Cascading Failures in Power Grids – Analysis and Algorithms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Prevention of Cascading Outages Using Sparse Wide Area Synchrophasor Measurements
Prevention of Cascading Outages Using Sparse Wide Area Synchrophasor Measurements Ahad Esmaeilian, Student Member and Mladen Kezunovic, Fellow, IEEE Abstract—Early prediction of cascade events outages followed analysis. In [9], a Performance Index (PI) is introduced based by immediate and proper control actions can prevent major on line voltage and loading condition to select reasonable blackouts. This paper introduces a novel method to predict contingency scenarios. A fast network screening contingency cascade event outage at early stage and mitigate it with proper control strategy. In the first step, methodology employs sparsely selection method is discussed in [10] which determines the located phasor measurement units to detect disturbances using location of buses with potential voltage problems, and defines electromechanical oscillation propagation phenomena. The a voltage-sensitive subsystem for contingency selection. A obtained information is used to update system topology and hybrid method is proposed in [11] which is a coordinated power flow. Next, a constrained spectral k-embedded clustering combination of PI methods, subnetwork solutions, method is defined to determine possible cascade event scenarios, compensation methods and sparse vector methods. Other and if needed proper switching action is listed to intentionally create islands to minimize load shedding and maintain voltage methods include, first-order sensitivity analysis based on profile of each island. The method was developed in MATLAB power flow results, neural network and pattern recognition and tested with IEEE 118 bus test system. The results [12-14]. demonstrate effectiveness and robustness of the proposed method. In [15], a comprehensive Vulnerability Index (VI) based method is proposed which considers effects of voltage and Index Terms—Cascade event detection, electromechanical reactive power, overload, distance relay performance, loss of wave propagation, intentional islanding, phasor measurement generators, loads and transmission lines. -

Controlling Cascading Failures with Cooperative Autonomous Agents
Controlling Cascading Failures with Cooperative Autonomous Agents Paul Hines1 and Sarosh Talukdar2,1 1Carnegie Mellon U., Department of Engineering and Public Policy 2Carnegie Mellon U., Department of Electrical and Computer Engineering Abstract Cascading failures in electricity networks cause blackouts and blackouts often come with severe economic and social consequences. Cascading failures are typically initiated by a set of equipment outages that cause operating constraint violations. These initiating events can be triggered by naturally occurring events, such as a wind storm, or human intervention, such as a terrorist attack. When violations persist in a network they can trigger additional outages which in turn may cause further violations. This paper proposes a method for limiting the social costs of cascading failures by eliminating violations before a dependent outage occurs. This global problem is solved using a new application of distributed model predictive control. Specifically, our method is to create a network of autonomous agents, one at each bus of a power network. The task assigned to each agent is to solve the global control problem with limited communication abilities. Each agent builds a simplified model of the network based on locally available data and solves its local problem using model predictive control and cooperation. Through extensive simulations with IEEE test networks, we find that the autonomous agent design meets its goals with limited communication. Experiments also demonstrate that cooperation among software agents can vastly improve system performance. Finally, we discuss the relevance of this work to some current policy issues. Keywords Cascading failures, autonomous agents, electrical power networks Biographies Paul Hines is currently a doctoral student in the Engineering and Public Policy department at Carnegie Mellon University. -
Final Blackout Report Chapters 7-10
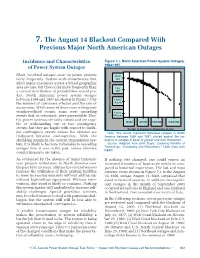
7. The August 14 Blackout Compared With Previous Major North American Outages Incidence and Characteristics Figure 7.1. North American Power System Outages, of Power System Outages 1984-1997 Short, localized outages occur on power systems fairly frequently. System-wide disturbances that affect many customers across a broad geographic area are rare, but they occur more frequently than a normal distribution of probabilities would pre- dict. North American power system outages between 1984 and 1997 are shown in Figure 7.1 by the number of customers affected and the rate of occurrence. While some of these were widespread weather-related events, some were cascading events that, in retrospect, were preventable. Elec- tric power systems are fairly robust and are capa- ble of withstanding one or two contingency events, but they are fragile with respect to multi- ple contingency events unless the systems are Note: The circles represent individual outages in North readjusted between contingencies. With the America between 1984 and 1997, plotted against the fre- shrinking margin in the current transmission sys- quency of outages of equal or greater size over that period. tem, it is likely to be more vulnerable to cascading Source: Adapted from John Doyle, California Institute of outages than it was in the past, unless effective Technology, “Complexity and Robustness,” 1999. Data from NERC. countermeasures are taken. As evidenced by the absence of major transmis- If nothing else changed, one could expect an sion projects undertaken in North America over increased frequency of large-scale events as com- the past 10 to 15 years, utilities have found ways to pared to historical experience. -

