Table of Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Governing Board Meeting 1-2 April 2015 – Association of Arab Universities
Euro-Mediterranean Universities Network TETHYS Governing Board Meeting 1-2 april 2015 – Association of Arab Universities A ce jour (6 mars 2015), le Consortium Téthys regroupe 76 universités réparties dans 17 pays du pourtour méditerranéen ALGERIE JORDANIE The Tethys Network Université Benyoucef Benkhedda - Alger Université Philadelphia - Amman Université Abderrahmane Mira - Béjaïa Université de Technologie Princesse Sumaya - Amman Université d’Oran Université de Mutah Université Badji Mokhtar - Annaba Université de Yarmouk Université du 08 Mai 1945 - Guelma Université Jordanienne de Science et technologie - Irbid Université du 20 Août 1955 - Skikda Université de Jordanie – Amman Université Larbi Ben M’hidi - Oum El Bouaghi Université Mohamed Khider - Biskra Université Constantine I LIBAN Université Constantine II Université Constantine III Université Saint-Esprit de Kaslik-Jounieh Today, the Tethys Network is Université d’Alger 2 Université Saint Joseph - Beyrouth Université de Balamand - Tripoli Université Libanaise – Beyrouth composed of 76 universities from 17 CHYPRE Université de Chypre - Nicosie LIBYE countries of the Mediterranean Université de Zawia CROATIE Université de Split Basin Université de Zagreb MALTE Université de Malte EGYPTE Université d’Alexandrie Université d’Assiut MAROC Université d’Helwan Université Abdelmalek Essaâdi - Tanger Université du Caire Université Chouaïb Doukkali - El Jadida MUST Université Science et Technologie - Le Caire Université Cadi Ayyad - Marrakech Université Française d’Egypte Université Euro-Méditerranéenne -

Report on the International Workshop on the Complex Turbulent Flows Tangier-Morocco, November 27-28, 2017
Report on the International Workshop on the Complex Turbulent Flows Tangier-Morocco, November 27-28, 2017 Otman Ben Mahjoub and Aziz Ouadoud Department of Physics Polydisciplinary Faculty of Larache Abdelmalek Essaadi University 92004 Larache, Morocco 1 Introduction 2 Participants The workshop attracted a total of 86 scientists from In the framework of scientific events, the Polydisci- 25 countries, including 35 PhD students as shown plinary Faculty of Larache and the University Abdel- in table1. Most participants came from European malek Essaadi in collaboration with the ERCOFTAC universities or research institutes. organized the international Workshop on the Com- plex Turbulent Flows held in Tangier, Morocco from ALGERIE 03 BELGUIM 02 the 27th to 28th of November 2017. The object of the BRESIL 01 CANADA 02 workshop was to deal with issues of turbulent and CHILE 01 DENMARK 01 complex flows, especially with the planet’s sudden EGYPT 01 FRANCE 09 climate change in oceans and atmosphere, which GERMANY 02 INDIA 01 have highly negative impacts on the sustainable ITALY 03 MOROCCO 26 development and management of resources. The NETHERLAND 02 POLAND 01 workshop brought together experimentalists, nu- REPUBLIC 01 RUSSIA 03 mericists and theoreticians from around the world CZECH with experts in turbulent flow simulations, compu- SINGAPORE 01 SPAIN 09 tational mathematics, and high-performance com- SWEDEN 01 SWISS 01 puting. Participants presented and discussed recent TUNISIE 08 UK 05 advances in the field of turbulence and topics re- USA 02 lated to the study of chaos, nonlinear dynamical systems of turbulent flows, and their application to atmospheric and oceanic flows. -

