Canonical Completeness in Lattice-Based Languages For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Physical and Mathematical Sciences 2014, № 1, P. 3–6 Mathematics ON
PROCEEDINGS OF THE YEREVAN STATE UNIVERSITY Physical and Mathematical Sciences 2014, № 1, p. 3–6 Mathematics ON ZIGZAG DE MORGAN FUNCTIONS V. A. ASLANYAN ∗ Oxford University UK, Chair of Algebra and Geometry YSU, Armenia There are five precomplete classes of De Morgan functions, four of them are defined as sets of functions preserving some finitary relations. However, the fifth class – the class of zigzag De Morgan functions, is not defined by relations. In this paper we announce the following result: zigzag De Morgan functions can be defined as functions preserving some finitary relation. MSC2010: 06D30; 06E30. Keywords: disjunctive (conjunctive) normal form of De Morgan function; closed and complete classes; quasimonotone and zigzag De Morgan functions. 1. Introduction. It is well known that the free Boolean algebra on n free generators is isomorphic to the Boolean algebra of Boolean functions of n variables. The free bounded distributive lattice on n free generators is isomorphic to the lattice of monotone Boolean functions of n variables. Analogous to these facts we have introduced the concept of De Morgan functions and proved that the free De Morgan algebra on n free generators is isomorphic to the De Morgan algebra of De Morgan functions of n variables [1]. The Post’s functional completeness theorem for Boolean functions plays an important role in discrete mathematics [2]. In the paper [3] we have established a functional completeness criterion for De Morgan functions. In this paper we show that zigzag De Morgan functions, which are used in the formulation of the functional completeness theorem, can be defined by a finitary relation. -
Expressive Completeness
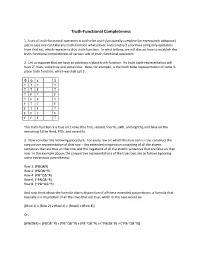
Truth-Functional Completeness 1. A set of truth-functional operators is said to be truth-functionally complete (or expressively adequate) just in case one can take any truth-function whatsoever, and construct a formula using only operators from that set, which represents that truth-function. In what follows, we will discuss how to establish the truth-functional completeness of various sets of truth-functional operators. 2. Let us suppose that we have an arbitrary n-place truth-function. Its truth table representation will have 2n rows, some true and some false. Here, for example, is the truth table representation of some 3- place truth function, which we shall call $: Φ ψ χ $ T T T T T T F T T F T F T F F T F T T F F T F T F F T F F F F T This truth-function $ is true on 5 rows (the first, second, fourth, sixth, and eighth), and false on the remaining 3 (the third, fifth, and seventh). 3. Now consider the following procedure: For every row on which this function is true, construct the conjunctive representation of that row – the extended conjunction consisting of all the atomic sentences that are true on that row and the negations of all the atomic sentences that are false on that row. In the example above, the conjunctive representations of the true rows are as follows (ignoring some extraneous parentheses): Row 1: (P&Q&R) Row 2: (P&Q&~R) Row 4: (P&~Q&~R) Row 6: (~P&Q&~R) Row 8: (~P&~Q&~R) And now think about the formula that is disjunction of all these extended conjunctions, a formula that basically is a disjunction of all the rows that are true, which in this case would be [(Row 1) v (Row 2) v (Row 4) v (Row6) v (Row 8)] Or, [(P&Q&R) v (P&Q&~R) v (P&~Q&~R) v (P&~Q&~R) v (~P&Q&~R) v (~P&~Q&~R)] 4. -

Completeness
Completeness The strange case of Dr. Skolem and Mr. G¨odel∗ Gabriele Lolli The completeness theorem has a history; such is the destiny of the impor- tant theorems, those for which for a long time one does not know (whether there is anything to prove and) what to prove. In its history, one can di- stinguish at least two main paths; the first one covers the slow and difficult comprehension of the problem in (what historians consider) the traditional development of mathematical logic canon, up to G¨odel'sproof in 1930; the second path follows the L¨owenheim-Skolem theorem. Although at certain points the two paths crossed each other, they started and continued with their own aims and problems. A classical topos of the history of mathema- tical logic concerns the how and the why L¨owenheim, Skolem and Herbrand did not discover the completeness theorem, though they proved it, or whe- ther they really proved, or perhaps they actually discovered, completeness. In following these two paths, we will not always respect strict chronology, keeping the two stories quite separate, until the crossing becomes decisive. In modern pre-mathematical logic, the notion of completeness does not appear. There are some interesting speculations in Kant which, by some stretching, could be realized as bearing some relation with the problem; Kant's remarks, however, are probably more related with incompleteness, in connection with his thoughts on the derivability of transcendental ideas (or concepts of reason) from categories (the intellect's concepts) through a pas- sage to the limit; thus, for instance, the causa prima, or the idea of causality, is the limit of implication, or God is the limit of disjunction, viz., the catego- ry of \comunance". -

