Techniques for Establishing Trust in Modern Constrained Sensing Platforms with Trusted Execution Environments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
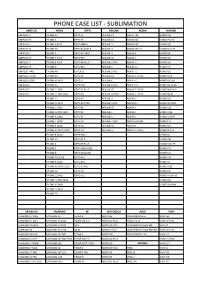
Qikink Product & Price List
PHONE CASE LIST - SUBLIMATION ONEPLUS APPLE OPPO REALME NOKIA HUAWEI ONEPLUS 3 IPHONE SE OPPO F3 REALME C1 NOKIA 730 HONOR 6X ONEPLUS 3T IPHONE 6 OPPO F5 REALME C2 NOKIA 640 HONOR 9 LITE ONEPLUS 5 IPHONE 6 PLUS OPPO FIND X REALME 3 NOKIA 540 HONOR Y9 ONEPLUS 5T IPHONE 6S OPPO REALME X REALME 3i NOKIA 7 PLUS HONOR 10 LITE ONEPLUS 6 IPHONE 7 OPPO F11 PRO REALME 5i NOKIA 8 HONOR 8C ONEPLUS 6T IPHONE 7 PLUS OPPO F15 REALME 5S NOKIA 6 HONOR 8X ONEPLUS 7 IPHONE 8 PLUS OPPO RENO 2F REALME 2 PRO NOKIA 3.1 HONOR 10 ONEPLUS 7T IPHONE X OPPO F11 REALME 3 NOKIA 2.1 HONOR 7C ONEPLUS 7PRO IPHONE XR OPPOF13 REALME 3 PRO NOKIA 7.1 HONOR 5C ONEPLUS 7T PRO IPHONE XS OPPO F1 REALME C3 NOKIA 3.1 PLUS HONOR P20 ONEPLUS NORD IPHONE XS MAX OPPO F7 REALME 6 NOKIA 5.1 HONOR 6PLUS ONEPLUS X IPHONE 11 OPPO A57 REALME 6 PRO NOKIA 7.2 HONOR PLAY 8A ONEPLUS 2 IPHONE 11 PRO OPPO F1 PLUS REALME X2 NOKIA 7.1 PLUS HONOR NOVA 3i ONEPLUS 1 IPHONE 11 PRO MAX OPPO F9 REALME X2 PRO NOKIA 6.1 PLUS HONOR PLAY IPHONE 12 OPPO A7 REALME 5 NOKIA 6.1 HONOR 8X IPHONE 12 MINI OPPO R17 PRO REALME 5 PRO NOKIA 8.1 HONOR 8X MAX IPHONE 12 PRO OPPO K1 REALME XT NOKIA 2 HONOR 20i IPHONE 12 PRO MAX OPPO F9 REALME 1 NOKIA 3 HONOR V20 IPHONE X LOGO OPPO F3 REALME X NOKIA 5 HONOR 6 PLAY IPHONE 7 LOGO OPPO A3 REALME 7 PRO NOKIA 6 (2018) HONOR 7X IPHONE 6 LOGO OPPO A5 REALME 5S NOKIA 8 HONOR 5X IPHONE XS MAX LOGO OPPO A9 REALME 5i NOKIA 2.1 PLUS HONOR 8 LITE IPHONE 8 LOGO OPPO R98 HONOR 8 IPHONE 5S OPPO F1 S HONOR 9N IPHONE 4 OPPO F3 PLUS HONOR 10 LITE IPHONE 5 OPPO A83 (2018) HONOR 7S IPHONE 8 -
Quick Start Guide Your Phone at a Glance
Quick Start Guide Your phone at a glance Thank you for choosing the Huawei smartphone. Before you start, let's take a look at your new phone. Press and hold the power button to power on your phone. To power off your phone, press and hold the power button, and touch Power off > OK. To forcibly restart your phone, press and hold the power button until your phone vibrates. Microphone Headset jack Status Front indicator camera Light Earpiece sensor Volume button Power button Home Return Menu Speaker Microphone Micro USB port Getting started Your phone's built-in battery is not user-removable. To Caution replace the battery, contact an authorized Huawei service center. Do not attempt to remove it yourself. Follow the instructions in the following figures to install your micro-SIM card, microSD card. Before you insert or remove the micro-SIM card, power off your phone. 1 5VKTZNKHGZZKX_IU\KX 2 /TYKXZZNK3OIXU9/3IGXJ 3 /TYKXZZNKSOIXU9*IGXJ5VZOUTGR 4 /TYZGRRZNKHGZZKX_IU\KX 5 )NGXMKZNKVNUTK Locking and unlocking the screen Press the power button to lock the screen. After your phone is idle for a specified period of time, its screen automatically locks. If the screen is off, press the power button to turn it on. Slide your finger in any direction to unlock the screen. Flick up from the bottom of the screen to quickly launch commonly used applications without unlocking the screen. Calling and messaging Touch to place a call using the dialer. You can also touch a phone number in a message, email, web page, or other screen to place a call. -

