Qlikview-Third-Party-License-Terms.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Licensing Information User Manual Release 9.1 F13415-01
Oracle® Hospitality Cruise Fleet Management Licensing Information User Manual Release 9.1 F13415-01 August 2019 LICENSING INFORMATION USER MANUAL Oracle® Hospitality Fleet Management Licensing Information User Manual Version 9.1 Copyright © 2004, 2019, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error- free. If you find any errors, please report them to us in writing. If this software or related documentation is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

AUTOMATIC DESIGN of NONCRYPTOGRAPHIC HASH FUNCTIONS USING GENETIC PROGRAMMING, Computational Intelligence, 4, 798– 831
Universidad uc3m Carlos Ill 0 -Archivo de Madrid This is a postprint version of the following published document: Estébanez, C., Saez, Y., Recio, G., and Isasi, P. (2014), AUTOMATIC DESIGN OF NONCRYPTOGRAPHIC HASH FUNCTIONS USING GENETIC PROGRAMMING, Computational Intelligence, 4, 798– 831 DOI: https://doi.org/10.1111/coin.12033 © 2014 Wiley Periodicals, Inc. AUTOMATIC DESIGN OF NONCRYPTOGRAPHIC HASH FUNCTIONS USING GENETIC PROGRAMMING CESAR ESTEBANEZ, YAGO SAEZ, GUSTAVO RECIO, AND PEDRO ISASI Department of Computer Science, Universidad Carlos III de Madrid, Madrid, Spain Noncryptographic hash functions have an immense number of important practical applications owing to their powerful search properties. However, those properties critically depend on good designs: Inappropriately chosen hash functions are a very common source of performance losses. On the other hand, hash functions are difficult to design: They are extremely nonlinear and counterintuitive, and relationships between the variables are often intricate and obscure. In this work, we demonstrate the utility of genetic programming (GP) and avalanche effect to automatically generate noncryptographic hashes that can compete with state-of-the-art hash functions. We describe the design and implementation of our system, called GP-hash, and its fitness function, based on avalanche properties. Also, we experimentally identify good terminal and function sets and parameters for this task, providing interesting information for future research in this topic. Using GP-hash, we were able to generate two different families of noncryptographic hashes. These hashes are able to compete with a selection of the most important functions of the hashing literature, most of them widely used in the industry and created by world-class hashing experts with years of experience. -

Software License Agreement (EULA)
Third-party Computer Software AutoVu™ ALPR cameras • angular-animate (https://docs.angularjs.org/api/ngAnimate) licensed under the terms of the MIT License (https://github.com/angular/angular.js/blob/master/LICENSE). © 2010-2016 Google, Inc. http://angularjs.org • angular-base64 (https://github.com/ninjatronic/angular-base64) licensed under the terms of the MIT License (https://github.com/ninjatronic/angular-base64/blob/master/LICENSE). © 2010 Nick Galbreath © 2013 Pete Martin • angular-translate (https://github.com/angular-translate/angular-translate) licensed under the terms of the MIT License (https://github.com/angular-translate/angular-translate/blob/master/LICENSE). © 2014 [email protected] • angular-translate-handler-log (https://github.com/angular-translate/bower-angular-translate-handler-log) licensed under the terms of the MIT License (https://github.com/angular-translate/angular-translate/blob/master/LICENSE). © 2014 [email protected] • angular-translate-loader-static-files (https://github.com/angular-translate/bower-angular-translate-loader-static-files) licensed under the terms of the MIT License (https://github.com/angular-translate/angular-translate/blob/master/LICENSE). © 2014 [email protected] • Angular Google Maps (http://angular-ui.github.io/angular-google-maps/#!/) licensed under the terms of the MIT License (https://opensource.org/licenses/MIT). © 2013-2016 angular-google-maps • AngularJS (http://angularjs.org/) licensed under the terms of the MIT License (https://github.com/angular/angular.js/blob/master/LICENSE). © 2010-2016 Google, Inc. http://angularjs.org • AngularUI Bootstrap (http://angular-ui.github.io/bootstrap/) licensed under the terms of the MIT License (https://github.com/angular- ui/bootstrap/blob/master/LICENSE). -

