Organisational Adoption of Innovation a Qualitative Study on Role-Based Access Control in the Physical Setting of a Data Centre
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![Fall 2011, KER202 Martin Hilbert Office Hours: by Appointment; Mhilbert [At] Usc.Edu](https://docslib.b-cdn.net/cover/5825/fall-2011-ker202-martin-hilbert-office-hours-by-appointment-mhilbert-at-usc-edu-385825.webp)
Fall 2011, KER202 Martin Hilbert Office Hours: by Appointment; Mhilbert [At] Usc.Edu
CMGT 582- Communication for International Development Fall 2011, KER202 Martin Hilbert Office hours: by appointment; mhilbert [at] usc.edu Course description: This course builds on two main concepts: Development: We are usually quick to note that we live in a global communication landscape, but we all too often do not pay enough attention to the fact that 82% of this world is living in conditions that are quite different from ours: the developing world. Half of the human population lives with less than US$2.50 per day, making that a monthly income of less than US$75 for every second member of our global information society. This does not only matter for those who are poor, but shapes the global communication landscape as a whole. We still start with reviewing the multiple dimensions of development. We will discuss questions like: What is development? Is poverty merely a matter of economic well-being? What are the driving forces behind development? What are the dynamics and interplay between developed and developing societies? What is and what can the international community (like the United Nations, World Bank, global NGOs) do about it? We will spend most of the time discussing the question: What is the role of communication as a building block for the development of a society? Digital innovation: At the same time, the introduction of digital ICT (Information and Communication Technologies) changes the lives of all people around the globe (directly or indirectly). In less than two decades, 2 out of 5 people worldwide have linked up through the Internet, and 4 out of 5 have connected with mobile telephony. -

Listening to Everett Rogers: Diffusion of Innovations and WAC Stephanie Vanderslice University of Central Arkansas
22 Language and Learning Across the Disciplines Listening to Everett Rogers: Diffusion of Innovations and WAC Stephanie Vanderslice University of Central Arkansas In “The Future of WAC” (1996), Barbara E. Walvoord suggests framing the history and future of the writing-across-the-curriculum move- ment according to social movement theory (58), explaining that WAC qualifies as a movement because of its “change agenda and its collective nature—faculty talking to one another, moving to effect reform” (58). Con- sequently, she proposes that her evaluation of WAC’s progress at the 25 year mark and her re-envisioning of its future within this movement frame will uniquely reveal its “characteristics, strengths, and problems in ways that may help us think creatively about them” (61). Certainly creativity may be the order of the day as the WAC move- ment, in spite of its successes, struggles to maintain its vitality and visibil- ity against the perennially resistant landscape of academe. Such resis- tance, educational reform scholar Parker J. Palmer reminds us, (though few at the front lines of the WAC movement need reminding) will remain an essential feature of the academy as long as teaching “retains low status... tenure decisions favor those who publish, [and] scarce dollars. .always go to research” (10). These conditions result in a “constitutional gridlock” which breeds the “mood of resignation. .and despair” so familiar to those seeking reform (10). Walvoord’s review of WAC’s progress from a social movement per- spective turns the literature in an important direction. By providing the template of social movement theory against which to examine their suc- cesses and failures, WAC proponents are forced to take a more analytical approach to their subject, an approach that transcends the more anec- dotal “what works and what doesn’t” scholarship that has dominated writing-across-the-curriculum, especially in its early and middle years. -