Brand Old Device
# New Device Old Device - Brand Old Device - Model Name 1 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE500KL 2 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE601KL 3 Galaxy A6+ Asus Asus ZenFone 2 ZE550ML 4 Galaxy A6+ Asus Asus Zenfone 2 ZE551ML 5 Galaxy A6+ Asus Asus Zenfone 3 Laser 6 Galaxy A6+ Asus Asus Zenfone 3 Max ZC520TL 7 Galaxy A6+ Asus Asus Zenfone 3 Max ZC553KL 8 Galaxy A6+ Asus Asus Zenfone 3 ZE520KL 9 Galaxy A6+ Asus Asus Zenfone 3 ZE552KL 10 Galaxy A6+ Asus Asus Zenfone 3s Max 11 Galaxy A6+ Asus Asus Zenfone Max 12 Galaxy A6+ Asus Asus Zenfone Selfie 13 Galaxy A6+ Asus Asus ZenFone Zoom ZX550 14 Galaxy A6+ Gionee Gionee A1 15 Galaxy A6+ Gionee Gionee A1 Lite 16 Galaxy A6+ Gionee Gionee A1 Plus 17 Galaxy A6+ Gionee Gionee Elife E8 18 Galaxy A6+ Gionee Gionee Elife S Plus 19 Galaxy A6+ Gionee Gionee Elife S7 20 Galaxy A6+ Gionee Gionee F103 21 Galaxy A6+ Gionee Gionee F103 Pro 22 Galaxy A6+ Gionee Gionee Marathon M4 23 Galaxy A6+ Gionee Gionee Marathon M5 24 Galaxy A6+ Gionee Gionee marathon M5 Lite 25 Galaxy A6+ Gionee Gionee Marathon M5 Plus 26 Galaxy A6+ Gionee Gionee P5L 27 Galaxy A6+ Gionee Gionee P7 Max 28 Galaxy A6+ Gionee Gionee S6 29 Galaxy A6+ Gionee Gionee S6 Pro 30 Galaxy A6+ Gionee Gionee S6s 31 Galaxy A6+ Gionee Gionee X1s 32 Galaxy A6+ Google Google Pixel 33 Galaxy A6+ Google Google Pixel XL LTE 34 Galaxy A6+ Google Nexus 5X 35 Galaxy A6+ Google Nexus 6 36 Galaxy A6+ Google Nexus 6P 37 Galaxy A6+ HTC Htc 10 38 Galaxy A6+ HTC Htc Desire 10 Pro 39 Galaxy A6+ HTC Htc Desire 628 40 Galaxy A6+ HTC HTC Desire 630 41 Galaxy A6+ -

Mobile- H2 2018
Barometer of mobile Internet connections in Turkey Publication of August 12 th , 2019 H2 2018 – H1 2019 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Summary of results ...................................................................................................................... 2 1.1 Summary table and nPerf score, all technologies combined .............................................. 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results 2G/3G/4G ............................................................................................................. 3 2.1 Data amount and distribution ............................................................................................... 3 2.2 Success rate 2G/3G/4G ........................................................................................................ 4 2.3 Download speed 2G/3G/4G .................................................................................................. 4 2.4 Upload speed 2G/3G/4G ....................................................................................................... 6 2.5 Latency 2G/3G/4G ................................................................................................................ 7 2.6 Browsing test 2G/3G/4G....................................................................................................... 8 2.7 Streaming test 2G/3G/4G .................................................................................................... -

ETUI W Kolorze Czarnym ALCATEL A3
