1201 Eff Reply Comments Class
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
1835. EXECUTIVE. *L POST OFFICE DEPARTMENT
1835. EXECUTIVE. *l POST OFFICE DEPARTMENT. Persons employed in the General Post Office, with the annual compensation of each. Where Compen Names. Offices. Born. sation. Dol. cts. Amos Kendall..., Postmaster General.... Mass. 6000 00 Charles K. Gardner Ass't P. M. Gen. 1st Div. N. Jersey250 0 00 SelahR. Hobbie.. Ass't P. M. Gen. 2d Div. N. York. 2500 00 P. S. Loughborough Chief Clerk Kentucky 1700 00 Robert Johnson. ., Accountant, 3d Division Penn 1400 00 CLERKS. Thomas B. Dyer... Principal Book Keeper Maryland 1400 00 Joseph W. Hand... Solicitor Conn 1400 00 John Suter Principal Pay Clerk. Maryland 1400 00 John McLeod Register's Office Scotland. 1200 00 William G. Eliot.. .Chie f Examiner Mass 1200 00 Michael T. Simpson Sup't Dead Letter OfficePen n 1200 00 David Saunders Chief Register Virginia.. 1200 00 Arthur Nelson Principal Clerk, N. Div.Marylan d 1200 00 Richard Dement Second Book Keeper.. do.. 1200 00 Josiah F.Caldwell.. Register's Office N. Jersey 1200 00 George L. Douglass Principal Clerk, S. Div.Kentucky -1200 00 Nicholas Tastet Bank Accountant Spain. 1200 00 Thomas Arbuckle.. Register's Office Ireland 1100 00 Samuel Fitzhugh.., do Maryland 1000 00 Wm. C,Lipscomb. do : for) Virginia. 1000 00 Thos. B. Addison. f Record Clerk con-> Maryland 1000 00 < routes and v....) Matthias Ross f. tracts, N. Div, N. Jersey1000 00 David Koones Dead Letter Office Maryland 1000 00 Presley Simpson... Examiner's Office Virginia- 1000 00 Grafton D. Hanson. Solicitor's Office.. Maryland 1000 00 Walter D. Addison. Recorder, Div. of Acc'ts do.. -

Treasury, HUD Submit Housing Reform Plans Federal Reserve Proposes
In classic Greek mythology, a golden apple of discord inscribed "For the fairest" was awarded to Aphrodite, beginning a chain of events that led to the Trojan War. GrayRobinson's newsletter reports on the most recent issues, individuals, and discourse deemed fairest in Washington. September 6, 2019 . aaaand we’re back. How was your August? We are thankful that our offices in Melbourne and Jacksonville, among others, were spared the worst of Hurricane Dorian, but the hurricane season still has almost three months to run. Stay safe, everybody. Treasury, HUD submit housing reform plans Treasury Secretary Steven Mnuchin and Housing and Urban Development Secretary Ben Carson submitted two plans to the White House yesterday for ending the conservatorship of Fannie Mae and Freddie Mac, restructuring the government guarantees for housing loans, and protecting taxpayers from further liability. The Treasury report calls for almost 50 legislative changes to limit the government’s role in the secondary market, enhance taxpayer protections, and encourage private-sector competition. “At the same time, reform should not and need not wait on Congress,” the report said. The HUD plan would “refocus” the Federal Housing Administration on its “core mission of helping low- and moderate-income borrowers.” Mnuchin, Carson, and Federal Housing Finance Administration Director Mark Calabria will appear before the Senate Banking Committee next Tuesday to discuss the plans. Senate Banking Committee Chairman Mike Crapo (R- ID) said yesterday that many of the Treasury plan’s provisions corresponded to elements of his own proposal, and that he would prefer “to fix the housing finance system through legislation.” Federal Reserve proposes capital requirements for insurance companies that own banks Today the Federal Reserve published a long-awaited proposal to create a capital framework for the eight insurance companies that own banks. -

