Decision Matrix: Selecting an Application Lifecycle Management Vendor
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

List of New Applications Added in ARL #2603
List of New Applications Added in ARL #2603 Application Name Publisher DataConnect 11.5 Actian Source Sans Pro 1.0 Adobe PDF Broker Process for Internet Explorer 21.1 Adobe Creative Suite CS6 Standard Adobe Collaboration Synchronizer 20.1 Adobe Collaboration Synchronizer 21.1 Adobe Connect 2020.12 Adobe AD Group Manager 1.1 Albus Bit AD Group Manager 1.2 Albus Bit Query Reporter 3.3 Allround Automations Monarch 13.0 Classic Altair Engineering IMAGEPro 1.1 AMETEK CrystalControl 2.1 AMETEK NekoHTML 1.9 Andy Clark Sherlock 6.2 Ansys Flash Banner Maker 1.0 Anvsoft Any Video Converter 5.5 Anvsoft TomeePlus 9.0 Apache Software Foundation Falcon 0.1 Apache Software Foundation JaxMe 0.5 Apache Software Foundation A-PDF Split A-PDF.com WealthTrack 9.0 Applied Systems Call Status Report 1.0 Aspect Software Inbound 7.3 Aspect Software CLIQ Web Manager 9.2 ASSA ABLOY CLIQ Web Manager 8.0 ASSA ABLOY Centerprise Data Integrator 7.6 Astera Software Bitbucket 2.0 Atlassian Jira Capture Chrome 1.0 Atlassian AudaEnterprise 4.0 Audatex Encode And Decode Files - Base64 1.0 Automation Anywhere Expert PDF 14.0 Avanquest Software ASG Plugin Avaya Discovery Tool 3.3 AvePoint DocAve 6.6 AvePoint DocAve 6.12 AvePoint DocAve 6.11 AvePoint DocAve 6.3 AvePoint DocAve 6.8 AvePoint DocAve 6.9 AvePoint FLY 4.5 AvePoint Wonderware Application Server Client 2020 AVEVA Group Cloud for Business On-Premises 2.0 Axure Software Solutions Automator 4.5 Axway Convene 5.8 Azeus Zulu 8.50 Azul Systems Zulu 11.35 Azul Systems Zulu 8.48 Azul Systems Zulu 15.28 Azul Systems Zulu -

Altova Umodel 2012 User & Reference Manual
User and Reference Manual Altova UModel 2012 User & Reference Manual All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Published: 2012 © 2012 Altova GmbH UML®, OMG™, Object Management Group™, and Unified Modeling Language™ are either registered trademarks or trademarks of Object Management Group, Inc. in the United States and/or other countries. Table of Contents 1 UModel 3 2 Introducing UModel 6 3 What's new in UModel 8 4 UModel tutorial 14 4.1 Starting UModel................................................................................................................. 16 4.2 Use cases ................................................................................................................ -

Code Review Is an Architectural Necessity
Code review is an architectural necessity Colin Dean @colindean 1 @ColinDean Software Engineer Organizer, Abstractions.io Wearer of many hats 2 My words are my own and not my employer(s), past or present. Please save questions until the end of the presentation. 3 Agenda • Quick anecdote • What is code review? • What problems does code review solve? • Quality attributes code review ensures • Tips for code reviews • Limitations 4 5 Agenda • Quick anecdote • What is code review? • What problems do code review solve? • Quality attributes code review ensures • Tips for code reviews • Limitations 6 What is code review? 7 Code review is the process by which those who maintain a software codebase evaluate a proposed change to that codebase, regardless of the source of the proposed change. 8 Code review is systematic examination of computer source code. Code Review, Wikipedia 9 Peer Review 10 Code Review 11 Code Review Vocabulary • Change - an individual unit of work altering what exists • Submission - a collection of changes • Submitter - the person proposing the submission • Reviewer - the people evaluating the submission • Annotation - remarks or ratings bestowed upon the submission 12 The submitter proposes changes in a submission, which is evaluated by a reviewer, who annotates or accepts it. 13 Most formal Least formal Team Pair Peer Inspection Walkthrough Ad-hoc review review programming deskcheck, passaround Wiegers’ peer review formality spectrum 14 Most formal Least formal Team Pair Peer Inspection Walkthrough Ad-hoc review review programming deskcheck, passaround Wiegers’ peer review formality spectrum 15 16 Agenda • Quick anecdote • What is code review? • What problems does code review solve? • Quality attributes code review ensures • Tips for code reviews • Limitations 17 Aside from the primary goal of reducing defects, Code review solves two major problems. -