Some Analogues of the Sheffer Stroke Function in N-Valued Logic
MA THEMA TICS SOME ANALOGUES OF THE SHEFFER STROKE FUNCTION IN n-VALUED LOGIe BY NORMAN M. MARTIN (Communicated by Prof. A. HEYTING at the meeting of June 24, 1950) The interpretation of the ordinary (two-valued) propositional logic in terms of a truth-table system with values "true" and "false" or, more abstractly, the numbers "I" and "2" has become customary. This has been useful in giving an algorithm for the concept "analytic" , in giving an adequacy criterion for the definability of one function by another and it has made possible the proof of adequacy of a list of primitive terms for the definition of all truth-functions (functional completeness). If we generalize the concept of truth-function so as to allow for systems of functions of 3, 4, etc. values (preserving the "extensionality" requirement on functions examined) we obtain systems of functions of more than 2 values analogous to the truth-table interpretation of the usual pro positional calculus. The problem of functional completeness (the term is due to TURQUETTE) arises in each ofthe resulting systems. Strictly speaking, this problem is notclosely connected with problems of deducibility but is rather a combinatorial question. It will be the purpose of this paper to examine the problem of functional completeness of functions in n-valued logic where by n-valued logic we mean that system of functions such that each function of the system determines, by substitution of an arbitrary numeral a for the symbol n in the definition of the n-valued function, a function in the truth table system of a values. -

Boolean Logic
Boolean logic Lecture 12 Contents . Propositions . Logical connectives and truth tables . Compound propositions . Disjunctive normal form (DNF) . Logical equivalence . Laws of logic . Predicate logic . Post's Functional Completeness Theorem Propositions . A proposition is a statement that is either true or false. Whichever of these (true or false) is the case is called the truth value of the proposition. ‘Canberra is the capital of Australia’ ‘There are 8 day in a week.’ . The first and third of these propositions are true, and the second and fourth are false. The following sentences are not propositions: ‘Where are you going?’ ‘Come here.’ ‘This sentence is false.’ Propositions . Propositions are conventionally symbolized using the letters Any of these may be used to symbolize specific propositions, e.g. :, Manchester, , … . is in Scotland, : Mammoths are extinct. The previous propositions are simple propositions since they make only a single statement. Logical connectives and truth tables . Simple propositions can be combined to form more complicated propositions called compound propositions. .The devices which are used to link pairs of propositions are called logical connectives and the truth value of any compound proposition is completely determined by the truth values of its component simple propositions, and the particular connective, or connectives, used to link them. ‘If Brian and Angela are not both happy, then either Brian is not happy or Angela is not happy.’ .The sentence about Brian and Angela is an example of a compound proposition. It is built up from the atomic propositions ‘Brian is happy’ and ‘Angela is happy’ using the words and, or, not and if-then. -

The Logic of Internal Rational Agent 1 Introduction
Australasian Journal of Logic Yaroslav Petrukhin The Logic of Internal Rational Agent Abstract: In this paper, we introduce a new four-valued logic which may be viewed as a variation on the theme of Kubyshkina and Zaitsev’s Logic of Rational Agent LRA [16]. We call our logic LIRA (Logic of Internal Rational Agency). In contrast to LRA, it has three designated values instead of one and a different interpretation of truth values, the same as in Zaitsev and Shramko’s bi-facial truth logic [42]. This logic may be useful in a situation when according to an agent’s point of view (i.e. internal point of view) her/his reasoning is rational, while from the external one it might be not the case. One may use LIRA, if one wants to reconstruct an agent’s way of thinking, compare it with respect to the real state of affairs, and understand why an agent thought in this or that way. Moreover, we discuss Kubyshkina and Zaitsev’s necessity and possibility operators for LRA definable by means of four-valued Kripke-style semantics and show that, due to two negations (as well as their combination) of LRA, two more possibility operators for LRA can be defined. Then we slightly modify all these modalities to be appropriate for LIRA. Finally, we formalize all the truth-functional n-ary extensions of the negation fragment of LIRA (including LIRA itself) as well as their basic modal extension via linear-type natural deduction systems. Keywords: Logic of rational agent, logic of internal rational agency, four-valued logic, logic of generalized truth values, modal logic, natural deduction, correspondence analysis. -

