Apache Karaf 2.4.1 Guides
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Osgi and GWT Integration Via Pax-Web and Maven (V:0.01)
OSGi and GWT integration via Pax-web and Maven (v:0.01) Sergio Blanco Diez Ignacio Diaz de Sarralde Carvajal January 13, 2010 Contents 1 Introduction 2 2 GWT 3 2.1 Toolkit overview.....................................3 2.1.1 Development overview..............................3 2.1.2 Google Web Toolkit component overview...................4 2.2 Workflow.........................................4 2.2.1 Project creation.................................4 2.2.2 Project structure.................................5 2.2.3 \Hosted" or Development server........................6 2.2.4 Module definition; .gwt.xml files........................8 2.2.5 Coding the client; GWT Widgets........................9 2.2.6 Coding the server; Remote Procedure Calls.................. 12 2.3 Other features...................................... 14 2.3.1 Internationalization............................... 14 2.3.2 Declarative User Interfaces........................... 14 3 OSGi and GWT integration 17 3.1 Creating the GWT Project............................... 17 3.2 Things to consider in GWT Maven projects...................... 20 3.3 Enabling OSGi in the GWT project.......................... 20 3.3.1 Turning the GWT project into a bundle.................... 20 3.3.2 Dependencies management........................... 25 3.3.3 Run using Pax Runner.............................. 28 1 Chapter 1 Introduction When developing complex OSGi applications it is usual to implement one or more web frontends, be them for end users or for consumption by other systems. OSGi provides a standard way to register servlets and resources under different URLs, but creating complex frontends can be dif- ficult and time consuming. When the frontend is SOA based, solutions like Apache CXF help exposing internal services via web services or REST. But if the frontend must be a fairly complex web application in itself, complexity rises. -

Talend Open Studio for Big Data Release Notes
Talend Open Studio for Big Data Release Notes 6.0.0 Talend Open Studio for Big Data Adapted for v6.0.0. Supersedes previous releases. Publication date July 2, 2015 Copyleft This documentation is provided under the terms of the Creative Commons Public License (CCPL). For more information about what you can and cannot do with this documentation in accordance with the CCPL, please read: http://creativecommons.org/licenses/by-nc-sa/2.0/ Notices Talend is a trademark of Talend, Inc. All brands, product names, company names, trademarks and service marks are the properties of their respective owners. License Agreement The software described in this documentation is licensed under the Apache License, Version 2.0 (the "License"); you may not use this software except in compliance with the License. You may obtain a copy of the License at http://www.apache.org/licenses/LICENSE-2.0.html. Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License. This product includes software developed at AOP Alliance (Java/J2EE AOP standards), ASM, Amazon, AntlR, Apache ActiveMQ, Apache Ant, Apache Avro, Apache Axiom, Apache Axis, Apache Axis 2, Apache Batik, Apache CXF, Apache Cassandra, Apache Chemistry, Apache Common Http Client, Apache Common Http Core, Apache Commons, Apache Commons Bcel, Apache Commons JxPath, Apache -

Return of Organization Exempt from Income
OMB No. 1545-0047 Return of Organization Exempt From Income Tax Form 990 Under section 501(c), 527, or 4947(a)(1) of the Internal Revenue Code (except black lung benefit trust or private foundation) Open to Public Department of the Treasury Internal Revenue Service The organization may have to use a copy of this return to satisfy state reporting requirements. Inspection A For the 2011 calendar year, or tax year beginning 5/1/2011 , and ending 4/30/2012 B Check if applicable: C Name of organization The Apache Software Foundation D Employer identification number Address change Doing Business As 47-0825376 Name change Number and street (or P.O. box if mail is not delivered to street address) Room/suite E Telephone number Initial return 1901 Munsey Drive (909) 374-9776 Terminated City or town, state or country, and ZIP + 4 Amended return Forest Hill MD 21050-2747 G Gross receipts $ 554,439 Application pending F Name and address of principal officer: H(a) Is this a group return for affiliates? Yes X No Jim Jagielski 1901 Munsey Drive, Forest Hill, MD 21050-2747 H(b) Are all affiliates included? Yes No I Tax-exempt status: X 501(c)(3) 501(c) ( ) (insert no.) 4947(a)(1) or 527 If "No," attach a list. (see instructions) J Website: http://www.apache.org/ H(c) Group exemption number K Form of organization: X Corporation Trust Association Other L Year of formation: 1999 M State of legal domicile: MD Part I Summary 1 Briefly describe the organization's mission or most significant activities: to provide open source software to the public that we sponsor free of charge 2 Check this box if the organization discontinued its operations or disposed of more than 25% of its net assets. -

