Lifesize UVC Platform™ Third Party Licenses
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Administrator's Guide
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release notes, and/or the latest version of the applicable documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/scanmail-for-microsoft- exchange.aspx Trend Micro, the Trend Micro t-ball logo, Apex Central, eManager, and ScanMail are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2020. Trend Micro Incorporated. All rights reserved. Document Part No.: SMEM149028/200709 Release Date: November 2020 Protected by U.S. Patent No.: 5,951,698 This documentation introduces the main features of the product and/or provides installation instructions for a production environment. Read through the documentation before installing or using the product. Detailed information about how to use specific features within the product may be available at the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Evaluate this documentation on the following site: https://www.trendmicro.com/download/documentation/rating.asp Privacy and Personal Data Collection Disclosure Certain features available in Trend Micro products collect and send feedback regarding product usage and detection information to Trend Micro. Some of this data is considered personal in certain jurisdictions and under certain regulations. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Windows X32 Cross Compile Guide
Guide for cross compiling Trezarcoin for windows. By Iwens Fortis Tested on Ubuntu 16.04.2 LTS. • Start on ubuntu your terminal (search for terminal with ubuntu dash top icon left, or press windows key to open dash). • First we need to install the dependencies, for this execute the following cmd’s stated below in the terminal window. The commands to execute are in the grey textboxes. The commands will ask for a password which and u have to confirm some commands with y from yes. Tip transfer the pdf to ubuntu for easy copy and paste. • First update the apt library. sudo apt-get update • Install needed dependencies to install mxe to cross compile Trezarcoin. sudo apt-get install p7zip-full autoconf automake autopoint bash bison bzip2 cmake flex gettext git g++ gperf intltool \ libffi-dev libtool libltdl-dev libssl-dev libxml-parser-perl make openssl patch perl pkg-config python ruby scons sed unzip \ wget xz-utils libtool-bin libgdk-pixbuf2.0-dev g++-multilib libc6-dev-i386 upx -y • We need to get latest mxe from github and compile libraries needed. git clone https://github.com/mxe/mxe.git cd mxe make MXE_TARGETS="i686-w64-mingw32.static" boost make MXE_TARGETS="i686-w64-mingw32.static" qttools make MXE_TARGETS="i686-w64-mingw32.static" miniupnpc • Next we need to compile the recommended Berkeley DB our self cd ~ wget 'http://download.oracle.com/berkeley-db/db-4.8.30.NC.tar.gz' tar zxvf db-4.8.30.NC.tar.gz cd db-4.8.30.NC • Now we will create a bash script for this execute the following commands to create the bash script. -

Open Source Software Attributions for ASCET-DEVELOPER 7.3.0
ASCET-DEVELOPER 7.3.0 OSS Attributions Open Source Software Attributions for ASCET-DEVELOPER 7.3.0 This document is provided as part of the fulfillment of OSS license conditions and does not require users to take any action before or while using the product. Page 1 of 102 ASCET-DEVELOPER 7.3.0 OSS Attributions Table of Contents Contents 1 List of used Open Source Components. ................................................................................................ 3 2 Appendix - License Text ................................................................................................................. 15 2.1 ANTLR Software Rights Notice .................................................................................................. 15 2.2 ASM License ......................................................................................................................... 16 2.3 Apache License 1.1 ................................................................................................................. 17 2.4 Apache License 2.0 ................................................................................................................. 18 2.5 BSD (Three Clause License) ...................................................................................................... 21 2.6 BSD 4-clause "Original" or "Old" License ..................................................................................... 22 2.7 Common Development and Distribution License 1.0..................................................................... -

