COMPUTER VIRUS] 130 Questions Collections
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 6 Working with Windows and DOS Systems Objectives • Explain the purpose and structure of file systems • Describe Microsoft file structures • Explain the structure of New Technology File System (NTFS) disks • List some options for decrypting drives encrypted with whole disk encryption Guide to Computer Forensics and Investigations 2 Objectives (continued) • Explain how the Windows Registry works • Describe Microsoft startup tasks • Describe MS-DOS startup tasks • Explain the purpose of a virtual machine Guide to Computer Forensics and Investigations 3 Understanding File Systems • File system – Gives OS a road map to data on a disk • Type of file system an OS uses determines how data is stored on the disk • A file system is usually directly related to an OS • When you need to access a suspect’s computer to acquire or inspect data – You should be familiar with the computer’s platform Guide to Computer Forensics and Investigations 4 Understanding the Boot Sequence • Complementary Metal Oxide Semiconductor (CMOS) – Computer stores system configuration and date and time information in the CMOS • When power to the system is off • Basic Input/Output System (BIOS) – Contains programs that perform input and output at the hardware level Guide to Computer Forensics and Investigations 5 Understanding the Boot Sequence (continued) • Bootstrap process – Contained in ROM, tells the computer how to proceed – Displays the key or keys you press to open the CMOS setup screen • CMOS should -

UM1721 User Manual Developing Applications on Stm32cube™ with Fatfs
UM1721 User manual Developing applications on STM32Cube™ with FatFs Introduction The STM32Cube™ is an STMicroelectronics original initiative to make developers’ lives easier by reducing development effort, time and cost. STM32Cube™ covers the whole STM32 portfolio. STM32Cube™ includes: • STM32CubeMX, a graphical software configuration tool that allows the generation of C initialization code using graphical wizards. • A comprehensive embedded software platform, delivered per Series (such as STM32CubeF4 for STM32F4 Series) – The STM32Cube™ HAL, STM32 abstraction layer embedded software ensuring maximized portability across the STM32 portfolio, – A consistent set of middleware components such as RTOS, USB, TCP/IP, Graphics, – All embedded software utilities, delivered with a full set of examples. A file system is the way in which files ares named and where they are placed logically for storage and retrieval. Its primary objective is to manage access to the data of files, and to manage the available space of the device(s) which contain it. Using a file system allows user to ensure reliability and to organize data in an efficient manner. This user manual is intended for developers who use STM32Cube™ MCU Package on STM32 microcontrollers. It provides a full description of how to use the STM32Cube™ firmware components with a generic FAT file system (FatFs); this user manual comes also with description of a set of examples based on common FatFs provided APIs. Please refer to the release notes of the STM32Cube™ MCU Package to know the version of FatFs firmware component used. This document is applicable to all STM32 devices; however for simplicity reason, the STM32F4xx devices and STM32CubeF4 are used as reference platform. -
COMPUTER VIRUSES: the Technology and Evolution of an Artificial Life Form
COMPUTER VIRUSES: The Technology and Evolution of an Artificial Life Form Written by: Karsten Johansson, 1994 NOTE: This document was written before the advent of Internet worms and trojans. It probably contains more information about the pre-commercial internet virus scene than any other singular source, and thus I have opted to make it available to the Internet as a historical reference. There are a couple of unfinished sections, but maybe if there is enough interest, I may be convinced to finish this and update it to reflect the current state of the malware industry, and update the Artificial Life stuff since so much has happened there since 1994. Permission is granted to use this information in any legitimate manner as long as (1) my copyright is maintained, (2) you give me credit for all material used, and (3) you send an email to [email protected] so I know where and how my research and writing is being used. There is no copy restriction on this document for reading or distribution, but (4) under no circumstances is sale or profit directly from my work permitted without my implicit authorization. (5) If distributed, this document must remain in its entirety, and shall not be altered from the original PDF file distributed at http://www.penetrationtest.com. Publishers interested in this manuscript or any of my other works may contact me at the same email address. Table of Contents COMPUTER VIRUSES: The Technology and Evolution of an Artificial Life Form............................................................................... 1 Table of Contents ........................................................................... 1 COMPUTER VIRUSES: The Technology and Evolution of an Artificial Life Form.............................................................................. -
A Computer Virus Primer
Purdue University Purdue e-Pubs Department of Computer Science Technical Reports Department of Computer Science 1989 A Computer Virus Primer Eugene H. Spafford Purdue University, [email protected] Kathleen A. Heaphy David J. Ferbrache Report Number: 89-935 Spafford, Eugene H.; Heaphy, Kathleen A.; and Ferbrache, David J., "A Computer Virus Primer" (1989). Department of Computer Science Technical Reports. Paper 795. https://docs.lib.purdue.edu/cstech/795 This document has been made available through Purdue e-Pubs, a service of the Purdue University Libraries. Please contact [email protected] for additional information. A COMPUTER VIRUS PRIMER Eugene H. Spafford Kathleen A. Heaphy David J. Ferbrache CSD TR-935 November 1989 A Computer Virus Primer1 Purdue University Technical Report CSD-TR-935 Eugene H. Spafford Kathleen A. Heaphy David J. Ferbrache 28 November 1989 1@ Copyright 1989 by ADAPSO, Inc. and Eugene H. SpaJford. All rights reserved. Abstract There has been considerable interest of late in computer viruses. Much of the information available is either of a highly theoretical nature, or describes a specific set of viruses. Neither is useful for providing an overview of how computer viruses work or how to protect against them. This report is a condensed explanation of viruses-their history, structure, and some information on how to deal with their threat. It should provide a general introduction to the topic without requiring the understanding of excessive detail. The interested reader is directed to the book from which this report is derived for further infor mation, including references to related works and sources, more technical detail, and information on some of the legal aspects ofcomputer viruses: Computer Viruses: Dealing with Electronic Vandalism and Programmed Threats, E. -
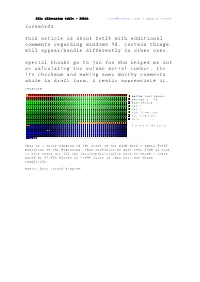
File Allocation Table - 16Bit [email protected] | Updates Closed Forewords This Article Is About Fat16 with Additional Comments Regarding Windows 98
file allocation table - 16bit [email protected] | updates closed forewords this article is about fat16 with additional comments regarding windows 98. certain things will appear/handle differently in other oses. special thanks go to jon fox who helped me out on calculating the volume serial number, the lfn checksum and making some worthy comments while in draft form, i really appreaciate it. overview master boot record sectors 1 - 62 boot record fat 1 fat 2 root directory sub directory data 1 block = 512 bytes this is a scale diagram of the start of the disk with a small fat16 partition at the beginning. this partition is just over 20mb in size, to save space not all the data/subdir/surplus area is shown - there would be 44,815 blocks or ~=896 lines if this part was shown completely. master boot record diagram -> executable code -> ending head -> boot indicator -> ending sector & -> starting head cylinder -> starting sector & -> the starting cylinder sector -> partiton type -> no. of sectors in partition -> executable signature 1 partition entry is as follows: and reads as: mbr in general ( =512 bytes ) the master boot record (mbr) is located in the first data sector on the hard disk. the mbr can have upto 4 primary partitions, each entry occupies 16 bytes. if the slot is unused, the space is filled with 00. each entry sets out the addressing parameters for the partition. hard disks have grown considerably in size since they were first invented, this has caused some strange addressing techniques to be used to ensure compatibility. hard drives used to be addressed by cylinder, head and sector (chs). -

