NSS Corporate Presentation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Universidad Pol Facultad D Trabajo
UNIVERSIDAD POLITÉCNICA DE MADRID FACULTAD DE INFORMÁTICA TRABAJO FINAL DE CARRERA ESTUDIO DEL PROTOCOLO XMPP DE MESAJERÍA ISTATÁEA, DE SUS ATECEDETES, Y DE SUS APLICACIOES CIVILES Y MILITARES Autor: José Carlos Díaz García Tutor: Rafael Martínez Olalla Madrid, Septiembre de 2008 2 A mis padres, Francisco y Pilar, que me empujaron siempre a terminar esta licenciatura y que tanto me han enseñado sobre la vida A mis abuelos (q.e.p.d.) A mi hijo icolás, que me ha dejado terminar este trabajo a pesar de robarle su tiempo de juego conmigo Y muy en especial, a Susana, mi fiel y leal compañera, y la luz que ilumina mi camino Agradecimientos En primer lugar, me gustaría agradecer a toda mi familia la comprensión y confianza que me han dado, una vez más, para poder concluir definitivamente esta etapa de mi vida. Sin su apoyo, no lo hubiera hecho. En segundo lugar, quiero agradecer a mis amigos Rafa y Carmen, su interés e insistencia para que llegara este momento. Por sus consejos y por su amistad, les debo mi gratitud. Por otra parte, quiero agradecer a mis compañeros asesores militares de Nextel Engineering sus explicaciones y sabios consejos, que sin duda han sido muy oportunos para escribir el capítulo cuarto de este trabajo. Del mismo modo, agradecer a Pepe Hevia, arquitecto de software de Alhambra Eidos, los buenos ratos compartidos alrrededor de nuestros viejos proyectos sobre XMPP y que encendieron prodigiosamente la mecha de este proyecto. A Jaime y a Bernardo, del Ministerio de Defensa, por haberme hecho descubrir las bondades de XMPP. -

School and Email Systems
Email system survey: Top 50 US Colleges US Note Email system Server queried Greeting News School ranking 1 Harvard University Mail2World imap.college.harvard.edu OK Mail2World IMAP4 Server 2.5 ready Sun Java SMS imap.princeton.edu OK [CAPABILITY IMAP4 IMAP4rev1 ACL QUOTA LITERAL+ NAMESPACE UIDPLUS CHILDREN BINARY LANGUAGE XSENDER X-NETSCAPE XSERVERINFO Princeton University 1 AUTH=PLAIN] Messaging Multiplexor (Sun Java(tm) System Messaging Server 6.2-5.05 (built Feb 16 2006)) Unknown mail.yale.edu OK [CAPABILITY IMAP4REV1 LOGIN-REFERRALS AUTH=PLAIN AUTH=LOGIN] pantheon-po14.its.yale.edu IMAP4rev1 2002.336 at Mon, 26 Jul 2010 14:10:23 Yale University 3 -0400 (EDT) Dovecot imap-server.its.caltech.edu OK Dovecot ready. Cyrus mail.alumni.caltech.edu OK posteaux1.caltech.edu Cyrus IMAP4 v2.2.12-Invoca-RPM-2.2.12-10.el4_8.4 server ready 4 California Institute of Technology Dovecot imap.gps.caltech.edu OK dovecot ready. Dovecot theory.caltech.edu OK dovecot ready. 4 Massachusetts Institute of Technology Unable to find a server to query (username.mail.mit.edu)Unknown 4 Stanford University Zimbra zm01.stanford.edu OK zm01.stanford.edu Zimbra IMAP4rev1 server ready Zimbra mailbox.zimbra.upenn.edu OK mailbox.zimbra.upenn.edu Zimbra IMAP4rev1 service ready 4 University of Pennsylvania Exchange 2010 webmail.wharton.upenn.edu OK The Microsoft Exchange IMAP4 service is ready. Dovecot imap.nevis.columbia.edu OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE AUTH=PLAIN] Dovecot ready. Lotus Domino equinox.law.columbia.edu OK Domino IMAP4 -