Commander Ship Port Tons Mate Gunner Boatswain Carpenter Cook
www.1812privateers.org ©Michael Dun Commander Ship Port Tons Mate Gunner Boatswain Carpenter Cook Surgeon William Auld Dalmarnock Glasgow 315 John Auld Robert Miller Peter Johnston Donald Smith Robert Paton William McAlpin Robert McGeorge Diana Glasgow 305 John Dal ? Henry Moss William Long John Birch Henry Jukes William Morgan William Abrams Dunlop Glasgow 331 David Hogg John Williams John Simpson William James John Nelson - Duncan Grey Eclipse Glasgow 263 James Foulke Martin Lawrence Joseph Kelly John Kerr Robert Moss - John Barr Cumming Edward Glasgow 236 John Jenkins James Lee Richard Wiles Thomas Long James Anderson William Bridger Alexander Hardie Emperor Alexander Glasgow 327 John Jones William Jones John Thomas William Thomas James Williams James Thomas Thomas Pollock Lousia Glasgow 324 Alexander McLauren Robert Caldwell Solomon Piike John Duncan James Caldwell none John Bald Maria Glasgow 309 Charles Nelson James Cotton? John George Thomas Wood William Lamb Richard Smith James Bogg Monarch Glasgow 375 Archibald Stewart Thomas Boutfield William Dial Lachlan McLean Donald Docherty none George Bell Bellona Greenock 361 James Wise Thomas Jones Alexander Wigley Philip Johnson Richard Dixon Thomas Dacers Daniel McLarty Caesar Greenock 432 Mathew Simpson John Thomson William Wilson Archibald Stewart Donald McKechnie William Lee Thomas Boag Caledonia Greenock 623 Thomas Wills James Barnes Richard Lee George Hunt William Richards Charles Bailey William Atholl Defiance Greenock 346 James McCullum Francis Duffin John Senston Robert Beck -

Official List of Members
OFFICIAL LIST OF MEMBERS OF THE HOUSE OF REPRESENTATIVES of the UNITED STATES AND THEIR PLACES OF RESIDENCE ONE HUNDRED SIXTEENTH CONGRESS • DECEMBER 15, 2020 Compiled by CHERYL L. JOHNSON, Clerk of the House of Representatives http://clerk.house.gov Democrats in roman (233); Republicans in italic (195); Independents and Libertarians underlined (2); vacancies (5) CA08, CA50, GA14, NC11, TX04; total 435. The number preceding the name is the Member's district. ALABAMA 1 Bradley Byrne .............................................. Fairhope 2 Martha Roby ................................................ Montgomery 3 Mike Rogers ................................................. Anniston 4 Robert B. Aderholt ....................................... Haleyville 5 Mo Brooks .................................................... Huntsville 6 Gary J. Palmer ............................................ Hoover 7 Terri A. Sewell ............................................. Birmingham ALASKA AT LARGE Don Young .................................................... Fort Yukon ARIZONA 1 Tom O'Halleran ........................................... Sedona 2 Ann Kirkpatrick .......................................... Tucson 3 Raúl M. Grijalva .......................................... Tucson 4 Paul A. Gosar ............................................... Prescott 5 Andy Biggs ................................................... Gilbert 6 David Schweikert ........................................ Fountain Hills 7 Ruben Gallego ............................................ -
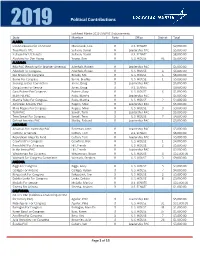
2019 Political Contributions
MEPAC Disbursement Political Contributions 2019 Lockheed Martin 2019 LMEPAC Disbursements State Member Party Office District Total ALASKA Lisa Murkowski for US Senate Murkowski, Lisa R U.S. SENATE $2,000.00 True North PAC Sullivan, Daniel R Leadership PAC $5,000.00 Sullivan For US Senate Sullivan, Daniel R U.S. SENATE $8,000.00 Alaskans For Don Young Young, Don R U.S. HOUSE AL $5,000.00 ALABAMA RBA PAC (Reaching for Brighter America) Aderholt, Robert R Leadership PAC $5,000.00 Aderholt for Congress Aderholt, Robert R U.S. HOUSE 4 $6,000.00 Mo Brooks for Congress Brooks, Mo R U.S. HOUSE 5 $6,000.00 Byrne For Congress Byrne, Bradley R U.S. HOUSE 1 $5,000.00 Seeking Justice Committee Jones, Doug D Leadership PAC $5,000.00 Doug Jones For Senate Jones, Doug D U.S. SENATE $9,000.00 Gary Palmer For Congress Palmer, Gary R U.S. HOUSE 6 $1,000.00 MARTHA PAC Roby, Martha R Leadership PAC $5,000.00 Martha Roby For Congress Roby, Martha R U.S. HOUSE 2 $4,000.00 American Security PAC Rogers, Mike R Leadership PAC $5,000.00 Mike Rogers For Congress Rogers, Mike R U.S. HOUSE 3 $9,000.00 Terri PAC Sewell, Terri D Leadership PAC $5,000.00 Terri Sewell For Congress Sewell, Terri D U.S. HOUSE 7 $4,000.00 Defend America PAC Shelby, Richard R Leadership PAC $5,000.00 ARKANSAS Arkansas for Leadership PAC Boozman, John R Leadership PAC $5,000.00 Cotton For Senate Cotton, Tom R U.S. -