6C Lecture 2: April 3, 2014
6c Lecture 2: April 3, 2014 2.1 Functional completeness, normal forms, and struc- tural induction Before we begin, lets give a formal definition of a truth table. Definition 2.1. A truth table for a set of propositional variables, is a function which assigns each valuation of these variables either the value true or false. Given a formula φ, the truth table of φ is the truth table assigning each valuation of the variables of v the corresponding truth value of φ. We are ready to begin: Definition 2.2. We say that a set S of logical connective is functionally com- plete if for every finite set of propositional variables p1; : : : ; pn and every truth table for the variables p1; : : : ; pn, there exists a propositional formula φ using the variables p1; : : : ; pn and connectives only from S so that φ has the given truth table. We will soon show that the set f:; ^; _g is functionally complete. Before this, lets do a quick example. Here is an example of a truth table for the variables p1; p2; p3: p1 p2 p3 T T T T T T F F T F T T T F F T F T T F F T F F F F T F F F F F If f:; ^; _g is functionally complete, then we must be able to find a formula using only f:; ^; _g which has this given truth table (indeed, we must be able to do this for every truth able). In this case, one such a formula is p1 ^ (:p2 _ p3). -

Warren Goldfarb, Notes on Metamathematics
Notes on Metamathematics Warren Goldfarb W.B. Pearson Professor of Modern Mathematics and Mathematical Logic Department of Philosophy Harvard University DRAFT: January 1, 2018 In Memory of Burton Dreben (1927{1999), whose spirited teaching on G¨odeliantopics provided the original inspiration for these Notes. Contents 1 Axiomatics 1 1.1 Formal languages . 1 1.2 Axioms and rules of inference . 5 1.3 Natural numbers: the successor function . 9 1.4 General notions . 13 1.5 Peano Arithmetic. 15 1.6 Basic laws of arithmetic . 18 2 G¨odel'sProof 23 2.1 G¨odelnumbering . 23 2.2 Primitive recursive functions and relations . 25 2.3 Arithmetization of syntax . 30 2.4 Numeralwise representability . 35 2.5 Proof of incompleteness . 37 2.6 `I am not derivable' . 40 3 Formalized Metamathematics 43 3.1 The Fixed Point Lemma . 43 3.2 G¨odel'sSecond Incompleteness Theorem . 47 3.3 The First Incompleteness Theorem Sharpened . 52 3.4 L¨ob'sTheorem . 55 4 Formalizing Primitive Recursion 59 4.1 ∆0,Σ1, and Π1 formulas . 59 4.2 Σ1-completeness and Σ1-soundness . 61 4.3 Proof of Representability . 63 3 5 Formalized Semantics 69 5.1 Tarski's Theorem . 69 5.2 Defining truth for LPA .......................... 72 5.3 Uses of the truth-definition . 74 5.4 Second-order Arithmetic . 76 5.5 Partial truth predicates . 79 5.6 Truth for other languages . 81 6 Computability 85 6.1 Computability . 85 6.2 Recursive and partial recursive functions . 87 6.3 The Normal Form Theorem and the Halting Problem . 91 6.4 Turing Machines . -

CS40-S13: Functional Completeness 1 Introduction
CS40-S13: Functional Completeness Victor Amelkin [email protected] April 12, 2013 In class, we have briefly discussed what functional completeness means and how to prove that a certain system (a set) of logical operators is functionally complete. In this note, I will review what functional completeness is, how to prove that a system of logical operators is complete as well as how to prove that a system is incomplete. 1 Introduction When we talk about logical operators, we mean operators like ^, _, :, !, ⊕. Logical operators work on propositions, i.e. if we write a ^ b, then both a and b are propositions. The mentioned propositions may be either simple or compound, as in a ^ :(x ! y) { here, a is simple, while b is compound. | {z } b For a logical operator it does not matter whether it operates on simple or compound propositions; the only thing that matters is that all the arguments are propositions, i.e., either True of False. Since logical operators apply to propositions and \return" either True or False, they can be seen as boolean functions. For example, conjunction ^(x1; x2) = x1 ^ x2 is a binary boolean function, i.e., it accepts two arguments (hence, \binary") that can be either True of False and returns either True of False (hence, \boolean"). As another example, negation can be seen as a unary (accepts only one argument) boolean function :(x) = :x. We, however, rarely use the functional notation ^(x1; x2) (like in f(x)); instead, we usually use the operator notation, e.g., x1 _ x2. (Similarly, when you do algebra, you probably write a + b instead of +(a; b), unless you do algebra in Lisp.) Further, instead of talking about logical operators, we will talk about boolean functions, but, having read the material above, you should understand that these two are the same. -