Communigate Pro Voip Administrator Training
CommuniGate Pro Real-Time Features CommuniGate Pro ● Internet Communications ● VoIP, Email, Collaboration, IM ● www.communigate.com CommuniGate Pro for VoIP Administrators • Audience: Server Administrators and Developers • Focus: CommuniGate Pro as the Signaling platform • Method: Understanding CommuniGate Pro operation for Real-Time Signaling services. “How it works” • Goal: Learn what CommuniGate Pro can do for you. CommuniGate Pro ● Internet Communications ● VoIP, Email, Collaboration, IM ● www.communigate.com Who is CommuniGate Systems • Founded • Communications Software • Focus on electronic mail and collaboration • Standards • Carrier Grade • Real-Time Communications • CommuniGate Pro CommuniGate Pro ● Internet Communications ● VoIP, Email, Collaboration, IM ● www.communigate.com What is CommuniGate Pro • Self-contained single package • Multithreaded • Multiplatform • Flexible • Extensible • Not just a product – it’s a platform CommuniGate Pro ● Internet Communications ● VoIP, Email, Collaboration, IM ● www.communigate.com Data Storage • Hierarchical – Logically – Physically • Efficient • Settings, Mail, Metadata, Templates, Middleware, Software CommuniGate Pro ● Internet Communications ● VoIP, Email, Collaboration, IM ● www.communigate.com System Kernel • Multithreading • Disk I/O • Network I/O • OS interfaces • Everything Else CommuniGate Pro ● Internet Communications ● VoIP, Email, Collaboration, IM ● www.communigate.com Standard Protocols • SMTP • POPPWD • POP3 • RADIUS • IMAP • TFTP • ACAP • SNMP • LDAP • SYSLOG • HTTP • FTP -

Administrative Web Guide
GO!NotifyLink Enterprise Server Enterprise Server Administrative Web Guide GO!NotifyLink Enterprise Server Administrative Web GuideConfiguring a New GO!NotifyLink Enterprise Server 1 Table of Contents Configuring a New GO!NotifyLink Enterprise Server 4 Accessing the Administrative Web 6 The License Manager 8 Adding New Licenses ................................................................................................... 9 Updating Licenses / Viewing License Details ............................................................... 9 Removing Licenses ..................................................................................................... 11 PDF Reader Licensing for BlackBerry Users .............................................................. 11 Server Administration 14 Server Administration Page Settings .......................................................................... 15 Messaging Settings ..................................................................................................... 18 SMTP Server Settings ................................................................................................ 22 Administrative Logins .................................................................................................. 22 Proxy Authentication (Super User Accounts) ............................................................. 25 Mail Server Settings .................................................................................................... 27 PIM Server Settings ................................................................................................... -

Market Observation D12.3 Report on Key Technology Issues in Current EAI, E- Business and Knowledge Management (Enterprise Collaboration with Semantic Web Services)
Report on key technology issues in current EAI, E-Business and Knowledge Management DIP Data, Information and Process Integration with Semantic Web Services FP6 - 507483 Deliverable WP 12: Market Observation D12.3 Report on Key Technology Issues in Current EAI, E- Business and Knowledge Management (Enterprise Collaboration with Semantic Web Services) Joachim Quantz, Berlecon Research Thorsten Wichmann, Berlecon Research January 4th , 2005 Deliverable 12.3 i 04/01/2005 Report on key technology issues in current EAI, E-Business and Knowledge Management EXECUTIVE SUMMARY Work Package 12 provides the DIP consortium and in particular the technology providers in DIP with real-world background information on potential application areas for Semantic Web Services (SWS). This deliverable continues the work started in D12.1 and provides an in-depth analysis of the potential of SWS in Enterprise Collaboration. Enterprise Collaboration is the second application area investigated in detail after Business Process Management, which is evaluated in Section 4 of D12.1. Subsequent deliverables will analyse the other application areas having high potential for SWS, namely content syndication, search/mining, and social software. Enterprise collaboration is an application area combining technology from portals, groupware and personal information management (PIM). It comprises basic groupware solutions (e.g. Microsoft Exchange), collaboration infrastructure (e.g. Lotus Workplace), and complex portal technology (e.g. Plumtree). Its main purpose is to provide all functionality needed for business collaboration within and across enterprise boundaries. Instead of having separate standalone products for functionality such as document exchange, conferencing, messaging or scheduling, an integrated solution will be required in the future Semantic Web Services could be used in enterprise collaboration to • realize the interfaces provided by the various collaboration components, • provide centralized information used throughout the individual collaboration components, e.g. -

