Exploring the Jolla Phone
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Survey on Architectures of Mobile Operating Systems: Challenges and Issues
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 3, March 2015, PP 73-76 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org A Survey on Architectures of Mobile Operating Systems: Challenges and Issues Prof. Y. K. Sundara Krishna1 HOD, Dept. of Computer Science, Krishna University Mr. G K Mohan Devarakonda2 Research Scholar, Krishna University Abstract: In the early years of mobile evolution, Discontinued Platforms Current mobile devices are enabled only with voice services Platforms that allow the users to communicate with each other. Symbian OS Android But now a days, the mobile technology undergone Palm OS IOS various changes to a great extent so that the devices Maemo OS Windows Phone allows the users not only to communicate but also to Meego OS Firefox OS attain a variety of services such as video calls, faster Black Berry OS browsing services,2d and 3d games, Camera, 2.1 Symbian OS: This Operating system was Banking Services, GPS services, File sharing developed by NOKIA. services, Tracking Services, M-Commerce and so many. The changes in mobile technology may be due Architecture: to Operating System or Hardware or Network or Memory. This paper presents a survey on evolutions SYMBIAN OS GUI Library in mobile developments especially on mobile operating system Architectures, challenges and Issues in various mobile operating Systems. Application Engines JAVA VM 1. INTRODUCTION Servers (Operating System Services) A Mobile operating system is a System Software that is specifically designed to run on handheld devices Symbian OS Base (File Server, Kernel) such as Mobile Phones, PDA’s. -

Mobile Platform Security Architectures: Software
Lecture 3 MOBILE SOFTWARE PLATFORM SECURITY You will be learning: . General model for mobile platform security Key security techniques and general architecture . Comparison of four systems Android, iOS, MeeGo (MSSF), Symbian 2 Mobile platforms revisited . Android ~2007 . Java ME ~2001 “feature phones”: 3 billion devices! Not in smartphone platforms . Symbian ~2004 First “smartphone” OS 3 Mobile platforms revisited . iOS ~2007 iP* devices; BSD-based . MeeGo ~2010 Linux-based MSSF (security architecture) . Windows Phone ~2010 . ... 4 Symbian . First widely deployed smartphone OS EPOC OS for Psion devices (1990s) . Microkernel architecture: OS components as user space services Accessed via Inter-process communication (IPC) 5 Symbian Platform Security . Introduced in ~2004 . Apps distributed via Nokia Store Sideloading supported . Permissions are called ‘capabilities’, fixed set (21) 4 Groups: User, System, Restricted, Manufacturer 6 Symbian Platform Security . Applications identified by: UID from protected range, based on trusted code signature Or UID picked by developer from unprotected range Optionally, vendor ID (VID), based on trusted code signature 7 Apple iOS . Native application development in Objective C Web applications on Webkit . Based on Darwin + TrustedBSD kernel extension TrustedBSD implements Mandatory Access Control Darwin also used in Mac OS X 8 iOS Platform Security . Apps distributed via iTunes App Store . One centralized signature authority Apple software vs. third party software . Runtime protection All third-party software sandboxed with same profile Permissions: ”entitlements” (post iOS 6) Contextual permission prompts: e.g. location 9 MeeGo . Linux-based open source OS, Intel, Nokia, Linux Foundation Evolved from Maemo and Moblin . Application development in Qt/C++ . Partially buried, but lives on Linux Foundation shifted to HTML5- based Tizen MeeGo -> Mer -> Jolla’s Sailfish OS 10 MeeGo Platform Security . -

Qml Controls from Scratch
CREATING QML CONTROLS FROM SCRATCH Chris Cortopassi Table of Contents Introduction ......................................................................................... 3 Part 0: Getting Started ......................................................................... 4 Part 1: Button ....................................................................................... 6 Part 2: CheckBox and RadioButton ...................................................... 8 Part 3: Switch ...................................................................................... 10 Part 4: Slider ........................................................................................ 12 Part 5: ScrollBar ................................................................................... 14 Part 6: ProgressBar.............................................................................. 15 Part 7: Spinner ..................................................................................... 16 Part 8: Dialog ....................................................................................... 17 Part 9: PageDots .................................................................................. 19 Part 10: Tabs ....................................................................................... 21 Part 11: Table ...................................................................................... 23 Part 12: TimePicker ............................................................................. 25 Part 13: DatePicker ............................................................................. -