Revealing Cascading Failure Vulnerability in Power Grids Using
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI 10.1109/TPDS.2013.2295814, IEEE Transactions on Parallel and Distributed Systems 1 Revealing Cascading Failure Vulnerability in Power Grids using Risk-Graph Yihai Zhu, Student Member, IEEE, Jun Yan, Student Member, IEEE, Yan Sun, Member, IEEE, and Haibo He, Senior Member, IEEE, Abstract—Security issues related to power grid networks have damage [1]. For example, the well-known Northeast blackout attracted the attention of researchers in many fields. Recently, in 2003 affected 55 million people and caused an estimated a new network model that combines complex network theories economic loss between $7 billions and $10 billions [2]. with power flow models was proposed. This model, referred to as the extended model, is suitable for investigating vulnerabilities in Large-scale power outage is often caused by cascading power grid networks. In this paper, we study cascading failures of failure. A cascading failure refers to a sequence of dependent power grids under the extended model. Particularly, we discover events, where the initial failure of one or more components that attack strategies that select target nodes (TNs) based on (i.e. substations and transmission lines) triggers the sequential load and degree do not yield the strongest attacks. Instead, we failure of other components [3], [4]. Triggers of the initial propose a novel metric, called the risk graph, and develop novel attack strategies that are much stronger than the load-based failures can be natural damage (e.g. -

Augmented Power Dispatch for Resilient Operation Through Controllable Series Compensation and N-1-1 Contingency Assessment
energies Article Augmented Power Dispatch for Resilient Operation through Controllable Series Compensation and N-1-1 Contingency Assessment Liping Huang 1 , Zhaoxiong Huang 1, Chun Sing Lai 1,2,* , Guangya Yang 3 , Zhuoli Zhao 1,*, Ning Tong 1, Xiaomei Wu 1 and Loi Lei Lai 1,* 1 Department of Electrical Engineering, School of Automation, Guangdong University of Technology, Guangzhou 510006, China; [email protected] (L.H.); [email protected] (Z.H.); [email protected] (N.T.); [email protected] (X.W.) 2 Brunel Interdisciplinary Power Systems Research Centre, Department of Electronic and Electrical Engineering, Brunel University London, London UB8 3PH, UK 3 Center for Electric Power and Energy, Department of Electrical Engineering, Technical University of Denmark, 2800 Kongens Lyngby, Denmark; [email protected] * Correspondence: [email protected] (C.S.L.); [email protected] (Z.Z.); [email protected] (L.L.L.) Abstract: Research on enhancing power system resilience against extreme events is attracting sig- nificant attention and becoming a top global agenda. In this paper, a preventive augmented power dispatch model is proposed to provide a resilient operation. In the proposed model, a new N-1-1 security criterion is proposed to select disruptive N-1-1 contingency cases that might trigger cascad- ing blackouts, and an iterative contingency assessment process based on the line outage distribution factor is proposed to deal with security constraints. In terms of optimization objectives, two objectives Citation: Huang, L.; Huang, Z.; Lai, related to power flow on the transmission line are considered to reduce the possibility of overload C.S.; Yang, G.; Zhao, Z.; Tong, N.; Wu, outages. -

Special Issue on “Thermal Safety of Chemical Processes”
processes Editorial Special Issue on “Thermal Safety of Chemical Processes” Dimitri Lefebvre 1 and Sébastien Leveneur 2,* 1 GREAH Research Group, UNIHAVRE, Normandie University, 76600 Le Havre, France; [email protected] 2 Laboratoire de Sécurité des Procédés Chimiques LSPC, EA4704, INSA Rouen, Normandie University, UNIROUEN, 76800 Saint-Étienne-du-Rouvray, France * Correspondence: [email protected]; Tel.: +33-2329-566-54 Chemistry plays an essential role in our modern society. The shift from fossil to biomass/renewable materials continues to increase rapidly industrial chemical activities and to generate more accidents. Such accidents can create a shortage in the supply of es- sential chemicals or deteriorate the financial situation of a chemical plant until bankruptcy. Safety analysis [1] and management [2] are essential to avoid major chemical accidents. Chemical accidents can be provoked by leakage, fire, explosion, or thermal runaway [3]. Two studies have shown that approximately 25% of chemical accidents are originated from a thermal runaway [3,4]. Runaway can be defined as a rapid, uncontrolled rise in temperature during a chemical reaction and occurs in non-isothermal mode. In this Special Issue, “Thermal Safety of Chemical Processes”, we aim to present the relevance and diversity of this research area. In particular, the issue proposes some research in the field of thermal parameters measurement [5], in the prediction of lithium-ion battery thermal runaway [6], and in thermal analysis of vacuum resistance furnace [7] or dust explosion [8]. Thermal runaway is the most common failure mode of lithium-ion battery which may lead to numerous safety incidents, because lithium-ion batteries are commonly used in Citation: Lefebvre, D.; Leveneur, S. -