Visual Build Help
Visual Build Professional User's Manual Copyright © 1999-2021 Kinook Software, Inc. Contents I Table of Contents Part I Introduction 1 1 Overview ................................................................................................................................... 1 2 Why Visual................................................................................................................................... Build? 1 3 New Features................................................................................................................................... 2 Version 4 .......................................................................................................................................................... 2 Version 5 .......................................................................................................................................................... 3 Version 6 .......................................................................................................................................................... 4 Version 7 .......................................................................................................................................................... 7 Version 8 .......................................................................................................................................................... 9 Version 9 ......................................................................................................................................................... -

Micro Focus Solutions 04
DevSecOps: How to integrate Security & Compliance into your Continuous Delivery pipelines Kevin A. Lee – [email protected] Senior Solutions Architect DevOps and Release Management Webinars (UK) •Automating DevSecOps: How to embed security into your continuous delivery pipelines •Enterprise DevOps: Release Management for the multi-modal Enterprise •Continuous Delivery Pipelines: Automating the value stream through continuous release https://www.microfocus.com/campaign/serena-release-management/ Agenda 01. What is DevSecOps? 02. Implementing DevSecOps 03. Micro Focus Solutions 04. Demonstration 05. Q&A What is DevSecOps Security threats are multiplying exponentially… … this is just in the UK!!! 157,000 customers employee data over 133,000 theft of £2.5m Data breach Personal and data breached in compromised in accounts hacked to from 9,000 stealing customer financial data of 2015, £400k fine 2016 acquire handsets customers' payment details 380,000 in 2016 account in 2016 who transacted on passengers hacked site in 2018, in 2018, potential potential £17m £500 fine fine Potential fines scaling massively under EU GDPR (May 2018) The majority of security breaches today are from application vulnerabilities 80% 90% Percentage of applications containing at Security incidents from exploits against least one critical or high vulnerability. 1 defects in the design or code of software. 2 1 2017 Application Security Research Update” by the HPE Software Security Research team 2 U.S. Department of Homeland Security’s U.S. Computer Emergency Response Team (US-CERT) Enterprise organizations have competing forces… I want it now! Business Built it Keep it faster Does it Make it stable work? secure Development Operations QA Security DevOps “DevOps (development and operations) is an enterprise software development phrase used to mean a type of agile relationship between development and IT operations. -

Ansys SCADE Lifecycle®
EMBEDDED SOFTWARE Ansys SCADE LifeCycle® SCADE LifeCycle is part of the Ansys Embedded Software family of products and solutions that includes modules providing unique support for application lifecycle management. This product line features requirements traceability via Application Lifecycle Management (ALM) tools, traceability from models, configuration and change management, and automatic documentation generation. SCADE LifeCycle enhances the functionalities of Ansys SCADE® tools with add-on modules that bridge SCADE solutions and Requirement Management tools or PLM/ALM (Product Lifecycle Management/ Application Lifecycle Management) tools. With SCADE LifeCycle, all systems and software teams involved in critical applications development can manage and control their design and verification activities across the full life cycle of their SCADE applications. / Requirements Traceability SCADE LifeCycle Application Lifecycle Management (ALM) Gateway provides an integrated traceability analysis solution for safety-critical design processes with SCADE Architect, SCADE Suite, SCADE Display, SCADE Solutions for ARINC 661 and SCADE Test: • Connection to ALM tools: linkage to DOORS NG, DOORS (9.6 and up) Jama Connect, Siemens Polarion, Dassault Systèmes Reqtify 2016. • Graphical creation of traceability links between requirements or other structured documents and SCADE models. • Traceability of test cases from SCADE Test Environment projects. • Bidirectional navigation across requirements and tests. • Customizable Export of SCADE artifacts to DOORS or Jama Connect. • Compliant with DO-178B, DO-178C, EN 50128, IEC 61508, ISO 26262, and IEC 60880 standards. EMBEDDED SOFTWARE / SCADE LifeCycle® // 1 / Project Documentation Generation SCADE LifeCycle Reporter automates the time-consuming creation of detailed and complete reports from SCADE Suite, SCADE Display, SCADE Architect and SCADE UA Page Creator for ARINC 661 designs through: • Generation of reports in RTF or HTML formats. -

