On the Effectiveness of Time Travel to Inject COVID-19 Alerts⋆
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Download Download
FIVE CENTURIES OF REGIONAL DEVELOPMENT IN NORTHWEST GERMANY AND THE NETHERLANDS Kees Terlouw Urban and Regional research centre Utrecht Faculty ofGeosciences Utrecht University [email protected] ABSTRACT Germany and the Netherlands have developed very differently over the centuries. A close examination of Dutch and German regions show the differentiated way in which regions profit from the changing developmental opportunities of the world-system. This article studies long term regional development using regional urban population in the Netherlands and Northwest Germany. Initially the coastal regions profited from the emerging trade based agricultural world system. Later on, state formation enabled some of the previously developed regions to regain their position. Industrialization concentrated the development. In recent times, development spreads, giving developmental opportunities to some previously disadvantaged regions that are well located and well-endowed to profit from the recent developments in the world-system. INTRODUCTION The world-system approach is mostly used to explain the differences in development between states. This paper applies the world-system approach to the development of regions in two countries which have from the start belonged to the world-system. The position of the Netherlands and Germany in the world-system has however changed considerably between the emergence of the world-system and the present. The Netherlands and Northwest Germany belonged from the start to the world-system (Wallerstein 1974). Several types of important relations shaped this area from the early modem times. For instance grain exports from the German part facilitated the population growth of Dutch trade cities. Half the food for these urban populations was imported. -

2021 EBFF Amateur Bodybuilding Championships
European Bodybuilding & Fitness Federation 2021 EBFF Amateur Bodybuilding Championships 12-17 May, 2021, Santa Susanna, Spain O F F I C I A L C O N T E S T R E S U L T S Men's Games Classic Bodybuilding, Open RD2x PLACE BORN BW/ BH RD1 RD3 RD4 Score No NAME COUNTRY 2 1 45 Bogdan Vaipan Romania 1983 86.2/183.7 10 18 8 0 26 2 49 Igor Sikora Serbia 1993 93/188 13 24 10 0 34 3 44 Siim Savisaar Estonia 1988 72.8/176.5 9 24 16 0 40 4 40 Aleksandar Cvetkovic Serbia 1982 76.4/176 23 46 25 0 71 5 50 Cosmin Iancu Romania 1987 69.2/170 26 50 22 0 72 6 41 Jeve Ojala Finland 1991 89/185.5 30 50 28 0 78 7 47 Dragos Enuta Romania 1982 74/174.4 32 0 0 0 0 8 42 Radoslaw Dykowski Poland 1980 84/181.4 44 0 0 0 0 9 39 Ramil Lipp Estonia 1980 77.1/179.5 45 0 0 0 0 10 38 Leo Polkki Finland 1993 82.2/178.8 50 0 0 0 0 11 37 Jozsef Nyircsak Hungary 1999 77.5/178.5 55 0 0 0 0 12 36 Olivier Pieters Belgium 1995 72.3/177 62 0 0 0 0 13 48 Ondrej Janus Czech Republic 1999 82.8/187 65 0 0 0 0 14 43 Mario Impens Belgium 1983 78.8/183.1 67 0 0 0 0 15 46 Michael Laschitz Austria 1989 75.8/179.5 72 0 0 0 0 Σ=15 Men's Wheelchair Bodybuilding Open RD1x PLACE BORN BW/ BH RD2 RD3 RD4 Score No NAME COUNTRY 2 1 90 Andrei Cimpan Romania 2000 / 12 6 0 0 18 2 89 Gilles Sagnard France / 18 9 0 0 27 Σ=2 Men's Physique up to 170 cm PLACE No NAME COUNTRY BORN BW/ BH RD1 RD2 RD3 RD4 Score 1 223 Ruslan Podopryhora Ukraine 1995 /168.2 8 7 0 0 7 2 222 Vitalii Salata Ukraine 1993 /165 9 10 0 0 10 3 218 Sebastian Jansson Sweden 1991 /166 14 15 0 0 15 4 215 Francisco Garcia Spain 1991 /168.5 -

Establishment of Predictive Validity and Reliability of a Newly Developed Fear of Falling Scale in Hong Kong