Active@ Partition Recovery User Guide
Active@ Partition Recovery User Guide 1 Active@ Partition Recovery Guide Copyright © 1999-2018, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. Active@ Partition Recovery, the Active@ Partition Recovery logo, Partition Recovery Software are trademarks of LSOFT TECHNOLOGIES INC. Active Data Recovery Software is a business name of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. Active@ Partition Recovery Guide 2 Contents Overview................................................................................................................................ 4 Using QuickScan to detect partitions just deleted ...................................................................... 6 Using SuperScan to analyze deleted and severely damaged volumes ........................................ -

File Allocation Table
File Allocation Table File Allocation Table (FAT) is a computer file system architecture and a FAT family of industry-standard file systems utilizing it. The FAT file system is a continuing standard which borrows source code from the original, legacy file Developer(s) Microsoft, NCR, system and proves to be simple and robust.[3] It offers useful performance SCP, IBM, Compaq, even in lightweight implementations, but cannot deliver the same Digital Research, performance, reliability and scalability as some modern file systems. It is, Novell, Caldera however, supported for compatibility reasons by nearly all currently developed Full name File Allocation Table operating systems for personal computers and many mobile devices and Variants 8-bit FAT, FAT12, embedded systems, and thus is a well-suited format for data exchange FAT16, FAT16B, between computers and devices of almost any type and age from 1981 up to FAT32, ExFAT, the present. FATX, FAT+ Originally designed in 1977 for use on floppy disks, FAT was soon adapted and Introduced 1977 with used almost universally on hard disks throughout the DOS and Windows 9x Standalone Disk eras for two decades.[4] As disk drives evolved, the capabilities of the file BASIC-80 system have been extended accordingly, resulting in three major file system Partition MBR/EBR: variants: FAT12, FAT16 and FAT32. The FAT standard has also been expanded identifier FAT12: 0x01 e.a. in other ways while generally preserving backward compatibility with existing (Extended Attribute) software. FAT16: 0x04 0x06 0x0E e.a. With the introduction of more powerful computers and operating systems, as FAT32: 0x0B 0x0C e.a. -