Lamadrid Android
ANDROID FGSDFG FDDFGDF ANTITRUST Android antitrust investigation DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET ANDROID FGSDFG FDDFGDF ANTITRUST Android antitrust investigation DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET ANDROID FGSDFG FDDFGDF ANTITRUST Android antitrust investigation DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET ANDROID THOUGHTS IN BRIEF: FGSDFG FDDFGDF(i) A quick overview of the facts (ii) Business considerations and ANTITRUSTbackground DOMINANT(iii)The POSITION Law : (I) Dominance mokmdokamsdfkmasodmkfosakdmfosdkmf(iv)The Law: (II) Predatory okmsadf allegations IT MARKET(v) The Law: (III) Bundling allegations ANDROID FGSDFG THE FACTS FDDFGDF ANTITRUST DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET • AndroidANDROID is an open source OS licensed on a royalty-free basis. Licensees remain free to do whatever they wish with the code (e.g. downloading,FGSDFG distributing or modifying –forking- it). • OEMs remain free to use Android with or without Google Apps (e.g. NokiaFDDFGDF X). • WhenANTITRUST OEMs wish to offer certain Google apps on top of Android they can enter into a MADA which requires them to (i) preload a minimum set ofDOMINANT apps (GMS); POSITION (ii) place Search widget and GooglePlay icons in a certain way; and (iii) use Google Search as default engine for the searchmokmdokamsdfkmasodmkfosakdmfosdkmf intent. okmsadf • OEMs (and users) remain at all times free to pre-install at any time any nonIT MARKET-Google app (including a non-Google App Store) = no Google walled garden (room for intra-ecosystem competition) ANDROID A MATTER OF DIFFERENT FGSDFG FDDFGDFBUSINESS MODELS ANTITRUST DOMINANT POSITION mokmdokamsdfkmasodmkfosakdmfosdkmf okmsadf IT MARKET EssentiallyANDROID 3 different business models for mobile operating systems (OSs): i. Apple’s vertically integrated model - Monetization via sales of devices. -

Meego Smartphones and Operating System Find a New Life in Jolla Ltd
Jolla Ltd. Press Release July 7, 2012 Helsinki, Finland FOR IMMEDIATE RELEASE MeeGo Smartphones and Operating System Find a New Life in Jolla Ltd. Jolla Ltd. is an independent Finland based smartphone product company which continues the excellent work that Nokia started with MeeGo. The Jolla team is formed by directors and core professionals from Nokia's MeeGo N9 organisation, together with some of the best minds working on MeeGo in the communities. Jussi Hurmola, CEO Jolla Ltd.: "Nokia created something wonderful - the world's best smartphone product. It deserves to be continued, and we will do that together with all the bright and gifted people contributing to the MeeGo success story." Jolla Ltd. will design, develop and sell new MeeGo based smartphones. Together with international private investors and partners, a new smartphone using this MeeGo based OS will be revealed later this year. Jolla Ltd. has been developing a new smartphone product and the OS since the end of 2011. The OS has evolved from MeeGo OS using Mer Core and Qt with Jolla technology including its own brand new UI. The Jolla team consists of a substantial number of MeeGo's core engineers and directors, and is aggressively hiring the top MeeGo and Linux talent to contribute to the next generation smartphone production. Company is headquartered in Helsinki, Finland and has an R&D office in Tampere, Finland. Sincerely, Jolla Ltd. Dr. Antti Saarnio - Chairman & Finance Mr. Jussi Hurmola - CEO Mr. Sami Pienimäki - VP, Sales & Business Development Mr. Stefano Mosconi - CIO Mr. Marc Dillon - COO Further inquiries: [email protected] Jolla Ltd. -

ECE 471 – Embedded Systems Lecture 8
ECE 471 { Embedded Systems Lecture 8 Vince Weaver http://www.eece.maine.edu/∼vweaver [email protected] 26 September 2013 Announcements • HW#2 is delayed • Read chapter 11 in textbook 1 Brief Overview of the Gumstix Overo Board TODO: Put a diagram here More details after boards are distributed. 2 Coding Directly for the Hardware One way of developing embedded systems is coding to the raw hardware, as you did with the STM Discovery Boards in ECE271. • Compile code • Prepare for upload (hexbin?) • Upload into FLASH • Boots to offset 3 • Setup, flat memory (usually), stack at top, code near bottom, IRQ vectors • Handle Interrupts • Must do I/O directly (no drivers) Although if lucky, can find existing code. 4 Instead, one can use an Operating System 5 Why Use an Operating System? • Provides Layers of Abstraction { Abstract hardware: hide hardware differences. same hardware interface for classes of hardware (things like video cameras, disks, keyboards, etc) despite differing implementation details { Abstract software: with VM get linear address space, same system calls on all systems { Abstraction comes at a cost. Higher overhead, unknown timing 6 • Multi-tasking / Multi-user • Security, permissions (Linus dial out onto /dev/hda) • Common code in kernel and libraries, no need to re- invent 7 What's included with an OS • kernel / drivers { Linux definition • also system libraries { Solaris definition • low-level utils / software / GUI { Windows definition Web Browser included? • Linux usually makes distinction between the OS Kernel and distribution. OSX/Windows usually doesn't. 8 Operating Systems Types • Monolithic kernel { everything in one big address space. -