ETUI w kolorze czarnym ALCATEL A3 5.0'' CZARNY ALCATEL PIXI 4 4.0'' 4034A CZARNY ALCATEL PIXI 4 5.0'' 5045X CZARNY ALCATEL POP C3 4033A CZARNY ALCATEL POP C5 5036A CZARNY ALCATEL POP C7 7041X CZARNY ALCATEL POP C9 7047D CZARNY ALCATEL U5 5044D 5044Y CZARNY HTC 10 CZARNY HTC DESIRE 310 CZARNY HTC DESIRE 500 CZARNY HTC DESIRE 516 CZARNY HTC DESIRE 610 CZARNY HTC DESIRE 616 CZARNY HTC DESIRE 626 CZARNY HTC DESIRE 650 CZARNY HTC DESIRE 816 CZARNY HTC ONE A9 CZARNY HTC ONE A9s CZARNY HTC ONE M9 CZARNY HTC U11 CZARNY HUAWEI ASCEND G510 CZARNY HUAWEI ASCEND Y530 CZARNY HUAWEI ASCEND Y600 CZARNY HUAWEI G8 GX8 CZARNY HUAWEI HONOR 4C CZARNY HUAWEI HONOR 6X CZARNY HUAWEI HONOR 7 LITE 5C CZARNY HUAWEI HONOR 8 CZARNY HUAWEI HONOR 9 CZARNY HUAWEI MATE 10 CZARNY HUAWEI MATE 10 LITE CZARNY HUAWEI MATE 10 PRO CZARNY HUAWEI MATE S CZARNY HUAWEI P10 CZARNY HUAWEI P10 LITE CZARNY HUAWEI P10 PLUS CZARNY HUAWEI P8 CZARNY HUAWEI P8 LITE 2017 CZARNY HUAWEI P8 LITE CZARNY HUAWEI P9 CZARNY HUAWEI P9 LITE CZARNY HUAWEI P9 LITE MINI CZARNY HUAWEI Y3 2017 CZARNY HUAWEI Y3 II CZARNY HUAWEI Y5 2017 Y6 2017 CZARNY HUAWEI Y5 Y560 CZARNY HUAWEI Y520 Y540 CZARNY HUAWEI Y541 CZARNY HUAWEI Y6 II CZARNY HUAWEI Y625 CZARNY HUAWEI Y7 CZARNY iPHONE 5C CZARNY iPHONE 5G CZARNY iPHONE 6 4.7'' CZARNY iPHONE 7 4.7'' 8 4.7'' CZARNY iPHONE 7 PLUS 5.5'' 8 PLUS CZARNY iPHONE X A1865 A1901 CZARNY LENOVO K6 NOTE CZARNY LENOVO MOTO C CZARNY LENOVO MOTO C PLUS CZARNY LENOVO MOTO E4 CZARNY LENOVO MOTO E4 PLUS CZARNY LENOVO MOTO G4 XT1622 CZARNY LENOVO VIBE C2 CZARNY LENOVO VIBE K5 CZARNY -

Boldbeast Call Recorder 9.1 Pro Apk
Boldbeast call recorder 9.1 pro apk Continue Call Recorder - Boldbeast Size: 2.95 MB Version: 9.1 File Type: APK System: Android 2.3 or above Description : Two reasons you need this app - you need a real business level call registrar, secure, clean, stable. You need high-quality records. Call recording features - Boldbeast apps: - Recording a phone call. Recording voice memos, meetings, lectures, etc. - Record management - search, playback, browsing, deletion, sending, backup, etc. Features Call Recorder - Boldbeast Mod : - All unlocked Installation Instructions: - Have you visited this site on your mobile phone? 1. Download the Apk file on your mobile phone. 2. Set and run it. 3. That's it, Enjoy! Have you visited this site on your desktop or laptop? 1. Download the Apk file on Pc. 2. Transfer the Apk file from PC to Android Phone (Via USB, Bluetooth, Wi-Fi). 3. Install and run it. 4. That's it, Enjoy! We provide call recorder (No Advertising) 13.7 APKs file for Android 4.1 and up. Call Recorder (No Advertising) is a free Tools app. It's easy to download and install on your cell phone. Please note that ApkPlz only share the original and free clean APK installer for Call Recorder (No Advertising) 13.7 APKs without any changes. The average score is 3.10 out of 5 stars in the playstore. If you want to know more about Call Recorder (No Advertising), you can visit the Boldbeast Software Support Center for more information All apps and games here only for home or personal use. If any download apk infringes your copyright, please contact us. -

Spardasecureapp-Geraeteliste.Pdf
SpardaSecureApp Übersicht der Smartphones Offiziell vom Hersteller unterstützte Geräte Mindestanforderung der Android-Version Asus Google Nexus 7 2013 6.0.1 6.0.1 Asus Google Nexus 7 6.0 6.0 Asus Google Nexus 7 ME370T 5.0.2 5.0.2 Asus Google Nexus 7 ME370T 5.1.1 5.1.1 Google Pixel 2 -US 8.1.0 Google Pixel 2 Android 10 -US 10 Google Pixel 2 8.1.0 Google Pixel 3 -US 9 Google Pixel 3 XL -US 9 Google Pixel 3a -US 9 Google Pixel 3a Android 10 -US 10 Google Pixel 3a XL -US 9 Google Pixel 3a XL Android 10 -US 10 Google Pixel 9.0 -US 9 Google Pixel Pie -US 9 Google Pixel XL 8.1.0 8.1.0 HTC Desire 610 4.4.2 HTC Desire 816 (HTC 710C) 5.0.2 HTC Droid DNA 4.4.2 HTC One E8 5.0.2 HTC One M8 6.0 HTC One M9 7.0 HTC U12+ 8.0.0 Honor 7 Lite 6.0 Huawei Ascend Mate 7 6.0 Huawei Ascend P8 Lite 5.0.2 Huawei Ascend P8 5.0.1 Huawei Google Nexus 6P 7.0 7.0 Huawei Google Nexus 6P 8.0 8.0.0 Huawei Honor 4A 5.1.1 Huawei Honor 4C Play 4.4.4 Huawei Honor 4X Play Che2-TL00 4.4.2 Huawei Honor 5X 6.0.1 Huawei Honor 6 H60-L01 4.4.2 Huawei Honor 6 H60-L04 4.4.2 Huawei Honor 6 Plus 4.4.2 Huawei Honor 7 PLK-L01 5.0 Huawei Honor 7i 6.0.1 Stand 16.04.2020 | SecureApp-Version 3.0.2 (SDK 2.7.3245) Offiziell vom Hersteller unterstützte Geräte Mindestanforderung der Android-Version Huawei P Smart 9 Huawei P10 9 Huawei P9 6.0 LG G2 Mini D620 5.0.2 LG G3 D855 5.0 LG G4c 5.0.2 LG G5 H830 8.0.0 LG Google Nexus 4 E960 5.1.1 LG Google Nexus 5 5.1 -US 5.1 LG Google Nexus 5 5.1 5.1 LG Google Nexus 5 6.0 6.0 LG Google Nexus 5 6.0.1 -US 6.0.1 LG Google Nexus 5 6.0.1 6.0.1 LG Google Nexus -

Supported Huawei Models & Features
HDE DONGLE LIST MODELS 1/4/2019 Read Read Unlock Vendor FRP / Direct Unlock Custom Model Modif. CPU Year unlock bootloader custom. IMEI MEID BT MAC SN and Huawei unlock fastboot SN codes code limit. country ID Ascend Qualcomm Ascend G620-A2 2015 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM8926 SnapTo HiSilicon Ascend D2 D2-0082 2013 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - K3V2 Hi3620 HiSilicon Ascend D2 D2-2010 2013 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - K3V2 Hi3620 HiSilicon Ascend D2 D2-5000 2013 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - K3V2 Hi3620 HiSilicon Ascend D2 D2-6114 2013 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - K3V2 Hi3620 Qualcomm Ascend G300 U8815-51 2012 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM7227A Qualcomm Ascend G300 U8815-71 2012 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM7227A Ascend Qualcomm C8810 Yes Yes Yes - - - Yes Yes Yes Yes - Yes - G300C MSM7627T Qualcomm Ascend G330 U8825 2012 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM8225 Ascend Qualcomm U8825D 2012 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - G330D MSM8225 Qualcomm Ascend G510 G510-0010 2011 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM8225 Qualcomm Ascend G510 G510-0100 2011 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM8225 Qualcomm Ascend G510 G510-0200 2011 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM8225 Qualcomm Ascend G510 G510-0251 2011 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM8225 Qualcomm Ascend G525 G525-U00 2013 Yes Yes Yes - - Yes - Yes Yes Yes - Yes - MSM8225Q Qualcomm Ascend G526 G526-L11 2013 Yes Yes Yes - - Yes - Yes Yes -

Huawei's Mobile Processors
Huawei's mobile processors Dezső Sima Vers. 2.1 November 2018 Sima Dezső, 2018 Huawei's mobile processors • 1. Overview • 2. Examples: The Kirin 950 • 2.1 The Kirin 950 • 2.2 The Kirin 960 • 2.3 The Kirin 970 • 2.4 The Kirin 980 • 3. References 1. Overview 1. Overview (1) Huawei [1] • Huawei Technologies Co. Ltd. is a Chinese multinational networking and telecommunications equipment and services company headquartered in Shenzhen China. • It was founded in 1987 and became the world's largest telecom equipment manufacturer. • The name Huawei (华为) means Chinese achievement. • Recently it has about 180 000 employees. Figure: Huawei's logo [1] Figure: Huawei's headquarter in Shenzen [1] 1. Overview (2) HiSilicon [2] • HiSilicon, a global fabless semiconductor and IC design company, headquartered in Shenzhen, China. • It was founded in 2004 as a subsidiary of Huawei. • It has offices and research centers worldwide, the number of the employees is about 7000. • HiSilicon purchases licenses mainly from ARM and designs in the first line application processors for mobiles. It filed over 5,000 patents. 1. Overview (3) 1. Overview Worldwide smartphone shipments by vendors Q4/2009 to Q4/2016 (million units) [3] 1. Overview (4) Worldwide market share of application processors in 2015 used in smartphones (based on revenue) [4] Market Processor lines Vendor Cores ISA share (examples) Qualcomm Snapdragon Qualcomm designed Krait cores ARMv7 42 % (USA) 200-800 ARM Cortex A line ARMv7/v8 Apple Apple A7-A9 Apple designed Cyclone core 21 % ARMv8 (USA) Apple A10 2xbig./4x LITTLE cores 8xARM Cortex A53 ARMv7 MediaTek Helio x10 (ARM big.LITTLE) 19 % (Taiwan) Helio X20 2xARM Cortex A72/8x A53 ARMv8 (ARM big.LITTLE) Samsung Exynos ARM Cortex A line ARMv7 (S. -

177781 Outdoorové Pouzdro/Puzdro Playa, Velikost/Veľkosť XXL, Černé/Čierne 177782 Outdoorové Pouzdro/Puzdro Playa, Velikost/Veľkosť XXL, Růžové/Ružové
177781 outdoorové pouzdro/puzdro Playa, velikost/veľkosť XXL, černé/čierne 177782 outdoorové pouzdro/puzdro Playa, velikost/veľkosť XXL, růžové/ružové KOMPATIBILITA Acer Liquid Z630 Alcatel One Touch Pop C9; One Touch Go Play; One Touch Hero 2; Idol 4s; Idol 4; Pop 4; Pop 4+; 3L Apple iPhone 6 Plus; 6s Plus; 7; X; 8 Plus; Xs; XR; Xs Max; 11 Pro; 11; 11 Pro Max; Archos 50c Oxygen; 50c Helium 4G; 50c Neon; 55 Helium+; 50c Plantium; Diamond Plus; 50 Cesium; 50 Cobalt; 55 Cobalt Plus; 50 Power; Asus ZenFone 6; Zenfone 2 Deluxe; Zenfone Selfie; Zenfone Zoom Blackberry Passport; Passport Silver Edition; Priv; Key2 Bq Aquaris E6; Aquaris M5.5; Aquaris C CAT S30; S41; S60; S31; S61 Coolpad Modena Gigaset ME Google Nexus 6; Nexus 6P; Nexus 5X; Pixel; Pixel 2; Pixel 2 XL; Pixel 3; Pixel 3 XL; Pixel 3A; Pixel 3A XL Haier W867; Voyage V3 Hisense HS-U980; HS-U970; G610M Honor 4X; 6 Plus; 4c; 5x; 5c; 6x; 6c; 9; 6A; 6C Pro; 7X; View 10; 9 Lite; 7A; 10; 7s; Play; 8x; 10 Lite; View 20 HTC One (M8/M8s); Desire 816; Desire 610; Desire 510; Desire 820; One (E8); Desire 620/620G; One (M9); One (M9+); Desire 728G; Desire 530; One S9; Desire 628 Dual SIM; U12+; U12 Life Huawei Y7 (2019); Ascend G630; Ascend G730; Ascend G750; Ascend Mate 7; Ascend G7; Y600; Mate S (Carrera); G8 (Rio); ShotX; Mate 8; GX8; P9 Lite; P9 Plus; Y5 II; Nova; Mate 9; Nova Plus; P8 Lite (2017); P10 Lite; Y6 (2017); Nova 2; Y6 Pro (2017); Mate 10 Lite; P Smart; P20 Pro; P20; P20 lite; Y7 (2018); Y5 (2018); Y9 (2018); Nova 3; P Smart+; Mate 20 Lite; Mate 20 Pro; Mate 20; P Smart (2019); -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.3 | September 