Scheduling and Sorting Algorithms for Robotic Warehousing Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

An Evolutionary Approach for Sorting Algorithms
ORIENTAL JOURNAL OF ISSN: 0974-6471 COMPUTER SCIENCE & TECHNOLOGY December 2014, An International Open Free Access, Peer Reviewed Research Journal Vol. 7, No. (3): Published By: Oriental Scientific Publishing Co., India. Pgs. 369-376 www.computerscijournal.org Root to Fruit (2): An Evolutionary Approach for Sorting Algorithms PRAMOD KADAM AND Sachin KADAM BVDU, IMED, Pune, India. (Received: November 10, 2014; Accepted: December 20, 2014) ABstract This paper continues the earlier thought of evolutionary study of sorting problem and sorting algorithms (Root to Fruit (1): An Evolutionary Study of Sorting Problem) [1]and concluded with the chronological list of early pioneers of sorting problem or algorithms. Latter in the study graphical method has been used to present an evolution of sorting problem and sorting algorithm on the time line. Key words: Evolutionary study of sorting, History of sorting Early Sorting algorithms, list of inventors for sorting. IntroDUCTION name and their contribution may skipped from the study. Therefore readers have all the rights to In spite of plentiful literature and research extent this study with the valid proofs. Ultimately in sorting algorithmic domain there is mess our objective behind this research is very much found in documentation as far as credential clear, that to provide strength to the evolutionary concern2. Perhaps this problem found due to lack study of sorting algorithms and shift towards a good of coordination and unavailability of common knowledge base to preserve work of our forebear platform or knowledge base in the same domain. for upcoming generation. Otherwise coming Evolutionary study of sorting algorithm or sorting generation could receive hardly information about problem is foundation of futuristic knowledge sorting problems and syllabi may restrict with some base for sorting problem domain1. -

Sorting Algorithm 1 Sorting Algorithm
Sorting algorithm 1 Sorting algorithm In computer science, a sorting algorithm is an algorithm that puts elements of a list in a certain order. The most-used orders are numerical order and lexicographical order. Efficient sorting is important for optimizing the use of other algorithms (such as search and merge algorithms) that require sorted lists to work correctly; it is also often useful for canonicalizing data and for producing human-readable output. More formally, the output must satisfy two conditions: 1. The output is in nondecreasing order (each element is no smaller than the previous element according to the desired total order); 2. The output is a permutation, or reordering, of the input. Since the dawn of computing, the sorting problem has attracted a great deal of research, perhaps due to the complexity of solving it efficiently despite its simple, familiar statement. For example, bubble sort was analyzed as early as 1956.[1] Although many consider it a solved problem, useful new sorting algorithms are still being invented (for example, library sort was first published in 2004). Sorting algorithms are prevalent in introductory computer science classes, where the abundance of algorithms for the problem provides a gentle introduction to a variety of core algorithm concepts, such as big O notation, divide and conquer algorithms, data structures, randomized algorithms, best, worst and average case analysis, time-space tradeoffs, and lower bounds. Classification Sorting algorithms used in computer science are often classified by: • Computational complexity (worst, average and best behaviour) of element comparisons in terms of the size of the list . For typical sorting algorithms good behavior is and bad behavior is . -

