Threat Landscape Report Q2 2019
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adobe Golive 5 Gratis Epub, Ebook
ADOBE GOLIVE 5 GRATIS Auteur: Deborah Shadovitz Aantal pagina's: 1024 pagina's Verschijningsdatum: none Uitgever: none EAN: 9789039516010 Taal: nl Link: Download hier letsland.nl Up to two pounds, will most likely ship priority. Over 2 pounds, will ship FedEx or parcel. International buyers: we ship using only the eBay global shipping program. We do not control what eBay charges, nor can we even see the amount. We cannot combine international shipping unless you contact us prior to any bids being placed on the items you want. We leave positive feedback as soon as payment is received, and would ask you to do the courtesy of allowing us to solve any issues you might have. Software might not work on other version of Mac OS. Please make sure it works on your machine before you buy it. Create and publish content for print and the Web faster and more easily than ever before--all at an outstanding value. Adobe integration makes it possible. The Adobe Creative Suite makes it affordable. Get the functionality most suited to your needs or install everything at once to ensure that the right tool is always there when you need it. With over new features, Adobe GoLive 5. Move from creative concepts to dynamic, high-impact Web sites with the power of one of the industry's most comprehensive and integrated Web applications. Despite a slightly delayed release, Adobe's GoLive 5. Graphically oriented designers will enjoy the program's drag-and-drop simplicity and tight integration with other Adobe packages such as PhotoShop and Illustrator; and serious coders should appreciate GoLive's new customization options and Code feature that protects existing code from undesired modification. -

Adobe Systems FY2006 10-K/A
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 ________________ FORM 10-K/A (Amendment No. 1) ________________ (Mark One) [X] ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 1, 2006 OR [ ] TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission file number: 0-15175 ADOBE SYSTEMS INCORPORATED (Exact name of registrant as specified in its charter) Delaware 77-0019522 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 345 Park Avenue, San Jose, California 95110-2704 (Address of principal executive offices and zip code) (408) 536-6000 (Registrant’s telephone number, including area code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered Common Stock, $0.0001 par value per share The NASDAQ Stock Market LLC (NASDAQ Global Select Market) Securities registered pursuant to Section 12(g) of the Act: None Indicate by checkmark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes [X] No [ ] Indicate by checkmark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes [ ] No [X] Indicate by checkmark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15 (d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -
Download Our Information in Adobe Acrobat Reader PDF Format
MIBCI Contractors - Home Phone: (586) 243-1223 E-mail: mbci@mbcicontractors. com Simplicity is complexity made simple Home Our Services Residential Gallery Commercial Gallery Contact Us Tips HOME Services COMMERCIAL MBCI Contractors is a professionally managed construction company, licensed by the State of ● Commercial Michigan; specializing in residential, commercial construction, custom built homes, additions, garages, basements, and complete home remodeling. RESIDENTIAL We offer all kinds of designs, permits, consultation and ● Custom Built professional work and results. Homes We provide a complete renovation project services. All ● Additions your construction needs are handled from the start ● Garages point to the end. ● Basements We run, manage and back your custom built, additions ● Kitchens and improvements during and after completion. ● Bathrooms ● Decks & porches Download our information in Adobe Acrobat Reader PDF format Copyright 2011 MBCI Contractors - All rights reserved Website Design by LAC Consulting Services http://www.mbcicontractors.com/mbcicontractors/29/12/2010 12:06:18 AM MBCI Contractors - Our Services Phone: (586) 243-1223 E-mail: mbci@mbcicontractors. com Simplicity is complexity made simple Home Our Services Residential Gallery Commercial Gallery Contact Us Tips OUR SERVICES Services COMMERCIAL COMMERCIAL Commercial construction from the ground up; or expansions; or renovations will be done according to ● Commercial your requirements. See Commercial Gallery for work we have done. RESIDENTIAL RESIDENTIAL ● Custom Built We do home improvements, renovations, and Homes additions. See Residential Gallery for possibilities ● Additions and options. ● Garages Custom Built Homes ● Basements MBCI can help build your custom home from ● Kitchens underground up. Together we can plan, design and ● Bathrooms build your dream home. ● Decks & porches Additions MBCI can design or use your design to build any size of addition from a whole floor to a one room, any size, shape and design. -