Hong Kong Physiotherapy Journal (2011) 29,2e11 available at www.sciencedirect.com journal homepage: www.hkpj-online.com RESEARCH REPORT Establishment of predictive validity and reliability of a newly developed fear of falling scale in Hong Kong Sheung Lin Kuo, PhD*, Jennifer Catherine Nitz, PhD Division of Physiotherapy, School of Health and Rehabilitation Sciences, The University of Queensland, St Lucia, Queensland, Australia KEYWORDS Abstract Fall events and fear of falling increase with age in healthy and frail older people. balance tests; Fear of falling has been identified as a significant falls risk factor. The aims of this study were elderly; to establish the interrater and test-retest reliability and predictive validity of the fear of falling fall screening; scale (FOFS). Sixty-nine subjects, 55 female and 14 male subjects, aged 65e97 years were fear of falling included. Subjects were asked to respond to the FOFS on three occasions to test interrater and test-retest reliability. In the absence of a suitable comparative test for concurrent validity, balance predictive formulae were developed and relationship to Functional Reach Test, Timed up & go, and Step Test performance were compared. Intraclass coefficient (2,1) of interrater and test-retest reliability was 0.96 and 0.94, respectively. The Cronbach a for the FOFS scores collected ranged from 0.94 to 0.97. From the results of the multiple regression analyses, prediction formulae for Functional Reach Test, Timed up & go test, and Step Test from the FOFS scores were generated. These formulae then predicted balance performance by the subjects. The interrater and test-retest reliability and the predictive validity of the FOFS were estab- lished. -

108513 Masterthesis.Raphael.Nitz
FSM - Finance & Strategic Management Master Thesis “Bankruptcy acquisitions in Europe: an empirical analysis of a value creating strategy” . Thesis supervisor: Domenico Tripodi Author of the thesis: Raphael Karl Roderich Nitz Date of Submission: May 17th, 2016 Characters: 147.396 Pages: 66 Abstract This thesis provides evidence that takeovers can be a value creating strategy for the acquirer. Depending on the circumstances especially the focus on bankruptcy acquisitions can be of high interest for an acquirer. 14,495 recent takeovers within years of 2008 and 2014 in the euro zone have been examined and the results provide empirical evidence that acquisitions can facilitate a value creating effect for the acquirers. Here, acquirers of bankrupt firms often have some previous relationships along their value chain to the target company which suggests that the acquirers are well informed about the possible value extraction and utilization of the target‘s assets. However, within the examined transactions, findings show that in Europe between 2008 and 2014 non-bankruptcy acquisitions outperformed the bankruptcy transactions. But this performance of bankruptcy acquisitions is time-specific. Firms that are able to acquire bankrupt firms even within a troubled economic cycle must be financially very stable and gain from their strong bargaining power within such an environment. They are able to earn excess returns upon deal announcements of 1.66 percentage points compared to buyers within the post-crisis situation. This evidence is in line with the opinion that some companies can take advantage of fire sales by bankrupt companies as part of a corporate restructuring. In addition, the type of the bankruptcy acquisition is of great importance as its performance is also industry-specific. -

How Do We Remember the Armenian Genocide and the Holocaust? a Global View of an Integrated Memory of Perpetrators, Victims and Third–Party Countries
6/2020 PEACE RESEARCH INSTITUTE FRANKFURT / LEIBNIZ-INSTITUT HESSISCHE STIFTUNG FRIEDENS- UND KONFLIKTFORSCHUNG ELDAD BEN AHARON // HOW DO WE REMEMBER THE ARMENIAN GENOCIDE AND THE HOLOCAUST? A GLOBAL VIEW OF AN INTEGRATED MEMORY OF PERPETRATORS, VICTIMS AND THIRD–PARTY COUNTRIES PRIF Report 6/2020 HOW DO WE REMEMBER THE ARMENIAN GENOCIDE AND THE HOLOCAUST? A GLOBAL VIEW OF AN INTEGRATED MEMORY OF PERPETRATORS, VICTIMS AND THIRD–PARTY COUNTRIES ELDAD BEN AHARON // ImprInt LEIBNIZ-INSTITUT HESSISCHE STIFTUNG FRIEDENS- UND KONFLIKTFORSCHUNG (HSFK) PEACE RESEARCH INSTITUTE FRANKFURT (PRIF) Cover: Titel: Holocaust Memorial in Berlin © flickr, /// Sarah, https://bit.ly/3kUdlY7., https://creativecommons.org/licenses/by-nc/2.0/ Text license: Creative Commons CC-BY-ND (Attribution/NoDerivatives/4.0 International). The images used are subject to their own licenses. Correspondence to: Peace Research Institute Frankfurt Baseler Straße 27–31 D-60329 Frankfurt am Main Telephone: +49 69 95 91 04-0 E-Mail: [email protected] https://www.prif.org ISBN: 978-3-946459-59-0 Summary In 1915, during World War I, the declining Ottoman Empire carried out an extended campaign of geno- cide against the Ottoman Armenians. From massacres to death marches, 1.5 million of the Armenian population were exterminated. The Holocaust, in which six million European Jews were exterminated as part of what the Nazis called the ‘Final Solution of the Jewish Question,’ was perpetrated during World War II. Over the last forty years, the memorialisation of the Holocaust has become a distinct aspect of Western culture, encompassing reparations, museums, memorials and documentaries, and even legislation criminal- ising its denial. -
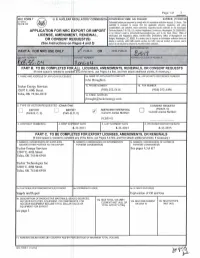
Export License Amendment Application from Tucker Energy
Page 1 of 3 APPROVED BY OMB: NO. 3150-0027 EXPIRES: (11/30/2015) Estimated burden per response to comply with this mandatory collection request: 2.4 hours. This submittal is reviewed to ensure that the applicable statutory. regulatory, and policy considerations are satisfied. Send comments regarding burden estimate to the Infonnation ~~~~;~::~PLICATIONUF::U:::R1::::::~~::::Services Branch (T-5 F53), U.S. Nuclear Regulatory Commission, Washington, DC 20555-0001, or by internet e-mail to [email protected], and to the Desk Officer. Office of LICENSE, AMENDME~T, RENEWAL, Infonnation and Regulatory Affairs, NEOB-10202, (3150-0027), Office of Management and OR CONSENT R~IQUEST(S) Budget, Washington, DC 20503. If a means used to impose an infonnation collection does not display a currently valid OMB control number, the NRC may not conduct or sponsor, and a (See Instructions onl~ages 4 and 5) person is not required to respond to, the infonnation collection. PART B. TO BE COMPLETED FokiALL LICENSES, AMENDMENTS, RENEWALS, OR CONSENT REQUESTS (If more space is needed to compl~tr any of the items, use Pages 3-4 first, and then attach additional sheets, if necessary.) 1. NAME AND ADDRESS OF APPLICANT/LICENSEE I 1a. NAME OF APPLICANT'S CONTACT 1b. APPLICANT'S REFERENCE NUMBER John Broughton Tucker Energy Services 1c. PHONE NUMBER 1d. FAX NUMBER 12607 E. 60th Street (918) 252-5416 (918) 252-4496 Tulsa, OK 74146-6910 1e. E-MAIL ADDRESS [email protected] 2. TYPE OF ACTION REQUESTED (Check OnJ) CONSENT REQUEST (Parts B, C) EXPORT IMPORT AMENDMENT/RENEWAL D D D Current License Number: (Parts B, C, E) (Parts Bi' D, E) Current License Number: PCB55-03 3. -

UMTS); LTE; Network Identity and Time Zone (NITZ); Service Description; Stage 1 (3GPP TS 22.042 Version 9.0.0 Release 9)
ETSI TS 122 042 V9.0.0 (2010-01) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Network Identity and Time Zone (NITZ); Service description; Stage 1 (3GPP TS 22.042 version 9.0.0 Release 9) 3GPP TS 22.042 version 9.0.0 Release 9 1 ETSI TS 122 042 V9.0.0 (2010-01) Reference RTS/TSGS-0122042v900 Keywords GSM, LTE, UMTS ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice Individual copies of the present document can be downloaded from: http://www.etsi.org The present document may be made available in more than one electronic version or in print. In any case of existing or perceived difference in contents between such versions, the reference version is the Portable Document Format (PDF). In case of dispute, the reference shall be the printing on ETSI printers of the PDF version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at http://portal.etsi.org/tb/status/status.asp If you find errors in the present document, please send your comment to one of the following services: http://portal.etsi.org/chaircor/ETSI_support.asp Copyright Notification No part may be reproduced except as authorized by written permission. -

SARA-G3 Series Dual and Quad-Band GSM/GPRS Modules Data Sheet
