Algorithmic Factorization of Polynomials Over Number Fields
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lesson 21 –Resultants
Lesson 21 –Resultants Elimination theory may be considered the origin of algebraic geometry; its history can be traced back to Newton (for special equations) and to Euler and Bezout. The classical method for computing varieties has been through the use of resultants, the focus of today’s discussion. The alternative of using Groebner bases is more recent, becoming fashionable with the onset of computers. Calculations with Groebner bases may reach their limitations quite quickly, however, so resultants remain useful in elimination theory. The proof of the Extension Theorem provided in the textbook (see pages 164-165) also makes good use of resultants. I. The Resultant Let be a UFD and let be the polynomials . The definition and motivation for the resultant of lies in the following very simple exercise. Exercise 1 Show that two polynomials and in have a nonconstant common divisor in if and only if there exist nonzero polynomials u, v such that where and . The equation can be turned into a numerical criterion for and to have a common factor. Actually, we use the equation instead, because the criterion turns out to be a little cleaner (as there are fewer negative signs). Observe that iff so has a solution iff has a solution . Exercise 2 (to be done outside of class) Given polynomials of positive degree, say , define where the l + m coefficients , ,…, , , ,…, are treated as unknowns. Substitute the formulas for f, g, u and v into the equation and compare coefficients of powers of x to produce the following system of linear equations with unknowns ci, di and coefficients ai, bj, in R. -

A Survey of Some Arithmetic Applications of Ergodic Theory in Negative Curvature
A survey of some arithmetic applications of ergodic theory in negative curvature Jouni Parkkonen Frédéric Paulin January 12, 2015 Abstract This paper is a survey of some arithmetic applications of techniques in the geometry and ergodic theory of negatively curved Riemannian manifolds, focusing on the joint works of the authors. We describe Diophantine approximation results of real numbers by quadratic irrational ones, and we discuss various results on the equidistribution in R, C and in the Heisenberg groups of arithmetically defined points. We explain how these results are consequences of equidistribution and counting properties of common perpendiculars between locally convex subsets in negatively curved orbifolds, proven using dynamical and ergodic properties of their geodesic flows. This exposition is based on lectures at the conference “Chaire Jean Morlet: Géométrie et systèmes dynamiques”, at the CIRM, Luminy, 2014. We thank B. Hasselblatt for his strong encouragements to write this survey. 1 1 Introduction For several decades, tools from dynamical systems, and in particular ergodic theory, have been used to derive arithmetic and number theoretic, in particular Diophantine approxi- mation results, see for instance the works of Furstenberg, Margulis, Sullivan, Dani, Klein- bock, Clozel, Oh, Ullmo, Lindenstrauss, Einsiedler, Michel, Venkatesh, Marklof, Green- Tao, Elkies-McMullen, Ratner, Mozes, Shah, Gorodnik, Ghosh, Weiss, Hersonsky-Paulin, Parkkonen-Paulin and many others, and the references [Kle2, Lin, Kle1, AMM, Ath, GorN, EiW, PaP5]. arXiv:1501.02072v1 [math.NT] 9 Jan 2015 In Subsection 2.2 of this survey, we introduce a general framework of Diophantine approximation in measured metric spaces, in which most of our arithmetic corollaries are inserted (see the end of Subsection 2.2 for references concerning this framework). -