Logical Connectives in Natural Languages
Logical connectives in natural languages Leo´ Picat Introduction Natural languages all have common points. These shared features define and constrain them. A key property of all natural languages is their learnability. As long as children are exposed to it, they can learn any spoken or signed language. This process takes place in environments in which children are not exposed to the full diversity of their mother tongue: it is with only few evidences that they master the ability to express themselves through language. As children are not exposed to negative evidences, learning a language would not be possible if con- straints were not present to limit the space of possible languages. Input-based theories predict that these constraints result from general cognition mechanisms. Knowledge-based theories predict that they are language specific and are part of a Universal Grammar [1]. Which approach is the right one is still a matter of debate and the implementation of these constraints within our brain is still to be determined. Yet, one can get a taste of them as they surface in linguistic universals. Universals have been formulated for most domains of linguistics. The first person to open the way was Greenberg [2] who described 50 statements about syntax and morphology across languages. In the phono- logical domain, all languages have stops for example [3]. Though, few universals are this absolute; most of them are more statistical truth or take the form of conditional statements. Universals have also been defined for semantics with more or less success [4]. Some of them shed light on non-linguistic abilities. -

Switching Circuits and Logic Design
Contents 1 Boolean Algebra F TECHN O OL E O T G U Y IT K T H S A N R I A N G A P I U D R N I 19 51 yog, km s kOflm^ Chittaranjan Mandal (IIT Kharagpur) SCLD January 28, 2020 1 / 12 Boolean Algebra Section outline Boolean expression manipulation 1 Boolean Algebra Exclusive OR SOP from sets Series-parallel switching Boolean expressions circuits Functional completeness Shannon decomposition Distinct Boolean functions F TECHN O OL E O T G U Y IT K T H S A N R I A N G A P I U D R N I 19 51 yog, km s kOflm^ Chittaranjan Mandal (IIT Kharagpur) SCLD January 28, 2020 2 / 12 1^2 A \ B (A \ B \ C) [ (A \ B \ C) abc + abc = ab 1^2^3^5 A (A \ B \ C) [ (A \ B \ C) [ (A \ B \ C) [ (A \ B \ C) abc + abc + abc + abc = ab + ab = a a I have an item from A a I don’t have an item from A ab + c I have an item from A but not from B or an item from C Boolean Algebra SOP from sets Sum of products from sets Selections Regions 1 A \ B \ C B 2 A \ B \ C 6 8 3 A \ B \ C 2 4 4 A \ B \ C 1 5 3 7 5 A \ B \ C A C 6 A \ B \ C 7 A \ B \ C 8 A \ B \ C F TECHN O OL E O T G U Y IT K T H S A N R I A N G A P I U D R N I 19 51 yog, km s kOflm^ Chittaranjan Mandal (IIT Kharagpur) SCLD January 28, 2020 3 / 12 (A \ B \ C) [ (A \ B \ C) abc + abc = ab 1^2^3^5 A (A \ B \ C) [ (A \ B \ C) [ (A \ B \ C) [ (A \ B \ C) abc + abc + abc + abc = ab + ab = a a I have an item from A a I don’t have an item from A ab + c I have an item from A but not from B or an item from C Boolean Algebra SOP from sets Sum of products from sets Selections Regions 1^2 A \ B 1 A \ B \ C B 2 A \ B \ C 6 -

An Introduction to Formal Logic
forall x: Calgary An Introduction to Formal Logic By P. D. Magnus Tim Button with additions by J. Robert Loftis Robert Trueman remixed and revised by Aaron Thomas-Bolduc Richard Zach Fall 2021 This book is based on forallx: Cambridge, by Tim Button (University College Lon- don), used under a CC BY 4.0 license, which is based in turn on forallx, by P.D. Magnus (University at Albany, State University of New York), used under a CC BY 4.0 li- cense, and was remixed, revised, & expanded by Aaron Thomas-Bolduc & Richard Zach (University of Calgary). It includes additional material from forallx by P.D. Magnus and Metatheory by Tim Button, used under a CC BY 4.0 license, from forallx: Lorain County Remix, by Cathal Woods and J. Robert Loftis, and from A Modal Logic Primer by Robert Trueman, used with permission. This work is licensed under a Creative Commons Attribution 4.0 license. You are free to copy and redistribute the material in any medium or format, and remix, transform, and build upon the material for any purpose, even commercially, under the following terms: ⊲ You must give appropriate credit, provide a link to the license, and indicate if changes were made. You may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use. ⊲ You may not apply legal terms or technological measures that legally restrict others from doing anything the license permits. The LATEX source for this book is available on GitHub and PDFs at forallx.openlogicproject.org.