A Summary of Diffusion of Innovations
Les Robinson | Phone 0414 674 676 | Email [email protected] Web www.enablingchange.com.au | Blog http://enablingchange.posterous.com A summary of Diffusion of Innovations Les Robinson Fully revised and rewritten Jan 2009 Diffusion of Innovations seeks to explain how innovations are taken up in a population. An innovation is an idea, behaviour, or object that is perceived as new by its audience. Diffusion of Innovations offers three valuable insights into the process of social change: - What qualities make an innovation spread successfully. - The importance of peer-peer conversations and peer networks. - Understanding the needs of different user segments. These insights have been tested in more than 6000 research studies and field tests, so they are amongst the most reliable in the social sciences. What qualities make innovations spread? Diffusion of Innovations takes a radically different approach to most other theories of change. Instead of focusing on persuading individuals to change, it sees change as being primarily about the evolution or “reinvention” of products and behaviours so they become better fits for the needs of individuals and groups. In Diffusion of Innovations it is not people who change, but the innovations themselves. Why do certain innovations spread more quickly than others? And why do others fail? Diffusion scholars recognise five qualities that determine the success of an innovation. This work is licensed under the Creative Commons Attribution-Noncommercial-No Derivative Works 2.5 Australia License. To view a copy of this license visit http://creativecommons.org/licenses/by-nc-nd/2.5/au/deed.en Attribution should be made to “Les Robinson www.enablingchange.com.au”. -
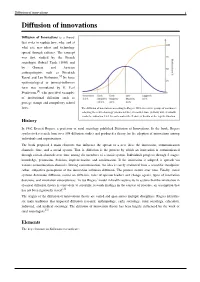
Diffusion of Innovations 1 Diffusion of Innovations
Diffusion of innovations 1 Diffusion of innovations Diffusion of Innovations is a theory that seeks to explain how, why, and at what rate new ideas and technology spread through cultures. The concept was first studied by the French sociologist Gabriel Tarde (1890) and by German and Austrian anthropologists such as Friedrich Ratzel and Leo Frobenius.[1] Its basic epidemiological or internal-influence form was formulated by H. Earl Pemberton,[2] who provided examples of institutional diffusion such as postage stamps and compulsory school laws. The diffusion of innovations according to Rogers. With successive groups of consumers adopting the new technology (shown in blue), its market share (yellow) will eventually reach the saturation level. In mathematics the S curve is known as the logistic function. History In 1962 Everett Rogers, a professor of rural sociology published Diffusion of Innovations. In the book, Rogers synthesized research from over 508 diffusion studies and produced a theory for the adoption of innovations among individuals and organizations. The book proposed 4 main elements that influence the spread of a new idea: the innovation, communication channels, time, and a social system. That is, diffusion is the process by which an innovation is communicated through certain channels over time among the members of a social system. Individuals progress through 5 stages: knowledge, persuasion, decision, implementation, and confirmation. If the innovation is adopted, it spreads via various communication channels. During communication, the idea is rarely evaluated from a scientific standpoint; rather, subjective perceptions of the innovation influence diffusion. The process occurs over time. Finally, social systems determine diffusion, norms on diffusion, roles of opinion leaders and change agents, types of innovation decisions, and innovation consequences. -

Provincializing Hegemonic Histories of Media and Communication Studies: Towards a Genealogy of Epistemic Resistance in Africa
Wendy Willems Provincializing hegemonic histories of media and communication studies: towards a genealogy of epistemic resistance in Africa Article (Accepted version) (Refereed) Original citation: Willems, Wendy (2014) Provincializing hegemonic histories of media and communication studies: towards a genealogy of epistemic resistance in Africa. Communication Theory. pp. 1-18. ISSN 1468-2885 (In Press) © 2014 International Communication Association This version available at: http://eprints.lse.ac.uk/57528/ Available in LSE Research Online: August 2014 LSE has developed LSE Research Online so that users may access research output of the School. Copyright © and Moral Rights for the papers on this site are retained by the individual authors and/or other copyright owners. Users may download and/or print one copy of any article(s) in LSE Research Online to facilitate their private study or for non-commercial research. You may not engage in further distribution of the material or use it for any profit-making activities or any commercial gain. You may freely distribute the URL (http://eprints.lse.ac.uk) of the LSE Research Online website. This document is the author’s final accepted version of the journal article. There may be differences between this version and the published version. You are advised to consult the publisher’s version if you wish to cite from it. Provincializing hegemonic histories of media and communication studies: towards a genealogy of epistemic resistance in Africa Wendy Willems Department of Media and Communications, London School of Economics and Political Science, London, United Kingdom Department of Media Studies, University of the Witwatersrand, Johannesburg, South Africa Original citation: Willems, W. -