Neon Core Infrastructure Services
NeOn-project.org NeOn: Lifecycle Support for Networked Ontologies Integrated Project (IST-2005-027595) Priority: IST-2004-2.4.7 – “Semantic-based knowledge and content systems” D6.4.2 NeOn core infrastructure services Deliverable Co-ordinator: Walter Waterfeld Deliverable Co-ordinating Institution: Software AG (SAG) Other Authors: Diana Maynard, University of Sheffield (USFD), Ian Roberts, University of Sheffield (USFD), Michael Gesmann, Software AG (SAG) Document Identifier: NEON/2010/D6.4.2/v1.0 Date due: October 31st, 2009 Class Deliverable: NEON EU-IST-2005-027595 Submission date: January 31st , 2010 Project start date: March 1, 2006 Version: v1.0 Project duration: 4 years State: Final Distribution: Public 2006–2010 © Copyright lies with the respective authors and their institutions. Page 2 of 25 NeOn Integrated Project EU-IST-027595 NeOn Consortium This document is a part of the NeOn research project funded by the IST Programme of the Commission of the European Communities by the grant number IST-2005-027595. The following partners are involved in the project: Open University (OU) – Coordinator Universität Karlsruhe – TH (UKARL) Knowledge Media Institute – KMi Institut für Angewandte Informatik und Formale Berrill Building, Walton Hall Beschreibungsverfahren – AIFB Milton Keynes, MK7 6AA Englerstrasse 11 United Kingdom D-76128 Karlsruhe, Germany Contact person: Enrico Motta Contact person: Andreas Harth E-mail address: [email protected] E-mail address: [email protected] Universidad Politécnica de Madrid (UPM) Software AG (SAG) Campus de Montegancedo Uhlandstrasse 12 28660 Boadilla del Monte 64297 Darmstadt Spain Germany Contact person: Asunción Gómez Pérez Contact person: Walter Waterfeld E-mail address: [email protected] E-mail address: [email protected] Intelligent Software Components S.A. -

Apache Karaf ${Karaf.Version}
Apache Karaf Version 2.2.5 Apache Karaf Users' Guide 1 Copyright 2011 The Apache Software Foundation The PDF format of the Karaf Manual has been generated by Prince XML (http://www.princexml.com). 2 Table of contents Overview Quick Start Users Guide Developers Guide 3 Overview 4 OVERVIEW Karaf Overview Apache Karaf is a small OSGi based runtime which provides a lightweight container onto which various components and applications can be deployed. Here is a short list of features supported by the Karaf: • Hot deployment: Karaf supports hot deployment of OSGi bundles by monitoring jar files inside the [home]/deploy directory. Each time a jar is copied in this folder, it will be installed inside the runtime. You can then update or delete it and changes will be handled automatically. In addition, Karaf also supports exploded bundles and custom deployers (Blueprint and Spring ones are included by default). • Dynamic configuration: Services are usually configured through the ConfigurationAdmin OSGi service. Such configuration can be defined in Karaf using property files inside the [home]/etc directory. These configurations are monitored and changes on the properties files will be propagated to the services. • Logging System: using a centralized logging back end supported by Log4J, Karaf supports a number of different APIs (JDK 1.4, JCL, SLF4J, Avalon, Tomcat, OSGi) • Provisioning: Provisioning of libraries or applications can be done through a number of different ways, by which they will be downloaded locally, installed and started. • Native OS integration: Karaf can be integrated into your own Operating System as a service so that the lifecycle will be bound to your Operating System. -