K-Quasiderivations
K-QUASIDERIVATIONS CALEB EMMONS, MIKE KREBS, AND ANTHONY SHAHEEN Abstract. A K-quasiderivation is a map which satisfies both the Product Rule and the Chain Rule. In this paper, we discuss sev- eral interesting families of K-quasiderivations. We first classify all K-quasiderivations on the ring of polynomials in one variable over an arbitrary commutative ring R with unity, thereby extend- ing a previous result. In particular, we show that any such K- quasiderivation must be linear over R. We then discuss two previ- ously undiscovered collections of (mostly) nonlinear K-quasiderivations on the set of functions defined on some subset of a field. Over the reals, our constructions yield a one-parameter family of K- quasiderivations which includes the ordinary derivative as a special case. 1. Introduction In the middle half of the twientieth century|perhaps as a reflection of the mathematical zeitgeist|Lausch, Menger, M¨uller,N¨obauerand others formulated a general axiomatic framework for the concept of the derivative. Their starting point was (usually) a composition ring, by which is meant a commutative ring R with an additional operation ◦ subject to the restrictions (f + g) ◦ h = (f ◦ h) + (g ◦ h), (f · g) ◦ h = (f ◦ h) · (g ◦ h), and (f ◦ g) ◦ h = f ◦ (g ◦ h) for all f; g; h 2 R. (See [1].) In M¨uller'sparlance [9], a K-derivation is a map D from a composition ring to itself such that D satisfies Additivity: D(f + g) = D(f) + D(g) (1) Product Rule: D(f · g) = f · D(g) + g · D(f) (2) Chain Rule D(f ◦ g) = [(D(f)) ◦ g] · D(g) (3) 2000 Mathematics Subject Classification. -

Gaussian Integers1
FORMALIZED MATHEMATICS Vol. 21, No. 2, Pages 115–125, 2013 DOI: 10.2478/forma-2013-0013 degruyter.com/view/j/forma Gaussian Integers1 Yuichi Futa Hiroyuki Okazaki Japan Advanced Institute Shinshu University of Science and Technology Nagano, Japan Ishikawa, Japan Daichi Mizushima2 Yasunari Shidama Shinshu University Shinshu University Nagano, Japan Nagano, Japan Summary. Gaussian integer is one of basic algebraic integers. In this artic- le we formalize some definitions about Gaussian integers [27]. We also formalize ring (called Gaussian integer ring), Z-module and Z-algebra generated by Gaus- sian integer mentioned above. Moreover, we formalize some definitions about Gaussian rational numbers and Gaussian rational number field. Then we prove that the Gaussian rational number field and a quotient field of the Gaussian integer ring are isomorphic. MSC: 11R04 03B35 Keywords: formalization of Gaussian integers; algebraic integers MML identifier: GAUSSINT, version: 8.1.02 5.17.1179 The notation and terminology used in this paper have been introduced in the following articles: [5], [1], [2], [6], [12], [11], [7], [8], [18], [24], [23], [16], [19], [21], [3], [9], [20], [14], [4], [28], [25], [22], [26], [15], [17], [10], and [13]. 1. Gaussian Integer Ring Now we state the proposition: (1) Let us consider natural numbers x, y. If x + y = 1, then x = 1 and y = 0 or x = 0 and y = 1. Proof: x ¬ 1. 1This work was supported by JSPS KAKENHI 21240001 and 22300285. 2This research was presented during the 2012 International Symposium on Information Theory and its Applications (ISITA2012) in Honolulu, USA. c 2013 University of Białystok CC-BY-SA License ver. -

January 10, 2010 CHAPTER SIX IRREDUCIBILITY and FACTORIZATION §1. BASIC DIVISIBILITY THEORY the Set of Polynomials Over a Field
January 10, 2010 CHAPTER SIX IRREDUCIBILITY AND FACTORIZATION §1. BASIC DIVISIBILITY THEORY The set of polynomials over a field F is a ring, whose structure shares with the ring of integers many characteristics. A polynomials is irreducible iff it cannot be factored as a product of polynomials of strictly lower degree. Otherwise, the polynomial is reducible. Every linear polynomial is irreducible, and, when F = C, these are the only ones. When F = R, then the only other irreducibles are quadratics with negative discriminants. However, when F = Q, there are irreducible polynomials of arbitrary degree. As for the integers, we have a division algorithm, which in this case takes the form that, if f(x) and g(x) are two polynomials, then there is a quotient q(x) and a remainder r(x) whose degree is less than that of g(x) for which f(x) = q(x)g(x) + r(x) . The greatest common divisor of two polynomials f(x) and g(x) is a polynomial of maximum degree that divides both f(x) and g(x). It is determined up to multiplication by a constant, and every common divisor divides the greatest common divisor. These correspond to similar results for the integers and can be established in the same way. One can determine a greatest common divisor by the Euclidean algorithm, and by going through the equations in the algorithm backward arrive at the result that there are polynomials u(x) and v(x) for which gcd (f(x), g(x)) = u(x)f(x) + v(x)g(x) . -

