Vulnerability Summary for the Week of November 14, 2016
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Content Management (CMS) Lecture 02: Content Management Systems - Introduction Mariusz Trzaska, Ph
Content Management (CMS) Lecture 02: Content Management Systems - introduction Mariusz Trzaska, Ph. D. [email protected], http:// www.mtrzaska.com Agenda Introduction CMS functionality Design of a CMS Classification and review of CMSs Summary Source : Wikipedia.com, Fragments of materials written by professor Kazimierz Subieta. Content management 2 Introduction Content Management System (CMS) Internet portal (Wikipedia): the kind of information service for which the Internet is a medium. Typically, a web portal includes news, weather, web directory, chat and search functionality. Content management 3 Introduction (2) Polish portals o Wirtualna Polska – first portal in Poland o Onet.pl o Gazeta.pl o o2.pl Foreign portals o Yahoo o AOL Content management 4 Introduction (3) Vortal – special kind of a portal, publishing information thematically similar to each other Wikipedia Examples o Theatrical vortal : http://www.e-teatr.pl/ o Sports vortal: http://new.sports.pl/ o Astronomical vortal : http://www.astronomia.pl/ o Treasure Hunter’s vortal: http://www.poszukiwania.pl o Software vortal: www.dobreprogramy.pl/ o Portals/ Vortals on Wikipedia: http://pl.wikipedia.org/wiki/Wikipedia:Wikiportale Content management 5 Creative chaos in the field of CMS Technological and market innovation and the possibility of earning big money cause the beginning of chaos. If A, B, C, formats are used for a given type of content, then a mapping A-B, B-A, A-C will be needed The lack of standards and incompatible solutions implies middleware, mostly based on the new format (see JSON, XML). The "two programmers in the garage" syndrome: the success of a micro-scale solution causes the bottom-up solution for the macro-scale to expand (see HTML, XML, ...). -

Vulnerability Summary Report of May, 2019
1 SB19-154 VULNERABILITY SUMMARY FOR MAY 2019 2 SB19-154 Vulnerability Summary for May 2019 Cybernetic GI Security Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) in the past week. The Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) / United States Computer Emergency Readiness Team, is sponsored by The NVD. For modified or updated entries, please visit the NVD, which contains historical vulnerability information. The vulnerabilities are based on the CVE vulnerability naming standard and determined by the Common Vulnerability Scoring System (CVSS) standard. They are organized according to severity, by the division of high, medium and low severities correspond to the following scores: High -Vulnerabilities will be labeled High severity if they have a CVSS base score of 10.0 - 7.0. Medium - Vulnerabilities will be labeled Medium severity if they have a CVSS base score of - 4.0 6.9 Low - Vulnerabilities will be labeled Low severity if they have a CVSS base score of 3.9 - 0.0 Entries may include additional information provided by organizations and efforts sponsored by Cybernetic GI. This data may include identifying information, values, definitions, and related links. The patch information is provided to users when available. Please note that some of the information in the bulletin is compiled from external, open source reports and is not a direct result of Cybernetic GI analysis. The NCCIC Weekly Vulnerability Summary Bulletin is created using information from the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD). -

Professional LAMP : Linux, Apache, Mysql, and PHP Web Development / Jason Gerner