IBM Websphere Application Server Community Edition V3.0 Helps Streamline the Creation of Osgi and Java Enterprise Edition 6 Applications
IBM United States Software Announcement 211-083, dated September 27, 2011 IBM WebSphere Application Server Community Edition V3.0 helps streamline the creation of OSGi and Java Enterprise Edition 6 applications Table of contents 1 Overview 6 Technical information 2 Key prerequisites 8 Ordering information 2 Planned availability date 9 Services 3 Description 9 Order now 6 Product positioning At a glance With WebSphere® Application Server Community Edition V3.0: • Developers can select just the components they need for optimum productivity (using OSGi and a component assembly model). • Developers can get JavaTM Enterprise Edition (Java EE) 6 applications started quickly for no charge. • System administrators are given more deployment and management options. • Organizations can take advantage of world-class, IBM® support options under a socket-based pricing model that can help reduce the cost burden in larger configurations. • You have access to a comprehensive and proven portfolio of middleware products from the WebSphere family. Overview WebSphere Application Server Community Edition V3.0 is the IBM open source- based application server that provides: • Java Enterprise Edition (Java EE) 6 support • An enterprise OSGi application programming model • Java Standard Edition (Java SE) 6 support Version 3 is built on Apache Geronimo and integrated with best-of-breed, open- source technology such as Apache Tomcat, Eclipse Equinox OSGi Framework, Apache Aries, Apache OpenEJB, Apache OpenJPA, Apache OpenWebBeans, and Apache MyFaces. Eclipse-based -

Avaliando a Dívida Técnica Em Produtos De Código Aberto Por Meio De Estudos Experimentais
UNIVERSIDADE FEDERAL DE GOIÁS INSTITUTO DE INFORMÁTICA IGOR RODRIGUES VIEIRA Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais Goiânia 2014 IGOR RODRIGUES VIEIRA Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais Dissertação apresentada ao Programa de Pós–Graduação do Instituto de Informática da Universidade Federal de Goiás, como requisito parcial para obtenção do título de Mestre em Ciência da Computação. Área de concentração: Ciência da Computação. Orientador: Prof. Dr. Auri Marcelo Rizzo Vincenzi Goiânia 2014 Ficha catalográfica elaborada automaticamente com os dados fornecidos pelo(a) autor(a), sob orientação do Sibi/UFG. Vieira, Igor Rodrigues Avaliando a dívida técnica em produtos de código aberto por meio de estudos experimentais [manuscrito] / Igor Rodrigues Vieira. - 2014. 100 f.: il. Orientador: Prof. Dr. Auri Marcelo Rizzo Vincenzi. Dissertação (Mestrado) - Universidade Federal de Goiás, Instituto de Informática (INF) , Programa de Pós-Graduação em Ciência da Computação, Goiânia, 2014. Bibliografia. Apêndice. Inclui algoritmos, lista de figuras, lista de tabelas. 1. Dívida técnica. 2. Qualidade de software. 3. Análise estática. 4. Produto de código aberto. 5. Estudo experimental. I. Vincenzi, Auri Marcelo Rizzo, orient. II. Título. Todos os direitos reservados. É proibida a reprodução total ou parcial do trabalho sem autorização da universidade, do autor e do orientador(a). Igor Rodrigues Vieira Graduado em Sistemas de Informação, pela Universidade Estadual de Goiás – UEG, com pós-graduação lato sensu em Desenvolvimento de Aplicações Web com Interfaces Ricas, pela Universidade Federal de Goiás – UFG. Foi Coordenador da Ouvidoria da UFG e, atualmente, é Analista de Tecnologia da Informação do Centro de Recursos Computacionais – CERCOMP/UFG. -

Apache Karaf Users' Guide
Apache Karaf Users' Guide Copyright 2010 The Apache Software Foundation 1 Table of contents • 1. Overview • 2. Quick start • 2.1. Quick Start (Source) • 3. Installation • 4. Understanding Karaf • 4.1. Console and Commands • 4.2. Remote Console • 4.3. Logging system • 4.4. Deployer • 4.5. Security framework • 4.6. Provisioning • 4.7. Administration • 4.8. Configuration • 5. Using Karaf • 5.1. Troubleshooting, Debugging and Profiling • 5.2. Developping applications • 5.3. Creating bundles for third party dependencies • 6. Advanced uses • 6.1. Extending the console • 6.2. Building custom distributions • 6.3. Programmatically connect to the console • 6.4. Embedding Karaf • 6.5. Deploying security providers • 6.6. Installing additional features • 6.7. Configuring Failover Deployments • 7. Optional Features • 7.1. Enabling Colorized Console Output On Windows 2 1. Overview Apache Karaf is a small OSGi based runtime which provides a lightweight container onto which various components and applications can be deployed. Here is a short list of features supported by the Karaf: • Hot deployment: Karaf supports hot deployment of OSGi bundles by monitoring jar files inside the [home]/deploy directory. Each time a jar is copied in this folder, it will be installed inside the runtime. You can then update or delete it and changes will be handled automatically. In addition, the Karaf also supports exploded bundles and custom deployers (blueprint and spring ones are included by default). • Dynamic configuration: Services are usually configured through the ConfigurationAdmin OSGi service. Such configuration can be defined in Karaf using property files inside the [home]/etc directory. These configurations are monitored and changes on the properties files will be propagated to the services. -