Applications of Hyperbolic Geometry to Continued Fractions and Diophantine Approximation
Applications of hyperbolic geometry to continued fractions and Diophantine approximation Robert Hines University of Colorado, Boulder April 1, 2019 A picture Summary Our goal is to generalize features of the preceding picture to some nearby settings: H2 H3 (H2)r × (H3)s Hn P 1(R) P 1(C) P 1(R)r × P 1(C)s Sn−1 SL2(R) SL2(C) SL2(F ⊗ R) SVn−1(R) SL2(Z) SL2(O) " SV (O) ideal right-angled triangles ideal polyhedra horoball bounded geodesic " neighborhoods trajectories quad. quad./Herm. " " forms forms closed geodesics closed surfaces aniso. subgroups " Ingredients Ingredients Upper half-space models in dimensions two and three Hyperbolic two-space: 2 H = fz = x + iy 2 C : y > 0g; 2 1 @H = P (R); 2 Isom(H ) = P GL2(R); az + b az¯ + b g · z = ; (det g = ±1); cz + d cz¯ + d + ∼ Stab (i) = SO2(R)={±1g = SO2(R): Hyperbolic three-space: 3 H = fζ = z + jt 2 H : t > 0; z 2 Cg; 3 1 @H = P (C); 3 Isom(H ) = P SL2(C) o hτi; g · ζ = (aζ + b)(cζ + d)−1; τ(ζ) =z ¯ + jt; + ∼ Stab (j) = SU2(C)={±1g = SO3(R): Binary quadratic and Hermitian forms Hyperbolic two- and three-space are the Riemannian symmetric spaces associated to G = SL2(R), SL2(C). The points can be identified with roots of binary forms: 2 SL2(R)=SO2(R) ! fdet. 1 pos. def. bin. quadratic formsg ! H p −b + b2 − 4ac g 7! ggt = ax2 + bxy + cy2 = Q 7! =: Z(Q) 2a 3 SL2(C)=SU2(C) ! fdet. -
![2.4 Algebra of Polynomials ([1], P.136-142) in This Section We Will Give a Brief Introduction to the Algebraic Properties of the Polynomial Algebra C[T]](https://docslib.b-cdn.net/cover/8740/2-4-algebra-of-polynomials-1-p-136-142-in-this-section-we-will-give-a-brief-introduction-to-the-algebraic-properties-of-the-polynomial-algebra-c-t-408740.webp)
2.4 Algebra of Polynomials ([1], P.136-142) in This Section We Will Give a Brief Introduction to the Algebraic Properties of the Polynomial Algebra C[T]
2.4 Algebra of polynomials ([1], p.136-142) In this section we will give a brief introduction to the algebraic properties of the polynomial algebra C[t]. In particular, we will see that C[t] admits many similarities to the algebraic properties of the set of integers Z. Remark 2.4.1. Let us first recall some of the algebraic properties of the set of integers Z. - division algorithm: given two integers w, z 2 Z, with jwj ≤ jzj, there exist a, r 2 Z, with 0 ≤ r < jwj such that z = aw + r. Moreover, the `long division' process allows us to determine a, r. Here r is the `remainder'. - prime factorisation: for any z 2 Z we can write a1 a2 as z = ±p1 p2 ··· ps , where pi are prime numbers. Moreover, this expression is essentially unique - it is unique up to ordering of the primes appearing. - Euclidean algorithm: given integers w, z 2 Z there exists a, b 2 Z such that aw + bz = gcd(w, z), where gcd(w, z) is the `greatest common divisor' of w and z. In particular, if w, z share no common prime factors then we can write aw + bz = 1. The Euclidean algorithm is a process by which we can determine a, b. We will now introduce the polynomial algebra in one variable. This is simply the set of all polynomials with complex coefficients and where we make explicit the C-vector space structure and the multiplicative structure that this set naturally exhibits. Definition 2.4.2. - The C-algebra of polynomials in one variable, is the quadruple (C[t], α, σ, µ)43 where (C[t], α, σ) is the C-vector space of polynomials in t with C-coefficients defined in Example 1.2.6, and µ : C[t] × C[t] ! C[t];(f , g) 7! µ(f , g), is the `multiplication' function. -