01_59723x ffirs.qxd 10/31/05 6:37 PM Page iii Professional LAMP Linux®, Apache, MySQL®, and PHP5 Web Development Jason Gerner Elizabeth Naramore Morgan L. Owens Matt Warden 01_59723x ffirs.qxd 10/31/05 6:37 PM Page i Professional LAMP 01_59723x ffirs.qxd 10/31/05 6:37 PM Page ii 01_59723x ffirs.qxd 10/31/05 6:37 PM Page iii Professional LAMP Linux®, Apache, MySQL®, and PHP5 Web Development Jason Gerner Elizabeth Naramore Morgan L. Owens Matt Warden 01_59723x ffirs.qxd 10/31/05 6:37 PM Page iv Professional LAMP: Linux®, Apache, MySQL®,and PHP5 Web Development Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2006 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN-13: 978-0-7645-9723-7 ISBN-10: 0-7645-9723-X Printed in the United States of America Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1MA/RW/RR/QV/IN Library of Congress Cataloging-in-Publication Data Professional LAMP : Linux, Apache, MySQL, and PHP Web development / Jason Gerner ... [et al.]. p. cm. ISBN-13: 978-0-7645-9723-7 (paper/website) ISBN-10: 0-7645-9723-X (paper/website) 1. Web site development. 2. Open source software. I. Title: Linux, Apache, MySQL, and PHP Web development. II. Gerner, Jason, 1978– TK5105.888.P677 2006 005.2'762—dc22 2005026487 No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, except as permitted under Section 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc., 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. -

Open Source Platforms - Content Management Systems (CMS)
Open Source Platforms - Content Management Systems (CMS) Γιάκας Αθανάσιος ΑΕΜ 531 Συστήματα Διαχείρισης Περιεχομένου ● Τα Συστήματα Διαχείρισης Περιεχομένου (ΣΔΠ, Content Management Systems, CMS) είναι διαδικτυακές εφαρμογές που επιτρέπουν την online τροποποίηση του περιεχομένου ενός δικτυακού τόπου. ● Οι διαχειριστές μέσω του διαδικτύου ενημερώνουν το περιεχόμενο στο ΣΔΠ, το οποίο είναι εγκατεστημένο σ' ένα διακομιστή. Οι αλλαγές αυτές γίνονται αυτόματα διαθέσιμες πάλι μέσω του διαδικτύου, σε όλους τους επισκέπτες και χρήστες του δικτυακού τόπου. Κατάλογος Συστημάτων Διαχείρισης Περιεχομένου Ανοιχτού Κώδικα ανά πλατφόρμα ● ASP.NET: DotNetNuke Community Edition , mojoPortal , Umbraco , N2 CMS , MvcCms ● JAVA: jAPS, OpenCms, Liferay, Dspace, Fedora, dotCMS, Nuxeo EP, Alfresco, Magnolia, Hippo, Calenco ● Perl: blosxom ,Bricolage , MojoMojo, Movable Type ,Twiki ,Scoop ,Slash ,WebGUI ● PHP: AdaptCMS Lite, Atutor, b2evolution, Bedita, BLOG:CMS, CivicSpace, CMS Made Simple, Concrete5, Dotclear, Drupal ,DynPG, eFront ,e107, Exponent CMS, eZ Publish, Frog CMS, Gamboo Web Suite, GCMS, ImpressCMS, Jaws, Joomla!, Habari, KnowledgeTree Document Management System, Lyceum,Mambo,Merlintalk, MiaCMS, Midgard CMS MODx, MySource Matrix (Squiz), Nucleus ,Opus,PHP-Fusion, PHP-Nuke, PHPSlash, phpWebSite,Pixie (CMS),RavenNuke CMS,SilverStripe,SPIP, TangoCMS, Textpattern,TikiWiki CMS/Groupware ,Tribiq CMS ,TYPO3 ,whCMS,WordPress,Website Baker, Xaraya, Zikula Κάποιοα από τα πιο δημοφιλή open source CMS ● Drupal ● Wordpress ● Joomla ● Textpattern ● Radiant CMS -
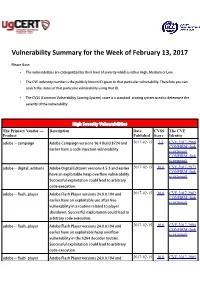
Vulnerability Summary for the Week of February 13, 2017
Vulnerability Summary for the Week of February 13, 2017 Please Note: • The vulnerabilities are cattegorized by their level of severity which is either High, Medium or Low. • The !" indentity number is the #ublicly $nown %& given to that #articular vulnerability. Therefore you can search the status of that #articular vulnerability using that %&. • The CVSS (Common Vulnerability Scoring 'ystem) score is a standard scoring system used to determine the severity of the vulnerability. High Severity Vulnerabilities The Primary Vendor --- Description Date CVSS The CVE Product Published Score Identity adobe ** cam#aign +dobe am#aign versions ,-.4 /uild 012. and 2017-02-15 7.5 CVE-2017-2968 CONFIRM (link earlier have a code in3ection vulnerability. is external) CONFIRM (link is external) adobe ** digital_editions +dobe Digital Editions versions ..5.3 and earlier 2017-02-15 10.0 CVE-2017-2973 CONFIRM (link have an e7#loitable hea# overflow vulnerability. is external) 'uccessful e7#loitation could lead to arbitrary code e7ecution. adobe ** flash4#layer +dobe 8lash Player versions 2..9.0.1:. and 2017-02-15 10.0 CVE-2017-2982 CONFIRM (link earlier have an e7#loitable use after free is external) vulnerability in a routine related to #layer shutdown. 'uccessful e7#loitation could lead to arbitrary code e7ecution. adobe ** flash4#layer +dobe 8lash Player versions 2..9.0.1:. and 2017-02-15 10.0 CVE-2017-2984 CONFIRM (link earlier have an e7#loitable hea# overflow is external) vulnerability in the h2-. decoder routine. 'uccessful e7#loitation could lead to arbitrary code e7ecution. adobe ** flash4#layer +dobe 8lash Player versions 2..9.0.1:. -