Apache Karaf 2.2.3, the Transitive Dependencies for This POM and the Bundles Listed in Src/Main/Resources/ Bundles.Properties
Apache Karaf Version 2.2.3 Apache Karaf Users' Guide 1 Copyright 2011 The Apache Software Foundation 2 Table of contents Overview Quick Start Users Guide Developers Guide 3 Overview 4 OVERVIEW Karaf Overview Apache Karaf is a small OSGi based runtime which provides a lightweight container onto which various components and applications can be deployed. Here is a short list of features supported by the Karaf: • Hot deployment: Karaf supports hot deployment of OSGi bundles by monitoring jar files inside the [home]/deploy directory. Each time a jar is copied in this folder, it will be installed inside the runtime. You can then update or delete it and changes will be handled automatically. In addition, Karaf also supports exploded bundles and custom deployers (Blueprint and Spring ones are included by default). • Dynamic configuration: Services are usually configured through the ConfigurationAdmin OSGi service. Such configuration can be defined in Karaf using property files inside the [home]/etc directory. These configurations are monitored and changes on the properties files will be propagated to the services. • Logging System: using a centralized logging back end supported by Log4J, Karaf supports a number of different APIs (JDK 1.4, JCL, SLF4J, Avalon, Tomcat, OSGi) • Provisioning: Provisioning of libraries or applications can be done through a number of different ways, by which they will be downloaded locally, installed and started. • Native OS integration: Karaf can be integrated into your own Operating System as a service so that the lifecycle will be bound to your Operating System. • Extensible Shell console: Karaf features a nice text console where you can manage the services, install new applications or libraries and manage their state. -

Hänninen, Arttu Enterprise Integration Patterns in Service Oriented Systems Master of Science Thesis
CORE Metadata, citation and similar papers at core.ac.uk Provided by Trepo - Institutional Repository of Tampere University Hänninen, Arttu Enterprise Integration Patterns in Service Oriented Systems Master of Science Thesis Examiner: Prof. Tommi Mikkonen Examiners and topic approved in the council meeting of Faculty of Information Technology on April 3rd, 2013. II TIIVISTELMÄ TAMPEREEN TEKNILLINEN YLIOPISTO Tietotekniikan koulutusohjelma Hänninen, Arttu: Enterprise Integration Patterns in Service Oriented Systems Diplomityö, 58 sivua Kesäkuu 2014 Pääaine: Ohjelmistotuotanto Tarkastajat: Prof. Tommi Mikkonen Avainsanat: Enterprise Integration Patterns, Palvelukeskeinen arkkitehtuuri (SOA), Viestipohjainen integraatio Palvelupohjaisen integraation toteuttaminen mihin tahansa tietojärjestelmään on haas- tavaa, sillä integraatioon liittyvät järjestelmät voivat muuttua jatkuvasti. Integraatiototeu- tusten tulee olla tarpeeksi joustavia, jotta ne pystyvät mukautumaan mahdollisiin muu- toksiin. Toteutukseen voidaan käyttää apuna eri sovelluskehyksiä, mutta ne eivät vält- tämättä takaa mitään standardoitua tapaa tehdä integraatio. Tätä varten on luotu joukko ohjeita (Enterprise Integration Patterns, EIP), jotka kuvaavat hyväksi havaittuja tapoja tehdä integraatioita. Tässä työssä keskitytään näiden mallien tutkimiseen ja siihen, miten niitä voidaan hyödyntää yritysjärjestelmissä. Jotta tutkimukseen saadaan konkreettinen vertailutulos, erään järjestelmän integraatioratkaisu tullaan päivittämään uuteen. Uusi ratkaisu hyödyntää sovelluskehystä, -