Final 1991 Division I Baseball
-----------------------------------------------------------------------------------------------------------------)------ ----- -- -- ------ -------- ----- -------------------------------------------- ---- ---- ------ --- FINAL 1991 DIVISION I BASEBALL. BATTING BATTING (2. 5 ab/game and 75 at bats) AB HTS AVG. (2. 5 ab/game and 75 at bats) AB HTS AVG. 1. Ron Dziezgowski, Duquesne SR 33 88 500 36. Matt Raleigh, Western Caro. ------- JR 62 223 92 . 413 2. Gene Schall, Villanova ------------ JR 40 155 75 484 37. Brent Gates , Minnesota ------------ JR 64 221 91 . 412 Mike Neill, Villanova ------------- JR 52 216 101 468 37. chris Sexton, Miami (Ohio) -------- SO 49 153 63 . 412 C. Hendrix, Campbell ------------ JR 52 192 89 464 39. Jason Geis , Portland -------------- JR 42 146 60 . 411 Tom Vantiger , Iowa St. ------------ SR 58 177 82 463 40. Glen Taylor, Iona ----------------- SR 36 105 43 410 Al Watson, New York Tech ---------- JR 52 188 87 463 41. John Callihan, Mercer ------------- JR 45 169 69 . 408 Mike Carlsen , FDU-Teaneck --------- JR 40 145 67 462 42. Jason Giambi, Long Beach St. ------ SO 60 199 81 . 407 Mike Edwards , Utah ---------------- SO 53 184 84 457 42. Greg Elliott, Md. -BaIt. County ---- SO 49 199 81 . 407 9. Scott Stahoviak, Creighton JR 72 267 120 449 44. Mike Welch, Geo. Washington ------- JR 56 209 85 . 407 10. Jon Sbrocco, Wright St. ----------- SO 51 179 80 447 45. Bob Higginson, Temple ------------- SO 46 156 63 . 404 11. John Burns, Md. -BaIt. County ------ SO 46 188 84 447 46. Ricky Bush, Jackson St. SR 34 114 46 . 404 12. Larry Sutton, Illinois ------------ JR 47 155 69 445 47. Ken Cavazzoni, Columbia ----------- SR 35 124 50 . 403 13. James Ruocchio, LIU-C. W. Post ----- SR 43 165 72 436 48. -

Over 270 Alumni Have Passed from Recreation Ballpark to the Major
Over 270 alumni have passed from Recreation Ballpark to the Major Leagues since 1946, including Hall of Famer Kirby Puckett and Cy Young Award winners Barry Zito and Max Scherzer. Here's a full list: In total, 290 Visalia alumni have reached the Major Leagues (through the 2018 season): Bob Talbot, OF, Cubs, 1953-54 Doug Hansen, OF, Indians, 1951 Eddie Winceniak, SS, Cubs, 1956-57 Howie Goss, OF, Pirates, Colt 45s, 1962-63 Chuck Essegian, OF, Phillies, Cardinals, Indians, Angels, Royals, 1958-75 Marty Kutyna, P, Athletics, Senators, 1959-62 Vic Davalillo, OF, Indians, Cardinals, Pirates, Athletics, Dodgers, 1963-80 Vada Pinson - *NL-GG '61*, OF, Reds, Cardinals, Dodgers, Orioles, Indians, Athletics, 1958-75 Joe Gains, OF, Reds, Orioles, Astros, 1960-66 Jack Baldschun, P, Phillies, Reds, Padres, 1961-67, 1969-70 Ken Hunt, P, Reds, 1961 Johnny Edwards *NL-GG '63, '64*, C, Reds, Cardinals, Astros, 1961-74 Hiraldo (Chico) Ruiz, INF, Reds, Angels, 1964-71 Jack Aker, P, Athletics, Pilots, Yankees, Cubs, Braves, Mets, 1964-74 Ken Harrelson, 1B-OF, Athletics, Senators, Red Sox, Indians, 1963-71 John Wojcik, OF, Athletics, 1962-64 Larry Stahl, OF, Athletics, Mets, Padres, Reds, 1964-73 Bill Landis, P, Athletics, Red Sox, 1963, 1967-69 Jose Santiago, P, Athletics, Red Sox, 1963-70 Cisco Carlos, P, White Sox, Senators, 1967-70 Dick Kenworthy, INF, White Sox, 1962-68 Ken Berry, OF, White Sox, Brewers, Indians, 1962-75 Ernie McAnally, P, Mets, 1971-74 Bruce Boisclair, OF, Mets, 1974-79 Charlie Williams, P, Mets, Giants, 1971-78 Ken Singleton *RC '82*, -