SARA-G3 series Dual and quad-band GSM/GPRS modules Data sheet Abstract Technical data sheet describing SARA-G3 series GSM/GPRS cellular modules. These modules are complete and cost-efficient solutions offering two-band or quad-band GSM/GPRS voice and/or data transmission technology in a compact form factor. UBX-13000993 - R24 C1-Public www.u-blox.com SARA-G3 series - Data sheet Document information Title SARA-G3 series Subtitle Dual and quad-band GSM/GPRS modules Document type Data sheet Document number UBX-13000993 Revision and date R24 18-Jun-2021 Disclosure restriction C1-Public Product status Corresponding content status Functional sample Draft For functional testing. Revised and supplementary data will be published later. In development / Objective specification Target values. Revised and supplementary data will be published later. Prototype Engineering sample Advance information Data based on early testing. Revised and supplementary data will be published later. Initial production Early production information Data from product verification. Revised and supplementary data may be published later. Mass production / Production information Document contains the final product specification. End of life This document applies to the following products: Product name Type number Modem version Application version PCN reference Product status SARA-G300 SARA-G300-00S-01 08.58 A01.01 UBX-16010060 Obsolete SARA-G310 SARA-G310-00S-01 08.58 A01.01 UBX-16010060 Obsolete SARA-G340 SARA-G340-00S-00 08.49 N.A. UBX-14000382 Obsolete SARA-G340-01S-00 08.70 A00.02 UBX-14039634 Obsolete SARA-G340-02S-00 08.90 A00.02 UBX-16001074 Obsolete SARA-G340-02S-01 08.90 A01.13 UBX-20057620 End of life SARA-G340 ATEX SARA-G340-02X-00 08.90 A00.02 UBX-16017766 Obsolete SARA-G340-02X-01 08.90 A01.13 UBX-20057620 Obsolete SARA-G350 SARA-G350-00S-00 08.49 N.A. -

TS-3GA-22.042(Rel11)V11.0.0 Network Identity and Timezone (NITZ)
TS-3GA-22.042(Rel11)v11.0.0 Network Identity and TimeZone (NITZ); Service description; Stage 1 2013 年 6 月 25 日制定 一般社団法人 情報通信技術委員会 THE TELECOMMUNICATION TECHNOLOGY COMMITTEE 本書は、一般社団法人情報通信技術委員会が著作権を保有しています。 内容の一部又は全部を一般社団法人情報通信技術委員会の許諾を得ることなく複製、 転載、改変、転用及びネットワーク上での送信、配布を行うことを禁止します。 TS-3GA-22.042(Rel11)v11.0.0 Network Identity and TimeZone (NITZ); Service description; Stage 1 <参考> [Remarks] 1.英文記述の適用レベル [Application level of English description] 適用レベル [Application level]:E2 本標準の本文、付属資料および付録の文章および図に英文記述を含んでいる。 [English description is included in the text and figures of main body, annexes and appendices.] 2.国際勧告等の関連 [Relationship with international recommendations and standards] 本標準は、3GPP で承認された Technical Specification 22.042 (Version 11.0.0) に準拠している。 [This standard is standardized based on the Technical Specification 22.042 (Version 11.0.0) approved by 3GPP.] 3.上記国際勧告等に対する追加項目等 [Departures from international recommendations] 原標準に対する変更項目 [Changes to original standard] 原標準が参照する標準のうち、TTC 標準に置き換える項目。[Standards referred to in the original standard, which are replaced by TTC standards.] 原標準が参照する標準のうち、それらに準拠した TTC 標準等が制定されている場合は自動的に 最新版 TTC 標準等に置き換え参照するものとする。 [Standards referred to in the original standard should be replaced by derived TTC standards.] 4.工業所有権 [IPR] 本標準に関わる「工業所有権等の実施の権利に係る確認書」の提出状況は、TTCホームページによる。 [Status of “Confirmation of IPR Licensing Condition” submitted is provided in the TTC web site.] 5.作成専門委員会 [Working Group] 3GPP 専門委員会 [3GPP Working Group] i 3GPP TS 22.042 V11.0.0 (2012-09) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Network Identity and TimeZone (NITZ); Service description; Stage 1 (Release 11) The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. -

B5 Call Ja 09.02.09
EXECUTIVE AGENCY FOR HEALTH AND CONSUMERS COMMON ACTIVITIES (JOINT ACTIONS) BETWEEN NATIONAL AUTHORITIES RESPONSIBLE FOR THE ENFORCEMENT OF CONSUMER PROTECTION LAWS (Regulation n° 2006/2004 on Consumer Protection Cooperation) ACTION 8 OF DECISION N° 1926/2006/EC ESTABLISHING A PROGRAMME FOR COMMUNITY ACTION IN THE FIELD OF CONSUMER POLICY CALL FOR PROPOSALS 2009 E-mail: [email protected] Web: http://ec.europa.eu/eahc/ Commission européenne, B-1049 Bruxelles / Europese Commissie, B-1049 Brussel - Belgium. Telephone: (32-2) 299 11 11. NOTICE Under Council Regulation (EC) No 58/2003 of 19 December 2002 laying down the statute for executive agencies to be entrusted with certain tasks in the management of Community programmes1, the Commission can decide to delegate all or part of the implementation of the programme of Community action in the field of consumer policy (2007-2013), on its behalf and under its responsibility, to