Career Publication Report As Tracked in CIOS Resources Generated June 16, 2009 Name: Everett Rogers Degree Date: 1957 Publicatio
Career Publication Report as Tracked In CIOS Resources Generated June 16, 2009 ( c Communication Institute for Online Scholarship, Inc.) Name: Everett Rogers Degree date: 1957 Publication Summary Count Source 2 Communication Theory 3 Communication Yearbook 2 Asian Journal of Communication 1 Communication 1 Convergence 10 Communication Research 1 Communication Studies 4 Gazette 2 Human Communication Research 3 Journal of Applied Communication 1 Journal of Business Communication 2 Journal of Broadcasting and Electronic Media 2 Journalism and Mass Communication Quarterly 8 Journal of Communication 1 Mass Communication & Society 1 Public Opinion Quarterly 1 Science Communication Authorship Summary Total papers: 45 Single authored papers: 13 Multiple authored papers: 32 First authored papers: 26 Non first authored papers: 19 Ranks/Weights Using CIOS Default Set Number of ranked/weighted publications: 81 Range of ranks (with ties): 1 - 54 Range of weights: 0.0 - 4.85 CNT RNK RCNT WGHT WCNT Publication 2 18 36 2.084 4.17 Communication Theory 3 4 12 4.308 12.92 Communication Yearbook 2 36 72 0.883 1.77 Asian Journal of Communication 1 nr Communication 1 54 54 0.000 0.00 Convergence 10 5 50 4.203 42.03 Communication Research 1 10 10 2.675 2.68 Communication Studies 4 54 216 0.000 0.00 Gazette 2 1 2 4.847 9.69 Human Communication Research 1 3 6 18 3.705 11.12 Journal of Applied Communication 1 44 44 0.381 0.38 Journal of Business Communication 2 30 60 1.094 2.19 Journal of Broadcasting and Electronic Media 2 28 56 1.210 2.42 Journalism and Mass -

Everett M. Rogers
Population and Reproductive Health Oral History Project Sophia Smith Collection, Smith College Northampton, MA Everett M. Rogers Interviewed by Deborah McFarlane June 27, 2004 Albuquerque, New Mexico This interview was made possible with generous support from the William and Flora Hewlett Foundation. © Sophia Smith Collection 2006 Population and Reproductive Health Oral History Project Sophia Smith Collection, Smith College Narrator Everett M. Rogers, Ph.D. (1931–2004) formalized the diffusion of innovations theory (1962), explaining how new ideas are incorporated into a culture. He applied these ideas to family planning and population communication in the late 1960s, explaining how taboo communication differs from other subjects. In his oral history he discusses his international experiences in Pakistan and India in particular, as well as his recollections of General Bill Draper. Interviewer Deborah R. McFarlane is professor of political science at the University of New Mexico. She is the author, with K.J. Meier, of The Politics of Fertility Control: Family Planning and Abortion Politics in the American States (Congressional Quarterly Press, 2001). McFarlane worked as an administrator and a consultant in reproductive health in the U.S. and internationally for more than three decades. Restrictions None Format Three 60-minute audiocassettes. Transcript Transcribed, audited and edited at Baylor University. Transcript has been reviewed and approved by Everett Rogers. Bibliography and Footnote Citation Forms Audio Recording Bibliography: Rogers, Everett M. Interview by Deborah McFarlane. Audio recording, June 27, 2004. Population and Reproductive Health Oral History Project, Sophia Smith Collection. Footnote: Everett M. Rogers, interview by Deborah McFarlane, audio recording, June 27, 2004, Population and Reproductive Health Oral History Project, Sophia Smith Collection, tape 2. -

