GW CSPRI Newsletter
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mayor and City Council Members FROM: Rob Hunt
TO: Mayor and City Council Members FROM: Rob Hunt, Interim City Manager SUBJECT: April 16, 2019 Agenda Items DATE: April 11, 2019 7:00 p.m. I. CALL TO ORDER REGULAR SESSION II. PLEDGE OF ALLEGIANCE AND INVOCATION III. CITIZEN COMMENTS This is the time for citizens to comment on subject matters, not on the agenda within the jurisdiction of the Tulare City Council. The Council Members ask that you keep your comments brief and positive. Creative criticism, presented with appropriate courtesy, is welcome. The Council cannot legally discuss or take official action on citizen request items that are introduced tonight. This is also the time for citizens to comment on items listed under the Consent Calendar or to request an item from the Consent Calendar be pulled for discussion purposes. Comments related to general business/city manager items or public hearing items will be heard at the time the item is discussed or at the time the Public Hearing is opened for comment. In fairness to all who wish to speak, each speaker will be allowed three minutes, with a maximum time of 15 minutes per item, unless otherwise extended by Council. Please begin your comments by stating and spelling your name and providing your city of residence. IV. COMMUNICATIONS Communications are to be submitted to the City Manager’s Office 10 days prior to a Council Meeting to be considered for this section of the Agenda. No action will be taken on matters listed under communications; however, the Council may direct staff to schedule issues raised during communications for a future agenda. -
Directory Great Basin Coordination and Dispatch
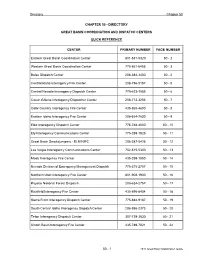
Directory Chapter 50 CHAPTER 50 - DIRECTORY GREAT BASIN COORDINATION AND DISPATCH CENTERS QUICK REFERENCE CENTER PRIMARY NUMBER PAGE NUMBER Eastern Great Basin Coordination Center 801-531-5320 50 - 2 Western Great Basin Coordination Center 775-861-6455 50 - 3 Boise Dispatch Center 208-384-3400 50 - 4 Central Idaho Interagency Fire Center 208-756-5157 50 - 5 Central Nevada Interagency Dispatch Center 775-623-1555 50 - 6 Coeur d'Alene Interagency Dispatcher Center 208-772-3283 50 - 7 Color Country Interagency Fire Center 435-865-4600 50 - 8 Eastern Idaho Interagency Fire Center 208-524-7600 50 - 9 Elko Interagency Dispatch Center 775-748-4000 50 - 10 Ely Interagency Communications Center 775-289-1925 50 - 11 Great Basin Smokejumpers - BLM NIFC 208-387-5426 50 - 12 Las Vegas Interagency Communications Center 702-515-5300 50 - 13 Moab Interagency Fire Center 435-259-1850 50 - 14 Nevada Division of Emergency Management Dispatch 775-315-2757 50 - 15 Northern Utah Interagency Fire Center 801-908-1900 50 - 16 Payette National Forest Dispatch 208-634-2757 50 - 17 Richfield Interagency Fire Center 435-896-8404 50 - 18 Sierra Front Interagency Dispatch Center 775-882-9187 50 - 19 South Central Idaho Interagency Dispatch Center 208-886-2373 50 - 20 Teton Interagency Dispatch Center 307-739-3630 50 - 21 Uintah Basin Interagency Fire Center 435-789-7021 50 - 22 50 - 1 2012 Great Basin Mobilization Guide Directory Chapter 50 UNIT: FIRE PHONE NUMBER: 801-531-5320 EASTERN GREAT BASIN COORDINATION CENTER NIGHT OR 24 HR PHONE NUMBER: 5500 W. Amelia Earhart -

Connection – Summer 2018