an executive agency. By Decision 2004/858/58/EC of 15 December 2004 the Commission created the "Executive Agency for the Public Health Programme" (PHEA), with a view to perform tasks linked to the implementation of the Community action in the field of Public Health, pursuant to Council Regulation (EC) N° 58/2003. On June, 20th 2008, the Commission transformed PHEA into the "Executive Agency for Health and Consumers" -hereinafter "EAHC"- (see Commission Decision 2008/544/EC) and decided to delegate to EAHC part of the implementation of the programme of Community action in the field of consumer policy (2007-2013), adopted by Decision No 1926/2006/EC of the European Parliament and the Council of 18 December 20062. -
SPSM'16 ~ White Rabbit in Mobile: Effect of Unsecured Clock Source In
White Rabbit in Mobile: Effect of Unsecured Clock Source in Smartphones Shinjo Park Altaf Shaik Ravishankar Borgaonkar TU Berlin & Telekom TU Berlin & Telekom Oxford University Innovation Laboratories Innovation Laboratories [email protected] [email protected] [email protected] berlin.de berlin.de Jean-Pierre Seifert TU Berlin & Telekom Innovation Laboratories [email protected] berlin.de ABSTRACT 1. INTRODUCTION With its high penetration rate and relatively good clock ac- The convergence towards smartphones, and the new mar- curacy, smartphones are replacing watches in several market ket opened by wearables integrated several devices into segments. Modern smartphones have more than one clock them, including wrist watches. According to CNET, the source to complement each other: NITZ (Network Identity popularity of smart watches negatively affected the sales of and Time Zone), NTP (Network Time Protocol), and GNSS traditional wrist watches [43]. Like wrist watches, they are (Global Navigation Satellite System) including GPS. NITZ designed to be carried every day, providing accurate time in- information is delivered by the cellular core network, indi- formation. While watches require manual adjustment when cating the network name and clock information. NTP pro- the battery has been changed or when there is a change vides a facility to synchronize the clock with a time server. regarding DST (Daylight Saving Time)1, smartphones au- Among these clock sources, only NITZ and NTP are up- tomatically retrieve current time information from multiple dated without user interaction, as location services require sources and propagate it to connected wearables like smart manual activation. -
Quectel LPWA Module Product Overview
Quectel LPWA Module Product Overview May, 2019 © Quectel Wireless Solutions Co., Ltd. All rights reserved LPWA Technology LPWA Modules Summary Product Overview Applications @ Quectel Wireless Solutions | May, 2019 | Page 2 Rev.: V2.2 | Status: Released LPWA Network Deployment (Updated on May 21, 2019) Over 25 mobile operators have committed to deploying Cat M1 and/or Cat NB1 networks. Sourced from GSMA. @ Quectel Wireless Solutions | May, 2019 | Page 3 Rev.: V2.2 | Status: Released NB-IoT Global Coverage (1) (Updated on May 21, 2019) NB-IoT = 78 Operator Country/Region Bands Operator Country/Region Bands Operator Country/Region Bands 3 HONG KONG 8 GRAMEENPHONE BANGLADESH 3, 8 (TBC) STC SAUDI ARABIA 12 A1 Austria KT SOUTH KOREA 3 SWISSCOM SWITZERLAND 20 Taiwan, Province of A1 Croatia Kyvistar Ukraine Taiwan Mobile 3,28 China AIS THAILAND 8 LGU+ SOUTH KOREA 5 TDC Denmark 20 APTG TAIWAIN 8 M1 SINGAPORE 20, 8 Telecom Italia Brazil (TIM Brazil) 3,28 ALTICE PORTUGAL 20 Maxis Malaysia (6 cities) Telecom Italia Italy 20 CHINA MOBILE CHINA 8 MOBITEL SRI LANKA 8 Telefonica Spain 20 CHINA MOBILE HONG KONG 3 MEGAFON RUSSIA 20, 8, 3 Telefonica Brazil CHINA TELECOM CHINA 5 Mobitel Sri Lanka Telefonica Germany CHINA UNICOM CHINA 3, 8 MTS RUSSIA 3 Telenor Denmark CHUNGHWA TAIWAIN 8 ORANGE BELGUIM 20 Telenor Norway 8,20 DIALOG SRI LANKA 3, 8 Proximus Belgium TELIA FINLAND 20, 3 DNA FINLAND 20 SFR France TELIA NORWAY 20 DU UAE SINGTEL SINGAPORE 8 TELIA SWEDEN 20 ELISA FINLAND 20, 3 Smartone Hong Kong TELIA DENMARK 20, 8 ETISALAT UAE 20 SOFTBANK JAPAN 1,8 TELIA ESTONIA FAREASTONE TAIWAIN 28 StarHub Singapore 8 TELKOMSEL IDONESIA 8 Sourced from GSMA.