Configuration Management for Distributed Development
Software Configuration Management Configuration Management for Distributed Development By Nina Rajkumar. © Think Business Networks Pvt. Ltd., July 2001 All rights reserved. You may make one attributed copy of this material for your own personal use. For additional information or assistance please contact Nina at (+91)422-320-606. www.thinkbn.com • 697A, Trichy Road, Coimbatore, TN 641045. Table of Contents Configuration Management for Distributed Development.............................. 4 Configuration Management ................................................................................ 5 Distributed Development.................................................................................... 5 Cases of Distributed Development ..................................................................... 6 Distance Working ........................................................................................... 6 Outsourcing..................................................................................................... 6 Co-located Groups .......................................................................................... 7 Distributed Groups.......................................................................................... 7 Architecture ........................................................................................................ 8 Remote Login.................................................................................................. 8 Several sites by Master-Slave connections .................................................... -

Opinnäytetyö Ohjeet
Lappeenrannan–Lahden teknillinen yliopisto LUT School of Engineering Science Tietotekniikan koulutusohjelma Kandidaatintyö Mikko Mustonen PARHAITEN OPETUSKÄYTTÖÖN SOVELTUVAN VERSIONHALLINTAJÄRJESTELMÄN LÖYTÄMINEN Työn tarkastaja: Tutkijaopettaja Uolevi Nikula Työn ohjaaja: Tutkijaopettaja Uolevi Nikula TIIVISTELMÄ LUT-yliopisto School of Engineering Science Tietotekniikan koulutusohjelma Mikko Mustonen Parhaiten opetuskäyttöön soveltuvan versionhallintajärjestelmän löytäminen Kandidaatintyö 2019 31 sivua, 8 kuvaa, 2 taulukkoa Työn tarkastajat: Tutkijaopettaja Uolevi Nikula Hakusanat: versionhallinta, versionhallintajärjestelmä, Git, GitLab, SVN, Subversion, oppimateriaali Keywords: version control, version control system, Git, GitLab, SVN, Subversion, learning material LUT-yliopistossa on tietotekniikan opetuksessa käytetty Apache Subversionia versionhallintaan. Subversionin käyttö kuitenkin johtaa ylimääräisiin ylläpitotoimiin LUTin tietohallinnolle. Lisäksi Subversionin julkaisun jälkeen on tullut uusia versionhallintajärjestelmiä ja tässä työssä tutkitaankin, olisiko Subversion syytä vaihtaa johonkin toiseen versionhallintajärjestelmään opetuskäytössä. Työn tavoitteena on löytää opetuskäyttöön parhaiten soveltuva versionhallintajärjestelmä ja tuottaa sille opetusmateriaalia. Työssä havaittiin, että Git on suosituin versionhallintajärjestelmä ja se on myös suhteellisen helppo käyttää. Lisäksi GitLab on tutkimuksen mukaan Suomen yliopistoissa käytetyin ja ominaisuuksiltaan ja hinnaltaan sopivin Gitin web-käyttöliittymä. Näille tehtiin -

Versie Beheer Systemen (VCS) 1
Versie beheer systemen (VCS) 1 Computerclub Volwassenen, Jeugd en Informatica vzw www.vji.be Versie beheer systemen (VCS) Inleiding ..................................................................................................................................... 2 Beheer repository en client programma’s .............................................................................. 2 In- en uitchecken, merging, labeling, branching.................................................................... 2 Software ..................................................................................................................................... 3 Microsoft Visual SourceSafe (VSS) ...................................................................................... 3 SourceOffSite..................................................................................................................... 3 VSSConnexion................................................................................................................... 3 Borland StarTeam .................................................................................................................. 3 CVS (Concurrent Versions System) ...................................................................................... 4 CvsGui................................................................................................................................4 TortoiseCVS...................................................................................................................... -