Professional LAMP : Linux, Apache, Mysql, and PHP Web Development / Jason Gerner
01_59723x ffirs.qxd 10/31/05 6:37 PM Page iii Professional LAMP Linux®, Apache, MySQL®, and PHP5 Web Development Jason Gerner Elizabeth Naramore Morgan L. Owens Matt Warden 01_59723x ffirs.qxd 10/31/05 6:37 PM Page iv Professional LAMP: Linux®, Apache, MySQL®,and PHP5 Web Development Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2006 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN-13: 978-0-7645-9723-7 ISBN-10: 0-7645-9723-X Printed in the United States of America Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 1MA/RW/RR/QV/IN Library of Congress Cataloging-in-Publication Data Professional LAMP : Linux, Apache, MySQL, and PHP Web development / Jason Gerner ... [et al.]. p. cm. ISBN-13: 978-0-7645-9723-7 (paper/website) ISBN-10: 0-7645-9723-X (paper/website) 1. Web site development. 2. Open source software. I. Title: Linux, Apache, MySQL, and PHP Web development. II. Gerner, Jason, 1978– TK5105.888.P677 2006 005.2'762—dc22 2005026487 No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, except as permitted under Section 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc., 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. -
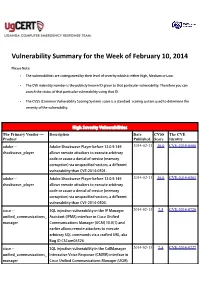
Vulnerability Summary for the Week of February 10, 2014
Vulnerability Summary for the Week of February 10, 2014 Please Note: • The vulnerabilities are cattegorized by their level of severity which is either High, Medium or Low. • The !" indentity number is the #ublicly $nown %& given to that #articular vulnerability. Therefore you can search the status of that #articular vulnerability using that %&. • The !'S (Common !ulnerability 'coring System) score is a standard scoring system used to determine the severity of the vulnerability. High Severity Vulnerabilities The Primary Vendor --- Description Date CVSS The CVE Product Published Score Identity adobe ** ,dobe 'hoc$wave Player before -..0.9.-10 2014-02-11 10.0 CVE-2014-0500 shoc$wave+#layer allows remote attac$ers to e2ecute arbitrary code or cause a denial of service (memory corru#tion) via uns#ecified vectors, a different vulnerability than !"*./-1*/3/-. adobe ** ,dobe 'hoc$wave Player before -..0.9.-10 2014-02-11 10.0 CVE-2014-0501 shoc$wave+#layer allows remote attac$ers to e2ecute arbitrary code or cause a denial of service (memory corru#tion) via uns#ecified vectors, a different vulnerability than !"*./-1*/3//. cisco ** 'QL in5ection vulnerability in the %P Manager 2014-02-13 7.5 CVE-2014-0726 unified_communications+ ,ssistant (%PM,) interface in isco 6nified manager ommunications Manager (6 M) -/.0(-) and earlier allows remote attac$ers to e2ecute arbitrary 'QL commands via a crafted 67L, a$a 8ug %D ' um/39.:. cisco ** 'QL in5ection vulnerability in the allManager 2014-02-13 7.5 CVE-2014-0727 unified_communications+ %nteractive !oice 7es#onse ( M%!7) interface in manager isco 6nified ommunications Manager (6 M) allows remote attac$ers to e2ecute arbitrary 'QL commands via a crafted 67L, a$a 8ug %D ' um/39-;. -
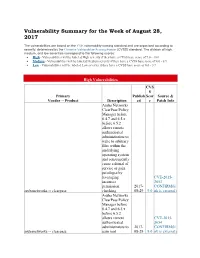
Vulnerability Summary for the Week of August 28, 2017
Vulnerability Summary for the Week of August 28, 2017 The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores: High - Vulnerabilities will be labeled High severity if they have a CVSS base score of 7.0 - 10.0 Medium - Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4.0 - 6.9 Low - Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0.0 - 3.9 High Vulnerabilities CVS S Primary Publish Scor Source & Vendor -- Product Description ed e Patch Info Aruba Networks ClearPass Policy Manager before 6.4.7 and 6.5.x before 6.5.2 allows remote authenticated administrators to write to arbitrary files within the underlying operating system and consequently cause a denial of service or gain privileges by leveraging CVE-2015- incorrect 3653 permission 2017- CONFIRM(li arubanetworks -- clearpass checking. 