Enhanced Antibacterial Efficiency of Cellulosic Fibers: Microencapsulation and Green Grafting Strategies
coatings Article Enhanced Antibacterial Efficiency of Cellulosic Fibers: Microencapsulation and Green Grafting Strategies Dorra Dridi 1,†, Aicha Bouaziz 2,3,†, Sondes Gargoubi 4,*, Abir Zouari 5, Fatma B’chir 6, Aghleb Bartegi 2, Hatem Majdoub 7 and Chedly Boudokhane 5 1 Unit of Analysis and Process Applied to the Environment (UR17ES32) Issat Mahdia, Department of Environmental Sciences & Nutrition, University of Monastir, Monastir 5000, Tunisia; [email protected] 2 Bio-Resources, Integrative Biology & Valorization (BIOLIVAL, LR14ES06), Higher Institute of Biotechnology of Monastir, University of Monastir, Monastir 5000, Tunisia; [email protected] (A.B.); [email protected] (A.B.) 3 Higher School of Health Sciences and Techniques of Sousse, University of Sousse, Sousse 4054, Tunisia 4 Textile Engineering Laboratory—LGTex, Textile Department, University of Monastir, Monastir 5000, Tunisia 5 Research Unity of Applied Chemistry and Environment, Faculty of Science of Monastir, University of Monastir, Monastir 5000, Tunisia; [email protected] (A.Z.); [email protected] (C.B.) 6 Research Department, Institute National de Recherche et d’Analyse Physico-Chimique-Pôle Technologique de Sidi Thabet, Sidi Thabet 2020, Tunisia; [email protected] 7 Laboratory of Advanced Materials and Interfaces, Faculty of Sciences of Monastir, University of Monastir, Monastir 5000, Tunisia; [email protected] * Correspondence: [email protected] † D. Dridi and A. Bouaziz contributed equally to this work as first authors. Abstract: We report an analysis of chemical components of essential oils from barks of Ceylon cinnamon and cloves of Syzygium aromaticum and an investigation of their antibacterial activity. The components Citation: Dridi, D.; Bouaziz, A.; of oils were determined by using Gas Chromatography/Mass Spectrometry (GC-MS) analysis, and Gargoubi, S.; Zouari, A.; B’chir, F.; the antimicrobial activity was assessed by the disk diffusion test. -

Adaptation of AL's Model to Foreign Countries
Programme HERE - Technical Assistance Mission “European experience of employment of graduates: Student support services for employability” Ferghana State University 10-11 July 2018 « The international dimension of AlmaLaurea: adaptation of the Italian model to foreign countries in the framework of Erasmus+ CBHE projects » Enrico Dongiovanni Project Manager for International Relations AlmaLaurea Interuniversity Consortium Outline The Erasmus+ CBHE TUNED Project: TUnisian Network for Employability and Development of graduates skills General overview Objectives Project partnership Working packages Deliverables & Indicators Mobility schedule General overview • Programme: Erasmus+, KA2 – CBHE Structural project • Duration: 36 months Start of the eligibility period: 15/10/2016 End of the eligibility period: 14/10/2019 • Partnership: 8 Tunisian Universities; Tunisian Ministry of Higher Education; 5 EU partners; 4 associated partners • Beneficiary country: Tunisia • Grant awarded: 688.010 € Objectives • Wider objective: To improve the match between universities education and the labour market requirements in Tunisia, enhancing the efficiency of the whole HE system by a certified system of QA and the monitoring of HE programmes and graduates • Specific objectives: To build Tunisian capacities by transferring EU best practices on graduates' employability and monitoring of universities' performances To enhance the empowerment of Tunisian universities To strengthen university/labour market linkages To increase the collaboration among Universities -
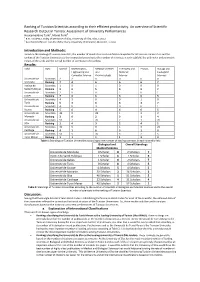
Ranking of Tunisian Scientists According to Their Efficient Productivity
Ranking of Tunisian Scientists according to their efficient productivity. An overview of Scientific Research Output in Tunisia: Assessment of University Performances Houcemeddine Turkia, Manel Turkib a B.Sc. Student, Faculty of Medicine of Sfax, University of Sfax, Sfax, Tunisia b Assistant Professor. Faculty of Pharmacy, University of Monastir, Monastir, Tunisia Introduction and Methods: Based on the Ranking of Tunisian Scientists, the number of scientists in each subfield is computed for all Tunisian Universities and the ranking of the Tunisian Universities is then computed according to the number of scientists in each subfield, the arithmetic and geometric means of the ranks and the overall number of scientists in the ranking. Results: Field Data Overall Mathematics, Medical Sciences Chemistry and Physics Biology and Engineering and and Material Geological Computer Science Pharmacology Science Sciences Université de Scientists 2 2 0 0 0 0 Manouba Ranking 7 4 6 6 6 7 Institut de Scientists 1 0 1 0 0 0 Santé Publique Ranking 9 6 5 6 6 7 Université de Scientists 2 0 0 1 0 1 Gabès Ranking 7 6 6 3 6 5 Université de Scientists 4 3 0 0 1 0 Tunis Ranking 5 3 6 6 4 7 Université de Scientists 4 0 3 0 0 1 Sousse Ranking 5 6 4 6 6 5 Université de Scientists 34 0 28 1 3 2 Monastir Ranking 3 6 2 3 1 4 Université de Scientists 51 2 20 2 1 26 Sfax Ranking 2 4 3 2 4 1 Université de Scientists 31 5 0 1 3 22 Carthage Ranking 4 1 6 3 1 2 Université de Scientists 52 5 35 5 2 5 Tunis Manar Ranking 1 1 1 1 3 3 Table 1: Standings of Tunisian Universities according -