Starteam 16.2
StarTeam 16.2 Release Notes Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright © Micro Focus 2017. All rights reserved. MICRO FOCUS, the Micro Focus logo and StarTeam are trademarks or registered trademarks of Micro Focus IP Development Limited or its subsidiaries or affiliated companies in the United States, United Kingdom and other countries. All other marks are the property of their respective owners. 2017-11-02 ii Contents StarTeam Release Notes ....................................................................................5 What's New ........................................................................................................ 6 16.2 ..................................................................................................................................... 6 StarTeam Command Line Tools .............................................................................. 6 StarTeam Cross-Platform Client ...............................................................................6 StarTeam Git Command Line Utility. .........................................................................7 StarTeam Server ...................................................................................................... 7 Workflow Extensions ................................................................................................ 8 StarTeam Web Client ................................................................................................8 16.1 Update 1 ......................................................................................................................9 -

Teamcity 7.1 Documentation.Pdf
1. TeamCity Documentation . 4 1.1 What's New in TeamCity 7.1 . 5 1.2 What's New in TeamCity 7.0 . 14 1.3 Getting Started . 26 1.4 Concepts . 30 1.4.1 Agent Home Directory . 31 1.4.2 Agent Requirements . 32 1.4.3 Agent Work Directory . 32 1.4.4 Authentication Scheme . 33 1.4.5 Build Agent . 33 1.4.6 Build Artifact . 34 1.4.7 Build Chain . 35 1.4.8 Build Checkout Directory . 36 1.4.9 Build Configuration . 37 1.4.10 Build Configuration Template . 38 1.4.11 Build Grid . 39 1.4.12 Build History . 40 1.4.13 Build Log . 40 1.4.14 Build Number . 40 1.4.15 Build Queue . 40 1.4.16 Build Runner . 41 1.4.17 Build State . 41 1.4.18 Build Tag . 42 1.4.19 Build Working Directory . 43 1.4.20 Change . 43 1.4.21 Change State . 43 1.4.22 Clean Checkout . 44 1.4.23 Clean-Up . 45 1.4.24 Code Coverage . 46 1.4.25 Code Duplicates . 47 1.4.26 Code Inspection . 47 1.4.27 Continuous Integration . 47 1.4.28 Dependent Build . 47 1.4.29 Difference Viewer . 49 1.4.30 Guest User . 50 1.4.31 History Build . 51 1.4.32 Notifier . 51 1.4.33 Personal Build . 52 1.4.34 Pinned Build . 52 1.4.35 Pre-Tested (Delayed) Commit . 52 1.4.36 Project . 53 1.4.37 Remote Run . .. -
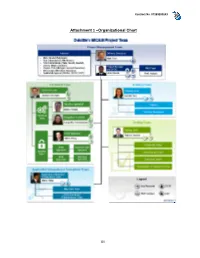
85 Attachment 1 –Organizational Chart
Contract No. 071B3200143 Attachment 1 –Organizational Chart 85 Contract No. 071B3200143 Appendix A - Breakdown of Hardware and Related Software Table 1: Hardware Cost ($): State Brand, Model # Item Specifications will provide from Comments and Description existing Contracts Total # of Virtual The hardware is Machines: 48 sized for Production, QA/Staging, Secure-24 VMware Total # of Virtual Development, and Cluster Access for CPUs: 96 Sandbox Server deploying ISIM, environments in the ISAM and ISFIM Total Virtual RAM: primary data center components 416 GB and for Production, and QA environments in the OS: RedHat Linux secondary data 6.x center The total storage is estimated for Total Storage: 35.7 Production, , TB QA/Staging, Development and Enterprise Class Sandbox Storage (3.8TB of Bronze SAN Storage Tier, 15.8TB of environments in the Silver Tier, 5.1TB of primary data center Logs Tier, 11TB of and for Production, Gold Tier) QA environments in the secondary data center CD/DVD Backup Device None None Rack w/ Power Supply Rack mountable Redundant Power Screen None None A total of 10 Web Gateway appliances are estimated for Production, QA/Staging, Web Gateway Development and Any other Hardware (list) v7.0 Hardware Appliance Sandbox environments in the primary data center and for Production, QA environments in the secondary data center. TOTAL $ 86 Contract No. 071B3200143 Table 2: Related Software Software Component Product Name Cost ($): State # of Licenses Comments License and Version will provide from existing Contracts Contractor user laptops already include this software. We will reuse the Report writers MS Office 2010 State owned software State of Michigan user licenses laptops will need this software for up to 4 users.