Some Properties of the Discriminant Matrices of a Linear Associative Algebra*
570 R. F. RINEHART [August, SOME PROPERTIES OF THE DISCRIMINANT MATRICES OF A LINEAR ASSOCIATIVE ALGEBRA* BY R. F. RINEHART 1. Introduction. Let A be a linear associative algebra over an algebraic field. Let d, e2, • • • , en be a basis for A and let £»•/*., (hjik = l,2, • • • , n), be the constants of multiplication corre sponding to this basis. The first and second discriminant mat rices of A, relative to this basis, are defined by Ti(A) = \\h(eres[ CrsiCij i, j=l T2(A) = \\h{eres / ,J CrsiC j II i,j=l where ti(eres) and fa{erea) are the first and second traces, respec tively, of eres. The first forms in terms of the constants of multi plication arise from the isomorphism between the first and sec ond matrices of the elements of A and the elements themselves. The second forms result from direct calculation of the traces of R(er)R(es) and S(er)S(es), R{ei) and S(ei) denoting, respectively, the first and second matrices of ei. The last forms of the dis criminant matrices show that each is symmetric. E. Noetherf and C. C. MacDuffeeJ discovered some of the interesting properties of these matrices, and shed new light on the particular case of the discriminant matrix of an algebraic equation. It is the purpose of this paper to develop additional properties of these matrices, and to interpret them in some fa miliar instances. Let A be subjected to a transformation of basis, of matrix M, 7 J rH%j€j 1,2, *0). -

Arxiv:2004.03341V1
RESULTANTS OVER PRINCIPAL ARTINIAN RINGS CLAUS FIEKER, TOMMY HOFMANN, AND CARLO SIRCANA Abstract. The resultant of two univariate polynomials is an invariant of great impor- tance in commutative algebra and vastly used in computer algebra systems. Here we present an algorithm to compute it over Artinian principal rings with a modified version of the Euclidean algorithm. Using the same strategy, we show how the reduced resultant and a pair of B´ezout coefficient can be computed. Particular attention is devoted to the special case of Z/nZ, where we perform a detailed analysis of the asymptotic cost of the algorithm. Finally, we illustrate how the algorithms can be exploited to improve ideal arithmetic in number fields and polynomial arithmetic over p-adic fields. 1. Introduction The computation of the resultant of two univariate polynomials is an important task in computer algebra and it is used for various purposes in algebraic number theory and commutative algebra. It is well-known that, over an effective field F, the resultant of two polynomials of degree at most d can be computed in O(M(d) log d) ([vzGG03, Section 11.2]), where M(d) is the number of operations required for the multiplication of poly- nomials of degree at most d. Whenever the coefficient ring is not a field (or an integral domain), the method to compute the resultant is given directly by the definition, via the determinant of the Sylvester matrix of the polynomials; thus the problem of determining the resultant reduces to a problem of linear algebra, which has a worse complexity. -