Factors Related to Teacher Adoption Rates and the Diffusion of a One to One Laptop Initiative in One Rural Public School District
FACTORS RELATED TO TEACHER ADOPTION RATES AND THE DIFFUSION OF A ONE TO ONE LAPTOP INITIATIVE IN ONE RURAL PUBLIC SCHOOL DISTRICT By Jacob Robert Quilliams Ted L. Miller David W. Rausch Professor of Learning and Leadership Professor of Learning and Leadership (Chair) (Committee Member) Elizabeth K. Crawford Nathaniel D. Line Associate Professor of Learning and Leadership External Reviewer (Committee Member) (Committee Member) FACTORS RELATED TO TEACHER ADOPTION RATES AND THE DIFFUSION OF A ONE TO ONE LAPTOP INITIATIVE IN ONE RURAL PUBLIC SCHOOL DISTRICT By Jacob Robert Quilliams A Dissertation Submitted to the Faculty of the University of Tennessee at Chattanooga in Partial Fulfillment of the Requirements of the Degree of Doctor of Philosophy: Learning and Leadership The University of Tennessee at Chattanooga Chattanooga, Tennessee December 2019 ii Copyright © 2019 By Jacob Robert Quilliams All Rights Reserved iii ABSTRACT The purpose of this study was to better understand how a one to one (1:1) Chromebook classroom initiative diffused in a rural public school system. To investigate this process a unique three part mixed methods study was created. In phase one of the study, teachers using a 1:1 Chromebook classroom were asked to participate in an online quantitative survey. In phase two, a Delphi technique was used to create an interview questionnaire. In phase three, one-on-one interviews were administered to 17 teachers with different levels of innovativeness. Specifically, this study was designed to investigate how factors such as perceived ease of use (PEOU), perceived use (PU), teacher demographic characteristics, and time of adoption related to teacher innovativeness. -

What's Inside
Vol. 33, No. 2 March 2005 At the 2005 ICA Conference in New York City Public Relations Chair’s Panel report on their efforts to date. The When Journalism, Culture, panel will open with 10-minute pre- and the Popular Intersect Friday, May 27, 12:45–2:00 p.m. sentations, after which the chair will Sheraton New York, invite questions from the floor. The Journalism Studies Lenox Ballroom session will be interactive. Popular Communication Sherry Devereaux Ferguson, U of Ottawa, Canada (Chair) Taskforce Committee Chairs: Saturday, May 28, 2:15–3:30 p.m. Craig Carroll, U of Southern Sheraton New York, In the spirit of the conference California—Annenberg, USA Empire Ballroom West theme, the Chair’s Panel will ad- (Chair) Barbie Zelizer, U of Pennsylvania dress ways to approach collabora- Betteke van Ruler, U of Amster- (Chair) tive research projects of global im- dam, The Netherlands (Vice- portance. The panel draws together Chair) What do notions of culture and the a group of international scholars popular offer the study of journal- who have been successful in propos- Taskforce Members and Panelists: ism? These papers deliberate on the ing, funding, collaborating, and con- Krishnamurthy Sriramesh, Nan- advantages and downsides that arise cluding international research proj- yang Technological U, Singapore when studying journalism through ects. Members of the Taskforce on Judy Motion, Waikato Manage- notions of culture and the popular. Cross-National Research (Public Re- ment School, New Zealand James Carey offersoffers anan analysisanalysis ooff lations Division), which was charged Sabine Einwiller, U of St. Gal- early connections between journal- with identifying, consolidating, and lens, Switzerland ism and the vernacular; John Hartley promoting opportunities for interna- Shannon Bowen, U of Houston, tional public relations research, will USA (continued on page 3) COMMUNICATIONS RESEARCH AND COMMUNICATION POLICY: An Update What’s Inside on the Media Ownership Issue by Philip M. -