Command-Line Guide for Linux, Mac & Windows
Command-line Guide for Linux, Mac & Windows info.nrao.edu /computing/guide/file-access-and-archiving/7zip/7z-7za-command-line-guide See also: File Archiving and Compression, Accessing and Sharing Files, Network Access, Windows Terminal Servers 7-Zip Versions 7-Zip is an Archive and File Management utility available in command-line versions for Linux/Mac, "P7Zip" (7z.exe), as well as for Windows, "7za" (7za.exe). Although its interface is deceptively simple, the command-line versions of 7ZIP are highly customizable archiving programs when used with the command parameters and switchesdescribed below. Windows users who want to use the command-line version should generate a Help Desk ticket to install the standalone 7za.exe version. To begin a session, open a terminal window. Invoke the version of 7Zip you are using by entering " 7z" for P7Zip (7z.exe), or "7za" for 7Zip for Windows (7za.exe) to start either the P7-Zip or 7za application prior to entering commands. Other than this program invocation command, all commands, parameters and switches are identical for all command-line versions. NOTE TO WINDOWS USERS: the following syntax examples begin by invoking the Linux command-line version, "7z". Please change the invocation to "7za" when applying these examples for use in 7-Zip for Windows. Command Line Syntax The general command line syntax begins by invoking the version of 7Zip you are using: "7z" for P7Zip (7z.exe) users or "7za" for 7Zip for Windows (7za.exe) users followed by the command and parameters: "command" "switches" "full_path_archive_name" "full_path_file_name" Eg; 7z a -p 7Zip_Archive Test_file.txt creates a 7z formatted archive named 7Zip_Archive that is protected with a password , then adds a file named test_file.txt to the archive. -
3. PE Portable Executable: a Look
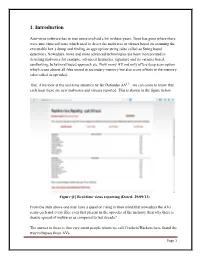
1. Introduction Anti-virus software has in true sense evolved a lot in these years. Time has gone where there were anti-virus software which used to detect the malwares or viruses based on scanning the executable hex`s dump and finding an appropriate string (also called as String based detection). Nowadays, more and more advanced technologies are been incorporated in detecting malwares for example, advanced heuristics, signature and its variants based, sandboxing, behavioral based approach etc. Now many AV not only offers deep scan option which scans almost all files stored in secondary memory but also scans offsets in the memory (also called as opcodes). But, if we look at the real-time statistics by Bit Defender AV[1] , we can come to know that each hour there are new malwares and viruses reported. This is shown in the figure below. Figure [1] Real-time virus reporting (Dated: 29/09/13) From the stats above one may have a question rising in their mind that nowadays the AVs scans each and every files even that present in the opcodes of the memory then why there is drastic spread of malwares as compared to last decade? The answer to these is that very smart people whom we call Crackers/Hackers have found the way to bypass these AVs. Page 1 They know the very detail about how the AV works and which AV have which type of detection capabilities for example if it scans based on string detection or if it scans based on sandboxing approach. We sometimes fail to remember that they (Crackers and Hackers) too have AV scanners from which they may scan their newly developed malware and viruses and can easily spread via plethora of medium, mostly the Internet. -

Thread Scheduling in Multi-Core Operating Systems Redha Gouicem
Thread Scheduling in Multi-core Operating Systems Redha Gouicem To cite this version: Redha Gouicem. Thread Scheduling in Multi-core Operating Systems. Computer Science [cs]. Sor- bonne Université, 2020. English. tel-02977242 HAL Id: tel-02977242 https://hal.archives-ouvertes.fr/tel-02977242 Submitted on 24 Oct 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Ph.D thesis in Computer Science Thread Scheduling in Multi-core Operating Systems How to Understand, Improve and Fix your Scheduler Redha GOUICEM Sorbonne Université Laboratoire d’Informatique de Paris 6 Inria Whisper Team PH.D.DEFENSE: 23 October 2020, Paris, France JURYMEMBERS: Mr. Pascal Felber, Full Professor, Université de Neuchâtel Reviewer Mr. Vivien Quéma, Full Professor, Grenoble INP (ENSIMAG) Reviewer Mr. Rachid Guerraoui, Full Professor, École Polytechnique Fédérale de Lausanne Examiner Ms. Karine Heydemann, Associate Professor, Sorbonne Université Examiner Mr. Etienne Rivière, Full Professor, University of Louvain Examiner Mr. Gilles Muller, Senior Research Scientist, Inria Advisor Mr. Julien Sopena, Associate Professor, Sorbonne Université Advisor ABSTRACT In this thesis, we address the problem of schedulers for multi-core architectures from several perspectives: design (simplicity and correct- ness), performance improvement and the development of application- specific schedulers. -