GO!Notifysync Pre-Purchase Checklist
GO!NotifySync Pre-Purchase Checklist Prior to purchasing GO!NotifySync you will need to identify the following configuration information. Consult your Mail Server Administrator, if necessary, to obtain this information. Mail Server Administrators can also reference, Guidelines for Administrators. My Mail Server Type is GO!NotifySync supports ActiveSync protocol versions 2.5, 12.0, or 12.1. GO!NotifySync is certified against the following versions of ActiveSync servers: GroupWise 8.0.2 HP2, 8.0.2 HP3, 2012, or 2014 with Novell Data Synchronizer or Novell Mobility Services 2.0 Microsoft Exchange 2010 Microsoft Exchange 2007 Microsoft Exchange 2003 Below is a list of additional ActiveSync servers. If these systems adhere to the supported ActiveSync protocol versions (2.5, 12.0, or 12.1), GO!NotifySync has a high probability of working as designed: AXIGEN Messaging CommuniGate Pro Google Hotmail IBM Lotus Notes Traveler v8.5.2.1 IceWarp Server Ipswitch IMail Server Kerio MailServer Office 365 Open-Xchange Scalix Zarafa Zimbra Collaboration Suite My Email Domain is The text after the @ sign in your Email address is your Email Domain. If your Email address is: [email protected], your Email Domain is: mycompany.com GO!NotifySync Pre-Purchase Checklist 1 My Mail/ActiveSync Server Address is This is the external address of your Mail/ActiveSync server. Information that may help you identify the ActiveSync Server Address: Your best source for this information is your Mail Server Administrator. What address is used to log into Web mail? That would be the ActiveSync Server address. Ask: What is the address I would use to connect to the ActiveSync Server? My Domain is Domain refers to a group of servers on a network that are administered as a unit. -
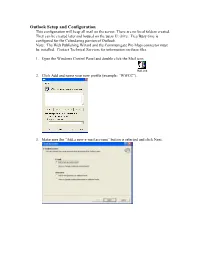
Outlook Setup and Configuration This Configuration Will Keep All Mail on the Server
Outlook Setup and Configuration This configuration will keep all mail on the server. There are no local folders created. They can be created later and housed on the users U: drive. Free/Busy time is configured for the Calendaring portion of Outlook. Note: The Web Publishing Wizard and the Communigate Pro Mapi connector must be installed. Contact Technical Services for information on these files. 1. Open the Windows Control Panel and double click the Mail icon. Mail..lnk 2. Click Add and name your new profile (example: “WWCC”). 3. Make sure the “Add a new e-mail account” button is selected and click Next. 4. Click the “Additional Server types” button and click next. 5. Under “Additional Server Types” CommuniGate Pro Server should be highlighted. Click Next 6. In the CommuniGate Pro Properties window key in Server name, Account Name (be sure to add the @wwcc.edu) and Password. (Account name and password are user specific.) The remember password box can be unchecked later. Under the Connection tab make sure the Connect using LAN is checked. Click OK 7. At the Profile window, click OK. 8. Open Outlook. It may take a few seconds to receive the information from the server. After Outlook opens, click View, click Folder List. In the left pane, the user’s folders on the mail server will display. 9. To setup Free/Busy time for the Calendar: Open the Options dialog box from Tools on the menu bar. Under Calendar, click Calendar Options then at the bottom of the window click Free/Busy options. 10. -

Mppv4 Installation and Upgrade Guide August 2008
MPPv4 Installation and Upgrade Guide August 2008 ABSTRACT This document provides guidelines for installing and upgrading MPP and its components. Message Partners, Inc. 271 North Avenue, Suite 1210 New Rochelle, NY 10801 USA (877) 302-2027 +1 (914) 712-9050 +1 (914) 206-9609 - Fax [email protected] Copyright Message Partners 1 Table of Contents 1 INTRODUCTION ........................................................................................3 2 ARCHITECTURE OVERVIEW.......................................................................4 2.1 MPP System Architecture...........................................................................................4 3 MPP SOFTWARE INSTALLATION .............. ERROR! BOOKMARK NOT DEFINED. 3.1 Overview.....................................................................................................................3 3.2 Deployment Scenarios ...............................................................................................3 3.3 Installing MPP.............................................................................................................5 3.4 Installing MPP on Mac OS X ......................................................................................8 3.5 Installing the MPP Virtual Appliance ..........................................................................9 3.6 MPP Trial Keys...........................................................Error! Bookmark not defined. 3.7 MPP Plug-in Modules...............................................................................................10 -