Open Source Used in Quantum SON Suite 18C
Open Source Used In Cisco SON Suite R18C Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-185964180 Open Source Used In Cisco SON Suite R18C 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-185964180 Contents 1.1 argparse 1.2.1 1.1.1 Available under license 1.2 blinker 1.3 1.2.1 Available under license 1.3 Boost 1.35.0 1.3.1 Available under license 1.4 Bunch 1.0.1 1.4.1 Available under license 1.5 colorama 0.2.4 1.5.1 Available under license 1.6 colorlog 0.6.0 1.6.1 Available under license 1.7 coverage 3.5.1 1.7.1 Available under license 1.8 cssmin 0.1.4 1.8.1 Available under license 1.9 cyrus-sasl 2.1.26 1.9.1 Available under license 1.10 cyrus-sasl/apsl subpart 2.1.26 1.10.1 Available under license 1.11 cyrus-sasl/cmu subpart 2.1.26 1.11.1 Notifications 1.11.2 Available under license 1.12 cyrus-sasl/eric young subpart 2.1.26 1.12.1 Notifications 1.12.2 Available under license Open Source Used In Cisco SON Suite R18C 2 1.13 distribute 0.6.34 -
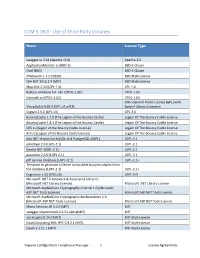
CCM 5.18.0 - Use of Third-Party Libraries
CCM 5.18.0 - Use of Third-Party Libraries Name License Type swagger-ui 3.24 (Apache v2.0) Apache-2.0 ApplicationMonitor.cs (BSD-2) BSD-2-Clause Oval (BSD) BSD-3-Clause IPNetwork 1.3.2.0 (BSD) BSD-Style License SSH.NET 2016.1.0 (MIT) BSD-Style License Mvp.Xml 2.3.0 (CPL-1.0) CPL-1.0 balloon windows for .net (CPOL-1.02) CPOL-1.02 Colorutil.cs (CPOL-1.02) CPOL-1.02 GNU General Public License (GPL) with SharpZipLib 0.81.0 (GPL v2 w/CE) Special Library Exception Cygwin 2.6.0 (GPL v3) GPL-3.0 BouncyCastle 1.7.0 (The Legion of the Bouncy Castle) Legion Of The Bouncy Castle License BouncyCastle 1.8.1 (The Legion of the Bouncy Castle) Legion Of The Bouncy Castle License DES.cs (Legion of the Bouncy Castle License) Legion Of The Bouncy Castle License Rc4.cs (Legion of the Bouncy Castle License) Legion Of The Bouncy Castle License Ado.NET drivers for MySQL and PostgreSQL (LGPL) LGPL-2.1 adodbapi 2.0 (LGPL-2.1) LGPL-2.1 Gentle.NET (LGPL-2.1) LGPL-2.1 paramiko 2.6.0 (LGPL 2.1) LGPL-2.1 p0f service database (LGPL v2.1) LGPL-2.1+ Template to generate a Gentle compatible business object from the database (LGPL-2.1) LGPL-2.1+ Cygrunsrv 1.62 (LPGLv3) LGPL-3.0 Microsoft .NET Framework & Associated Libraries (Microsoft.NET Library License) Microsoft .NET Library License Microsoft.AspNetCore.Cryptography.Internal 1.0 (Microsoft ASP.NET Tools License) Microsoft ASP.NET Tools License Microsoft.AspNetCore.Cryptography.KeyDerivation 1.0 (Microsoft ASP.NET Tools License) Microsoft ASP.NET Tools License Mono.Security.dll 4.0.0 (MIT) MIT swagger.objectmodel-2.2.31-alpha(MIT) -

Implementation of the Programming Language Dino – a Case Study in Dynamic Language Performance
Implementation of the Programming Language Dino – A Case Study in Dynamic Language Performance Vladimir N. Makarov Red Hat [email protected] Abstract design of the language, its type system and particular features such The article gives a brief overview of the current state of program- as multithreading, heterogeneous extensible arrays, array slices, ming language Dino in order to see where its stands between other associative tables, first-class functions, pattern-matching, as well dynamic programming languages. Then it describes the current im- as Dino’s unique approach to class inheritance via the ‘use’ class plementation, used tools and major implementation decisions in- composition operator. cluding how to implement a stable, portable and simple JIT com- The second part of the article describes Dino’s implementation. piler. We outline the overall structure of the Dino interpreter and just- We study the effect of major implementation decisions on the in-time compiler (JIT) and the design of the byte code and major performance of Dino on x86-64, AARCH64, and Powerpc64. In optimizations. We also describe implementation details such as brief, the performance of some model benchmark on x86-64 was the garbage collection system, the algorithms underlying Dino’s improved by 3.1 times after moving from a stack based virtual data structures, Dino’s built-in profiling system, and the various machine to a register-transfer architecture, a further 1.5 times by tools and libraries used in the implementation. Our goal is to give adding byte code combining, a further 2.3 times through the use an overview of the major implementation decisions involved in of JIT, and a further 4.4 times by performing type inference with a dynamic language, including how to implement a stable and byte code specialization, with a resulting overall performance im- portable JIT. -

Hash-Flooding Dos Reloaded
Hash-flooding DoS reloaded: Hash flooding begins? attacks and defenses July 1998 article Jean-Philippe Aumasson, “Designing and attacking Kudelski Security (NAGRA) port scan detection tools” by Solar Designer (Alexander D. J. Bernstein, Peslyak) in Phrack Magazine: University of Illinois at Chicago & Technische Universiteit Eindhoven “In scanlogd, I’m using a hash table to lookup source addresses. Martin Boßlet, This works very well for the Ruby Core Team typical case ::: average lookup time is better than that of a binary search. ::: Hash-flooding DoS reloaded: Hash flooding begins? However, an attacker can attacks and defenses choose her addresses (most July 1998 article likely spoofed) to cause hash Jean-Philippe Aumasson, “Designing and attacking collisions, effectively replacing the Kudelski Security (NAGRA) port scan detection tools” hash table lookup with a linear by Solar Designer (Alexander D. J. Bernstein, search. Depending on how many Peslyak) in Phrack Magazine: University of Illinois at Chicago & entries we keep, this might make Technische Universiteit Eindhoven “In scanlogd, I’m using a hash scanlogd not be able to pick table to lookup source addresses. ::: Martin Boßlet, new packets up in time. I’ve This works very well for the Ruby Core Team solved this problem by limiting typical case ::: average lookup the number of hash collisions, and time is better than that of a discarding the oldest entry with binary search. ::: the same hash value when the limit is reached. Hash-flooding DoS reloaded: Hash flooding begins? However, an attacker can attacks and defenses choose her addresses (most July 1998 article likely spoofed) to cause hash Jean-Philippe Aumasson, “Designing and attacking collisions, effectively replacing the Kudelski Security (NAGRA) port scan detection tools” hash table lookup with a linear by Solar Designer (Alexander D. -

On Realizing the Concept Study Sciencesoft of the European Middleware Initiative Open Software for Open Science
On Realizing the Concept Study ScienceSoft of the European Middleware Initiative Open Software for Open Science Alberto Di Meglio, Florida Estrella Morris Riedel European Center for Nuclear Research Juelich Supercomputing Centre CERN Forschungszentrum Juelich Geneva, Switzerland Juelich, Germany {Alberto.Di.Meglio,Florida Estrella}@cern.ch [email protected] Abstract—In September 2011 the European Middleware focused on people and their publications, but do not currently Initiative (EMI) started discussing the feasibility of creating an allow collecting information about software and the open source community for science with other projects like EGI, organizations and projects developing or using it. Being able to StratusLab, OpenAIRE, iMarine, and IGE, SMEs like DCore, aggregate the power of cataloguing services of software, Maat, SixSq, SharedObjects, communities like WLCG and people and organizations, analyse trends and generate statistics LSGC. The general idea of establishing an open source and reports would provide a sound basis for judging the community dedicated to software for scientific applications was popularity of software products, enable social-networking-style understood and appreciated by most people. However, the lack of collaborations amongst users and developers, create active, a precise definition of goals and scope is a limiting factor that has cross-disciplinary communities and better promote the value of also made many people sceptical of the initiative. In order to such collaborations and their impact on science in general. understand more precisely what such an open source initiative should do and how, EMI has started a more formal feasibility Rating software and providing a means by which it can be cited study around a concept called ScienceSoft – Open Software for in a similar manner to publications and datasets would enable Open Science. -

Annals of the University of North Carolina Wilmington Master of Science in Computer Science and Information Systems
Annals of the University of North Carolina Wilmington Master of Science in Computer Science and Information Systems RE-VISIONING OF THE AUTOMATIC GRADING/LEARNING SYSTEM Jason Felds A Capstone Project Submitted to the University of North Carolina Wilmington in Partial Fulfillment of the Requirements for the Degree of Master of Science Department of Computer Science Department of Information Systems and Operations Management University of North Carolina Wilmington 2012 Approved by Advisory Committee ______________________________ ______________________________ Dr. Bryan Reinicke Dr. Laurie Patterson ______________________________ ______________________________ Kevin Matthews Dr. Thomas Janicki, Chair Accepted By _______________________________ Dean, Graduate School Abstract Re-visioning of the Automatic Grading/Learning System. Felds, Jason, 2012. Capstone Paper, University of North Carolina Wilmington. In 2008, the ISOM department at UNCW implemented a system that would allow students in certain classes to be able to submit electronic files to be automatically graded as part of the existing grade book system. While that system has been successful, enhancements are desired to make the system more user-friendly and to grade additional features. A number of flaws have been uncovered with the Automatic Grading/Learning System (AGLS) that should be corrected. The goal of this project is to make it easier for the professor to create and grade assignments, but also to make the AGLS more generic so it may be used by other grade book systems. -

Storefront Third Party Notices
StoreFront™ Third Party Notices StoreFront™ may include third party software components licensed under the following terms. This list was generated using third party software as of the date listed. This list may change with specific versions of the product and may not be complete; it is provided “As-Is.” TO THE EXTENT PERMITTED BY APPLICABLE LAW, CITRIX AND ITS SUPPLIERS MAKE NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, WITH REGARD TO THE LIST OR ITS ACCURACY OR COMPLETENESS, OR WITH RESPECT TO ANY RESULTS TO BE OBTAINED FROM USE OR DISTRIBUTION OF THE LIST. BY USING OR DISTRIBUTING THE LIST, YOU AGREE THAT IN NO EVENT SHALL CITRIX BE HELD LIABLE FOR ANY SPECIAL, DIRECT, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY OTHER DAMAGES WHATSOEVER RESULTING FROM ANY USE OR DISTRIBUTION OF THIS LIST. Castle Windsor Castle Windsor 3.3.0 Copyright 2004-2014 Castle Project - http://www.castleproject.org/ Licensed under the Apache License, Version 2.0 Microsoft Unity Microsoft Unity Application Block (Unity) 2.1 Copyright © 2011 Microsoft Corporation. Licensed under the Microsoft Public License (MS-PL) https://msdn.microsoft.com/en-us/library/hh237493.aspx Microsoft Prism Microsoft Patterns and Practices: Prism 2.2 Copyright © 2010 Microsoft Corporation. Licensed under the Microsoft Public License (MS-PL) http://compositewpf.codeplex.com/releases/view/46046 Microsoft Common Service Locator Microsoft patterns & practices: Common Service Locator 1.0 Copyright © Microsoft Corporation. Licensed under the Microsoft Public License (MS-PL) Microsoft .Net Reference Source Microsoft .NET Reference Source Copyright © Microsoft Corporation. Licensed under the MIT license. Managed Esent ManagedEsent Release 1.9.4 Copyright © Microsoft Corporation. -

Automated Malware Analysis Report for Phish Survey.Js
ID: 382893 Sample Name: phish_survey.js Cookbook: default.jbs Time: 20:27:42 Date: 06/04/2021 Version: 31.0.0 Emerald Table of Contents Table of Contents 2 Analysis Report phish_survey.js 3 Overview 3 General Information 3 Detection 3 Signatures 3 Classification 3 Startup 3 Malware Configuration 3 Yara Overview 3 Sigma Overview 3 Signature Overview 3 Mitre Att&ck Matrix 4 Behavior Graph 4 Screenshots 5 Thumbnails 5 Antivirus, Machine Learning and Genetic Malware Detection 6 Initial Sample 6 Dropped Files 6 Unpacked PE Files 6 Domains 6 URLs 6 Domains and IPs 7 Contacted Domains 7 URLs from Memory and Binaries 7 Contacted IPs 8 General Information 8 Simulations 9 Behavior and APIs 9 Joe Sandbox View / Context 9 IPs 9 Domains 9 ASN 9 JA3 Fingerprints 9 Dropped Files 9 Created / dropped Files 9 Static File Info 9 General 9 File Icon 9 Network Behavior 10 Code Manipulations 10 Statistics 10 System Behavior 10 Analysis Process: wscript.exe PID: 6168 Parent PID: 3388 10 General 10 File Activities 10 Disassembly 10 Code Analysis 10 Copyright Joe Security LLC 2021 Page 2 of 10 Analysis Report phish_survey.js Overview General Information Detection Signatures Classification Sample phish_survey.js Name: FFoouunndd WSSHH tttiiimeerrr fffoorrr JJaavvaassccrrriiippttt oorrr VV… Analysis ID: 382893 JFJaaovvuaan d/// VVWBBSSSHccr rritiipipmttt feffiiillrlee f owwrii ittJthha vveaerrsryyc rllloiopnntg go srs …V MD5: b3c1f68ef7299a7… PJParrrovogagrr ra/a mVB ddSooceersisp ntn ofoitltte ss hwhooitwhw vmeuurycc hhlo aanccgttt iiivsviii… SHA1: b8e9103fffa864a… -
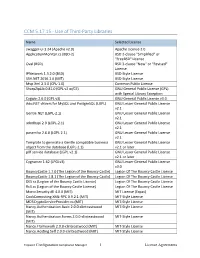
CCM 5.17.15 - Use of Third-Party Libraries
CCM 5.17.15 - Use of Third-Party Libraries Name Selected License swagger-ui 3.24 (Apache v2.0) Apache License 2.0 ApplicationMonitor.cs (BSD-2) BSD 2-clause "Simplified" or "FreeBSD" License Oval (BSD) BSD 3-clause "New" or "Revised" License IPNetwork 1.3.2.0 (BSD) BSD-Style License SSH.NET 2016.1.0 (MIT) BSD-Style License Mvp.Xml 2.3.0 (CPL-1.0) Common Public License SharpZipLib 0.81.0 (GPL v2 w/CE) GNU General Public License (GPL) with Special Library Exception Cygwin 2.6.0 (GPL v3) GNU General Public License v3.0 Ado.NET drivers for MySQL and PostgreSQL (LGPL) GNU Lesser General Public License v2.1 Gentle.NET (LGPL-2.1) GNU Lesser General Public License v2.1 adodbapi 2.0 (LGPL-2.1) GNU Lesser General Public License v2.1 paramiko 2.6.0 (LGPL 2.1) GNU Lesser General Public License v2.1 Template to generate a Gentle compatible business GNU Lesser General Public License object from the database (LGPL-2.1) v2.1 or later p0f service database (LGPL v2.1) GNU Lesser General Public License v2.1 or later Cygrunsrv 1.62 (LPGLv3) GNU Lesser General Public License v3.0 BouncyCastle 1.7.0 (The Legion of the Bouncy Castle) Legion Of The Bouncy Castle License BouncyCastle 1.8.1 (The Legion of the Bouncy Castle) Legion Of The Bouncy Castle License DES.cs (Legion of the Bouncy Castle License) Legion Of The Bouncy Castle License Rc4.cs (Legion of the Bouncy Castle License) Legion Of The Bouncy Castle License Mono.Security.dll 4.0.0 (MIT) MIT License (Expat) CookComputing XML-RPC 0.9.2.1 (MIT) MIT-Style License MD5CryptoServiceProvider.cs (MIT) MIT-Style