Full-Graph-Limited-Mvn-Deps.Pdf
org.jboss.cl.jboss-cl-2.0.9.GA org.jboss.cl.jboss-cl-parent-2.2.1.GA org.jboss.cl.jboss-classloader-N/A org.jboss.cl.jboss-classloading-vfs-N/A org.jboss.cl.jboss-classloading-N/A org.primefaces.extensions.master-pom-1.0.0 org.sonatype.mercury.mercury-mp3-1.0-alpha-1 org.primefaces.themes.overcast-${primefaces.theme.version} org.primefaces.themes.dark-hive-${primefaces.theme.version}org.primefaces.themes.humanity-${primefaces.theme.version}org.primefaces.themes.le-frog-${primefaces.theme.version} org.primefaces.themes.south-street-${primefaces.theme.version}org.primefaces.themes.sunny-${primefaces.theme.version}org.primefaces.themes.hot-sneaks-${primefaces.theme.version}org.primefaces.themes.cupertino-${primefaces.theme.version} org.primefaces.themes.trontastic-${primefaces.theme.version}org.primefaces.themes.excite-bike-${primefaces.theme.version} org.apache.maven.mercury.mercury-external-N/A org.primefaces.themes.redmond-${primefaces.theme.version}org.primefaces.themes.afterwork-${primefaces.theme.version}org.primefaces.themes.glass-x-${primefaces.theme.version}org.primefaces.themes.home-${primefaces.theme.version} org.primefaces.themes.black-tie-${primefaces.theme.version}org.primefaces.themes.eggplant-${primefaces.theme.version} org.apache.maven.mercury.mercury-repo-remote-m2-N/Aorg.apache.maven.mercury.mercury-md-sat-N/A org.primefaces.themes.ui-lightness-${primefaces.theme.version}org.primefaces.themes.midnight-${primefaces.theme.version}org.primefaces.themes.mint-choc-${primefaces.theme.version}org.primefaces.themes.afternoon-${primefaces.theme.version}org.primefaces.themes.dot-luv-${primefaces.theme.version}org.primefaces.themes.smoothness-${primefaces.theme.version}org.primefaces.themes.swanky-purse-${primefaces.theme.version} -
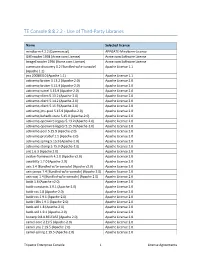
TE Console 8.8.2.2 - Use of Third-Party Libraries
TE Console 8.8.2.2 - Use of Third-Party Libraries Name Selected License mindterm 4.2.2 (Commercial) APPGATE-Mindterm-License GifEncoder 1998 (Acme.com License) Acme.com Software License ImageEncoder 1996 (Acme.com License) Acme.com Software License commons-discovery 0.2 [Bundled w/te-console] Apache License 1.1 (Apache 1.1) jrcs 20080310 (Apache 1.1) Apache License 1.1 activemQ-broker 5.13.2 (Apache-2.0) Apache License 2.0 activemQ-broker 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-camel 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-client 5.13.2 (Apache-2.0) Apache License 2.0 activemQ-client 5.14.2 (Apache-2.0) Apache License 2.0 activemQ-client 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-jms-pool 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-kahadb-store 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-openwire-legacy 5.13.2 (Apache-2.0) Apache License 2.0 activemQ-openwire-legacy 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-pool 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-protobuf 1.1 (Apache-2.0) Apache License 2.0 activemQ-spring 5.15.9 (Apache-2.0) Apache License 2.0 activemQ-stomp 5.15.9 (Apache-2.0) Apache License 2.0 ant 1.6.3 (Apache 2.0) Apache License 2.0 avalon-framework 4.2.0 (Apache v2.0) Apache License 2.0 awaitility 1.7.0 (Apache-2.0) Apache License 2.0 axis 1.4 [Bundled w/te-console] (Apache v2.0) Apache License 2.0 axis-jaxrpc 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 axis-saaj 1.4 [Bundled w/te-console] (Apache 2.0) Apache License 2.0 batik 1.6 (Apache v2.0) Apache License 2.0 batik-constants