The Internationalisation of Higher Education in the Mediterranean CURRENT and PROSPECTIVE TRENDS
The Internationalisation of Higher Education in the Mediterranean CURRENT AND PROSPECTIVE TRENDS @2021 Union for the Mediterranean Address: Union for the Mediterranean [UfM] ufmsecretariat Palacio de Pedralbes @UfMSecretariat Pere Duran Farell, 11 ES-08034 Barcelona, Spain union-for-the-mediterranean Web: http://www.ufmsecretariat.org @ufmsecretariat Higher Education & Research Phone: +34 93 521 41 51 E-mail: [email protected] Authors: (in alphabetical order): Maria Giulia Ballatore, Raniero Chelli, Federica De Giorgi, Marco Di Donato, Federica Li Muli, Silvia Marchionne, Anne-Laurence Pastorini, Eugenio Platania, Martina Zipoli Coordination: Marco Di Donato, UNIMED; João Lobo, UfM Advisory: Itaf Ben Abdallah, UfM Creative layout: kapusons Download publication: https://ufmsecretariat.org/info-center/publications/ How to cite this publication: UNIMED (2021). The Internationalisation of Higher Education in the Mediterranean, Current and prospective trends. Barcelona: Union for the Mediterranean Disclaimer: Neither the Union for the Mediterranean nor any person acting on behalf of the Union for the Mediterranean is responsible for the use that might be made of the information contained in this report. The information and views set out in this report do not reflect the official opinion of the Union for the Mediterranean. Responsibility for the information and views expressed therein lies entirely with the authors. All care has been taken by the authors to ensure that, where necessary, permission was obtained to use any parts of manuscripts including illustrations, maps and graphs on which intellectual property rights already exist from the titular holder(s) of such rights or from her/his or their legal representative. Copyright: © Union for the Mediterranean, 2021 Reproduction is authorised provided the source is acknowledged. -

Bibliometric Study of African Publications in Dental Medicine in Indexed Journals Between 2008 and 2018
Research Article ISSN 2639-9490 Research Article Oral Health & Dental Science Bibliometric Study of African Publications in Dental Medicine in Indexed Journals between 2008 and 2018 Bennani A1*, Hamza M2, Kalali C3 and Jari A4 1Professor of Department of fixed prosthodontics, Faculty of Dentistry, University Hassan II, Casablanca, Morocco. *Correspondence: 2Professor of Department of Epidemiology and biostatistics, Bennani A, Professor of Department of fixed prosthodontics, Faculty of Dentistry, University Hassan II, Casablanca, Morocco. Faculty of Dentistry, University Hassan II, Casablanca, Morocco. 3Dentist, Private practice, Casablanca, Morocco. Received: 20 December 2020; Accepted: 07 January 2021 4Dentist, Private practice, Casablanca, Morocco. Citation: Bennani A, Hamza M, Kalali C, et al. Bibliometric Study of African Publications in Dental Medicine in Indexed Journals between 2008 and 2018. Oral Health Dental Sci. 2021; 4(3); 1-12. ABSTRACT Introduction: The objective of this work is to make a bibliometric analysis of publications in odontology of African universities between January 2008 and December 2018 based on publications published in indexed journals on Pubmed. Material and Methods: Our work is a comprehensive retrospective descriptive study intended to carry out a bibliometric analysis of articles in odontology published between January 1, 2008 and December 31, 2018 by professor researchers from African universities. For each selected article, we determined the authors, the title, their affiliations, the year of publication. Results: Based on our sample of 19 African countries (Morocco, Algeria, Tunisia, Egypt, Nigeria, Cameroon, Côte d 'Ivoire, Ethiopia, Ghana, Guinea, Kenya, Libya, Madagascar, Mali, South Africa, DRC Congo, Senegal, Sudan, Zimbabwe) that included 66 faculties; the results of our study showed: • In terms of the number of global publications, Egypt, Nigeria, Morocco and South Africa are the leading countries. -