College Baseball Foundation January 30, 2008 Boyd, Thank You For
College Baseball Foundation P.O. Box 6507 Phone: 806-742-0301 x249 Lubbock TX 79493-6507 E-mail: [email protected] January 30, 2008 Boyd, Thank you for participating in the balloting for the College Baseball Hall of Fame’s 2008 Induction Class. We appreciate your willingness to help. In the voters packet you will find the official ballot, an example ballot, and the nominee biographies: 1. The official ballot is what you return to us. Please return to us no later than Mon- day, February 11. 2. The example ballot’s purpose is to demonstrate the balloting rules. Obviously the names on the example ballot are not the nominee names. That was done to prevent you from being biased by the rankings you see there. 3. Each nominee has a profile in the biography packet. Some are more detailed than others and reflect what we received from the institutions and/or obtained in our own research. The ballot instructions are somewhat detailed, so be sure to read the directions at the top of the official ballot. Use the example ballot as a reference. Please try to consider the nominees based on their collegiate careers. In many cases nominees have gone on to professional careers but keep the focus on his college career as a player and/or coach. The Veterans (pre-1947) nominees often lack biographical details relative to those in the post-1947 categories. In those cases, the criteria may take on a broader spectrum to include the impact they had on the game/history of college baseball, etc. -

Thomas Woodrow Wilson James Madison* James Monroe* Edith
FAMOUS MEMBERS OF THE JEFFERSON SOCIETY PRESIDENTS OF THE UNITED STATES OF AMERICA Thomas Woodrow Wilson James Madison∗ James Monroe∗ FIRST LADIES OF THE UNITED STATES Edith Bolling Galt Wilson∗ PRIME MINISTERS OF THE UNITED KINGDOM Margaret H. Thatcher, Baroness Thatcher∗ SPEAKERS OF THE UNITED STATES HOUSE OF REPRESENTATIVES Robert Mercer Taliaferro Hunter UNITED STATES SENATORS Oscar W. Underwood, Senate Minority Leader, Alabama Hugh Scott, Senate Minority Leader, Pennsylvania Robert Mercer Taliaferro Hunter, Virginia Willis P. Bocock, Virginia John S. Barbour Jr., Virginia Harry F. Byrd Jr., Virginia John Warwick Daniel, Virginia Claude A. Swanson, Virginia Charles J. Faulkner, West Virginia John Sharp Williams, Mississippi John W. Stevenson, Kentucky Robert Toombs, Georgia Clement C. Clay, Alabama Louis Wigfall, Texas Charles Allen Culberson, Texas William Cabell Bruce, Maryland Eugene J. McCarthy, Minnesota∗ James Monroe, Virginia∗ MEMBERS OF THE UNITED STATES HOUSE OF REPRESENTATIVES Oscar W. Underwood, House Majority Leader, Alabama John Sharp Williams, House Minority Leader, Mississippi Robert Mercer Taliaferro Hunter, Virginia Richard Parker, Virginia Robert A. Thompson, Virginia Thomas H. Bayly, Virginia Richard L. T. Beale, Virginia William Ballard Preston, Virginia John S. Caskie, Virginia Alexander H. H. Stuart, Virginia James Alexander Seddon, Virginia John Randolph Tucker, Virginia Roger A. Pryor, Virginia John Critcher, Virginia Colgate W. Darden, Virginia Claude A. Swanson, Virginia John S. Barbour Jr., Virginia William L. Wilson, West Virginia Wharton J. Green, North Carolina William Waters Boyce, South Carolina Hugh Scott, Pennsylvania Joseph Chappell Hutcheson, Texas John W. Stevenson, Kentucky Robert Toombs, Georgia Thomas W. Ligon, Maryland Augustus Maxwell, Florida William Henry Brockenbrough, Florida Eugene J. -