08-29 9.0 nk is external) Aruba Networks ClearPass Policy Manager before 6.4.7 and 6.5.x before 6.5.2 allows remote CVE-2015- authenticated 3654 administrators to 2017- CONFIRM(li arubanetworks -- clearpass gain root 08-29 9.0 nk is external) CVS S Primary Publish Scor Source & Vendor -- Product Description ed e Patch Info privileges via unspecified vectors, a different vulnerability than CVE-2015-4649. Aruba Networks ClearPass Policy Manager before 6.4.7 and 6.5.x before 6.5.2 allows remote authenticated administrators to gain root CVE-2015- privileges via 4649 unspecified CONFIRM(li vectors, a different nk is external) vulnerability than 2017- BID(link is arubanetworks -- clearpass CVE-2015-3654. -

Content Management Systems (CMS) Lecture 04: Content Management Systems – Presentation of Popular Solutions
Content Management Systems (CMS) Lecture 04: Content Management Systems – presentation of popular solutions Mariusz Trzaska, Ph. D. [email protected], http:// www.mtrzaska.com Agenda Presentation of several free systems. Popularity of CMS. Security of CMS. New trends Summary. Content management (CMS) 2 Introduction Sources: o The 20 point CMS test from http://www.openadvantage.org o https://www.ionos.com/digitalguide/hosting/cms /cms-comparison-a-review-of-the-best-platforms/ Content management (CMS) 3 Some popular CMSs (open-source) WordPress Orchard Drupal Magnolia Joomla Contao Xoops Neon Exponent CMS Plone Typo3 Exponent CMS Content management (CMS) 4 WordPress Used to be a blogging system. Currently: o powerful, o universal, o easy to use CMS system. One of the most popular in the world. Content management (CMS) 5 WordPress (2) Features o Dashboard with customizable widgets; o Preview of visual themes without applying them; o Simple image editing for articles; o Dedicated tag for automatic splitting of posts into pages; o Automatic media embedding; o Support for multiple portals on a single installation; Content management (CMS) 6 WordPress (3) Features – cont. o Very good WYSIWIG editor (classic and block- based); o Ability to specify the publication date; o Dedicated mobile applications for Android and iOS; o Optional blocking of posts with a password; o Draft content; o Good search system; o Friendly urls; Content management (CMS) 7 WordPress (4) Features – cont. o Multi-language support (GUI); o Importing content from other systems; o Automatic core and plugin updates; o Extensive API to facilitate potential integration with other systems; o Possibility of authentication using external services, e.g. -
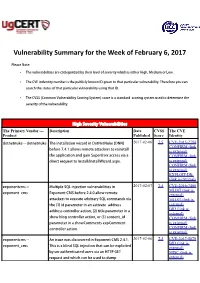
Vulnerability Summary for the Week of February 6, 2017
Vulnerability Summary for the Week of February 6, 2017 Please Note: • The vulnerabilities are cattegorized by their level of severity which is either High, Medium or Low. • The !" indentity number is the #ublicly $nown %& given to that #articular vulnerability. Therefore you can search the status of that #articular vulnerability using that %&. • The CVSS (Common Vulnerability Scoring 'ystem) score is a standard scoring system used to determine the severity of the vulnerability. High Severity Vulnerabilities The Primary Vendor --- Description Date CVSS The CVE Product Published Score Identity dotnetnu$e ** dotnetnu$e The installation wizard in DotNetNu$e (DNN) 2017-02-06 7.5 CVE-2015-2794 CONFIRM (link before +.4.- allows remote attac$ers to reinstall is external) the a##lication and gain 'u#er.ser access via a CONFIRM (link direct re/uest to %nstall/%nstallWizard.as#2. is external) CONFIRM (link is external) EXPLOIT-DB (link is external) e2#onentcms ** Multi#le 'QL in5ection vulnerabilities in 2017-02-07 7.5 CVE-2016-7400 MLIST (link is e2#onent3cms "2#onent M' before 6.4.0 allow remote external) attac$ers to e2ecute arbitrary 'QL commands via MLIST (link is the (-) id #arameter in an activate3address external) BID (link is address controller action, (6) title #arameter in a external) show blog controller action, or (8) content3id CONFIRM (link #arameter in a showComments e2# omment is external) controller action. CONFIRM (link is external) e2#onentcms ** 9n issue was discovered in "2#onent M' 6.4.1. 2017-02-06 7.5 CVE-2017-5879 BID (link is e2#onent3cms This is a blind '4L in5ection that can be e2#loited external) by un*authenticated users via an HTTP :"T MISC (link is re/uest and which can be used to dum# external) database data out to a malicious server, using an out*of*band techni/ue, such as select3loadfile(). -

