Hidden Whois and Infringing Domain Names: Making the Case for Registrar Liability Ian J
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Privacy Policy V1.1
CENTRALNIC LTD REGISTRY PRIVACY POLICY Version 1.1 September 2018 CentralNic Ltd 35-39 Moorgate London EC2R 6AR Table of Contents TABLE OF CONTENTS ......................................................................................................................... 2 AMENDMENT ISSUE SHEET ................................................................................................................. 3 INTRODUCTION ................................................................................................................................ 4 DATA PROTECTION RIGHTS ................................................................................................................. 5 RELATIONSHIP WITH REGISTRARS ......................................................................................................... 6 WHAT INFORMATION CENTRALNIC COLLECTS .......................................................................................... 6 INFORMATION CENTRALNIC DOES NOT COLLECT ....................................................................................... 8 HOW INFORMATION IS STORED ............................................................................................................ 8 HOW WE USE INFORMATION ............................................................................................................... 8 HOW INFORMATION IS PROTECTED ..................................................................................................... 13 HOW INFORMATION IS DELETED ........................................................................................................ -

Web Portal User Manual For
Web Portal User Manual for ©Copyright 2009 Afilias Limited Afilias Managed DNS – Web Portal User Manual Contents 1. Introduction ................................................................................................................ 1 1.1 About Afilias Managed DNS Service ........................................................................ 1 1.2 Afilias Managed DNS Service Website Help ............................................................. 1 1.3 Support .................................................................................................................. 2 2. DNS Portal Login Screen ............................................................................................... 4 3. MyAccount Screen ....................................................................................................... 5 3.1 Users & Groups ...................................................................................................... 5 3.1.1 User Details Tab ...................................................................................................... 6 3.1.2 User Password Tab .................................................................................................. 7 3.1.3 Users Tab ................................................................................................................. 8 3.1.4 Groups Tab .............................................................................................................. 9 3.2 Add User ............................................................................................................... -

ICANN Registry Request Service
ICANN Registry Request Service Ticket ID: X8T8C-0S4B2 Registry Name: Public Interest Registry gTLD: .org Status: ICANN Review Status Date: 2013-06-04 22:05:48 Print Date: 2013-06-04 22:06:10 Proposed Service Name of Proposed Service: Technical description of Proposed Service: Technical Description of Proposed Service: Background: BTAPPA will be beneficial in situations where one ICANN-accredited registrar purchases (the "Gaining Registrar"), by means of a stock or asset purchase, merger or similar transaction, a portion, but not all, of another ICANN accredited registrar's domain name portfolio ("Losing Registrar") in the .ORG top-level domains ("TLDs") or where a Gaining Registrar receives a request from a registrant to transfer a significant number of its domain names from a Losing Registrar to such Gaining Registrar. Unless an entire portfolio of domain names is being transferred, Gaining Registrars must request that each domain name be transferred individually. Gaining Registrars must meet the following requirements: oGaining Registrar must be ICANN accredited for the .ORG TLD. oGaining Registrar must be in good standing and be under a Registry-Registrar Agreement with PIR. oGaining Registrar must provide PIR with evidence (i.e., affidavit, sale documents) that sets forth the transfer date or, if an acquisition, the target closing date. oIf domain names are to be transferred from multiple Losing Registrars, then they must be Registrar Affiliates. A Registrar Affiliate is a registrar entity that controls, is controlled by or is under common control with, another the Losing Registrar. oTransfers of domain names to multiple Gaining Registrars will not be permitted, regardless of familiar relationship. -

Afilias Limited Request 28 January 2020
Registry Services Evaluation Policy (RSEP) Request January 17, 2020 Registry Operator Afilias Limited Request Details Case Number: 00941695 This Registry Services Evaluation Policy (RSEP) request form should be submitted for review by ICANN org when a registry operator is adding, modifying, or removing a Registry Service for a TLD or group of TLDs. The RSEP Process webpage provides additional information about the process and lists RSEP requests that have been reviewed and/or approved by ICANN org. If you are proposing a service that was previously approved, we encourage you to respond similarly to the most recently approved request(s) to facilitate ICANN org’s review. Certain known Registry Services are identified in the Naming Services portal (NSp) case type list under “RSEP Fast Track” (example: “RSEP Fast Track – BTAPPA”). If you would like to submit a request for one of these services, please exit this case and select the specific Fast Track case type. Unless the service is identified under RSEP Fast Track, all other RSEP requests should be submitted through this form. Helpful Tips • Click the “Save” button to save your work. This will allow you to return to the request at a later time and will not submit the request. • You may print or save your request as a PDF by clicking the printer icon in the upper right corner. You must click “Save” at least once in order to print the request. • Click the “Submit” button to submit your completed request to ICANN org. • Complete the information requested below. All fields marked with an asterisk (*) are required. -

Brief of Internet Commerce Association
No. 19-46 IN THE Supreme Court of the United States U.S. PATENT AND TRADEMARK OFFICE, ET AL., Petitioners, v. BOOKING.COM B.V., Respondent. ON WRIT OF CERTIORARI TO THE UNITED STATES COURT OF APPEALS FOR THE FOURTH CIRCUIT BRIEF OF THE INTERNET COMMERCE ASSOCIATION AS AMICUS CURIAE IN SUPPORT OF RESPONDENT Megan L. Brown Counsel of Record David E. Weslow Ari S. Meltzer Jeremy J. Broggi WILEY REIN LLP 1776 K Street NW Washington, DC 20006 (202) 719-7000 [email protected] February 19, 2020 Counsel for Amicus Curiae - i - TABLE OF CONTENTS Page TABLE OF CITED AUTHORITIES .......................... ii INTEREST OF AMICUS CURIAE ............................1 SUMMARY OF ARGUMENT .....................................3 ARGUMENT ...............................................................7 I. The Government Seeks A Bright-Line Rule That Would Devalue Registered Domain Names As A Class Of Intellectual Property Assets. ...............................................................7 II. The Government’s Rule Would Discourage Investment In The Internet Economy By Precluding Trademark Protection For New Types of Domain Names. ............................... 13 III. The Government’s Rule Would Eliminate A Critical Consumer Protection And Anti-Fraud Tool, Opening The Door To More Domain Name Abuse. ................................................... 15 A. Cybercriminals Abuse Domain Names Through Typosquatting And Domain Name Hijacking To Perpetrate Fraud And Proliferate Malware. .................... 16 B. Companies Rely On Trademark Protection To Combat Domain Name Abuse. ................................................... 20 C. Non-Trademark Remedies Do Not Provide A Sufficient Means For Combatting Domain Name Abuse. ..... 26 CONCLUSION .......................................................... 28 - ii - TABLE OF CITED AUTHORITIES Page(s) Cases Central Source LLC v. annaulcreditreports.com, No. 20-CV-84 (E.D. Va.) ....................................... 23 Central Source LLC v. aabbualcreditreport.com, No. 14-CV-918 (E.D. -

Sullivan-Nevett-Brooks to Marby Et Al. 22Jan20
January 22, 2020 Göran Marby Chief Executive Officer Maarten Botterman Chair of the Board of Directors Members of the Board of Directors John Jeffrey General Counsel Internet Corporation for Assigned Names and Numbers 12025 East Waterfront Drive Suite 300 Los Angeles, CA 90094-2536 Dear ICANN Leadership: On January 16, 2020, several members of Congress wrote to you regarding the agreement reached among the Internet Society, Public Interest Registry (PIR) and Ethos Capital with respect to the .ORG top-level domain. A number of important issues were raised in the letter that we would like to address, just as we welcomed the opportunity to address questions posed in a letter dated December 23, 2019, to which we replied on January 6, 2020 (attached). As we stated in our response, this transaction serves the public interest in several important ways. First, it will ensure the long-term growth and development of the .ORG domain by enabling PIR to expand its work and the services it provides to the nonprofit community and other .ORG users in innovative and socially responsible ways. Second, it will provide essential support for the ongoing work of the Internet Society by providing a substantial endowment that will ensure its ability to continue its efforts to build a more accessible, inclusive and secure Internet around the world. In addition, Ethos has announced it will maintain the same technology, and will keep PIR’s management team in place, so that .ORG will remain secure, reliable and stable. And the Internet Society, Ethos and PIR have taken the unprecedented step of publishing PIR’s notice of change of control to ICANN, as well as the answers to ICANN’s questions, in what has been the most transparent process of a change of indirect control in ICANN’s history. -