Evaluation of Sorting Algorithms, Mathematical and Empirical Analysis of Sorting Algorithms
International Journal of Scientific & Engineering Research Volume 8, Issue 5, May-2017 86 ISSN 2229-5518 Evaluation of Sorting Algorithms, Mathematical and Empirical Analysis of sorting Algorithms Sapram Choudaiah P Chandu Chowdary M Kavitha ABSTRACT:Sorting is an important data structure in many real life applications. A number of sorting algorithms are in existence till date. This paper continues the earlier thought of evolutionary study of sorting problem and sorting algorithms concluded with the chronological list of early pioneers of sorting problem or algorithms. Latter in the study graphical method has been used to present an evolution of sorting problem and sorting algorithm on the time line. An extensive analysis has been done compared with the traditional mathematical methods of ―Bubble Sort, Selection Sort, Insertion Sort, Merge Sort, Quick Sort. Observations have been obtained on comparing with the existing approaches of All Sorts. An “Empirical Analysis” consists of rigorous complexity analysis by various sorting algorithms, in which comparison and real swapping of all the variables are calculatedAll algorithms were tested on random data of various ranges from small to large. It is an attempt to compare the performance of various sorting algorithm, with the aim of comparing their speed when sorting an integer inputs.The empirical data obtained by using the program reveals that Quick sort algorithm is fastest and Bubble sort is slowest. Keywords: Bubble Sort, Insertion sort, Quick Sort, Merge Sort, Selection Sort, Heap Sort,CPU Time. Introduction In spite of plentiful literature and research in more dimension to student for thinking4. Whereas, sorting algorithmic domain there is mess found in this thinking become a mark of respect to all our documentation as far as credential concern2. -

Sorting Algorithm 1 Sorting Algorithm
Sorting algorithm 1 Sorting algorithm A sorting algorithm is an algorithm that puts elements of a list in a certain order. The most-used orders are numerical order and lexicographical order. Efficient sorting is important for optimizing the use of other algorithms (such as search and merge algorithms) which require input data to be in sorted lists; it is also often useful for canonicalizing data and for producing human-readable output. More formally, the output must satisfy two conditions: 1. The output is in nondecreasing order (each element is no smaller than the previous element according to the desired total order); 2. The output is a permutation (reordering) of the input. Since the dawn of computing, the sorting problem has attracted a great deal of research, perhaps due to the complexity of solving it efficiently despite its simple, familiar statement. For example, bubble sort was analyzed as early as 1956.[1] Although many consider it a solved problem, useful new sorting algorithms are still being invented (for example, library sort was first published in 2006). Sorting algorithms are prevalent in introductory computer science classes, where the abundance of algorithms for the problem provides a gentle introduction to a variety of core algorithm concepts, such as big O notation, divide and conquer algorithms, data structures, randomized algorithms, best, worst and average case analysis, time-space tradeoffs, and upper and lower bounds. Classification Sorting algorithms are often classified by: • Computational complexity (worst, average and best behavior) of element comparisons in terms of the size of the list (n). For typical serial sorting algorithms good behavior is O(n log n), with parallel sort in O(log2 n), and bad behavior is O(n2). -
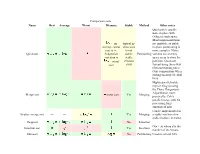
Comparison Sorts Name Best Average Worst Memory Stable Method Other Notes Quicksort Is Usually Done in Place with O(Log N) Stack Space
Comparison sorts Name Best Average Worst Memory Stable Method Other notes Quicksort is usually done in place with O(log n) stack space. Most implementations on typical in- are unstable, as stable average, worst place sort in-place partitioning is case is ; is not more complex. Naïve Quicksort Sedgewick stable; Partitioning variants use an O(n) variation is stable space array to store the worst versions partition. Quicksort case exist variant using three-way (fat) partitioning takes O(n) comparisons when sorting an array of equal keys. Highly parallelizable (up to O(log n) using the Three Hungarian's Algorithmor, more Merge sort worst case Yes Merging practically, Cole's parallel merge sort) for processing large amounts of data. Can be implemented as In-place merge sort — — Yes Merging a stable sort based on stable in-place merging. Heapsort No Selection O(n + d) where d is the Insertion sort Yes Insertion number of inversions. Introsort No Partitioning Used in several STL Comparison sorts Name Best Average Worst Memory Stable Method Other notes & Selection implementations. Stable with O(n) extra Selection sort No Selection space, for example using lists. Makes n comparisons Insertion & Timsort Yes when the data is already Merging sorted or reverse sorted. Makes n comparisons Cubesort Yes Insertion when the data is already sorted or reverse sorted. Small code size, no use Depends on gap of call stack, reasonably sequence; fast, useful where Shell sort or best known is No Insertion memory is at a premium such as embedded and older mainframe applications. Bubble sort Yes Exchanging Tiny code size. -