Criando Sites Com Um Sistema De Gerenciamento De Conteúdo (CMS - Content Management Systems )
Criando sites com um Sistema de Gerenciamento de Conteúdo (CMS - Content Management Systems ) Sistema de Gerenciamento de Conteúdo (Content Management Systems - CMS ) Entendendo o que são Servidor Web e Host Preparando o computador para ser um servidor web Aprendendo a instalar e usar o CMS Wordpress Prof. Cláudio Toldo Webjornalismo 2 Sistema de Gerenciamento de Conteúdo (CMS - Content Management Systems ) O que é CMS: Um sistema gestor de sites, blogs, portais e intranets que integra ferramentas para criar, gerir (editar e inserir) conteúdos sem a necessidade de programação de código, cujo objetivo é estruturar e facilitar a criação, administração, distribuição, publicação e disponibilidade da informação de forma dinâmica, através de uma interface via internet. Os CMS são frameworks, “um esqueleto” de website pré-programado, com recursos básicos e de manutenção e administração prontamente disponíveis. Principais CMS (php + MySql + Apache): Wordpress, Joomla! e Drupal Outros: AdaptCMS Lite, BLOG:CMS, CivicSpace, eFront, Exponent CMS, ExpressionEngine, GCMS, ImpressCMS, Jaws, KnowledgeTree Document Management System, Lyceum, Mambo, MiaCMS, MODx, MySource Matrix (Squiz), Nucleus CMS, OneCMS, Opus, PHP-Fusion, PHP-Nuke, PHPSlash, phpWCMS, SilverStripe, SPIP, TangoCMS, Textpattern, TikiWiki CMS/Groupware, Tribiq CMS, TYPO3, whCMS, Midgard CMS, Frog CMS, MediaWiki, Merlintalk, phpWebSite, Habari, eZ Publish, Xaraya Os CMS são criados sob a licença GNU General Public License (Licença Pública Geral) GNU GPL ou simplesmente GPL, é a designação da licença para software livre idealizada por Richard Stallman no final da década de 1980, no âmbito do projeto GNU da Free Software Foundation (FSF). A GPL é a licença com maior utilização por parte de projetos de software livre, em grande parte devido à sua adoção para o Linux. -

Introduction to Website Designing & Development
SHREE SATGURUVE NAMAH Introduction to Website Designing & Development (Draft Version) Introduction to Website Designing & Development - 1 - List of Topics • Web-Application Management - An Overview • Web-Application / WebApp - Introduction • List of Web-Programming Language Popularity • What Web-Programming languages are people talking about? • Popular Web-Programming languages – An Overview • Database - Overview • Popular Web-Database Systems – An Overview • Database – Parameters • Application Service Provider (ASP) - What is it about? • Application Service Provider (ASP) - How it works? • Integrated Development Environment (IDE) • Comparison of Integrated Development Environments • Web-Application / WebApp - Development Guide • Before You Code: Part A – Reviewing Hosting Plans Features • Before You Code: Part B – Reviewing Hosting Plans Features • Before You Code: Web Site Basics: Stuff Beginners Need To Know • Before You Code: Database Websites from Scratch • Definition of Framework? • What is Application Framework? • What is Software Framework? • What is Web-Application Framework? • What is Enterprise Architecture Framework? • List of Content Management Frameworks (CMF) • List of Content Management Systems (CMS) • List of Web-application Frameworks • Glossary / Acronym / File Extensions • References • Conclusion Introduction to Website Designing & Development - 2 - Web-Application Management - An Overview - DATA PRESENTATION APPLICATION SERVER DATABASE SERVER Content Management Web-Programming Language Record/Files Management (Client-Side