thanks to Dr. David Peter, Head of Department, Computer Science and Engineering, for providing us the right ambience for carrying out this work. I am profoundly indebted to my seminar guide, Ms. Latha R. Nair for innumerable acts of timely advice, encouragement and I sincerely express my gratitude to her. I express my immense pleasure and thankfulness to all the teachers and staff of the Department of Computer Science and Engineering, CUSAT for their cooperation and support. Last but not the least, I thank all others, and especially my classmates who in one way or another helped me in the successful completion of this work.