Comparing a Transmission Planning Study of Cascading with Historical Line Outage Data Ian Dobson Iowa State University, [email protected]
Electrical and Computer Engineering Conference Electrical and Computer Engineering Papers, Posters and Presentations 2016 Comparing a transmission planning study of cascading with historical line outage data Ian Dobson Iowa State University, [email protected] M. Papic Idaho Power Company Follow this and additional works at: http://lib.dr.iastate.edu/ece_conf Part of the Power and Energy Commons Recommended Citation Dobson, Ian and Papic, M., "Comparing a transmission planning study of cascading with historical line outage data" (2016). Electrical and Computer Engineering Conference Papers, Posters and Presentations. 48. http://lib.dr.iastate.edu/ece_conf/48 This Conference Proceeding is brought to you for free and open access by the Electrical and Computer Engineering at Iowa State University Digital Repository. It has been accepted for inclusion in Electrical and Computer Engineering Conference Papers, Posters and Presentations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Comparing a transmission planning study of cascading with historical line outage data Abstract The ap per presents an initial comparison of a transmission planning study of cascading outages with a statistical analysis of historical outages. The lp anning study identifies the most vulnerable places in the Idaho system and outages that lead to cascading and interruption of load. This analysis is based on a number of case scenarios (short-term and long-term) that cover different seasonal and operating conditions. The historical analysis processes Idaho outage data and estimates statistics, using the number of transmission line outages as a measure of the extent of cascading. An initial number of lines outaged can lead to a cascading propagation of further outages. -

DOE Technical Support Document
Department of Energy Technical Support Document Notice of Final Rulemaking National Environmental Policy Act Implementing Procedures (10 CFR Part 1021) November 2020 This Technical Support Document supplements the Department of Energy’s (DOE’s) Notice of Final Rulemaking to update its National Environmental Policy Act (NEPA) regulations (10 CFR 1021) regarding authorizations under section 3 of the Natural Gas Act (15 U.S.C. 717). See 85 FR 78197, December 4, 2020, at https://beta.regulations.gov/docket/DOE-HQ-2020-0017. Each of the documents cited below are incorporated, in their entirety, into DOE’s record for this rulemaking. Technical Studies LNG Monthly 2020 (Office of Fossil Energy, U.S. Department of Energy): https://www.energy.gov/fe/downloads/lng-monthly-2020. Among the reported data: • Calculated from the number of rows for each year (2017–2019) in the tab “LNG Exports – Repository” in LNG 2020.xlsx: LNG shipments associated with DOE export authorizations numbered 209 in 2017, 330 in 2018, and 563 in 2019. Life Cycle Greenhouse Gas Perspective on Exporting Liquefied Natural Gas from the United States: 2019 Update (U.S. Department of Energy, National Energy Technology Laboratory, September 12, 2019): https://www.energy.gov/sites/prod/files/2019/09/f66/2019%20NETL%20LCA- GHG%20Report.pdf • (Page 32) “This analysis has determined that the use of U.S. LNG exports for power production in European and Asian markets will not increase GHG emissions from a life cycle perspective, when compared to regional coal extraction and consumption for power production.” LNG Information Paper #3, LNG Ships, 2019 Update (GIIGNL - The International Group of Liquefied Natural Gas Importers): https://giignl.org/sites/default/files/PUBLIC_AREA/About_LNG/4_LNG_Basics/giignl2019_infopapers3 .pdf This paper describes the transport of liquefied natural gas (LNG) in large ships known as LNG carriers and summarizes the international security measures established by the International Maritime Organisation (IMO). -

Power Grid Cascading Failure Mitigation by Reinforcement Learning
Power Grid Cascading Failure Mitigation by Reinforcement Learning Yongli Zhu * 1 Abstract climate change, having a stable power grid is critical for renewable resources integration; This paper proposes a cascading failure mitigation strategy based on Reinforcement Learning (RL). 2) The backup generators are typically fossil-fuel (e.g., coal, The motivation of the Multi-Stage Cascading Fail- diesel) based units that emit greenhouse gases. ure (MSCF) problem and its connection with the Therefore, it is meaningful to develop nuanced strategies to challenge of climate change are introduced. The mitigate a cascading failure at its early stage with as little bottom-level corrective control of the MCSF prob- generation cost as possible. lem is formulated based on DCOPF (Direct Cur- rent Optimal Power Flow). Then, to mitigate the The cascading failure mitigation can be regarded as a MSCF issue by a high-level RL-based strategy, stochastic dynamic programming problem with unknown physics-informed reward, action, and state are de- information about the risk of failures. Previous researches vised. Besides, both shallow and deep neural net- try to tackle this problem based on either mathematical work architectures are tested. Experiments on the programming methods or heuristic methods. For example, IEEE 118-bus system by the proposed mitigation bi-level programming is used to mitigate cascading fail- strategy demonstrate a promising performance in ures when energy storages exist (Du & Lu, 2014). In (Han reducing system collapses. et al., 2018), an algorithm based on percolation theory is employed for mitigating cascading failures by using UPFC (Unified Power Flow Controller) to redistribute the system 1. -