Managerial Optimism Level and Investment Decision: Decision Tree Analysis
International Journal of Social Science Studies Vol. 6, No. 1; January 2018 ISSN 2324-8033 E-ISSN 2324-8041 Published by Redfame Publishing URL: http://ijsss.redfame.com Managerial Optimism Level and Investment Decision: Decision Tree Analysis Mohamed Ali Azouzi1& Anis Jarboui2 1Doctor and HDR Financial and Accounting, Assistant Professor in Finance and Accounting Methods, Faculty of Management Mahdia, Tunisia University of Monastir, Tunisia 2Doctor and HDR Financial and Accounting, Associate Professor of Universities, Higher Institute of Business Administration (ISAAS) University of Sfax, Tunisia Correspondence: Mohamed Ali Azouzi, Doctor and HDR Financial and Accounting, Assistant Professor in Finance and Accounting Methods, Faculty of Management Mahdia, Tunisia University of Monastir, Tunisia. Received: October 12, 2017 Accepted: December 18, 2017 Available online: December 19, 2017 doi:10.11114/ijsss.v6i1.2694 URL: https://doi.org/10.11114/ijsss.v6i1.2694 Abstract This paper deals with the relationship existing between the emotional aspect and decision-making. More specifically, it examines the links between managerial optimism, and effectiveness of the investment decision. We introduce an approach based Decision Tree analysis with a series of semi-directive interviews. CEO optimism level was measured using a questionnaire with several items. As for the selected sample was composed of 100 Tunisian managers. The originality of this research paper is guaranteed since it traits the behavioral corporate policy choice in emergent markets. In the best of our knowledge, this is the first study in the Tunisian context that explores such area of research. Our results show that Tunisian optimistic leader who seeks the pioneering advantage for him and his company is encouraged to adjust its specific investment decision (investment, overinvestment or under-investment in the short term or long term ...) to ensure that advantage pioneer. -

Screening of Antioxidant Potentials and Bioactive Properties of the Extracts Obtained from Two Centaurea L. Species (C. Kroumirensis Coss. and C. Sicula L. Subsp Sicula)
applied sciences Article Screening of Antioxidant Potentials and Bioactive Properties of the Extracts Obtained from Two Centaurea L. Species (C. kroumirensis Coss. and C. sicula L. subsp sicula) Nedra Dhouibi 1, Simona Manuguerra 2 , Rosaria Arena 2 , Abdelkarim Mahdhi 3, Concetta Maria Messina 2,* , Andrea Santulli 2,4 and Hatem Dhaouadi 1 1 UR13ES63-Chimie Appliquée et Environnement, Département de Chimie, Faculté des Sciences, Université de Monastir, Bvd de l’Environnement, Monastir 5000, Tunisie; [email protected] (N.D.); [email protected] (H.D.) 2 Laboratorio di Biochimica Marina ed Ecotossicologia, Dipartimento di Scienze della terra e del Mare DiSTeM, Università degli Studi di Palermo, Via G. Barlotta 4, 91100 Trapani, Italy; [email protected] (S.M.); [email protected] (R.A.); [email protected] (A.S.) 3 Laboratory of Analysis, Treatment and Valorization of Pollutants of the Environment and Products, Faculty of Pharmacy, University of Monastir, Monastir 5000, Tunisia; [email protected] 4 Istituto di Biologia Marina, Consorzio Universitario della Provincia di Trapani, Via G. Barlotta 4, 91100 Trapani, Italy * Correspondence: [email protected] Received: 28 February 2020; Accepted: 18 March 2020; Published: 26 March 2020 Abstract: Herbal medicines, dietary supplements, or infusions with health promoting effects can note strong consumer demand. Hence, researchers and scientists have been increasingly focusing on the promotion of medicinal plants. In this respect, the present study has the evaluation of the biological properties of different extracts (hexane, chloroform, methanol, ultrasonic, essential oil, and supercritical) obtained from two Centaurea species (C. kroumirensis (Coss.) and C. sicula L. -

Sagesse Amélioration De La Gouvernance Dans Le Système De L’Enseignement Supérieur En Tunisie
sAGESSE Amélioration de la Gouvernance dans le système de l’EnSeignement Supérieur en Tunisie Objectives: * To contribute to the modernisation of the HE management and to the improvement of governance in Tunisia, providing an operational support methodologically rigorous and based on international best practices. * To create an integrated definition and control system for quality in university education in every university of the consortium. * To support the creation of new decision and management procedures to define the internal/external staff of the HEIs charged of the management and control of processes. * Development of skills and competencies by academic, administrative and managerial staff. * To promote the creation of an e-administration department in every university of the consortium for an innovative, effective and more autonomous management. Activities: * Research and analysis about best practices concerning governance in Tunisia. * Training seminars, study visits and best practice exchange to train the administrative and managerial staff. * Design of a Quality Handbook about financial management procedures. * In each university of the consortium: definition of a strategical project and related Action Plans and creation of offices to put them in place. * Information seminars about good governance addressed to the Tunisian Ministry for Higher Education and Scientific Research and the Tunisian National Body for Evaluation, Quality Assurance and Accreditation. * Elaboration of a White Book of recommendation addressed to interest groups and national, regional and international authorities. Follow the project IN ACTION Results: * Development of skills about governance and quality assessment by managerial and academic staff of the universities. * Development of skills about financial management by administrative staff of the universities. -