KASPERSKY Security for Mail Server Keep Your Corporate Mail System Free of Spam and Malware
KASPERSKY SECUrity FOR MaiL SerVer Keep your corporate mail system free of spam and malware Email has become a major channel for malware distribution. Virus outbreaks cause companies significant financial damage by undermining the integrity and confidentiality of their information. In addition, companies face considerable losses due to employees needing to delete hundreds of unwanted messages from their mailboxes each day. The extra traffic caused by such unwanted mail has to be paid for too. Kaspersky Security for Mail Server is a High Value solution from Kaspersky Lab that is easy to install and use. It effectively protects traffic running through mail and groupware servers from the latest malware and spam. The solution includes refreshed applications that ensure the security of all popular mail servers, including Microsoft® Exchange, Lotus® Domino®, Sendmail, qmail, Postfix, Exim and CommuniGate Pro. Kaspersky Security for Mail Server can also be used to set up a dedicated mail gateway and works seamlessly in even the most complex heterogeneous infrastructures. KEY BENEFITS PROTECTS MAIL SERVERS AND COLLABORATION PLATFORMS Kaspersky Security for Mail Server works to protect mail on the latest versions of major mail and collaboration platforms, including: Microsoft® Exchange, IBM Lotus® Domino® (installed on Windows® or Linux platforms) and Linux- based mail servers. REDUCES TRAFFIC LOAD Intelligent spam filtering significantly reduces traffic load in your organization. OpTIMIZE SYSTEM RESOURCES A new antivirus engine, load balancing of server resources, optimized antivirus scanning technology and the option to exclude specified objects from scanning increase performance and reduce the resources needed to perform antivirus scans. CONTROL WITH EASE Simple, user-friendly management tools, information on mail protection status, plus flexible settings for scans and reporting give you efficient control of your mail and document security. -
Communigate Pro Messaging Platform
WHITE PAPER 01/03 CommuniGate Pro Messaging Platform Transforming Email and Calendaring Overview As e-mail continues to be the preferred method of business “CommuniGate Pro is a feature-rich messaging server that communication, choosing a mature and complete e-mail not only offers superior IMAP, POP3, and SMTP services, server becomes a mission critical decision. Organizations but also provides HTML-based e-mail access, excellent anti- need a robust yet easy to manage solution and reliable tech- spam capabilities, LDAP support, and a state-of-the-art list nical support from the system vendor. According to a report server.” from technology analysts IDC, on an average day in 2000, Internet standard messaging, combined with sophisticated 9.7 billion e-mail messages were sent worldwide. By the collaborative functionality makes CommuniGate Pro an year 2005 that number will grow to 35 billion. ideal solution for organizations looking for calendaring and scheduling on the desktop, or those wanting to replace Making matters more complicated, offering only e-mail is expensive and unreliable messaging environments without not enough. Organizations must offer other services includ- losing end user functionality. ing mailing lists, address books, calendaring and scheduling, look-ups for local and remote account information, secure Web based e-mail, and personal Web sites. Is your messaging infrastructure ready? Proven First released in 1998, CommuniGate Pro is a proven solu- This overview will introduce you to CommuniGate Pro, the tion, with several thousand servers hosting 30 million active carrier scale internet messaging software from Communi- users worldwide. It earned its excellent reputation meeting Gate Systems. -

Communigate Pro Messaging Server 1 Features 2 Administrating 3 Support and Discussions 3 What Is New in Communigate Pro Updates? 3
CommuniGate Pro Messaging Server 1 Features 2 Administrating 3 Support and Discussions 3 What Is New in CommuniGate Pro Updates? 3 CommuniGate Pro Installation 5 Installation 5 Installing on a MS Windows XP/2000/NT/9x/ME System 5 Installing on a Sun Solaris System. 7 Installing on a Linux System. 7 Installing on a MacOS X (Darwin) System. 9 Installing on a MacOS X Server (Rhapsody) System. 9 Installing on a FreeBSD System. 10 Installing on a BSDI BSD/OS System. 11 Installing on an OpenBSD System. 12 Installing on an AIX System. 13 Installing on an HP/UX System. 13 Installing on a Tru64 (Digital Unix) System. 14 Installing on an SGI IRIX System. 15 Installing on an SCO UnixWare System. 16 Installing on an IBM OS/400 System. 17 Installing on a QNX System. 18 Installing on an IBM OS/2 System. 18 Installing on a BeOS System. 19 Initial Configuration 20 Upgrading to a Newer Version 22 Moving to a New Hardware Server 22 Migrating to CommuniGate Pro 25 Supporting Network Users 25 Supporting Local Users 26 Using Legacy Mailboxes 26 CommuniGate Pro I Converting Passwords 27 Migrating from sendmail 29 Migrating from Post.Office® servers 30 Migrating from Netscape®/iPlanet Messaging servers 31 Migrating from IMail® servers 31 Migrating from CommuniGate/MacOS and SIMS 31 Migrating from Microsoft® Exchange Servers 31 Copying Mailboxes from Other POP Servers 31 Copying Mailboxes from Other IMAP Servers 33 Copying All Mailboxes from Other Servers 35 Migrating from an Arbitrary Server ("on-the-fly" migration) 38 Switching Servers 39 Moving to Secondary -

Email Server Configuration Guide Table of Contents
Email Server Configuration Guide Table of Contents Configure MLArchiver for SMTP...................................................................................3 Configure MLArchiver for POP or IMAP........................................................................5 Office 365 using SMTP................................................................................................6 Microsoft Exchange using SMTP (2007 – 2013).........................................................13 Microsoft Exchange 2016 using SMTP.......................................................................24 Microsoft Exchange 2007-2013 using POP3 or IMAP.................................................29 Microsoft Exchange 2016 using POP3 or IMAP..........................................................31 Microsoft Office 365 using IMAP................................................................................35 Google Apps Professional (Business and Education) – IMAP or POP..........................38 Kerio using POP or IMAP............................................................................................42 Notes/Domino Email Server......................................................................................44 Unix Mail Server........................................................................................................ 46 Zimbra Mail Server...................................................................................................47 Communigate Pro Mail Server..................................................................................48