ConnectionCHRISTIAN BROTHERS SUMMER 2018 THE CHRISTIAN BROTHERS 150 Years in California A PUBLICATION FOR THE ALUMNI, PARENTS & FRIENDS OF CHRISTIAN BROTHERS HIGH SCHOOL CB Leadership Team Lorcan P. Barnes President Chris Orr Principal June McBride Board of Trustees Director of Finance David Desmond ’94 The Board of Trustees at Christian Brothers High School is comprised of 11 volunteers Assistant Principal dedicated to safeguarding and advancing the school’s Lasallian Catholic college preparatory mission. Before joining the Board of Trustees, candidates undergo Michelle Williams training on Lasallian charism (history, spirituality and philosophy of education) and Assistant Principal Policy Governance, a model used by Lasallian schools throughout the District of Myra Makelim San Francisco New Orleans. In the 2017–18 school year, the board welcomed two new Human Resources Director members, Marianne Evashenk and Heidi Harrison. David Walrath serves in the role of chair and Mr. Stephen Mahaney ’69 is the vice chair. Kristen McCarthy Director of Admissions & The Policy Governance model comprises an inclusive, written set of goals for the school, Communications called Ends Policies, which guide the board in monitoring the performance of the school through the President/CEO. Ends Policies help ensure that Christian Brothers High Nancy Smith-Fagan School adheres to the vision of the Brothers of the Christian Schools and the District Director of Advancement of San Francisco New Orleans. “The Board thanks the families who have entrusted their children to our school,” says Chair David Walrath. “We are constantly amazed by our unbelievable students. They are creative, hardworking and committed to the Lasallian Core Principles. Assisting Connection is a publication of these students are the school’s faculty, staff and administration. -

The New Yorker-20180326.Pdf
PRICE $8.99 MAR. 26, 2018 MARCH 26, 2018 6 GOINGS ON ABOUT TOWN 17 THE TALK OF THE TOWN Amy Davidson Sorkin on White House mayhem; Allbirds’ moral fibres; Trump’s Twitter blockees; Sheila Hicks looms large; #MeToo and men. ANNALS OF THEATRE Michael Schulman 22 The Ascension Marianne Elliott and “Angels in America.” SHOUTS & MURMURS Ian Frazier 27 The British Museum of Your Stuff ONWARD AND UPWARD WITH THE ARTS Hua Hsu 28 Hip-Hop’s New Frontier 88rising’s Asian imports. PROFILES Connie Bruck 36 California v. Trump Jerry Brown’s last term as governor. PORTFOLIO Sharif Hamza 48 Gun Country with Dana Goodyear Firearms enthusiasts of the Parkland generation. FICTION Tommy Orange 58 “The State” THE CRITICS A CRITIC AT LARGE Jill Lepore 64 Rachel Carson’s writings on the sea. BOOKS Adam Kirsch 73 Two new histories of the Jews. 77 Briefly Noted THE CURRENT CINEMA Anthony Lane 78 “Tomb Raider,” “Isle of Dogs.” POEMS J. Estanislao Lopez 32 “Meditation on Beauty” Lucie Brock-Broido 44 “Giraffe” COVER Barry Blitt “Exposed” DRAWINGS Roz Chast, Zachary Kanin, Seth Fleishman, William Haefeli, Charlie Hankin, P. C. Vey, Bishakh Som, Peter Kuper, Carolita Johnson, Tom Cheney, Emily Flake, Edward Koren SPOTS Miguel Porlan CONTRIBUTORS The real story, in real time. Connie Bruck (“California v. Trump,” Hua Hsu (“Hip-Hop’s New Frontier,” p. 36) has been a staff writer since 1989. p. 28), a staff writer, is the author of “A She has published three books, among Floating Chinaman.” them “The Predators’ Ball.” Jill Lepore (A Critic at Large, p. -

Repartitie Aferenta Trimestrului I - 2019 - Straini DACIN SARA