Hk Hk38 21 56 + + + Y Xyx X 8 40
New York City College of Technology [MODULE 5: FACTORING. SOLVE QUADRATIC EQUATIONS BY FACTORING] MAT 1175 PLTL Workshops Name: ___________________________________ Points: ______ 1. The Greatest Common Factor The greatest common factor (GCF) for a polynomial is the largest monomial that divides each term of the polynomial. GCF contains the GCF of the numerical coefficients and each variable raised to the smallest exponent that appear. a. Factor 8x4 4x3 16x2 4x 24 b. Factor 9 ba 43 3 ba 32 6ab 2 2. Factoring by Grouping a. Factor 56 21k 8h 3hk b. Factor 5x2 40x xy 8y 3. Factoring Trinomials with Lead Coefficients of 1 Steps to factoring trinomials with lead coefficient of 1 1. Write the trinomial in descending powers. 2. List the factorizations of the third term of the trinomial. 3. Pick the factorization where the sum of the factors is the coefficient of the middle term. 4. Check by multiplying the binomials. a. Factor x2 8x 12 b. Factor y 2 9y 36 1 Prepared by Profs. Ghezzi, Han, and Liou-Mark Supported by BMI, NSF STEP #0622493, and Perkins New York City College of Technology [MODULE 5: FACTORING. SOLVE QUADRATIC EQUATIONS BY FACTORING] MAT 1175 PLTL Workshops c. Factor a2 7ab 8b2 d. Factor x2 9xy 18y 2 e. Factor x3214 x 45 x f. Factor 2xx2 24 90 4. Factoring Trinomials with Lead Coefficients other than 1 Method: Trial-and-error 1. Multiply the resultant binomials. 2. Check the sum of the inner and the outer terms is the original middle term bx . a. Factor 2h2 5h 12 b. -
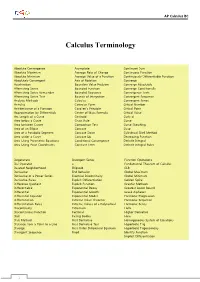
Calculus Terminology
AP Calculus BC Calculus Terminology Absolute Convergence Asymptote Continued Sum Absolute Maximum Average Rate of Change Continuous Function Absolute Minimum Average Value of a Function Continuously Differentiable Function Absolutely Convergent Axis of Rotation Converge Acceleration Boundary Value Problem Converge Absolutely Alternating Series Bounded Function Converge Conditionally Alternating Series Remainder Bounded Sequence Convergence Tests Alternating Series Test Bounds of Integration Convergent Sequence Analytic Methods Calculus Convergent Series Annulus Cartesian Form Critical Number Antiderivative of a Function Cavalieri’s Principle Critical Point Approximation by Differentials Center of Mass Formula Critical Value Arc Length of a Curve Centroid Curly d Area below a Curve Chain Rule Curve Area between Curves Comparison Test Curve Sketching Area of an Ellipse Concave Cusp Area of a Parabolic Segment Concave Down Cylindrical Shell Method Area under a Curve Concave Up Decreasing Function Area Using Parametric Equations Conditional Convergence Definite Integral Area Using Polar Coordinates Constant Term Definite Integral Rules Degenerate Divergent Series Function Operations Del Operator e Fundamental Theorem of Calculus Deleted Neighborhood Ellipsoid GLB Derivative End Behavior Global Maximum Derivative of a Power Series Essential Discontinuity Global Minimum Derivative Rules Explicit Differentiation Golden Spiral Difference Quotient Explicit Function Graphic Methods Differentiable Exponential Decay Greatest Lower Bound Differential -

Subclass Discriminant Nonnegative Matrix Factorization for Facial Image Analysis
Pattern Recognition 45 (2012) 4080–4091 Contents lists available at SciVerse ScienceDirect Pattern Recognition journal homepage: www.elsevier.com/locate/pr Subclass discriminant Nonnegative Matrix Factorization for facial image analysis Symeon Nikitidis b,a, Anastasios Tefas b, Nikos Nikolaidis b,a, Ioannis Pitas b,a,n a Informatics and Telematics Institute, Center for Research and Technology, Hellas, Greece b Department of Informatics, Aristotle University of Thessaloniki, Greece article info abstract Article history: Nonnegative Matrix Factorization (NMF) is among the most popular subspace methods, widely used in Received 4 October 2011 a variety of image processing problems. Recently, a discriminant NMF method that incorporates Linear Received in revised form Discriminant Analysis inspired criteria has been proposed, which achieves an efficient decomposition of 21 March 2012 the provided data to its discriminant parts, thus enhancing classification performance. However, this Accepted 26 April 2012 approach possesses certain limitations, since it assumes that the underlying data distribution is Available online 16 May 2012 unimodal, which is often unrealistic. To remedy this limitation, we regard that data inside each class Keywords: have a multimodal distribution, thus forming clusters and use criteria inspired by Clustering based Nonnegative Matrix Factorization Discriminant Analysis. The proposed method incorporates appropriate discriminant constraints in the Subclass discriminant analysis NMF decomposition cost function in order to address the problem of finding discriminant projections Multiplicative updates that enhance class separability in the reduced dimensional projection space, while taking into account Facial expression recognition Face recognition subclass information. The developed algorithm has been applied for both facial expression and face recognition on three popular databases.