Search the Whois Database
Search the whois database. Is this really GoDaddy.com? BobParsons.com See the internet version of our Verify the site for your protection! new "Window Washer" ad here! Did we go too far -- again? Domains Hosting & Servers Site Builders Email SSL Certificates Business Domain Auctions Reseller Plans Logout My Account Company Info Why our prices are so low Our Values What's New! FAQ Commercials RSS Feeds Search again Enter a domain name: PFLP-ELECTIONS.NET Whois Server Version 1.3 More About Domains Domain names in the .com and .net domains can now be registered ● Compare our prices with many different competing registrars. Go to http://www.internic.net for detailed information. ● Why our prices are so low ● Transfer your domain to GoDaddy.com for just $6.95! Includes a 1-year Domain Name: PFLP-ELECTIONS.NET extension. Registrar: TUCOWS INC. ● Find out what this domain is worth Whois Server: whois.opensrs.net Referral URL: http://domainhelp.tucows.com Name Server: NS3.LNHI.NET Name Server: NS2.LNHI.NET Name Server: NS1.LNHI.NET Available TLDs Status: REGISTRAR-LOCK Updated Date: 29-dec-2005 PFLP-ELECTIONS.COM $8.95 SAVE! Creation Date: 29-dec-2005 Expiration Date: 29-dec-2006 PFLP-ELECTIONS.ORG $7.95 SAVE! PFLP-ELECTIONS.INFO $5.95 SAVE! >>> Last update of whois database: Wed, 11 Jan 2006 02:39:40 EST <<< $7.95 SAVE! NOTICE: The expiration date displayed in this record is the date the PFLP-ELECTIONS.BIZ registrar's sponsorship of the domain name registration in the registry is $7.95 SAVE! currently set to expire. -

Investor Presentation
Investor presentation 05.06.2021 Nasdaq (TCX) | TSX (TC) 1 Safe Harbor Statement This presentation may contain forward-looking statements, relating to the Company’s operations or to the environment in which it operates, which are based on Tucows Inc.’s operations, estimates, forecasts and projections. These statements are not guarantees of future performance and are subject to important risks, uncertainties and assumptions concerning future conditions that may ultimately prove to be inaccurate or differ materially from actual future events or results. A number of important factors could cause actual outcomes and results to differ materially from those expressed in these forward-looking statements. Consequently, investors should not place undue reliance on these forward-looking statements, which are based on Tucows Inc.’s current expectations, estimates, projections, beliefs and assumptions. These forward-looking statements speak only as of the date of this presentation and are based upon the information available to Tucows Inc. at this time. Tucows Inc. disclaims any intention or obligation to update or revise any forward-looking statements, whether as a result of new information, future events or otherwise. 2 Table of Contents 01 02 03 Our business Domain services Mobile Services Page 4 Page 11 Page 16 04 05 Resources06 Fiber Internet Services Quarterly Financial Highlights Page 18 Page 23 Page 26 3 Our business Consistent, reliable cash flow generation + growth 4 Our business Investment Summary Consistent and reliable revenue and Visible -

Department of Homeland Security, Directive 139-01 Domain Names
Department of Homeland Security DHS Directives System MD Number: 139-01 Revision Number: 00 Issue Date: 07/31/2007 DOMAIN NAMES I. Purpose This directive establishes Department of Homeland Security (DHS) policy regarding the approval and acquisition of Domain Names Services (DNS) for web sites owned or operated by, or on behalf of, DHS and its organizational elements. II. Scope This directive applies to all DHS organizational elements. III. Authorities A. This directive is governed by Public Laws, regulations, and other directives, such as: 1. Department Of Homeland Security Management Directives: MD 4400.1 – "DHS WEB (INTERNET, INTRANET, AND EXTRANET INFORMATION) AND INFORMATION SYSTEMS." 2. Request for Comments (RFC) 2146 titled "U.S. Government Internet Domain Names." a. In May 1997, the General Services Administration (GSA) issued RFC 2146, which described the registration policies for the top-level domain ".GOV". The purpose of RFC 2146 was to establish a single identifiable Internet name for each U.S. Federal government agency. b. RFC 2146 restricts Domain Name registration to coincide with the approved structure of the U.S. Government, as listed in the document "Codes for the Identification of Federal and Federally Assisted Organizations," Federal Information Processing Standards (FIPS) 95-1 (or its successor). RFC 2146 provides for waivers to this restriction to be granted based upon the advice of the agency Chief Information Officer. 3. For more information on the .GOV naming convention visit: <http://www.dotgov.gov/dnc.aspx>. - 1 - MD # 139-01 Revision # 00 B. References: 1. RFC 1480 - The U.S. Domain: <http://www.dotgov.gov/help_rfc1480.aspx>. -

Beginner's Guide to Domain Names
Beginner’s Guide to D O M A I N N A M E S THIS IS ONE OF A SERIES OF GUIDES ABOUT ISSUES OF IMPORTANCE TO INTERNET USERS. EDUCATING NEW USERS ABOUT INTERNET ISSUES IS PART OF ICANN’S MISSION TO ENSURE A STABLE, SECURE, GLOBALLY INTEROPERABLE INTERNET. ICANN PREPARED THIS GUIDE AT THE REQUEST OF THE AT-LARGE ADVISORY COMMITTEE, THE VOICE OF THE INDIVIDUAL INTERNET USER AT ICANN. WE SINCERELY HOPE YOU FIND IT HELPFUL. TA b l E O f C ontents Introduction.................................................................................................................................................................................................................................2 Domain Names...........................................................................................................................................................................................................................3 1 What.is.a.domain.name.and.how.does.it.work?...........................................................................................................................................3 2 ...How.do.I.register.a.domain.name?.......................................................................................................................................................................3 . 3 ...How.do.I.select.a.domain.name.to.register?..................................................................................................................................................4 4 What.is.a.registrar.and.how.do.I.select.one?...................................................................................................................................................5 -
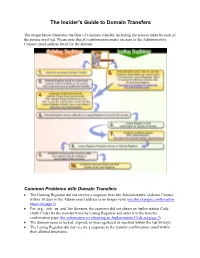
The Insider's Guide to Domain Transfers
The Insider’s Guide to Domain Transfers The image below illustrates the flow of a domain transfer, including the actions taken by each of the parties involved. Please note that all confirmation emails are sent to the Administrative Contact email address listed for the domain. Common Problems with Domain Transfers • The Gaining Registrar did not receive a response from the Administrative (Admin) Contact within 30 days or the Admin email address is no longer valid (see the example confirmation email on page 3). • For .org, .info, .us, and .biz domains, the customer did not obtain an Authorization Code (Auth Code) for the transfer from the Losing Registrar and enter it in the transfer confirmation page (for information on obtaining an Authorization Code see page 2). • The domain name is locked, expired, or was registered or renewed within the last 60 days. • The Losing Registrar did not receive a response to the transfer confirmation email within their allotted timeframe. 2 Registrar Contact Information The table below lists the contact information for the most common Registrars and describes how to obtain a transfer Authorization Code from each for .org, .info, .us, and .biz domain names. Registrar To obtain an Auth Code (.org, .info, .us, .biz) Contact Info Transfer Approval Network Call 24 hour support and request Auth Code and (888) 642-9675 24/7 Confirmation Email sent to Solutions they will send to ‘Admin’ contact on domain. the primary contact on record to approve transfer. Register.com Within Account Management click on a Domain (800) 899-0724 24/7 Link within the email Name to view its details. -

("Agreement"), Is Between Tucows Domains Inc
MASTER DOMAIN REGISTRATION AGREEMENT THIS REGISTRATION AGREEMENT ("Agreement"), is between Tucows Domains Inc. ("Tucows") and you, on behalf of yourself or the entity you represent ("Registrant"), as offered through the Reseller participating in Tucows' distribution channel for domain name registrations. Any reference to "Registry" or "Registry Operator" shall refer to the registry administrator of the applicable top-level domain ("TLD"). This Agreement explains Tucows' obligations to Registrant, and Registrant's obligations to Tucows, for the domain registration services. By agreeing to the terms and conditions set forth in this Agreement, Registrant agrees to be bound by the rules and regulations set forth in this Agreement, and by a registry for that particular TLD. DOMAIN NAME REGISTRATION. Domain name registrations are for a limited term, which ends on the expiration date communicated to the Registrant. A domain name submitted through Tucows will be deemed active when the relevant registry accepts the Registrant's application and activates Registrant's domain name registration or renewal. Tucows cannot guarantee that Registrant will obtain a desired domain name, even if an inquiry indicates that a domain name is available at the time of application. Tucows is not responsible for any inaccuracies or errors in the domain name registration or renewal process. FEES. Registrant agrees to pay Reseller the applicable service fees prior to the registration or renewal of a domain. All fees payable here under are non-refundable even if Registrant's domain name registration is suspended, cancelled or transferred prior to the end of your current registration term. TERM. This Agreement will remain in effect during the term of the domain name registration as selected, recorded and paid for at the time of registration or renewal.