Table of Contents
Parallel Programming Models Lawrence Rauchwerger http://parasol.tamu.edu Table of Contents Introduction to Parallelism Introduction to Programming Models Shared Memory Programming Message Passing Programming Shared Memory Models PGAS Languages Other Programming Models 1 Acknowledgement Material in this course has been adapted from various (cited) authoritative sources Presentation has been put together with the help of Dr. Mauro Bianco, Antoniu Pop, Tim Smith and Nathan Thomas – Parasol Lab, Department of Computer Science, Texas A&M University. What Will You Get from Class Ideas about parallel processing Different approaches to parallel programming Additional material in your classnotes 2 Table of Contents Introduction to Parallelism – What is Parallelism ? What is the Goal ? Introduction to Programming Models Shared Memory Programming Message Passing Programming Shared Memory Models PGAS Languages Other Programming Models Introduction to Parallelism Sequential Computing – Single CPU executes stream of instructions. Adapted from: http://www.llnl.gov/computing/tutorials/parallel_comp 3 Introduction to Parallelism Parallel computing – Partition problem into multiple, concurrent streams of instructions. Classification Flynn’s Taxonomy (1966-now) Nowadays SISD SIMD SPMD Single Instruction Single Instruction Single Program Single Data Multiple Data Multiple Data MISD MIMD MPMD Multiple Instructions Multiple Instructions Multiple Program Single Data Multiple Data Multiple Data • Execution models impact the above programming model • Traditional computer is SISD • SIMD is data parallelism while MISD is pure task parallelism • MIMD is a mixed model (harder to program) • SPMD and MPMD are less synchronized than SIMD and MIMD • SPMD is most used model, but MPMD is becoming popular 4 Introduction to Parallelism Goal of parallel computing – Save time - reduce wall clock time. -

Qualitative and Quantitative Evaluation of Software Packers
Qualitative and Quantitative Evaluation of Software Packers Mar´ıa Bazus,´ Ricardo J. Rodr´ıguez, Jose´ Merseguer « All wrongs reversed [email protected] ¸ @RicardoJRdez ¸ www.ricardojrodriguez.es Department of Computer Science and Systems Engineering University of Zaragoza, Spain December 12, 2015 NoConName 2015 Barcelona (Spain) $whoami Ph.D. on Comp. Sci. (Univ. of Zaragoza, Spain) (2013) Assistant Professor at University of Zaragoza Performance analysis on critical, complex systems Secure Software Engineering Advance malware analysis RFID/NFC Security Not prosecuted ^¨ Speaker at NcN, HackLU, RootedCON, STIC CCN-CERT, HIP, MalCON, HITB. M. Bazus,´ R.J. Rodr´ıguez, J. Merseguer Qualitative and Quantitative Evaluation of Software Packers NcN 2015 2 / 39 Agenda 1 Introduction 2 Contributions and Related Work 3 Previous Concepts 4 Software Protection Taxonomy 5 Software Packers Under Study 6 Qualitative and Quantitative Evaluation Qualitative Evaluation Quantitative Evaluation 7 Conclusions and Future Work M. Bazus,´ R.J. Rodr´ıguez, J. Merseguer Qualitative and Quantitative Evaluation of Software Packers NcN 2015 3 / 39 Agenda 1 Introduction 2 Contributions and Related Work 3 Previous Concepts 4 Software Protection Taxonomy 5 Software Packers Under Study 6 Qualitative and Quantitative Evaluation Qualitative Evaluation Quantitative Evaluation 7 Conclusions and Future Work M. Bazus,´ R.J. Rodr´ıguez, J. Merseguer Qualitative and Quantitative Evaluation of Software Packers NcN 2015 4 / 39 RE uses: legitimate and illegitimate X Find software bugs X Get interoperability with legacy systems X Detect malicious software X Detect vulnerabilities to create/spread malware X Obtain (or avoid) software license duplication Introduction (I): Reverse Engineering WTF? To analyse a binary program with machine-code vision Types of analysis: Static analysis( + not executed, * all paths explored) Dynamic analysis( * truly executed, + but just one path explored!) M. -