Birch Hall, Rooms 105 / 107 (Birch Lab a / B) Each: 19 Seat Classroom (18 Student, 1 Instructor)
Tech Training Classroom Software Modified 5/19/2015 DC Redwood Hall, Room G6 (POST), Birch Hall, Rooms 105 / 107 (Birch Lab A / B) Each: 19 seat classroom (18 student, 1 instructor) All labs equipped with Apple Mac Minis (2.7GHz Intel Core i7, 4GB 1333MHz DDR3, AMD Radeon HD 6630M 256MB 500GB Toshiba 5400rpm SATA3 Hard Drive) Software Windows 7 Mac OS 10.9.5 Internet Browsers Microsoft Internet Explorer 9 √ Google Chrome 41 (PC), 39 (Mac) √ √ Mozilla Firefox 36.0.1 (PC), 33.1.1 (Mac) √ √ Safari 7.1 √ Microsoft Office Microsoft Professional Plus 2010 SP3 (Word, Excel, PowerPoint, Access, Publisher, InfoPath, Sharepoint Workspace, Lync, OneNote) *No Outlook* √ Microsoft Professional Plus 2013 SP1 (Word, Excel, PowerPoint, Access, Outlook, Publisher, InfoPath, Lync, OneNote, OneDrive) √ Microsoft Visio 2013 √ Microsoft Project 2013 √ Microsoft Office 2011 14.4.6 (Word, Excel, PowerPoint, Outlook) and Lync 14.0.10, OneNote 15.4, OneDrive 17.3.4501) √ Zimbra Connector for Microsoft Outlook 8.0.8 √ Graphics Software Adobe CS6 Design & Web Premium √ √ Adobe Bridge CS6 x64 5.0.2.4 √ √ Adobe DPS App Builder 3.2.0 √ √ Adobe DNG Converter 8.6 √ √ Adobe Dreamweaver CS6 12.0 Win / 12.0.3 Mac √ √ Adobe Extension Manager CS6 6.0.8 √ √ Adobe Fireworks CS6 12.0.1 √ √ Adobe Flash Professional CS6 12.0.2 √ √ Adobe Illustrator CS6 x64 16.0.3 Win /16.0.4 Mac √ √ Adobe InDesign CS6 8.0.2 √ √ Adobe Media Encoder CS6 6.0.3.1 Win / 6.0.2 Mac √ √ Adobe Photoshop Extended CS6 x64 13.0.1 Win / 13.0.6 Mac √ √ Adobe Acrobat Pro 10.1.12 √ √ Adobe Distiller 10.1.12 √ -

Computer Technology Read... Courses
Computer Technology Readiness for Online Courses - LEGs/Schools COMPUTER TECHNOLOGY READINESS FOR WVS ONLINE COURSES Whether working on a computer at school, home, or another location, you want to be sure it is ready to handle most anything that may come up in an online course. Online courses make use of a wide variety of features and technologies such as: Java, Flash, HTML5, CSS2/3, and depending on the course, other specialized components that help achieve a more immersive learning experience. Due to the wide array of technologies in our over 100 courses, there are some limitations to browsers and devices that are supported. At present, our course providers test and verify a wide variety of devices and have ongoing programs to migrate away from any technologies that are not compliant with newer mobile platforms. In general however, lightweight devices such as Google Chromebooks or Nooks that have very limited technology support for Java or Flash, will not be compatible with the majority of our courses. Supported Browsers: You may use recent versions of the following browsers on a technology capable device that supports Java, Flash, and improvements to HTML including HTML5. ● Mozilla Firefox – If using Firefox as a browser and students are reporting that content will not load, audio files or pictures are missing on assessments, and assessments are blank, it may be due to a known issue of displaying mixed content in the Firefox browser. Firefox has developed an add-on that allows for mixed content to display. Work with your local IT support to install this add-on below as needed: https://addons.mozilla.org/en-US/firefox/addon/toggle-mixed-active-content/?src=ss Once installed, a small toolbar will appear in the bottom of your web browser. -
Buying Guide : Version Comparison | Adobe Photoshop
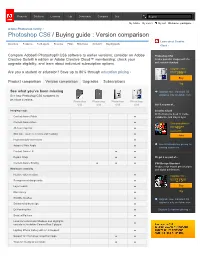
Products Solutions Learning Help Downloads Company Buy My Adobe My orders My cart Welcome, paulajane Adobe Photoshop family / Photoshop CS6 / Buying guide : Version comparison Learn about Creative Overview Features Tech specs Reviews FAQ Showcase In depth Buying guide Cloud › Compare Adobe® Photoshop® CS6 software to earlier versions; consider an Adobe Photoshop CS6 Creative Suite® 6 edition or Adobe Creative Cloud™ membership; check your Create powerful images with the upgrade eligibility; and learn about individual subscription options. professional standard Upgrade from Are you a student or educator? Save up to 80% through education pricing › US $199 00 Buy Product comparison Version comparison Upgrades Subscriptions Try See what you've been missing Upgrade now. Individual CS See how Photoshop CS6 compares to upgrades only on Adobe.com. previous versions. Photoshop Photoshop Photoshop Photoshop CS3 CS4 CS5 CS6 Get it as part of... Imaging magic Creative Cloud All the tools you need to create, Content-Aware Patch collaborate, and stay in sync Content-Aware Move One-year plan for All-new Crop tool US $ 99 49 per month Skin tone–aware selections and masking Join Improved auto-corrections Adaptive Wide Angle Special introductory pricing for existing customers Content-Aware Fill Puppet Warp Or get it as part of... Content-Aware Scaling CS6 Design Standard Produce high-impact print designs Maximum creativity and digital publications Intuitive video creation Upgrade from Reengineered design tools US $ 00 275 Layer search Buy Blur Gallery -
Step-By-Step Guide to Set-Up BDM Searchable Journal Voucher
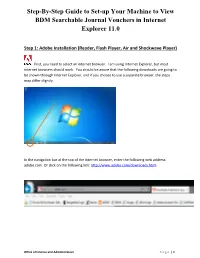
Step-By-Step Guide to Set-up Your Machine to View BDM Searchable Journal Vouchers in Internet Explorer 11.0 Step 1: Adobe Installation (Reader, Flash Player, Air and Shockwave Player) First, you need to select an internet browser. I am using Internet Explorer, but most internet browsers should work. You should be aware that the following downloads are going to be shown through Internet Explorer, and if you choose to use a separate browser, the steps may differ slightly. In the navigation bar at the top of the internet browser, enter the following web address: adobe.com. Or click on the following link: http://www.adobe.com/downloads.html Office of Finance and Administration P a g e | 1 Once you have entered the web address it will bring you to Adobe’s Downloads page. There are four downloads on the right hand side that you are going to need to download. They are Adobe Reader, Adobe Flash Player, Adobe AIR, and Adobe Shockwave Player. We will start with Adobe Reader. First, you need to click on the box that says Adobe Reader. This link will take you to the following page. Once here you need to UNCHECK both boxes that ask you to install the Optional Offer, then click on the button that says Install Now. After you have selected the Save File option, the file will be sent to the bottom of your browser. You need to then click the Save button. After you have selected the Save button, you need to select the Run button. Office of Finance and Administration P a g e | 2 Next, you need to allow your computer to download Adobe. -

Lista De Softwares Homologados
SOP - Segurança e Operação LISTA DE SOFTWARES HOMOLOGADOS (Versão 20210613– Atualizada em 13 de Junho de 2021) Sumário Áreas Administrativas2 I. Sistemas Operacionais2 II. Softwares Gratuitos2 IV. Softwares Licenciados13 V. Softwares Governamentais15 VI. Softwares Administrativos / CPD15 VII. Demais Softwares16 Áreas Administrativas I. Sistemas Operacionais Microsoft Windows Vista Business - Service Pack 2; Microsoft Windows Vista Enterprise - Service Pack 2; Microsoft Windows Vista Ultimate - Service Pack 2; Microsoft Windows 7 Professional – Service Pack 1; Microsoft Windows 7 Professional Enterprise – Service Pack 1; Microsoft Windows 7 Professional Ultimate - Service Pack 1; Microsoft Windows 8/8.1 Professional; Microsoft Windows 8/8.1 Enterprise. Microsoft Windows 10 Pro; Microsoft Windows 10 Enterprise; Microsoft Windows 10 Education. Importante: Todos os sistemas operacionais requerem licenças por parte dos usuários. Os equipamentos que estiverem utilizando o sistema operacional diferente do licenciado serão formatados e terão reinstalada a licença inicialmente adquirida. Atualmente as licenças são de responsabilidade das estruturas organizacionais da UnB, devendo ser salvaguardadas pelos respectivos usuários. II. Softwares Gratuitos Software Especificação Software para Compressão de Arquivos/Pastas; 7zip Ele é ideal para organizar e-books, guias, artigos e outros arquivos que envolvam texto e Adobe Digital Editions imagem nos formatos PDF e OCP, utilizando uma interface agradável e intuitiva. Adobe Reader DC Programa para visualizar, imprimir e comentar Voltar ao Sumário Página | 2 documentos PDF; O Shockwave Player exibe conteúdos da Adobe Shockwave Player 12 Internet que foram criados usando o Adobe ou superior Director; É um programa que faz lembrar coisas fácil. Porque é muito mais eficiente do que métodos de estudo tradicionais, você pode Anki diminuir muito seu tempo gasto estudando, ou aumentar muito a quantidade que você aprende. -

Raport CERT.GOV.PL Za III Kwartal 2011 Pdf, 2.12 MB
Agencja Bezpieczeństwa Wewnętrznego Raport kwartalny CERT.GOV.PL lipiec – wrzesień 2011 1. Informacje dotyczące zespołu CERT.GOV.PL .................................................................. 2 2. Statystyki systemu ARAKIS-GOV..................................................................................... 3 3. Statystyki incydentów ......................................................................................................... 5 4. Istotne podatności, zagrożenia i biuletyny zabezpieczeń ................................................... 9 5. Testy bezpieczeństwa witryn WWW instytucji państwowych ......................................... 18 6. Informacje z systemów zewnętrznych .............................................................................. 20 7. Inne działania CERT.GOV.PL ......................................................................................... 25 Agencja Bezpieczeństwa Wewnętrznego 1. Informacje dotyczące zespołu CERT.GOV.PL Rządowy Zespół Reagowania na Incydenty Komputerowe CERT.GOV.PL został powołany w dniu 1 lutego 2008 roku. Podstawowym zadaniem zespołu jest zapewnianie i rozwijanie zdolności jednostek organizacyjnych administracji publicznej Rzeczypospolitej Polskiej do ochrony przed cyberzagrożeniami, ze szczególnym uwzględnieniem ataków ukierunkowanych na infrastrukturę obejmującą systemy i sieci teleinformatyczne, których zniszczenie lub zakłócenie może stanowić zagrożenie dla życia, zdrowia ludzi, dziedzictwa narodowego oraz środowiska w znacznych rozmiarach, albo spowodować -

Adbe 10K Fy11- Final
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 _____________________________ FORM 10-K (Mark One) ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 2, 2011 or TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File Number: 0-15175 ADOBE SYSTEMS INCORPORATED (Exact name of registrant as specified in its charter) _____________________________ Delaware 77-0019522 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 345 Park Avenue, San Jose, California 95110-2704 (Address of principal executive offices and zip code) (408) 536-6000 (Registrant’s telephone number, including area code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered Common Stock, $0.0001 par value per share The NASDAQ Stock Market LLC (NASDAQ Global Select Market) Securities registered pursuant to Section 12(g) of the Act: None _____________________________ Indicate by checkmark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes No Indicate by checkmark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes No Indicate by checkmark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15 (d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports) and (2) has been subject to such filing requirements for the past 90 days. -

Webassign Student Guide June 2010 Webassign Student Guide Is Published by Advanced Instructional Systems, Inc
WebAssign Student Guide June 2010 WebAssign Student Guide is published by Advanced Instructional Systems, Inc. © 2010 by Advanced Instructional Systems, Inc. All rights reserved. Printed in the United States of America. 06.02.2010 WebAssign™ is a service mark of Advanced Instructional Systems, Inc. calcPad®, chemPad®, pencilPad®, and Personal Study Plan® are registered trademarks of Advanced Instructional Systems, Inc. (dba WebAssign). WebAssign™, physPad™, and numberLine™ are trademarks of WebAssign. Adobe®, Acrobat®, Acrobat Reader®, Flash®, and Shockwave® are registered trademarks of Adobe Systems Incorporated in the United States, other countries, or both. Apple®, Mac®, and Safari® are registered trademarks of Apple Inc., in the United States, other countries, or both. Internet Explorer®, Microsoft®, PowerPoint®, and Windows® are registered trademarks of Microsoft Corporation in the United States, other countries, or both. Java™ is a trademark of Sun Microsystems, Inc. in the United States, other countries, or both. Linux® is the registered trademark of Linus Torvalds in the United States, other countries, or both. Mozilla® and Firefox® are registered trademarks of the Mozilla Foundation in the United States, other countries, or both. Other product and company names mentioned herein may be the trademarks of their respective owners. Under the copyright laws, neither this documentation nor the software may be copied, in whole or in part, without the written con- sent of Advanced Instructional Systems, except in the normal use of the software. Questions in the database that are identified with a specific textbook have been used with the permission of the publisher who owns the copyright. Order the WebAssign service from: WebAssign Centennial Campus 1730 Varsity Drive Suite 200 Raleigh, NC 27606 Web: http://webassign.net Tel: (800) 955-8275 or (919) 829-8181 Fax: (919) 829-1516 Email: [email protected] Contents i Contents 1. -

1.4 Courselab and Lms
CourseLab 2.7. User Manual 1. WHAT IS COURSELAB? ....................................................................................................................................... 5 1.1 KEY FEATURES OF COURSELAB .................................................................................................................................... 5 1.2 SYSTEM REQUIREMENTS ............................................................................................................................................ 5 1.3 COMPLIANCE TO THE STANDARDS ............................................................................................................................... 6 1.4 COURSELAB AND LMS .............................................................................................................................................. 6 2. INTERFACE ......................................................................................................................................................... 7 2.1 COURSE PANE ......................................................................................................................................................... 8 2.2 MODULE WINDOW ................................................................................................................................................... 9 2.3 TASK PANE ........................................................................................................................................................... 10 2.3.1 Frame structure ........................................................................................................................................