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 20,489 DEVICE PROFILES +2,256 APP VERSIONS UFED TOUCH2, UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.3 | September 2016 UFED LOGICAL ANALYZER HIGHLIGHTS NOW SUPPORTING iPHONE 7 AND iPHONE 7 PLUS DEVICES! DEVICE SUPPORT The new iPhone devices can now be extracted by Advanced Physical extraction and decoding of rooted and unencrypted Logical, Logical and File System extraction methods. Samsung Galaxy S7 and Note 7 devices. NOW SUPPORTING ANDROID V7.0 NOUGAT! Limitations apply. See below.* FORENSIC DEVICE PROFILES v.5.3 Total Logical extraction 122 8,785 Physical extraction* 56 4,584 CELLEBRITE SUPPORTS iOS 10! File system extraction 128 4,699 File system, Advanced Logical and Logical extractions and Extract/disable user lock 18 2,421 decoding from Apple devices running iOS 10 (limited to unencrypted iTunes backup). Total 324 20,489 The number of unique mobile devices with passcode capabilities is 3,844 *Including GPS devices SUPPORTED METHODS IN CELLEBRITE’S PHONE LISTS PHYSICAL EXTRACTION AND DECODING OF ROOTED AND The list of supported devices and capabilities now also includes UNENCRYPTED SAMSUNG GALAXY S7 AND NOTE 7 DEVICES available methods for Physical and File System Extractions. This Samsung GSM SM-G930FD Galaxy S7 Dous, SM-N930A Galaxy info visibility is the reflection of UFED available methods and Note 7, SM-N930T Galaxy Note 7, SM-G9300 can be very beneficial when looking for new devices and new Galaxy S7, SM-G9308 Galaxy S7 Duos, SM-G9350 Galaxy S7 Edge supported capabilities. PHYSICAL -

Discoveries of MBB Trends
Discoveries of MBB Trends —2015 Eight Major Findings from the Perspectives of User Experience, Terminals, and Mobile Services HUAWEI.COM Overview his is an age for rapid development of mobile broadband (MBB). Subscribers nowadays are quite used to access all sorts of information on their mobile phones. MBB has never been so close to Tpeople. After summarizing the 2015 mobile service experience, mobile terminal development trend, and future mobile services, Huawei has the following eight key findings. • Mobile service experience: It is expected that 70% of mobile data comes from video traffic in 2020. Subscribers will get more used to watching videos on their mobile phones anytime anywhere. Meanwhile, the Voice over LTE (VoLTE) service will bring new audio-visual experience to 4G subscribers. • Terminals: In 2015, more than 70% of mobile phones are equipped with a display supporting the entry-level retina PPI (in normal cases). With the increased battery capacity, the battery life of mobile phones is not prolonged accordingly. Battery life extension can be achieved through optimization of mobile applications. • Future services: To support retina-level virtual reality (VR) anytime anywhere, the data rate must reach the Gbps level. With development of Internet of Things (IoT), more things will consume data traffic automatically to meet the specific scenario requirement of people. Discoveries of MBB Trends 02 Key Finding Mobile Video Everywhere ccording to the analysis on global data traffic of mobile applications, traffic from MBB developed countries, such as Japan and Korea, accounts for more than 50% of total traffic. In emerging markets, Amobile video traffic proportion increases rapidly.