List of Government Officials (May 2020)
Updated 12/07/2020 GOVERNMENT OFFICIALS PRESIDENT President Donald John Trump VICE PRESIDENT Vice President Michael Richard Pence HEADS OF EXECUTIVE DEPARTMENTS Secretary of Health and Human Services Alex Azar II Attorney General William Barr Secretary of Interior David Bernhardt Secretary of Energy Danny Ray Brouillette Secretary of Housing and Urban Development Benjamin Carson Sr. Secretary of Transportation Elaine Chao Secretary of Education Elisabeth DeVos (Acting) Secretary of Defense Christopher D. Miller Secretary of Treasury Steven Mnuchin Secretary of Agriculture George “Sonny” Perdue III Secretary of State Michael Pompeo Secretary of Commerce Wilbur Ross Jr. Secretary of Labor Eugene Scalia Secretary of Veterans Affairs Robert Wilkie Jr. (Acting) Secretary of Homeland Security Chad Wolf MEMBERS OF CONGRESS Ralph Abraham Jr. Alma Adams Robert Aderholt Peter Aguilar Andrew Lamar Alexander Jr. Richard “Rick” Allen Colin Allred Justin Amash Mark Amodei Kelly Armstrong Jodey Arrington Cynthia “Cindy” Axne Brian Babin Donald Bacon James “Jim” Baird William Troy Balderson Tammy Baldwin James “Jim” Edward Banks Garland Hale “Andy” Barr Nanette Barragán John Barrasso III Karen Bass Joyce Beatty Michael Bennet Amerish Babulal “Ami” Bera John Warren “Jack” Bergman Donald Sternoff Beyer Jr. Andrew Steven “Andy” Biggs Gus M. Bilirakis James Daniel Bishop Robert Bishop Sanford Bishop Jr. Marsha Blackburn Earl Blumenauer Richard Blumenthal Roy Blunt Lisa Blunt Rochester Suzanne Bonamici Cory Booker John Boozman Michael Bost Brendan Boyle Kevin Brady Michael K. Braun Anthony Brindisi Morris Jackson “Mo” Brooks Jr. Susan Brooks Anthony G. Brown Sherrod Brown Julia Brownley Vernon G. Buchanan Kenneth Buck Larry Bucshon Theodore “Ted” Budd Timothy Burchett Michael C. -

Henry Carter Stuart in Virginia Folitics 1855-1933
HENRY CARTER STUART IN VIRGINIA FOLITICS 1855-1933 Charles Evans Poston Columbia, South Carol i.na BoAo, University of Richmond, 1968 A Thesis Presented to the Graduate Faculty of the University of Virginia in Candidacy for the Degree of Master of Arts Corcoran Department of History University of Virginia June 1970 :.'.c\.EFACE lic'nry C;,i·tL:r Stu,n·t, Governor of Virginiu from 1914 to 1918, has been 3 ph,,ntom-like figure in Virginia history. Ile has never been subjected to the scrutiny of close and systematic study; ye� those familiar with his career, while not painting him as a wc�k governor, have not portraycci his administration as particularly striking either. Moreover, Stuart's relationship to the Demo cratic Party in the first two decades of this century is blurred. Some historians of the period place him squarely in the Martin org anization ranks as early as 1909; others consioer him an independent until 1920 at least. This essay seeks to clarify Stuart's political affilic1tions in Virginia. Moreover, while its sights are not firmly focused on hi� governorship, enough work has been done to indicate i i is major pcLicies as governor and to offer some evaluation of them. An iL-depth study of Stuart's a dministration, however, must await a iurcher study which is planned as a doctoral dissertation. The staff of the Virginia State Library in Richmond was most he��ful during the cowrsc o� researching the �a�cr, as was the sta:f of the University.of Virginia's Alderffi2n Li�rary. -

Heroes and Rallies Baseball
Heroes and Rallies Baseball Setup Pick two teams to go head to head, and fill out your lineups on the scoresheet. Each team receives 8 skill assignments to give to individual players. All of the skill assignments listed below must be used within your starting lineup for a total of 8. A player may possess two assignments if you wish. Rate your lineup by placing the appropriate notation beside a player’s name on the scoresheet. 1) star hitter (H) 2) star slugger (S) 3) star runner (R) 4) star fielder (F) 5) poor hitter (H-) 6) weak hitter (S-) 7) slow runner (R-) 8) poor fielder (F-) Once a player has a skill assignment, he cannot transfer it to another player. There is one additional skill assignment available for an ace pitcher (X). You may, however, choose not to start one. Make any pitcher a poor hitter as well (H-), so there will be two poor hitters if a pitcher is in the lineup. Game Play Roll the dice for each player who comes up to bat, reading the colored die first and the white die second. If a result occurs on the Batting chart which displays an image of a ballplayer, the inning is considered finished with no further scoring. Draw an X in the box on the scoresheet representing the current hitter’s at-bat. When his team next comes up to bat, the next player in the lineup will hit. If the color of a chart result corresponds to the color of the skill assignment of the player who is currently up to bat, the result changes to the one shown on the bottom of the Batting chart.