Kernel Threads
CSMC 412 Operating Systems Prof. Ashok K Agrawala © 2019 Ashok Agrawala February 20 1 Threads & Concurrency Operating System Concepts – 10th Edition Silberschatz, Galvin and Gagne ©2018 Threads • Overview • Multicore Programming • Multithreading Models • Thread Libraries • Implicit Threading • Threading Issues • Operating System Examples February 20 Copyright 2018 Silberschatz, Gavin & Gagne 3 Objectives • To introduce the notion of a thread—a fundamental unit of CPU utilization that forms the basis of multithreaded computer systems • To discuss the APIs for the Pthreads, Windows, and Java thread libraries • To explore several strategies that provide implicit threading • To examine issues related to multithreaded programming • To cover operating system support for threads in Windows and Linux February 20 Copyright 2018 Silberschatz, Gavin & Gagne 4 Process PC … Address Space February 20 Copyright 2018 Silberschatz, Gavin & Gagne 5 Process Control Block (PCB) Information associated with each process (also called task control block) • Process state – running, waiting, etc • Program counter – location of instruction to next execute • CPU registers – contents of all process- centric registers • CPU scheduling information- priorities, scheduling queue pointers • Memory-management information – memory allocated to the process • Accounting information – CPU used, clock time elapsed since start, time limits • I/O status information – I/O devices allocated to process, list of open files February 20 Copyright 2018 Silberschatz, Gavin & Gagne 6 -

NSWI 0138: Advanced Unix Programming
NSWI 0138: Advanced Unix programming (c) 2011-2016 Vladim´ırKotal (c) 2009-2010 Jan Pechanec, Vladim´ırKotal SISAL MFF UK, Malostransk´en´am.25, 118 00 Praha 1 Charles University Czech Republic Vladim´ırKotal [email protected] March 10, 2016 1 Vladim´ırKotal NSWI 0138 (Advanced Unix programming) Contents 1 Overview 5 1.1 What is this lecture about? . .5 1.2 The lecture will cover... .5 1.3 A few notes on source code files . .6 2 Testing 6 2.1 Why?...........................................6 2.2 When ? . .6 2.3 Types of testing . .7 3 Debugging 8 3.1 Debuging in general . .8 3.2 Observing . .9 3.3 Helper tools . .9 3.3.1 ctags . .9 3.3.2 cscope . 10 3.3.3 OpenGrok . 11 3.3.4 Other tools . 11 3.4 Debugging data . 11 3.4.1 stabs . 11 3.4.2 DWARF . 12 3.4.3 CTF (Compact C Type Format) . 12 3.5 Resource leaks . 13 3.6 libumem . 13 3.6.1 How does libumem work . 14 3.6.2 Using libumem+mdb to find memory leaks . 14 3.6.3 How does ::findleaks work . 16 3.7 watchmalloc . 17 3.8 Call tracing . 18 3.9 Using /proc . 19 3.10 Debugging dynamic libraries . 20 3.11 Debuggers . 20 3.12 Symbol search and interposition . 20 3.13 dtrace . 21 4 Terminals 21 4.1 Terminal I/O Overview . 21 4.2 Terminal I/O Overview (cont.) . 22 4.3 Physical (Hardware) Terminal . 24 4.4 stty(1) command . 24 4.5 TTY Driver Connected To a Phy Terminal . -

Oracle Database Licensing Information for Additional Information
Oracle® Exadata Database Machine Licensing Information 11g Release 2 (11.2) E25431-04 November 2013 Oracle Exadata Database Machine Licensing Information, 11g Release 2 (11.2) E25431-04 Copyright © 2012, 2013, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs.