Cyber Security Study for Automotive Ethernet in Japan Automotive Industry
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Published on July 21, 2021 1. Changes in Constituents 2
Results of the Periodic Review and Component Stocks of Tokyo Stock Exchange Dividend Focus 100 Index (Effective July 30, 2021) Published on July 21, 2021 1. Changes in Constituents Addition(18) Deletion(18) CodeName Code Name 1414SHO-BOND Holdings Co.,Ltd. 1801 TAISEI CORPORATION 2154BeNext-Yumeshin Group Co. 1802 OBAYASHI CORPORATION 3191JOYFUL HONDA CO.,LTD. 1812 KAJIMA CORPORATION 4452Kao Corporation 2502 Asahi Group Holdings,Ltd. 5401NIPPON STEEL CORPORATION 4004 Showa Denko K.K. 5713Sumitomo Metal Mining Co.,Ltd. 4183 Mitsui Chemicals,Inc. 5802Sumitomo Electric Industries,Ltd. 4204 Sekisui Chemical Co.,Ltd. 5851RYOBI LIMITED 4324 DENTSU GROUP INC. 6028TechnoPro Holdings,Inc. 4768 OTSUKA CORPORATION 6502TOSHIBA CORPORATION 4927 POLA ORBIS HOLDINGS INC. 6503Mitsubishi Electric Corporation 5105 Toyo Tire Corporation 6988NITTO DENKO CORPORATION 5301 TOKAI CARBON CO.,LTD. 7011Mitsubishi Heavy Industries,Ltd. 6269 MODEC,INC. 7202ISUZU MOTORS LIMITED 6448 BROTHER INDUSTRIES,LTD. 7267HONDA MOTOR CO.,LTD. 6501 Hitachi,Ltd. 7956PIGEON CORPORATION 7270 SUBARU CORPORATION 9062NIPPON EXPRESS CO.,LTD. 8015 TOYOTA TSUSHO CORPORATION 9101Nippon Yusen Kabushiki Kaisha 8473 SBI Holdings,Inc. 2.Dividend yield (estimated) 3.50% 3. Constituent Issues (sort by local code) No. local code name 1 1414 SHO-BOND Holdings Co.,Ltd. 2 1605 INPEX CORPORATION 3 1878 DAITO TRUST CONSTRUCTION CO.,LTD. 4 1911 Sumitomo Forestry Co.,Ltd. 5 1925 DAIWA HOUSE INDUSTRY CO.,LTD. 6 1954 Nippon Koei Co.,Ltd. 7 2154 BeNext-Yumeshin Group Co. 8 2503 Kirin Holdings Company,Limited 9 2579 Coca-Cola Bottlers Japan Holdings Inc. 10 2914 JAPAN TOBACCO INC. 11 3003 Hulic Co.,Ltd. 12 3105 Nisshinbo Holdings Inc. 13 3191 JOYFUL HONDA CO.,LTD. -

Turn for More Solutions
Audio Solutions Installation & Design Services Servers Carts Kiosks Small Form Factor Computers Desktops Lighting Software PRODUCTS Disaster Recovery Products Notebooks & Tablets Telehealth Solutions Interactive Solutions Rugged Telemedicine Kits Temperature Sensing Kiosks Interactive Touchscreen LCDs Sanitizable Technology Wall-Mounted Arms & Cabinets A | COMPUTING SOLUTIONS D | VIRTUALIZATION 1. ACCESSORIES: Belkin, C2G, Case Logic, Kensington, Targus 1. BACKUP & DR: Arcserve, Barracuda, Nakivo, Veeam, Zerto 2. ANTIVIRUS: AVG, BitDefender, Malware Bytes, McAfee, Panda 2. CLOUD: Arcserve, Greencloud, Microsoft Security, Sophos, Symantec, Total Defense, Trend Micro 3. DESKTOP VIRTUALIZATION: Citrix, HVE, NComputing, VMWare 3. DESKTOPS: Howard, Dell, HP, Lenovo, Tangent 4. SERVER VIRTUALIZATION: Hyper-V, VMWare, XenServer 4. MANAGEMENT SOLUTIONS: Symantec 5. SERVERS: Howard, Dell, HPE, HVE, Lenovo, Microsoft, Nutanix 5. MOBILE PRESENTATION & CHARGING STATIONS: Aver, Bretford, 6. SOFTWARE-DEFINED STORAGE: Datacore Kwikboost, LocknCharge 7. STORAGE: Dell EMC, HPE, HVE, Lenovo, QNAP, Synology 6. NOTEBOOKS & TABLETS: Howard, Acer, Asus, Cybernet, Dell, Getac, HP, 8. VIRTUAL DESKTOP INFRASTRUCTURE: Citrix, Dell, HVE, Inuvika, LG, Lenovo, Microsoft, Panasonic, Samsung, Tangent, Toshiba, Xplore NComputing, VMWare 7. PRINTERS (2D & 3D): Brother, Canon, Dell, DYMO, Epson, HP, Lexmark, Panasonic, Samsung, Xerox 8. VIRTUAL REALITY: Epson, HP, Oculus Rift, Samsung E | PHYSICAL SECURITY 1. ACCESS CONTROL: 3xlogic, Avue Technologies, Axis, Bosch, B | AUDIOVISUAL SOLUTIONS GeoVision, Isonas, Openpath, MotorCast 2. CLOUD: Brivo, Openpath 1. AUDIO SOLUTIONS: Howard, AMX, Harman, Panasonic 3. DISPLAYS: LG, NEC, Panasonic, Planar, Samsung, Sharp, Sony, ViewSonic 2. BROADCASTING: Panasonic, Sony, Tri-Caster 4. ENCODERS: Axis, Bosch, Hikvision, Panasonic 3. CABLES: C2G, Comprehensive, Crestron, Peerless 5. MASS NOTIFICATION: Singlewire 4. FURNITURE: Middle Atlantic, Spectrum Industries, Worthington Direct 6. MOUNTING & ACCESSORIES: Advidia, Altronix, Avue Technologies, 5. -

Factset-Top Ten-0521.Xlsm
Pax International Sustainable Economy Fund USD 7/31/2021 Port. Ending Market Value Portfolio Weight ASML Holding NV 34,391,879.94 4.3 Roche Holding Ltd 28,162,840.25 3.5 Novo Nordisk A/S Class B 17,719,993.74 2.2 SAP SE 17,154,858.23 2.1 AstraZeneca PLC 15,759,939.73 2.0 Unilever PLC 13,234,315.16 1.7 Commonwealth Bank of Australia 13,046,820.57 1.6 L'Oreal SA 10,415,009.32 1.3 Schneider Electric SE 10,269,506.68 1.3 GlaxoSmithKline plc 9,942,271.59 1.2 Allianz SE 9,890,811.85 1.2 Hong Kong Exchanges & Clearing Ltd. 9,477,680.83 1.2 Lonza Group AG 9,369,993.95 1.2 RELX PLC 9,269,729.12 1.2 BNP Paribas SA Class A 8,824,299.39 1.1 Takeda Pharmaceutical Co. Ltd. 8,557,780.88 1.1 Air Liquide SA 8,445,618.28 1.1 KDDI Corporation 7,560,223.63 0.9 Recruit Holdings Co., Ltd. 7,424,282.72 0.9 HOYA CORPORATION 7,295,471.27 0.9 ABB Ltd. 7,293,350.84 0.9 BASF SE 7,257,816.71 0.9 Tokyo Electron Ltd. 7,049,583.59 0.9 Munich Reinsurance Company 7,019,776.96 0.9 ASSA ABLOY AB Class B 6,982,707.69 0.9 Vestas Wind Systems A/S 6,965,518.08 0.9 Merck KGaA 6,868,081.50 0.9 Iberdrola SA 6,581,084.07 0.8 Compagnie Generale des Etablissements Michelin SCA 6,555,056.14 0.8 Straumann Holding AG 6,480,282.66 0.8 Atlas Copco AB Class B 6,194,910.19 0.8 Deutsche Boerse AG 6,186,305.10 0.8 UPM-Kymmene Oyj 5,956,283.07 0.7 Deutsche Post AG 5,851,177.11 0.7 Enel SpA 5,808,234.13 0.7 AXA SA 5,790,969.55 0.7 Nintendo Co., Ltd. -
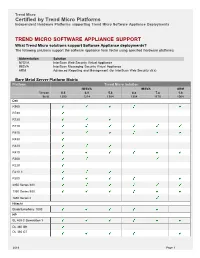
Certified by Trend Micro Platforms Independent Hardware Platforms Supporting Trend Micro Software Appliance Deployments
Trend Micro Certified by Trend Micro Platforms Independent Hardware Platforms supporting Trend Micro Software Appliance Deployments TREND MICRO SOFTWARE APPLIANCE SUPPORT What Trend Micro solutions support Software Appliance deployments? The following solutions support the software appliance form factor using specified hardware platforms Abbreviation Solution IWSVA InterScan Web Security Virtual Appliance IMSVA InterScan Messaging Security Virtual Appliance ARM Advanced Reporting and Management (for InterScan Web Security v5.x) Bare Metal Server Platform Matrix Platform Trend Micro Solution IWSVA IMSVA ARM Version 6.5 6.0 5.6 8.x 7.x 1.6 Build 1200 1214 1364 1304 1170 1068 Dell R900 R730 R720 R710 R610 R430 R420 R410 R300 R220 R210 II R200 2950 Series II/III 1950 Series II/III 1850 Series II Hitachi BladeSymphony 1000 HP BL 460 C Generation 1 DL 360 G9 DL 360 G7 2019 Page 1 Trend Micro Certified by Trend Micro Platforms Independent Hardware Platforms supporting Trend Micro Software Appliance Deployments Platform Trend Micro Solution IWSVA IMSVA ARM Version 6.5 6.0 5.6 8.x 7.x 1.6 Build 1200 1214 1364 1304 1170 1068 DL 360 G6 DL 380 G9 DL 380 G7 DL 380 G6 DL 380 G5 DL 385 G6 DL 385 G2 DL 350 G5 DL 388p G8 DL 380p G8 IBM Systems x3550 Systems x3550 M5 NEC Express5800 R120a-1 Express5800 R120RH-1 Resilience ATL 1012 Sun Sunfire X4450 SuperMicro Superserver 1026T Superserver 5016T Bare Metal Server Specifications Platform Hardware Specifications CPU Memory Hard Drive HD Controller NIC Dell PowerEdge R900 2 x Intel X7460 32GB Memory, 300 GB -

Annual REPORT 2013 77
ITOCHU CORPORATION ANNUAL REPORT 2013 77 Corporate Social Responsibility 78 CSR for ITOCHU Corporation 80 Activity Highlight: Resolving Social Issues through Business Striving to Resolve the Problems of Cotton Farmers in India through the Supply Chain Pre Organic Cotton Program 82 Documentary Report Project on Supply Chains Producing Lithium-Ion Batteries 85 ISO 26000 Core Subjects and ITOCHU’s Initiatives 86 Human Rights 87 Labor Practices 89 The Environment 91 Fair Operating Practices 92 Consumer Issues 93 Community Involvement and Development 78 ITOCHU CORPORATION ANNUAL REPORT 2013 CSR for ITOCHU Corporation ITOCHU Corporation is pursuing multifaceted corporate activities in various regions of the world and a wide range of fields. As such, ITOCHU is well aware of the impact of those activities on the global environment and society. For ITOCHU, CSR entails making a contribution to building sustainable societies through business activities. As a global company, it is our mission to be “Committed to the Global Good.” ITOCHU Mission and Values CSR Management System ITOCHU founder Chubei Itoh first launched a wholesale linen CSR Committee Examination and promotion of CSR policies and measures business in 1858. For more than 150 years since, ITOCHU has passed down the spirit of sampo yoshi (Good for the CSR Promotion & Global Environment Department, seller, Good for the buyer, and Good for society), a manage- Corporate Communications Division ment philosophy embraced by Ohmi merchants. Planning and proposal of CSR measures After considering ways to demonstrate its commitment CSR Taskforce to society as an international corporation and to put this Discussion of report production and CSR promotion measures commitment into practice, in 1992 ITOCHU formulated “Committed to the Global Good” as a corporate philosophy. -

GTC-ONE-Minute-Brief-92.Pdf
Equity | Currencies & Commodities | Corporate & Global Economic News & Economic Calendar 29 January 2019 Economic and political news Key indices Bosasa’s Ex-Chief Operating Officer, Angelo Agrizzi, in his testimony, As at 28 1 Day 1 D % WTD % MTD % Prev. month YTD % disclosed that the company agreed to pay ZAR300,000 a month to Jan 2019 Chg Chg Chg Chg % Chg Chg former President, Jacob Zuma’s charitable foundation to shield it from JSE All Share 53767.47 -282.76 -0.52 -0.52 1.95 4.09 1.95 prosecution. (ZAR) JSE Top 40 (ZAR) 47600.25 -292.16 -0.61 -0.61 1.87 4.63 1.87 South Africa’s Transport Minister, Blade Nzimande, stated that the government is keen to see South African Airways (SAA) debt restructured FTSE 100 (GBP) 6747.10 -62.12 -0.91 -0.91 0.28 -3.61 0.28 at the earliest. Meanwhile, SAA Chief Executive Officer, Vuyani Jarana, DAX 30 (EUR) 11210.31 -71.48 -0.63 -0.63 6.17 -6.20 6.17 stated that commercial banks have in principle approved ZAR3.5bn of CAC 40 (EUR) 4888.58 -37.24 -0.76 -0.76 3.34 -5.46 3.34 the funding SAA requires for operating expenses until April. S&P 500 (USD) 2643.85 -20.91 -0.78 -0.78 5.47 -9.18 5.47 Nasdaq Trade union, Solidarity, stated that former South African Broadcasting 7085.69 -79.18 -1.11 -1.11 6.79 -9.48 6.79 Corporation Chief Operating Officer, Hlaudi Motsoeneng, has made his Composite (USD) first payment of ZAR300,000 to the union. -

U.S. V. Aisin Seiki Co., Ltd. : Information
Case 1:14-cr-00229-JMS-MJD Document 1 Filed 11/13/14 Page 1 of 6 PageID #: 1 UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF INDIANA INDIANAPOLIS DIVISION UNITED STATES OF AMERICA ) Case No. ) ) Filed: v. ) ) Violation: 15 U.S.C. § 1 ) AISIN SEIKI CO., LTD., ) Defendant. 114: -cr-02 2 JMS-MJD9 INFORMATION COUNT ONE CONSPIRACY TO RESTRAIN TRADE 15 u.s.c. § 1 THE UNITED STATES, ACTING THROUGH ITS ATTORNEYS, CHARGES: I. Defendant and Co-Conspirators 1. AISIN SEIKI CO., LTD. ("Defendant") is a corporation organized and existing under the laws of Japan with its registered headquarters in Kari ya, Japan, and U.S. subsidiaries in various locations, including Northville, MI. During the period covered by this Information, the Defendant was engaged in the business of manufacturing and selling variable valve timing ("VVT") devices to automobile manufacturers, including General Motors Company, Nissan Motor Co., Ltd., Volvo Car Corporation, BMW AG, and certain of their subsidiaries, affiliates, and suppliers (collectively, "Automobile Manufacturers") for installation in vehicles manufactured and sold in the United States and elsewhere. Case 1:14-cr-00229-JMS-MJD Document 1 Filed 11/13/14 Page 2 of 6 PageID #: 2 2. Another corporation and other individuals, not made defendants in this Information, participated as co-conspirators in the offense charged in this Information and performed acts and made statements in furtherance thereof. 3. Whenever in this Information reference is made to any act, deed, or transaction of any corporation, the allegation means that the corporation engaged in the act, deed, or transaction by or through its officers, directors, agents, employees, or other representatives while they were actively engaged in the management, direction, control, or transaction of its business or affairs. -

Employee Relations
Employee Relations As a general trading company that has a diverse range of businesses around the world, ITOCHU believes that its human resources are its greatest management asset. Accordingly, ITOCHU will proactively advance efforts to develop and strengthen human resources as the management foundation supporting the growth of its business activities. We will continue to pursue human resources initiatives, such as cultivating industry professionals and creating systems in which diverse human resources can flourish globally. Policies and Tasks for Fiscal 2014 For ITOCHU Corporation, human resources are its greatest management assets as a general trading company. “Brand-new Deal 2014,” our medium-term management plan launched from fiscal 2014, inherits the basic policies of the previous medium-term management plan and continues to outline a variety of initiatives pertaining to human resources, such as cultivating “industry professionals” and “strong human resources.” By executing the medium-term plan and these measures, we intend to further enhance the structure that will support utilization of our human resources, enabling diverse human resources to demonstrate their skills and abilities to the fullest. Fumihiko Kobayashi Managing Executive Officer, General Manager, Human Resources & General Affairs Division 56 Employee Relations Human Resource Development Supporting the “Seeking of New Opportunities” Human Resource Development Supporting the “Seeking of New Opportunities” Human resources are what support the stable, ongoing growth of ITOCHU Corporation. Our human resource development activities are available to employees throughout the Group, both domestically and in overseas blocs. Based on each employee’s work experience and abilities, we strive to help them develop into professionals who play an active role in their business field and to provide them with the skills necessary to manage business on a global level. -

Partners... More Choices
MORE PARTNERS... MORE CHOICES... 3Dconnexion Alcatel Internetworking AT&T Best Data Products Chatsworth Products, 3M Alera Technologies Atek Electronics, Inc. Black Box Inc. 4XEM Alk Associates ATEN Technologies BlackBerry (RIM) Check Point Software Allied Telesis Atlas Sound Blue Coat Cherry Keyboards A Alsoft Software Attachmate BlueSocket Chief Manufacturing Absolute Software Altec Lansing ATTO Technology BMC Software Ciena Access Data Altova Australian Monitor Bogen Cisco Systems Accuscreen Aluratek Autodesk Box.com Citizen America ACD Systems Amazon Avaya Boxtone Corporation Acer America Ambir Technology AVer Information Brady Industries Citrix Systems Acronis AMD Avery Dennison Brenthaven ClearCube Technology Actiontec Electronics American Avnet Integrated Bretford Clearone ActivePDF Microsystems Avocent Brocade Clearswift Adaptec AMPHENOL Axiohm Brooktrout Clickfree ADC Andrea Products Axiom Brother CMS Peripherals Telecommunications Antec AXIS Communications Buffalo Technologies COBY Addonics APC BUSlink Code Scanners Adesso APG B Cognitive Receipt Adobe AppSense Balt, Inc. C Printers ADTRAN Apricorn Barco C2G Commscope Advanced Media APRIVA Bare Bones Software CA CommVault Services APW Products Barracuda Networks Caldera Component One Aec Software ARCHOS Barrister Global Canary Compsee AeroScout Arista Networks Services Canon CompuCover AirWatch Array Networks Battery Biz Capella Technologies Comtrol Aitech Artromick Battery Technology Case Logic Condusiv Aladdin Knowledge Aruba Networks Bay Dynamics Casio Contour Design Systems -

Notice of Convocation the 59Th Ordinary General Meeting of Shareholders
Notice of Convocation The 59th Ordinary General Meeting of Shareholders The following is an English translation of the Notice of Convocation of the 59th Ordinary General Meeting of Shareholders of SECOM CO., LTD. to be held on June 25, 2020, except for the translation of the INSTRUCTION ON ONLINE VOTING and the ACCESS MAP FOR THE PLACE OF THE MEETING in the Notice. The Company provides this translation for your reference and convenience only and without any warranty as to its accuracy or otherwise. [English Translation] 1 Table of Contents Notice of Convocation of The 59th Ordinary General Meeting of Shareholders ····· 3 Reference Document Concerning the General Meeting of Shareholders ··············· 7 Business Report ····················································································· 16 Consolidated Financial Statements ······························································ 49 Non-Consolidated Financial Statements ······················································· 53 Auditors’ Reports ··················································································· 57 (Note) This Table of Contents is for this abridged English translation only, and not the same as that in the original Japanese documents. [English Translation] 2 Stock Exchange Code: 9735 June 3, 2020 Notice of Convocation of The 59th Ordinary General Meeting of Shareholders Dear Shareholders: Secom Co., Ltd. (the “Company”) hereby notifies you as follows that the 59th Ordinary General Meeting of Shareholders of the Company will be held as described below. In order to avoid the risk of COVID-19 infections at the meeting, we strongly recommend that shareholders exercise their voting rights by mail or via the Internet instead of attending the meeting in person. Please exercise your voting rights by mail or via the Internet after studying the Reference Document Concerning the General Meeting of Shareholders attached below and exercise your voting rights on or before 6:00 p.m. -

Water Leaders Summit Keynote Speaker
Water for the Future summi t&expo Water Leaders Summit Keynote speaker Kala Vairavamoorthy IWA Executive Director Professor Kala Vairavamoorthy is an internationally recognised water resource management expert, with particular expertise in urban water issues. He combines a strong engineering background with practical international experience. He has published extensively and has a strong international profile working closely with the World Bank, UN-Habitat, UNESCO, GWP, SIWI and the EU. Prior to joining the International Water Association, he was the Deputy Director General for Research at the International Water Management Institute. Kala has been a member of many International Scientific Committees. Currently he serves on the Stockholm’s World Water Week’s Scientific Program Committee and the Global Water Partnership’s Technical Committee. He was Co-chair of IWA’s Cities of the Future Program and also a member of Singapore International Water Week’s Program Committee. Graham Duxbury Chief Executive Officer, Groundwork, UK Graham Duxbury is Chief Executive of Groundwork UK, a leading NGO promoting community-led solutions to social, economic and environmental challenges in the UK. Graham was appointed Chief Executive in March 2014, having worked for Groundwork UK in a number of national roles for the previous 15 years. His responsibilities have encompassed building national relationships and partnerships, generating income, developing national programmes and leading on policy and strategic communications. Graham joined Groundwork UK in 1998, prior to which he undertook a number of communications roles in the voluntary, public and private sectors. Shan-Shan Guo Vice Chairman of Delta Electronics Foundation ‧Defined corporate’s branding strategy and consolidated its positioning under the “Smarter. -

Ranking of Stocks by Market Capitalization(As of End of Feb.2020)
Ranking of Stocks by Market Capitalization(As of End of Feb.2020) 1st Section Rank Code Issue Market Capitalization \100mil. 1 7203 TOYOTA MOTOR CORPORATION 232,553 2 9984 SoftBank Group Corp. 104,762 3 9437 NTT DOCOMO,INC. 97,638 4 6758 SONY CORPORATION 84,162 5 6861 KEYENCE CORPORATION 83,687 6 8306 Mitsubishi UFJ Financial Group,Inc. 72,242 7 9433 KDDI CORPORATION 72,027 8 9434 SoftBank Corp. 67,618 9 9432 NIPPON TELEGRAPH AND TELEPHONE CORPORATION 66,792 10 4519 CHUGAI PHARMACEUTICAL CO.,LTD. 65,567 11 6098 Recruit Holdings Co.,Ltd. 63,734 12 4502 Takeda Pharmaceutical Company Limited 59,318 13 9983 FAST RETAILING CO.,LTD. 56,685 14 7267 HONDA MOTOR CO.,LTD. 50,710 15 4063 Shin-Etsu Chemical Co.,Ltd. 50,603 16 8316 Sumitomo Mitsui Financial Group,Inc. 47,841 17 7974 Nintendo Co.,Ltd. 47,756 18 4568 DAIICHI SANKYO COMPANY,LIMITED 46,723 19 4661 ORIENTAL LAND CO.,LTD. 44,606 20 7182 JAPAN POST BANK Co.,Ltd. 43,380 21 6367 DAIKIN INDUSTRIES,LTD. 43,161 22 8058 Mitsubishi Corporation 42,773 23 8766 Tokio Marine Holdings,Inc. 41,187 24 8001 ITOCHU Corporation 39,012 25 6981 Murata Manufacturing Co.,Ltd. 38,663 26 6594 NIDEC CORPORATION 38,102 27 4452 Kao Corporation 37,923 28 8411 Mizuho Financial Group,Inc. 37,479 29 8035 Tokyo Electron Limited 36,883 30 6954 FANUC CORPORATION 36,664 31 9022 Central Japan Railway Company 36,626 32 7751 CANON INC. 36,458 33 7741 HOYA CORPORATION 36,355 34 6501 Hitachi,Ltd.