Mobile Linux Mojo the XYZ of Mobile Tlas PDQ!
Mobile Linux Mojo The XYZ of Mobile TLAs PDQ! Bill Weinberg January 29, 2009 Copyright © 2009 Bill Weinberg, LinuxPundit,com Alphabet Soup . Too many TLAs – Non-profits – Commercial Entities – Tool Kits – Standards . ORG Typology – Standards Bodies – Implementation Consortia – Hybrids MIPS and Open Source Copyright © 2008 Bill Weinberg, LinuxPundit,com Page: 2 The Big Four . Ahem, Now Three . OHA - Open Handset Alliance – Founded by Google, together with Sprint, TIM, Motorola, et al. – Performs/support development of Android platform . LiMo Foundation – Orig. Motorola, NEC, NTT, Panasonic, Samsung, Vodaphone – Goal of created shared, open middleware mobile OS . LiPS - Linux Phone Standards Forum – Founded by France Telecom/Orange, ACCESS et al. – Worked to create standards for Linux-based telephony m/w – Merged with LiMo Foundation in June 2008 . Moblin - Mobile Linux – Founded by Intel, (initially) targeting Intel Atom CPUs – Platform / distribution to support MIDs, Nettops, UMPC MIPS and Open Source Copyright © 2008 Bill Weinberg, LinuxPundit,com Page: 3 LiMo and Android . Android is a complete mobile stack LiMo is a platform for enabling that includes applications applications and services Android, as Free Software, should LiMo membership represents appeal to Tier II/III OEMs and Tier I OEMs, ISVs and operators ODMs, who lack resources LiMo aims to leave Android strives to be “room for differentiation” a stylish phone stack LiMo presents Linux-native APIs Android is based on Dalvik, a Java work-alike The LiMo SDK has/will have compliance test suites OHA has a “non Fragmentation” pledge MIPS and Open Source Copyright © 2008 Bill Weinberg, LinuxPundit,com Page: 4 And a whole lot more . -

Linux Foundation to Host Meego Workgroup
Linux Foundation To Host MeeGo Workgroup New Open Source Software Platform Backed by Intel and Nokia will Power the Next Generation of Computing Devices SAN FRANCISCO, February 15, 2010 – The Linux Foundation, the nonprofit organization dedicated to accelerating the growth of Linux, today announced it will host the MeeGo project, the open source software platform for the next generation of computing devices. MeeGo combines Intel’s Moblin™ and Nokia’s Maemo projects into one Linux-based platform. MeeGo, announced today in a joint release by Intel and Nokia, will be deployed across many computing device types - including pocketable mobile computers, netbooks, tablets, mediaphones, connected TVs and in-vehicle infotainment systems, and brings together the leaders in computing and mobile communications as the project’s backers. MeeGo is designed for cross-device, cross-architecture computing and is built from the ground up for a new class of powerful computing devices. The workgroup will be hosted by the Linux Foundation as a fully open source project, encouraging community contributions in line with the best practices of the open source development model. The Linux Foundation expects MeeGo to be adopted widely by device manufacturers, network operators, software vendors and developers across multiple device types and for many organizations and developers to participate in the workgroup. “With MeeGo, you have the world’s leader in computing – Intel – uniting with the world’s leader in communications – Nokia – in a true open source project hosted at the Linux Foundation,” said Jim Zemlin, executive director at the Linux Foundation. “MeeGo has been built from the ground up for rich, mobile devices and will deliver choice to consumers without lock-in. -
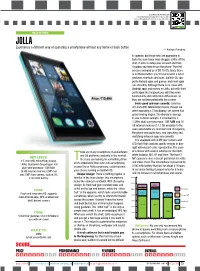
Overall Features Performance Price
Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE JOLLA Experience a different way of operating a smartphone without any home or back button — Ashok Pandey to operate, but those who are upgrading to taste the new flavor may struggle a little. At the start, it asks to setup your account and then, it guides you how to use the phone. The first screen reminded us of BB 10 OS. Since there is no Home button, you’ll have to learn a lot of gestures, shortcuts and cues. Sailfish OS sup- ports Android apps and games, and most apps run smoothly. Although there is no issue with Android apps and games on Jolla, but with third party apps like facebook you will find some functionality and notification differences, as Price: `15,490 they are not integrated with the system. Feels good and runs smooth: Jolla has 4.5-inch qHD (960x450p) display, though we were expecting a 720p display, yet screen has good viewing angles. The display is average to use in direct sunlight. It is backed by a 1.4GHz dual-core processor, 1GB RAM and 16 GB internal memory (13.7 GB available to the user) expandable via microSD card. Navigating the phone was quite easy, and launching and switching between apps was smooth. It is equipped with 8 MP rear camera with LED flash that captures quality images in day- light with decent color reproduction. The cam- here are many smartphone manufacturers era comes with several settings for the flash, and OS platforms available in the market. -