Cascading Power Outages Propagate Locally in an Influence Graph That Is
1 Cascading Power Outages Propagate Locally in an Influence Graph that is not the Actual Grid Topology Paul D. H. Hines, Senior Member, IEEE, Ian Dobson, Fellow, IEEE, Pooya Rezaei, Student Member, IEEE Abstract—In a cascading power transmission outage, com- as disease propagation [4], [5]. Similar topological contagion ponent outages propagate non-locally; after one component models have been suggested as a tool for power systems outages, the next failure may be very distant, both topologically analysis (e.g., [6], [7]). and geographically. As a result, simple models of topological contagion do not accurately represent the propagation of cascades This approach has two problems. First, in power grids it is in power systems. However, cascading power outages do follow more appropriate to focus first on line (edge) outages, since patterns, some of which are useful in understanding and reducing line outages are an order of magnitude more likely than node blackout risk. This paper describes a method by which the data (substation) outages. More importantly, as is well known to from many cascading failure simulations can be transformed power systems engineers, cascading outages in power systems into a graph-based model of influences that provides actionable information about the many ways that cascades propagate in propagate non-locally as well as locally. In a power grid, the a particular system. The resulting “influence graph” model is next component to fail after a particular line outages may be Markovian, in that component outage probabilities depend only very distant, both geographically and topologically [8]. This on the outages that occurred in the prior generation. -

A Modeling and Simulation Framework for the Reliability/Availability
A modeling and simulation framework for the reliability/availability assessment of a power transmission grid subject to cascading failures under extreme weather conditions Francesco Cadini, Gian Agliardi, Enrico Zio To cite this version: Francesco Cadini, Gian Agliardi, Enrico Zio. A modeling and simulation framework for the reliability/availability assessment of a power transmission grid subject to cascading failures un- der extreme weather conditions. Applied Energy, Elsevier, 2017, 185, Part 1, pp.267-279. 10.1016/j.apenergy.2016.10.086. hal-01652288 HAL Id: hal-01652288 https://hal.archives-ouvertes.fr/hal-01652288 Submitted on 30 Nov 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Applied Energy 185 (2017) 267–279 Contents lists available at ScienceDirect Applied Energy journal homepage: www.elsevier.com/locate/apenergy A modeling and simulation framework for the reliability/availability assessment of a power transmission grid subject to cascading failures under extreme weather conditions ⇑ Francesco Cadini a, , Gian Luca Agliardi a, Enrico Zio a,b a Dipartimento di Energia, Politecnico di Milano, Via La Masa 34, 20156, Italy b Chair System Science and the Energy Challenge, Fondation Electricite’ de France (EDF), CentraleSupélec, Université Paris-Saclay, Grande Voie des Vignes, 92290 Chatenay-Malabry, France highlights We combine stochastic extreme weather model and realistic power grid fault dynamics. -

The Cost of Cascading Failure Risk and Resilience Within UK Infrastructure Networks
The cost of cascading failure risk and resilience within UK infrastructure networks 4CMR | Department of Land Economy Dr Scott Kelly [email protected] www.scottjkelly.com 28 th March 2014 1 Agenda 1. Infrastructure and the UK economy 2. Input-Output analysis of UK infrastructure 3. Results from ITRC hotspot analysis 4. MonteCarlo simulations of cascading infrastructure failure 2 Research Objectives ITRC WS2 Objective: “Develop network models to analyse the vulnerability of interdependent infrastructure systems and the risks of infrastructure to people and the economy, in present and future climate and socio-economic scenarios” ITRC Deliverable 2.6: “An input-output analysis of the consequences of infrastructure failure for present and future economic scenarios ” 3 Research questions What is the contribution of infrastructure to the UK economy? What are the interdependencies between infrastructure service sectors and other economic sectors? What are the economic losses (indirect + direct) resulting from infrastructure failure? What is the best way to estimate variability and uncertainty in the underlying impact distributions? 4 PART 1 Infrastructure and the economy 5 Eight defining characteristics of infrastructure systems Provides a service Lumpy Long lasting Immobile Natural monopoly Used by end consumers Part of a network Interdependent and by industry 6 Economics of UK Infrastructure Infrastructure services contribute to 9.2% of UK GDP Change in GVA GVA(1992) GVA(2004) GVA(2008) % Growth SIC(2003) Sector (£2008) (1992 - 2008) (£million)