Repartitie aferenta trimestrului I - 2019 - straini DACIN SARA TITLU TITLU ORIGINAL AN TARA R1 R2 R3 R4 R5 R6 R7 R8 S1 S2 S3 S4 S5 S6 S7 S8 13 13 2010 US Gela Babluani Gela Babluani Greg Pruss - Gregory Pruss Roland Emmerich - VG Roland Emmerich - VG 2012 2012 2009 US BILD KUNST Harald Kloser BILD KUNST 007: Coordonata Skyfall Skyfall 2012 GB/US Sam Mendes - ALCS Neal Purvis - ALCS Robert Wade - ALCS John Logan - ALCS 007: partea lui de consolare Quantum of Solace 2008 GB/US Marc Forster Neal Purvis - ALCS Robert Wade - ALCS Paul Haggis - ALCS 007: Viitorul e in mainile lui - 007 si Imperiul zilei de maine Tomorrow Never Dies 1997 GB/US Roger Spottiswoode Bruce Feirstein - ALCS Roland Emmerich - VG Roland Emmerich - VG 10 000 HR 10 000 BC 2008 US BILD KUNST Harlad Kloser BILD KUNST 1000 post Terra After Earth 2013 US M. Night Shyamalan Gary Whitta M. Night Shyamalan Binbir Gece - season 1, episode 1001 de nopti (ep.001) 1 2006 TR Kudret Sabanci - SETEM Yildiz Tunc Murat Lutfu Mehmet Bilal Ethem Yekta Binbir Gece - season 1, episode 1001 de nopti (ep.002) 2 2006 TR Kudret Sabanci - SETEM Yildiz Tunc Murat Lutfu Mehmet Bilal Ethem Yekta Binbir Gece - season 1, episode 1001 de nopti (ep.003) 3 2006 TR Kudret Sabanci - SETEM Yildiz Tunc Murat Lutfu Mehmet Bilal Ethem Yekta Binbir Gece - season 1, episode 1001 de nopti (ep.004) 4 2006 TR Kudret Sabanci - SETEM Yildiz Tunc Murat Lutfu Mehmet Bilal Ethem Yekta Binbir Gece - season 1, episode 1001 de nopti (ep.005) 5 2006 TR Kudret Sabanci - SETEM Yildiz Tunc Murat Lutfu Mehmet Bilal Ethem Yekta -

Tony Carey 2017
TONY CAREY [email protected], 310-617-6188, https://pro-labs.imdb.com/name/nm1814693/?ref_=sch_int PRODUCER/LINE PRODUCER “PEN15” - Budget & Prep Consultant, Awesomeness TV/HULU Single Camera Series 2017 - Present “ROB LOWE: Stories I Only Tell My Friends” – Live, One Man Show 2017 – Present Lowe Profile Productions “BILL MAHER LIVE” – Standup Tour Commercial Shoot 2017 “UMA & DEVAN, NAMASTE” - Sharmaji Prods, Toonz Media Group - Animated Pilot 2016 “STAN AGAINST EVIL” – Budget & Prep Consultant, Radical Media - IFC Single Cam Series 2016 “YOUNG & HUNGRY” – ABC Family Multicam Pilot & Series 2013 - 2015 The Tannenbaum Co., ProdCo, David Holden, Ashley Tisdale, Emily Osment “PARTNERS” – FX Multicam Series 2013 - 2014 Lionsgate, Bob Boyett, Robert Horn, Kelsey Grammer, Martin Lawrence “THE MILLERS” – CBS Productions, Greg Garcia, James Burrows - CBS Multicam Pilot 2013 UNTITLED TAD QUILL PILOT – CBS Multicam Pilot 2013 CBS Productions, Tad Quill, Mathew Broderick, Jimmy Burrows - Director “FRIEND ME” CBS Prods, The Tannenbaum Co, Chris Mintz Plasse - CBS Multicam Series 2012 “BEFORE WE MADE IT” – CBS Multicam Pilot 2012 Universal Television, CBS Productions, Berman-Braun, Spike Feresten UNTITLED MARTIN LAWRENCE PILOT – CBS Multicam Pilot 2012 CBS Productions, Mike Lisbe & Nate Reger, Martin Lawrence “¡ROB!” – CBS Multicam Pilots & Series 2011 - 2012 CBS Productions, The Tannenbaum Company, Lew Morton, Rob Schneider “DENNIS MILLER: THE BIG SPEECH” - HBO Standup Special 2010 Happy Family Prods, Brillstein Entertainment Partners, Marc Gurvitz, Dennis Miller “BEACH LANE” – NBC Multicam & Singlecam Pilot – New York, NY 2010 NBC Universal, Lorne Michaels, Paul Simms, Mathew Broderick PRODUCTION EXECUTIVE (see additional pages for production list ) QLA/GUTHRIE CASTLE LTD. - Production & Creative Consultant 2017 BET CABLE NETWORK - Production Executive, Consultant & EIC “Somebodies” 2008 - 2009 FX NETWORK - Vice President of Production 2006 - 2007 BRILLSTEIN - GREY ENTERTAINMENT - V.P. -

Bafta Rocliffe New Comedy Showcase
The BAFTA Rocliffe partnership holds four developmental Presenter and Rocliffe Producer BAFTA ROCLIFFE writing events annually in the UK and in the US. 2014 sees two FARAH ABUSHWESHA [email protected] forums focusing on television comedy at the Guardian Edinburgh NEW COMEDY SHOWCASE 2014 sees two forums focusing on television comedy at the Guardian International Television Festival in August, as well as for a fourth Event Producer KAM KANDOLA FLYNN Edinburgh International Television Festival in August, as well as for a fourth consecutive year at the New York Television Festival in October. [email protected] with special guests SHARON HORGAN, ROB DELANEY, consecutive year at the New York Television Festival in October. Our Our next London event in September will focus on writing for Event Producer next London event in September will focus on writing for children and in children and in December we hold our annual film forum. JULIA CARRUTHERS MYFANWY MOORE and AMY HARTWICK December we hold our annual film forum. [email protected] A huge thank you to our script selection panel and jurors for their Event Producer THURSDAY 21 AUGUST 2014 role in selecting the featured extracts. They included Alex Moody, BRADLEY DOWN GUARDIAN EDINBURGH INTERNATIONAL TELEVISION FESTIVAL Anil Gupta, Arabella McGuigan, Ben Boyer, Ben Caudell, Ben [email protected] Farrell, Caroline Norris, Chantelle Woodnutt, Chris Sussman, Director Dan Hine, Dan March, David Freedman, David Quantick, SUSAN JACOBSON [email protected] Dawson Brothers, Elaine Gracie, Fiona McDermott, Jack Bayles, The BAFTA Rocliffe New Comedy Showcase, now in its Jamie Jay Johnson, Jon Wakeham, Kate Leys, Katie Boyles, Kevin Casting CATHERINE WILLIS fifteenth year, is a platform for new writing and networking. -

CID Public Safety Task Force Report (2016)
CHINATOWN-INTERNATIONAL DISTRICT PUBLIC SAFETY TASK FORCE REPORT Seattle OfficeCITY of OFPlanning SEATTLE & June 2016 Community Development Chinatown International District Public Safety Task Force Hyeok Kim (Co-Chair) I-Miun Liu Deputy Mayor, Mayor's Office Business Owner, Oasis Tea Zone, Eastern Café Carmen Best (Co-Chair) Sokha Danh Deputy Chief of Police, Seattle Police Department Economic Development Specialist, SCIDpda Maiko Winkler-Chin (Co-Chair) Abdi Mohamed Executive Director, Seattle Chinatown-ID Preservation Organizer, Working Washington & Development Authority Larry Larson Tam Nguyen (Co-Chair) Manager, American Hotel Business owner, Tamarind Tree, Greg Garcia President, Friends of Little Saigon Community Impact Manager, United Way Sharyne Shiu-Thornton Tom Im Board Member, Seattle Indian Health Board Community Planning & Development Manager, InterIm Ali Lee CDA Member Liaison, Greater Seattle Chinese Chamber of Ron Chew Commerce Executive Director, ICHS Foundation Richard Mar Sonny Nguyen President, International District Emergency Center Engagement Coordinator, Washington Bus Minh-Duc Nguyen Karen Yoshitomi Executive Director, Helping Link Executive Director, Japanese Cultural & Community Sue May Eng Center President, Chong Wa Benevolent Association Alan Lai Sheila Burrus Crime Victim Service Director, Chinese Information & Community member, Filipino American community Service Center City of Seattle Chinatown-International District Public Safety Task Force Report 2 Support Staff Support Gary Johnson Yun Pitre Center City Coordinator, Office of Planning & District Coordinator, Department of Neighborhoods Community Development Rebecca Frestedt Scott Lindsay ISRD Coordinator, Department of Neighborhoods Mayor’s Special Assistant on Police Reform and Public David Lavelle Safety West Precinct Liaison Attorney, Seattle City Attorney’s David Mendoza Office Policy Advisor, Mayor’s Office of Policy and Innovation Capt. -

SPRING 2013 the Frostburg State University Magazineprofile
VOL 25 NO 2 SPRING 2013 The Frostburg State University Magazineprofile Distinctly Frostburg FSU Recognized for Its Exceptional Educational Experience ENGAGED STUDENTS SUCCESSFUL OUTCOMES GREAT TEACHING VIBRANT COMMUNITY Honoring a Fallen Hero 11 | Title IX Broadens Horizons 20 | Leadership & Homecoming Weekend 24 ENGAGED STUDENTS SUCCESSFUL OUTCOMES GREAT TEACHING VIBRANT COMMUNITY From the President n fall 2012, FSU was named a College of FSU’s vibrant community, something profile Distinction because of how we stand out in we support through lectures, performances, Vol. 25 No. 2 Spring 2013 four key areas: student engagement, the exhibitions and speakers, is also growing in Prole is published for alumni, parents, friends, quality of our teaching, the vibrancy of new directions. We are pleased to welcome faculty and sta of Frostburg State University. our college community and the success of Dr. Rosemary M. omas, our vice president our graduates. It is an honor that in many for University Advancement and executive President Iways arms the quality educational experience director of the FSU Foundation, whose vision will Dr. Jonathan C. Gibralter we have provided for years. But it is also an honor strengthen our marketing and branding initiatives Vice President for that inspires us as we think about who we want to and philanthropy. We are also pleased to have a University Advancement become in the years ahead. new director of Alumni Programs and Special Dr. Rosemary M. Thomas In this issue, we take a closer look at how we Events, Laura McCullough, whose role will be to Editor excel as a College of Distinction. When it comes ensure our alumni feel connected to the vibrant Liz Douglas Medcalf to student engagement, as you read through this community Frostburg provides and connected to issue, you’ll discover that our students are proud each other through new anity groups. -

This Is a Test
‘THE SEVEN YEAR HITCH’ CAST BIOS NATALIE HALL (Jennifer) – Natalie Hall hails from Vancouver, Canada and is best known for playing Colby Chandler on the ABC daytime drama, “All My Children.” She is currently shooting a lead role in the feature film, “Plus One” for director, Dennis Iliadis. Hall has also starred on the hit ABC Family Series, “Pretty Little Liars” and most recently starred in the Hallmark Channel Original Movie Event “Love’s Christmas Journey” alongside Sean Astin, JoBeth Williams and Ernest Borgnine. Natalie's theatre credits include the National Tour of Broadway's, A Chorus Line, in which she was nominated for an Ovation Award along with the Broadway tour of Wicked and Broadway’s Rising Stars at New York Town Hall. Television appearances include the CBS dramatic series, “The Good Wife” and NBC’s “Law & Order: SUV.” ### DARIN BROOKS (Kevin) – Born in Honolulu, Hawaii Darin Brooks began his career on-stage starring as Rapunzel's Prince in his high school’s production of Into the Woods. Not soon after he found himself on television portraying Max Brady in the Emmy® Award-winning daytime soap opera “Days Of Our Lives,” from 2005-2010. Brooks continued his roles on television series including “Miss Behave,” Spike’s “Blue Mountain State” and “My Wife And Kids.” Brooks has also appeared as a host for “Two Scoop” and “America Goes Bollywood.” On the big screen, Brooks’ credits include, “Blue Crush,” “Truth Or Dare,” “Staring At The Sun” and “Big Bounce.” An avid sportsman, Brooks’ hobbies include surfing, snowboarding, skiing and cycling. ### RYAN DOOM (Bryce) – Born in Phoenix, Arizona, Ryan Doom’s family moved East, settling in Spring, Texas when he was only eight years-old. -

Downloaded More Than 212,000 Times Since the Ipad's April 3Rd Launch,” the Futon Critic, 14 Apr
Distribution Agreement In presenting this thesis or dissertation as a partial fulfillment of the requirements for an advanced degree from Emory University, I hereby grant to Emory University and its agents the non-exclusive license to archive, make accessible, and display my thesis or dissertation in whole or in part in all forms of media, now or hereafter known, including display on the world wide web. I understand that I may select some access restrictions as part of the online submission of this thesis or dissertation. I retain all ownership rights to the copyright of the thesis or dissertation. I also retain the right to use in future works (such as articles or books) all or part of this thesis or dissertation. Signature _____________________________ ______________ Nicholas Bestor Date TV to Talk About: The CW and Post-Network Television By Nicholas Bestor Master of Arts Film Studies Michele Schreiber, Ph.D. Advisor Eddy Von Mueller, Ph.D. Committee Member Karla Oeler, Ph.D. Committee Member Accepted: Lisa A. Tedesco, Ph.D. Dean of the James T. Laney School of Graduate Studies ___________________ Date TV to Talk About: The CW and Post-Network Television By Nicholas Bestor B.A., Middlebury College, 2005 Advisor: Michele Schreiber, Ph.D. An abstract of A thesis submitted to the Faculty of the James T. Laney School of Graduate Studies of Emory University in partial fulfillment of the requirements for the degree of Master of Arts in Film Studies 2012 Abstract TV to Talk About: The CW and Post-Network Television By Nicholas Bestor The CW is the smallest of the American broadcast networks, but it has made the most of its marginal position by committing itself wholly to servicing a niche demographic. -

Broadway in Hollywood 2019-20 Season Hamilton
BROADWAY IN HOLLYWOOD 2019-20 SEASON ONE SEASON FEATURING EIGHT L.A. PREMIERES ALL DIRECT FROM BROADWAY PLAYING BOTH THE PANTAGES & DOLBY THEATRES PANTAGES THEATRE Disney’s FROZEN SUMMER: The Donna Summer Musical ANASTASIA DOLBY THEATRE MEAN GIRLS Jimmy Buffett’s ESCAPE TO MARGARITAVILLE Lerner & Loewe’s MY FAIR LADY Nickelodeon’s THE SPONGEBOB MUSICAL …and the winner of Ten 2018 Tony Awards including Best Musical THE BAND’S VISIT NEW 2019-20 SEASON TICKETS NOW ON SALE CURRENT SEASON TICKET HOLDERS CAN RENEW SEATS BEGINNING TODAY SPECIAL ANNOUNCEMENT HAMILTON WILL RETURN TO THE PANTAGES THEATRE PERFORMANCES BEGIN MARCH 2020 NEW & RENEWING SEASON TICKET HOLDERS WILL HAVE PRIORITY ACCESS TO THIS ADDITIONAL EVENT Broadway in Hollywood 2019-20 Season Announcement Page 1 of 8 Tuesday, February 5, 2019 – The Hollywood Pantages, a Nederlander Theatre, is proud to announce the BROADWAY IN HOLLYWOOD 2019-20 Season , consisting of eight Los Angeles premieres, all direct from Broadway. This season will mark the first time Los Angeles Theatre audiences will have regular access to Broadway National Tours at both the Pantages and Dolby Theatres in Hollywood. 8 great shows, 2 iconic theatres, one blockbuster season. Pantages Theatre General Manager Jeff Loeb states, “There are so many new and amazing experiences in store for our audiences this season – it’s almost impossible to pinpoint what to celebrate first! By working with our neighbors at the Dolby Theatre to add this gorgeous venue to our family of presenting theatres, we have entered a world of endless theatrical possibilities. More shows. Longer runs. Endless memories – all while staying rooted in the neighborhood we love.