Scientific Research and Essays
Scientific Research and Essays http://www.academicjournals.org/SRE/Editors.htm OPEN ACCESS JOURNALS SRE Home Editors About SRE Dr. NJ Tonukari Publication Ethics Editor-in-Chief Submit Manuscripts Scientific Research and Essays Academic Journals Instructions for Authors Editors Prof. Sivakumar Manickam Chemical and Nanopharmaceutical Call For Paper Process Engineering, Archive Department of Chemical and Environmental Engineering Conferences Head, Manufacturing and Industrial Associations Processes Research Division, Faculty of Engineering, E-books Director, Centre for Nanotechnology and Advanced Materials (CENTAM) Related Journals The University of Nottingham Malaysia ■Journal of Cell & Animal Biology Campus, African Journal of Environmental Jalan Broga, 43500 Semenyih, ■ Science & Technology Selangor, Malaysia. Biotechnology & Molecular Biology ■ Reviews Associate Editors African Journal of Agricultural ■ Research Prof. N. Mohamed El Sawi African Journal of Microbiology ■ Mahmoud Research Department of Biochemistry, Faculty of African Journal of Pure & Applied ■ science, Chemistry King AbdulAziz university, ■African Journal of Food Science Saudia Arabia. ■African Journal of Biotechnology African Journal of Pharmacy & ■ Prof. Ali Delice Pharmacology Science and Mathematics Education ■African Journal of Plant Science Journal of Medicinal Plant Department, ■ Research Atatürk Faculty of Education, ■International Journal of Physical Marmara University, Sciences Turkey. ■African Journal of Biochemistry Research Prof. Mira Grdisa Rudjer Boskovic -

Molecular Phylogeny of 42 Species of Culicoides (Diptera, Ceratopogonidae) from Three Continents
Parasite 2017, 24,23 Ó D. Augot et al., published by EDP Sciences, 2017 DOI: 10.1051/parasite/2017020 Available online at: www.parasite-journal.org RESEARCH ARTICLE OPEN ACCESS Molecular phylogeny of 42 species of Culicoides (Diptera, Ceratopogonidae) from three continents Denis Augot1, Bruno Mathieu2, Leila Hadj-Henni1, Véronique Barriel3, Sonia Zapata Mena4, Sylvia Smolis1, Darine Slama5, Fano José Randrianambinintsoa6, Gabriel Trueba4, Matthieu Kaltenbach7, Nil Rahola8,9, and Jérôme Depaquit1 1 USC Vecpar, ANSES-LSA, Université de Reims Champagne-Ardenne, SFR Cap Santé, Faculté de Pharmacie, 51 rue Cognacq-Jay, EA 4688, Reims 51096, France 2 Institut de Parasitologie et de Pathologie Tropicale de Strasbourg, Université de Strasbourg, Faculté de Médecine, 3 rue Koeberlé, EA7292, Strasbourg 67000, France 3 Muséum National d’Histoire Naturelle, CR2P-UMR 7207 CNRS, MNHN, UPMC, 8 rue Buffon, CP 38, 75005 Paris, France 4 Instituto de Microbiologia, Colegio de Ciencias Biologicas y Ambientales, Universidad San Francisco de Quito, Cumbayá, EC170157 Quito, Pichincha, Ecuador 5 Laboratory of Medical and Molecular Parasitology-Mycology, Faculty of Pharmacy, University of Monastir, 99UR/08-05, 5000 Monastir, Tunisia 6 Medical Entomology Unit, Institut Pasteur de Madagascar, Ambatofotsikely, BP 1274, Antananarivo 101, Madagascar 7 Laboratoire de Pharmacologie, Université de Reims Champagne-Ardenne, UFR Pharmacie, 51 rue Cognacq-Jay, 51100 Reims, France 8 Unité MIVEGEC, UMR 224-5290 IRD-CNRS-UM, Centre IRD de Montpellier, BP 64501, 911 avenue Agropolis, 34394 Montpellier, France 9 Centre International de Recherches Médicales de Franceville (CIRMF), BP 769, Franceville, Gabon Received 28 October 2016, Accepted 19 May 2017, Published online 22 June 2017 Abstract – The genus Culicoides includes vectors of important animal diseases such as bluetongue and Schmallenberg virus (BTV and SBV).