Sailfish OS Interview Questions and Answers Guide
Sailfish OS Interview Questions And Answers Guide. Global Guideline. https://www.globalguideline.com/ Sailfish OS Interview Questions And Answers Global Guideline . COM Sailfish OS Job Interview Preparation Guide. Question # 1 Tell us what you know about Sailfish OS? Answer:- Sailfish is a Linux-based mobile operating system developed by Jolla in cooperation with the Mer project and supported by the Sailfish Alliance. It is to be used in upcoming smartphones by Jolla and other licencees. Although it is primarily targeted at mobile phones, it is also intended to support other categories of devices. Read More Answers. Question # 2 Explain Sailfish OS Components? Answer:- Jolla has revealed its plans to use the following technologies in Sailfish OS: The Mer software distribution core A custom built user interface HTML5 QML and Qt Read More Answers. Question # 3 Do you know about Sailfish OS software availability? Answer:- Sailfish will be able to run most applications that were originally developed for MeeGo and Android, in addition to native Sailfish applications. This will give it a large catalogue of available apps on launch. Considering upon Jolla's declarations that Sailfish OS is be able to use software from following platforms Sailfish (natively created + ported like from Qt, Symbian, MeeGo - developers have reported that porting a Qt written software with Sailfish SDK takes a few hours only) Android applications are directly running in Sailfish OS. They are compatible as they are in third-party Android stores, with no needed modification (in most cases). MeeGo (because of backward compatibility thanks to MeeGo code legacy included in the Mer core) Unix and Linux (as Sailfish is Linux then using such a software is possible, especially RPM packages, either in terminal/console mode or with limitations implying from using Sailfish UI, if not ported and adjusted) HTML5 Read More Answers. -

Mer: Core OS Mobile & Devices
Mer: Core OS mobile & devices Qt Developer Days - Silicon Valley 2012 Carl Symons Introduction Plasma Active chooses Mer Not just another Linux distribution Focus - device providers Where's Mer? SDKs - apps & platform Get Mer Resources Carl Symons Large company Mktg/BusDev Start-ups } Slightly geeky Grassroots LinuxFest organizer KDE News editor/promo KDE Plasma Active Mer upstream and downstream First LinuxCon September 2009 Portland Moblin is a hot topic Moblin 2.1 for phones introduced MeeGo Announced February 201 0 Moblin & Maemo merger Support for Intel Atom Desktop Summit August 11 , 2011 Berlin; Free Desktop meeting Developer orientation; ExoPCs MeeGo AppStore A real Linux OS LinuxCon - Vancouver August 1 8, 2011 Intel AppUp Developer orientation; ExoPCs MeeGo AppStore show real Linux OS; possibilities Intel AppUp Elements September 28, 2011 National developer conference Tizen announced (led by Intel and Samsung) MeeGo and Qt abandoned HTML5/CSS3 Maemo Reconstructed October 3, 2011 Mer announced The spirit of MeeGo lives on Plasma Active chooses Mer October 5, 2011 No viable alternative Lightweight Mer talent and community Performant Boot time - more than a minute to about 1 5 seconds on Atom tablet Not just another Linux MeeGo - large company dominated; closed governance Mer - Core OS only Packages Focus - Device Providers Complete world class platform for building commercial products Modern, clean Linux Easy to try; easy to port Systems, structures, processes, code to serve device providers Where's Mer? X86, ARM, MIPS NemoMobile -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily.