Optimizing Windows 10 Update Adoption
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The NT Insider May-June 2016
; The commandments of x64 assembly: ; ; 1. Thou Shalt Not Write Inline Assembly ; 2. Thou Shalt Generate Unwind Data ; 3. Thou Shalt Comment Each Line of Assembly ; include macamd64.inc ; ; External C function to read an article ; ; NTSTATUS ; TheNTInsiderReadSingleArticle( ; PCHAR ArticleDescription, ; ULONG_PTR PageNumber, ; ); ; EXTERN TheNTInsiderReadSingleArticle:PROC .DATA PeterPontificates BYTE "COMPUTER SCIENCE EDUCATION? (YUP, STILL SUCKS)", 0 NewWaysToConnect BYTE "INTRODUCTION TO SIMPLE PERIPHERAL BUS DEVICES AND DRIVERS", 0 TipsForUsingIoTargets BYTE "A FEW RULES TO MAKE YOUR USE OF I/O TARGETS SIMPLE", 0 TodayInDriverSigning BYTE "COLOR ME CONFUSED (STILL. AGAIN.)", 0 AnalystsPerspective BYTE "MY DRIVER PASSES DRIVER VERIFIER! (OR DOES IT…)", 0 ByeByeCoInstallers BYTE "SURPRISE? NEW VERSIONS OF WDF NO LONGER SUPPORTED DOWNLEVEL", 0 .CODE NESTED_ENTRY TheNTInsiderReadEntireIssue, _TEXT save_reg rcx, 8h ; Home RCX save_reg rdx, 10h ; Home RDX save_reg r8, 18h ; Home R8 save_reg r9, 20h ; Home R9 alloc_stack 20h ; Make home space for TheNTInsiderReadSingleArticle END_PROLOGUE ; We are done manipulating the stack, so emit the ; appropriate unwind stuff lea rcx, [PeterPontificates] ; We're about to read the first article mov rdx, 4 ; Put page number in RDX. I realize this comment ; isn't useful, but I'm supposed to comment every ; line... call TheNTInsiderReadSingleArticle ; Read the article! test eax, eax ; Returns an NTSTATUS, so check SF js Exit ; If it's set there's an error and we need to leave lea rcx, [NewWaysToConnect] ; Time for the second article! mov rdx, 6 ; Do what I did last time call TheNTInsiderReadSingleArticle ; Read the next article! test eax, eax ; Testin'... js Exit ; And jumpin'... A publication of OSR Open Systems Resources, Inc. Resources, Systems Open OSR of A publication lea rcx, [TipsForUsingIoTargts] ; Let's read another article! mov rdx, 8 ; TODO: Learn to write a MASM loop.. -

Shorten Device Boot Time for Automotive IVI and Navigation Systems
Shorten Device Boot Time for Automotive IVI and Navigation Systems Jim Huang ( 黃敬群 ) <[email protected]> Dr. Shi-wu Lo <[email protected]> May 28, 2013 / Automotive Linux Summit (Spring) Rights to copy © Copyright 2013 0xlab http://0xlab.org/ [email protected] Attribution – ShareAlike 3.0 Corrections, suggestions, contributions and translations You are free are welcome! to copy, distribute, display, and perform the work to make derivative works Latest update: May 28, 2013 to make commercial use of the work Under the following conditions Attribution. You must give the original author credit. Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. For any reuse or distribution, you must make clear to others the license terms of this work. Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. License text: http://creativecommons.org/licenses/by-sa/3.0/legalcode Goal of This Presentation • Propose a practical approach of the mixture of ARM hibernation (suspend to disk) and Linux user-space checkpointing – to shorten device boot time • An intrusive technique for Android/Linux – minimal init script and root file system changes are required • Boot time is one of the key factors for Automotive IVI – mentioned by “Linux Powered Clusters” and “Silver Bullet of Virtualization (Pitfalls, Challenges and Concerns) Continued” at ALS 2013 – highlighted by “Boot Time Optimizations” at ALS 2012 About this presentation • joint development efforts of the following entities – 0xlab team - http://0xlab.org/ – OSLab, National Chung Cheng University of Taiwan, led by Dr. -

Through the Looking Glass: Webcam Interception and Protection in Kernel
VIRUS BULLETIN www.virusbulletin.com Covering the global threat landscape THROUGH THE LOOKING GLASS: and WIA (Windows Image Acquisition), which provides a WEBCAM INTERCEPTION AND still image acquisition API. PROTECTION IN KERNEL MODE ATTACK VECTORS Ronen Slavin & Michael Maltsev Reason Software, USA Let’s pretend for a moment that we’re the bad guys. We have gained control of a victim’s computer and we can run any code on it. We would like to use his camera to get a photo or a video to use for our nefarious purposes. What are our INTRODUCTION options? When we talk about digital privacy, the computer’s webcam The simplest option is just to use one of the user-mode APIs is one of the most relevant components. We all have a tiny mentioned previously. By default, Windows allows every fear that someone might be looking through our computer’s app to access the computer’s camera, with the exception of camera, spying on us and watching our every move [1]. And Store apps on Windows 10. The downside for the attackers is while some of us think this scenario is restricted to the realm that camera access will turn on the indicator LED, giving the of movies, the reality is that malware authors and threat victim an indication that somebody is watching him. actors don’t shy away from incorporating such capabilities A sneakier method is to spy on the victim when he turns on into their malware arsenals [2]. the camera himself. Patrick Wardle described a technique Camera manufacturers protect their customers by incorporating like this for Mac [8], but there’s no reason the principle into their devices an indicator LED that illuminates when can’t be applied to Windows, albeit with a slightly different the camera is in use. -

Latest Features Available from the Windows 10 Updates That Could Be Beneficial for Students & Businesses Based Within the Milwaukee Area
Latest features available from the windows 10 updates that could be beneficial for students & businesses based within the Milwaukee area By: Jeremy Konetz | November 20, 2018 | Informative Article What are some of the benefits that the latest windows 10 updates provide to students and Milwaukee area-based businesses? Note the last three updates made available through windows 10 updates are windows 10 version 1709 (Released: January 23, 2018), windows 10 version 1803 (Released: July 6, 2018), and windows 10 version 1809 (Released: October 1, 2018). What are some of the beneficial updates provided in the Windows 10 update version 1709 released on January 23, 2018, one of the first updates Windows 10 released this year. What are the areas that this update has improved on? 1) Deployment a. Launching the autopilot application. i. Accomplished through a zero-touch experience. Example shown in figure 1. Figure 1 Resource link: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10- version-1709 ii. Client or organization profile configuration can be accomplished at the vendor with the devices sent directly to them upon completion. Example shown in figure 2. Figure 2 1 Resource link: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10- version-1709 b. Activation on subscription to windows 10. i. Feature allows for Windows 10 enterprise to be deployed within an organizational networks structure without applying any keys or rebooting of devices or components within an organizations operational system. See figure 3. Figure 3 1 Resource link: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10- version-1709 ii. -
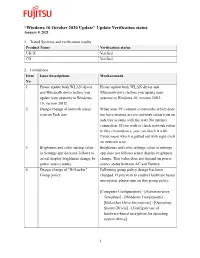
“Windows 10 October 2020 Update” Update Verification Status January 8, 2021
“Windows 10 October 2020 Update” Update Verification status January 8, 2021 1. Tested Systems and verification results Product Name Verification status UH-X Verified CH Verified 2. Limitations Item Issue descriptions Workarounds No 1 Please update both WLAN driver Please update both WLAN driver and and Bluetooth driver before you Bluetooth driver before you update your update your systems to Windows systems to Windows 10, version 20H2. 10, version 20H2. 2 Design change of network status When your PC connect to networks which does icon on Task tray. not have internet access, network status icon on task tray is same with the state No internet connection. If you wish to check network status in this circumstance, you can check it with flyout menu which is pulled out with right click on network icon. 3 Brightness and color setting value Brightness and color settings value in settings in Settings app does not follows to app does not follows actual display brightness actual display brightness change by change. This value does not depend on power power source status. source status between AC and Battery. 4 Design change of "BitLocker" Following group policy design has been Group policy. changed. If you wish to enable Hardware based encryption, please turn on this group policy. [Computer Configuration] - [Administrative Templates] - [Windows Components] - [BitLocker Drive Encryption] - [Operating System Drives] - [Configure use of hardware-based encryption for operating system drives] 1 Previous design: If the policy is not enabled, Hardware based encryption is enabled as default. New design: If the policy is not enabled, Software based encryption is enabled as default. -

WIN-911 7.17 & WEB-911 Xtools 7.13 System Requirements
WIN-911 7.17 & WEB-911 XTools 7.13 System Requirements WIN-911 • Personal computer with 2.1 GHz Pentium 4 processor or higher • Microsoft Windows XP Service Pack 3, Microsoft Windows Server 2003 Service Pack 1 or later, Microsoft Windows 2003 R2, Microsoft Windows 7 Service Pack 1, Microsoft Windows Server 2008 Service Pack 2, Microsoft Server 2008 R2 Service Pack 1, Microsoft Windows 8 & 8.1, Microsoft Server 2012, Microsoft Server 2012 R2, Windows 10. (Only US Versions of Windows) *** TAPI Voice Calls are NOT SUPPORTED in Windows 10 Version 1903 *** • 2GB of RAM. Additional RAM is recommended if additional programs are to be run simultaneously. • 2 GB of hard disk space • Optional Notification Hardware: Dial-out Paging Data fax modem and a dedicated analog phone line Voice Dial-outs/ins Dialogic telephonic card or a TAPI voice modem and a dedicated analog phone line. *** TAPI is NOT SUPPORTED in Windows 10 Version 1903 *** SMS Text Messaging GSM, CDMA or HSPA modem with an activated cellular account. Email Broadband always-on internet connection. Local Announcer Sound card and audio output source. Printing Dot Matrix printer or a printer capable of printing a "line-at-a-time" is recommended. WEB-911 Service • Must be installed on the same machine as WIN-911 • Microsoft .NET 4.0 and Internet Information Services (IIS) are also required • Microsoft Windows XP Service Pack 3, Microsoft Windows Server 2003 Service Pack 1 or later, Microsoft Windows 2003 R2, Microsoft Windows 7 Service Pack 1, Microsoft Windows Server 2008 Service Pack 2, Microsoft Server 2008 R2 Service Pack 1, Microsoft Windows 8 & 8.1, Microsoft Server 2012, Microsoft Server 2012 R2, Windows 10. -