Sorting Algorithms Bubble Sort Selection Sort Insertion Sort
Sorting Algorithms I Analysis and Design of Algorithms Sorting Algorithms Bubble Sort Selection Sort Insertion Sort Analysis and Design of Algorithms Sorting Algorithm is an algorithm made up of a series of instructions that takes an array as input, and outputs a sorted array. There are many sorting algorithms, such as: . Selection Sort, Bubble Sort, Insertion Sort, Merge Sort, Heap Sort, QuickSort, Radix Sort, Counting Sort, Bucket Sort, ShellSort, Comb Sort, Pigeonhole Sort, Cycle Sort Analysis and Design of Algorithms Bubble Sort Analysis and Design of Algorithms Bubble Sort is the simplest sorting algorithm that works by repeatedly swapping the adjacent elements if they are in wrong order. Analysis and Design of Algorithms Algorithm: . Step1: Compare each pair of adjacent elements in the list . Step2: Swap two element if necessary . Step3: Repeat this process for all the elements until the entire array is sorted Analysis and Design of Algorithms Example 1 Assume the following Array: 5 1 4 2 Analysis and Design of Algorithms First Iteration: Compare 5 1 4 2 j j+1 Analysis and Design of Algorithms First Iteration: Swap 1 5 4 2 j j+1 Analysis and Design of Algorithms First Iteration: Compare 1 5 4 2 j j+1 Analysis and Design of Algorithms First Iteration: Swap 1 4 5 2 j j+1 Analysis and Design of Algorithms First Iteration: Compare 1 4 5 2 j j+1 Analysis and Design of Algorithms First Iteration: Swap 1 4 2 5 j j+1 Analysis and Design of Algorithms 1 4 2 5 Analysis and Design of Algorithms Second Iteration: -
Contents Classification Comparison of Algorithms Popular Sorting
From Wikipedia, the free encyclopedia A sorting algorithm is an algorithm that puts elements of a list in a certain order. The most-used orders are numerical order and lexicographical order. Efficient sorting is important for optimizing the use of other algorithms (such as search and merge algorithms) which require input data to be in sorted lists; it is also often useful for canonicalizing data and for producing human- readable output. More formally, the output must satisfy two conditions: 1. The output is in nondecreasing order (each element is no smaller than the previous element according to the desired total order); 2. The output is a permutation (reordering) of the input. Further, the data is often taken to be in an array, which allows random access, rather than a list, which only allows sequential access, though often algorithms can be applied with suitable modification to either type of data. Since the dawn of computing, the sorting problem has attracted a great deal of research, perhaps due to the complexity of solving it efficiently despite its simple, familiar statement. For example, bubble sort was analyzed as early as 1956.[1] Comparison sorting algorithms have a fundamental requirement of O(n log n) comparisons (some input sequences will require a multiple of n log n comparisons); algorithms not based on comparisons, such as counting sort, can have better performance. Although many consider sorting a solved problem—asymptotically optimal algorithms have been known since the mid-20th century—useful new algorithms are still being invented, with the now widely used Timsort dating to 2002, and the library sort being first published in 2006. -

CSE373: Data Structure & Algorithms Comparison Sorting
Sorting Riley Porter CSE373: Data Structures & Algorithms 1 Introduction to Sorting • Why study sorting? – Good algorithm practice! • Different sorting algorithms have different trade-offs – No single “best” sort for all scenarios – Knowing one way to sort just isn’t enough • Not usually asked about on tech interviews... – but if it comes up, you look bad if you can’t talk about it CSE373: Data Structures2 & Algorithms More Reasons to Sort General technique in computing: Preprocess data to make subsequent operations faster Example: Sort the data so that you can – Find the kth largest in constant time for any k – Perform binary search to find elements in logarithmic time Whether the performance of the preprocessing matters depends on – How often the data will change (and how much it will change) – How much data there is CSE373: Data Structures & 3 Algorithms Definition: Comparison Sort A computational problem with the following input and output Input: An array A of length n comparable elements Output: The same array A, containing the same elements where: for any i and j where 0 i < j < n then A[i] A[j] CSE373: Data Structures & 4 Algorithms More Definitions In-Place Sort: A sorting algorithm is in-place if it requires only O(1) extra space to sort the array. – Usually modifies input array – Can be useful: lets us minimize memory Stable Sort: A sorting algorithm is stable if any equal items remain in the same relative order before and after the sort. – Items that ’compare’ the same might not be exact duplicates – Might want to sort on some, but not all attributes of an item – Can be useful to sort on one attribute first, then another one CSE373: Data Structures & 5 Algorithms Stable Sort Example Input: [(8, "fox"), (9, "dog"), (4, "wolf"), (8, "cow")] Compare function: compare pairs by number only Output (stable sort): [(4, "wolf"), (8, "fox"), (8, "cow"), (9, "dog")] Output (unstable sort): [(4, "wolf"), (8, "cow"), (8, "fox"), (9, "dog")] CSE373: Data Structures & 6 Algorithms Lots of algorithms for sorting.. -

Sorting Algorithms
Lecture 15: Sorting CSE 373: Data Structures and Algorithms Algorithms CSE 373 WI 19 - KASEY CHAMPION 1 Administrivia Piazza! Homework - HW 5 Part 1 Due Friday 2/22 - HW 5 Part 2 Out Friday, due 3/1 - HW 3 Regrade Option due 3/1 Grades - HW 1, 2 & 3 Grades into Canvas soon - Socrative EC status into Canvas soon - HW 4 Grades published by 3/1 - Midterm Grades PubLished CSE 373 SP 18 - KASEY CHAMPION 2 Midterm Stats CSE 373 19 WI - KASEY CHAMPION 3 Sorting CSE 373 19 WI - KASEY CHAMPION 4 Types of Sorts Comparison Sorts Niche Sorts aka “linear sorts” Compare two elements at a time Leverages specific properties about the General sort, works for most types of elements items in the list to achieve faster Element must form a “consistent, total ordering” runtimes For every element a, b and c in the list the niche sorts typically run O(n) time following must be true: - If a <= b and b <= a then a = b In this class we’ll focus on comparison - If a <= b and b <= c then a <= c sorts - Either a <= b is true or <= a What does this mean? compareTo() works for your elements Comparison sorts run at fastest O(nlog(n)) time CSE 373 SP 18 - KASEY CHAMPION 5 Sort Approaches In Place sort A sorting algorithm is in-place if it requires only O(1) extra space to sort the array Typically modifies the input collection Useful to minimize memory usage Stable sort A sorting algorithm is stable if any equal items remain in the same relative order before and after the sort Why do we care? - Sometimes we want to sort based on some, but not all attributes of an item - -

CSE 332: Comparison Sorts
CSE 332: Comparison Sorts Michael Lee Wednesday, February 1, 2016 1 Why bother? Why not just use Collections.sort()? 2 Why study sorting? Tradeoffs I There is no ‘best’ sorting algorithm. I DIfferent sorts have different purposes/tradeoffs. Tech interviews I Nobody asks about sorting on interviews... I ...but if it comes up, you look bad if you can’t talk about it. 3 Definition: Comparison Sort SORT is a computational problem with the following preconditions and postconditions: Preconditions (input) An array A of length n where each element is of type E A consistent, total ordering on all elements of type E: compare(a, b) Postconditions (outputs) For all 0 ≤ i < j < n, A[k] ≤ A[j] Every item in the original array must be in the sorted array A comparison sort algorithm solves SORT. 4 More definitions In-place sort A sorting algorithm is in-place if it requires only O(1) extra space to sort the array. I Usually modifies input array I Can be useful: lets us minimize memory 5 More definitions Stable sort A sorting algorithm is stable if any equal items remain in the same relative order before and after the sort. I Observation: We sometimes want to sort on some, but not all attribute of an item I Items that ’compare’ the same might not be exact duplicates I Sometimes useful to sort on one attribute first, then another one 6 Stable sort: Example Input: I Array: [(8, "fox"), (9, "dog"), (4, "wolf"), (8, "cow")] I Compare function: compare pairs by number only Output; stable sort: [(4, "wolf"), (8, "fox"), (8, "cow"), (9, "dog")] Output; unstable sort: [(4, "wolf"), (8, "cow"), (8, "fox"), (9, "dog")] 7 Overview of sorting algorithms There are many sorts.. -

Performances of Modified Diminishing Increment Sorting in Improving the Performances of Some Sorting Algorithms
Oyelami Olufemi Moses Performances of Modified Diminishing Increment Sorting In Improving the Performances of Some Sorting Algorithms Oyelami Olufemi Moses [email protected] College of Computing and Communication Studies Computer Science Programme Bowen University Iwo, Nigeria Abstract There are several sorting algorithms in existence. Some are well known while others are not so well known, but important. However, more and more are still being developed to take care of the weaknesses of the existing ones and to make sorting simpler to implement. One of such new algorithms is the Modified Diminishing Increment Sorting (MDIS). In this article, a review is carried out of this algorithm and the several existing algorithms it has been employed to improve. In addition, a variant of MDIS christened Circlesort which applies MDIS in a recursive manner is also presented. Its performance comparisons with MDIS and other notable algorithms in the b est case, average case and the worst case are presented. This review will help prospective application developers that need to implement sorting determine when MDIS and its variant are strong and when the algorithms compared with them also have their own strengths so as to guide their choices. Keywords: Diminishing Increment Sorting, Modified Diminishing Increment Sorting, Performance. Efficiency, Circlesort, Shellsort, Improved Shellsort, Oyelami’s Sort. 1. INTRODUCTION Sorting is considered to be the most fundamental problem in the study of algorithms [1]. This is why this subject is worth considering. The more sorting algorithms there are, the better and the merrier because different sorting algorithms are suitable for different data characteristics and according to Donald Ervin Knuth, who is a renowned computer scientist and the author of one of the most respected references in computer science, “There is no known ‘best’ way to sort; there are many best methods, depending on what is to be sorted, on what machine and for what purpose” [2]. -

Defining a Modified Cycle Sort Algorithm and Parallel Critique with Other Sorting Algorithms (GRDJE/ Volume 5 / Issue 5 / 001)
GRD Journals- Global Research and Development Journal for Engineering | Volume 5 | Issue 5 | April 2020 ISSN- 2455-5703 Defining a Modified Cycle Sort Algorithm and Parallel Critique with other Sorting Algorithms Nakib Aman Turzo Lecturer Department of Computer Science and Engineering Varendra University Pritom Sarker Biplob Kumar Student Student Department of Computer Science and Engineering Department of Computer Science and Engineering Varendra University Varendra University Jyotirmoy Ghose Amit Chakraborty Student Student Department of Computer Science and Engineering Department of Computer Science and Engineering National Institute of Technology, Rourkela Varendra University Abstract Professionals of computer sciences have to confront with different complexities and problems. The pivot point of the problem which requires the focus is sorting algorithm. Sorting is the rearrangement of items or integers in an ordered way. In this research platform a modified cycle sort algorithm was devised and then comparative study of different sorting algorithms like Selection sort, Merge sort, Cycle sort and Bubble sort is being done. We also used other variety of other sorting algorithms with it. An entirely modified concept which is being sorted out. A program instigated in python has been used for gauging of CPU time taken by each algorithm. Results were obtained after cataloguing and graphically represented. For core precision program was casted a number of times and it’s concluded that modified cycle sort was the best option among all linear sorting algorithms where we have duplicate data and for large inputs efficiency has also ascended. Keywords- Sorting Algorithms, Cycle Sort, Merge Sort, Bubble Sort, Selection Sort, Time Complexity I. INTRODUCTION An algorithm is an explicit, precise, unambiguous, mechanically executable sequence of elementary instructions, usually intended to accomplish a specific purpose.