Computer Viruses Demystified Viruses
Computer viruses demystified Viruses Email Internet Mobile devices Safety Reference Computer viruses demystified Contents Viruses Why viruses matter 5 Email Viruses, Trojans and worms 7 Internet Virus hoaxes 23 Mobile devices Top 10 viruses 27 Email 33 Safety The internet 39 Reference Mobile phones and palmtops 47 Ten steps to safer computing 55 Useful links 59 Glossary 61 Index 69 Contents 3 4 Why viruses matter VVirusesiruses Email Computer viruses, hackers, crackers, data crime. They make headline news and – so Internet the media claim – cost us millions. But do viruses and all the other nasties in Mobile devices cyberspace matter? Do they really do much harm? Safety If you’re in any doubt, just try imagining Reference what could happen in your office or home. Imagine that no-one has updated your anti-virus software for a few months. When they do, you find that your accounts spreadsheets are infected with a new virus that changes figures at random. Naturally you keep backups. But you might have been backing up infected files for months. How do you know which figures to trust? Now imagine that a new email virus has been released. Your company is receiving so many emails that you decide to shut down your email gateway altogether … and miss an urgent order from a big customer. Why viruses Suppose that you’ve been studying at home for an MBA. matter You’ve almost finished your dissertation when one of your 5 children puts a new game on your PC and infects it. The VVirusesiruses virus deletes everything on the hard drive … including all your hard work. -

Virus Bulletin, October 1995
ISSN 0956-9979 OCTOBER 1995 THE INTERNATIONAL PUBLICATION ON COMPUTER VIRUS PREVENTION, RECOGNITION AND REMOVAL Editor: Ian Whalley CONTENTS Assistant Editor: Megan Palfrey EDITORIAL Technical Editor: Jakub Kaminski ‘…and it infects PDP11 executables as well…’ 2 Consulting Editors: VIRUS PREVALENCE TABLE 3 Richard Ford, NCSA, USA Edward Wilding, Network Security, UK NEWS 1. WinWord.Concept 3 2. Virus Awareness Campaign 3 IBM PC VIRUSES (UPDATE) 4 IN THIS ISSUE: INSIGHT • Hacking around. Our former editor, Richard Ford, put on a Where My Eyes Look 6 hacker’s hat for a few days and visited a different kind of CONFERENCE REPORT conference: read his report on p.9. DefCon: Fear and Loathing? 9 • What’s next, folks? Much media hype has been made of Microsoft’s new operating system, Windows 95. We discover VIRUS ANALYSES whether they noted our article on how viruses affect the system 1. Burglar: The New Pretender 10 (June 1995) in a series of follow-up tests – see p.14. 2. DiskWasher 12 • Detecting a new way. IBM has released a new version of its TUTORIAL anti-virus software for NetWare: is it an improvement on their Windows 95: Even Better than the Real Thing? 14 original? Turn to p.18 for our review. FEATURE Computer Viruses: Naming and Classification, Pt II 16 PRODUCT REVIEWS 1. IBM AntiVirus for NetWare 18 2. Norton Utilities 21 END NOTES & NEWS 24 VIRUS BULLETIN ©1995 Virus Bulletin Ltd, 21 The Quadrant, Abingdon, Oxfordshire, OX14 3YS, England. Tel +44 1235 555139. /95/$0.00+2.50 No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form without the prior written permission of the publishers. -

Partition Manager™ 12 Home
PARAGON Software GmbH Heinrich-von-Stephan-Str. 5c 79100 Freiburg, Germany Tel. +49 (0) 761 59018201 Fax +49 (0) 761 59018130 Internet www.paragon-software.com Email [email protected] Partition Manager™ 12 Home User Manual Copyright© 1994-2013 Paragon Software GmbH. All rights reserved. 2 Contents Introduction .......................................................................................................................... 5 What’s New in Partition Manager 12 ........................................................................................................... 5 Product Components ............................................................................................................. 5 Features Overview ................................................................................................................. 5 Features ..................................................................................................................................................... 5 User Friendly Fault Minimizing Interface ................................................................................................................................ 5 Backup Facilities ...................................................................................................................................................................... 6 Restore Facilities ....................................................................................................................................................................