Listening to Everett Rogers: Diffusion of Innovations and WAC Stephanie Vanderslice University of Central Arkansas
22 Language and Learning Across the Disciplines Listening to Everett Rogers: Diffusion of Innovations and WAC Stephanie Vanderslice University of Central Arkansas In “The Future of WAC” (1996), Barbara E. Walvoord suggests framing the history and future of the writing-across-the-curriculum move- ment according to social movement theory (58), explaining that WAC qualifies as a movement because of its “change agenda and its collective nature—faculty talking to one another, moving to effect reform” (58). Con- sequently, she proposes that her evaluation of WAC’s progress at the 25 year mark and her re-envisioning of its future within this movement frame will uniquely reveal its “characteristics, strengths, and problems in ways that may help us think creatively about them” (61). Certainly creativity may be the order of the day as the WAC move- ment, in spite of its successes, struggles to maintain its vitality and visibil- ity against the perennially resistant landscape of academe. Such resis- tance, educational reform scholar Parker J. Palmer reminds us, (though few at the front lines of the WAC movement need reminding) will remain an essential feature of the academy as long as teaching “retains low status... tenure decisions favor those who publish, [and] scarce dollars. .always go to research” (10). These conditions result in a “constitutional gridlock” which breeds the “mood of resignation. .and despair” so familiar to those seeking reform (10). Walvoord’s review of WAC’s progress from a social movement per- spective turns the literature in an important direction. By providing the template of social movement theory against which to examine their suc- cesses and failures, WAC proponents are forced to take a more analytical approach to their subject, an approach that transcends the more anec- dotal “what works and what doesn’t” scholarship that has dominated writing-across-the-curriculum, especially in its early and middle years. -

Innovators Or Laggards: Surveying Diffusion Of
INNOVATORS OR LAGGARDS: SURVEYING DIFFUSION OF INNOVATIONS BY PUBLIC RELATIONS PRACTITIONERS A Thesis Presented to The Graduate Faculty of The University of Akron In Partial Fulfillment Of the Requirements for the Degree Master of Arts Carol A. Savery August, 2005 ii ABSTRACT Everett M. Rogers’ diffusion of innovations theory was used as a framework to study 116 chapter members of the Public Relations Society of America (PRSA) in a Midwestern state. A web-based survey and paper-based survey were both used to collect the self-reporting data. According to Rogers (1986), “Diffusion is the process by which an innovation is communicated through certain channels over a period of time among members of a social system” (p. 117). Public relations practitioners are the members of the social system that were studied. Rogers defined an innovation as, “an idea, practice, or object that is perceived to be new by an individual or other unit of adoption” (p. 117). Diffusion research centers on the conditions which increase or decrease the likelihood that a new idea, product or practice will be adopted by members of a given culture. A literature review of diffusion of innovation showed no research applying Rogers’ theory to public relations. It is hoped that this thesis research will to add to the body of knowledge about diffusion of innovation in public relations by helping to identify the perceived innovation attributes, influences, obstacles and relative advantage of innovations by public relations practitioners. This could assist public relations agencies in weighing the pros and cons of future decisions and strategies for implementing innovations. -

Diffusion of Innovations
Diffusion of innovations of innovations took off in the subfield of rural sociol- 100 ogy in the midwestern United States in the 1920s and 1930s. Agriculture technology was advancing rapidly, and researchers started to examine how independent 75 Market share % share Market farmers were adopting hybrid seeds, equipment, and techniques.[5] A study of the adoption of hybrid corn seed 50 in Iowa by Ryan and Gross (1943) solidified the prior work on diffusion into a distinct paradigm that would [5][6] 25 be cited consistently in the future. Since its start in rural sociology, Diffusion of Innovations has been ap- 0 plied to numerous contexts, including medical sociology, Innovators Early Early Late Laggards communications, marketing, development studies, health 2.5 % Adopters Majority Majority 16 % 13.5 % 34 % 34 % promotion, organizational studies, knowledge manage- ment, and complexity studies,[7] with a particularly large The diffusion of innovations according to Rogers. With succes- impact on the use of medicines, medical techniques, and sive groups of consumers adopting the new technology (shown health communications.[8] In organizational studies, its in blue), its market share (yellow) will eventually reach the sat- basic epidemiological or internal-influence form was for- uration level. In mathematics, the yellow curve is known as the mulated by H. Earl Pemberton,[9] who provided examples logistic function. The curve is broken into sections of adopters. of institutional diffusion[10] such as postage stamps and standardized school ethics codes. Diffusion of innovations is a theory that seeks to ex- In 1962 Everett Rogers, a professor of rural sociol- plain how, why, and at what rate new ideas and technology ogy, published his seminal work: Diffusion of Innova- spread through cultures.