Administrative Guide for Windows 10 and Windows Server Fall Creators Update (1709)
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1903 (May 2019 Update) General Purpose Operating System Protection Profile © 2019 Microsoft. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

Exam 70-797: Configuring Windows Devices (Pilot) – Skills Measured
Exam 70-797: Configuring Windows Devices (pilot) – Skills Measured Audience Profile This exam validates a candidate’s fundamental knowledge and skills for building solid identities, protection of content (data loss protection), mobile device management policy, virtualization with Hyper-V, application management using the Company Portal and the Windows Store. Candidates will be evaluated on Windows 10 security and integrated Azure features. In addition to their professional experience, candidates who take this exam should already have the following technical knowledge: Experience with Windows desktop administration, maintenance, and troubleshooting Basic experience and understanding of Windows networking technologies Introductory-level knowledge of Active Directory and Microsoft Intune Candidates can take this exam and meet the prerequisites by obtaining equivalent knowledge and skills through practical experience as a Windows device support technician or a Windows device system administrator. Skills Measured NOTE: The bullets that appear below each of the skills measured are intended to illustrate how we are assessing that skill. This list is not definitive or exhaustive. NOTE: In most cases, exams do NOT cover preview features, and some features will only be added to an exam when they are GA (General Availability). Manage identity (13%) Support Windows Store and cloud apps install and manage software by using Microsoft Office 365 and Windows Store apps, sideload apps by using Microsoft Intune, sideload apps into online and offline images, deeplink apps by using Microsoft Intune, integrate Microsoft account including personalization settings Support authentication and authorization identifying and resolving issues related to the following: Multi-factor authentication including certificates, Microsoft Passport, virtual smart cards, picture passwords, and biometrics; workgroup vs. -

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -

Reference & Manual
DynaPDF 4.0 Reference & Manual API Reference Version 4.0.59 September 16, 2021 Legal Notices Copyright: © 2003-2021 Jens Boschulte, DynaForms GmbH. All rights reserved. DynaForms GmbH Burbecker Street 24 D-58285 Gevelsberg, Germany Trade Register HRB 9770, District Court Hagen CEO Jens Boschulte Phone: ++49 23 32-666 78 37 Fax: ++49 23 32-666 78 38 If you have questions please send an email to [email protected], or contact us by phone. This publication and the information herein is furnished as is, is subject to change without notice, and should not be construed as a commitment by DynaForms GmbH. DynaForms assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes and no infringement of third-party rights. Adobe, Acrobat, and PostScript are trademarks of Adobe Systems Inc. AIX, IBM, and OS/390, are trademarks of International Business Machines Corporation. Microsoft, Windows, and Windows NT are trademarks of Microsoft Corporation. Apple, Mac OS, and Safari are trademarks of Apple Computer, Inc. registered in the United States and other countries. TrueType is a trademark of Apple Computer, Inc. Unicode and the Unicode logo are trademarks of Unicode, Inc. UNIX is a trademark of The Open Group. Solaris is a trademark of Sun Microsystems, Inc. Tru64 is a trademark of Hewlett-Packard. Linux is a trademark of Linus Torvalds. Other company product and service names may be trademarks or service marks of others. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -
Eaton Intelligent Power® Protector User’S Guide
Eaton Intelligent Power® Protector User’s Guide Eaton Intelligent Power® Protector – User’s Guide – / AI-1.28 www.eaton.com Table of Contents 1 Introduction .................................................................................................................. 4 2 Installation .................................................................................................................... 5 2.1 Installation Prerequisites .................................................................................................................. 5 2.1.1 On the System Hosting « Intelligent Power® Protector » .............................................................. 5 2.1.2 On the System that Displays Web-based Graphical User Interface............................................. 6 2.2 Quick Start & Installation .................................................................................................................. 7 2.3 Windows Installation ......................................................................................................................... 9 2.3.1 Graphical installation .................................................................................................................... 9 2.3.2 Installation / Uninstallation from command line .......................................................................... 10 2.3.3 Uninstalling the Product .............................................................................................................. 11 2.4 Linux Installation .............................................................................................................................