A Novel 2D Cat Map Based Fast Data Encryption Scheme
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dynamics Forced by Homoclinic Orbits
DYNAMICS FORCED BY HOMOCLINIC ORBITS VALENT´IN MENDOZA Abstract. The complexity of a dynamical system exhibiting a homoclinic orbit is given by the orbits that it forces. In this work we present a method, based in pruning theory, to determine the dynamical core of a homoclinic orbit of a Smale diffeomorphism on the 2-disk. Due to Cantwell and Conlon, this set is uniquely determined in the isotopy class of the orbit, up a topological conjugacy, so it contains the dynamics forced by the homoclinic orbit. Moreover we apply the method for finding the orbits forced by certain infinite families of homoclinic horseshoe orbits and propose its generalization to an arbitrary Smale map. 1. Introduction Since the Poincar´e'sdiscovery of homoclinic orbits, it is known that dynamical systems with one of these orbits have a very complex behaviour. Such a feature was explained by Smale in terms of his celebrated horseshoe map [40]; more precisely, if a surface diffeomorphism f has a homoclinic point then, there exists an invariant set Λ where a power of f is conjugated to the shift σ defined on the compact space Σ2 = f0; 1gZ of symbol sequences. To understand how complex is a diffeomorphism having a periodic or homoclinic orbit, we need the notion of forcing. First we will define it for periodic orbits. 1.1. Braid types of periodic orbits. Let P and Q be two periodic orbits of homeomorphisms f and g of the closed disk D2, respectively. We say that (P; f) and (Q; g) are equivalent if there is an orientation-preserving homeomorphism h : D2 ! D2 with h(P ) = Q such that f is isotopic to h−1 ◦ g ◦ h relative to P . -

Computing Complex Horseshoes by Means of Piecewise Maps
November 26, 2018 3:54 ws-ijbc International Journal of Bifurcation and Chaos c World Scientific Publishing Company Computing complex horseshoes by means of piecewise maps Alvaro´ G. L´opez, Alvar´ Daza, Jes´us M. Seoane Nonlinear Dynamics, Chaos and Complex Systems Group, Departamento de F´ısica, Universidad Rey Juan Carlos, Tulip´an s/n, 28933 M´ostoles, Madrid, Spain [email protected] Miguel A. F. Sanju´an Nonlinear Dynamics, Chaos and Complex Systems Group, Departamento de F´ısica, Universidad Rey Juan Carlos, Tulip´an s/n, 28933 M´ostoles, Madrid, Spain Department of Applied Informatics, Kaunas University of Technology, Studentu 50-415, Kaunas LT-51368, Lithuania Received (to be inserted by publisher) A systematic procedure to numerically compute a horseshoe map is presented. This new method uses piecewise functions and expresses the required operations by means of elementary transfor- mations, such as translations, scalings, projections and rotations. By repeatedly combining such transformations, arbitrarily complex folding structures can be created. We show the potential of these horseshoe piecewise maps to illustrate several central concepts of nonlinear dynamical systems, as for example the Wada property. Keywords: Chaos, Nonlinear Dynamics, Computational Modelling, Horseshoe map 1. Introduction The Smale horseshoe map is one of the hallmarks of chaos. It was devised in the 1960’s by Stephen Smale arXiv:1806.06748v2 [nlin.CD] 23 Nov 2018 [Smale, 1967] to reproduce the dynamics of a chaotic flow in the neighborhood of a given periodic orbit. It describes in the simplest way the dynamics of homoclinic tangles, which were encountered by Henri Poincar´e[Poincar´e, 1890] and were intensively studied by George Birkhoff [Birkhoff, 1927], and later on by Mary Catwright and John Littlewood, among others [Catwright & Littlewood, 1945, 1947; Levinson, 1949]. -

Hyperbolic Dynamical Systems, Chaos, and Smale's
Hyperbolic dynamical systems, chaos, and Smale's horseshoe: a guided tour∗ Yuxi Liu Abstract This document gives an illustrated overview of several areas in dynamical systems, at the level of beginning graduate students in mathematics. We start with Poincar´e's discovery of chaos in the three-body problem, and define the Poincar´esection method for studying dynamical systems. Then we discuss the long-term behavior of iterating a n diffeomorphism in R around a fixed point, and obtain the concept of hyperbolicity. As an example, we prove that Arnold's cat map is hyperbolic. Around hyperbolic fixed points, we discover chaotic homoclinic tangles, from which we extract a source of the chaos: Smale's horseshoe. Then we prove that the behavior of the Smale horseshoe is the same as the binary shift, reducing the problem to symbolic dynamics. We conclude with applications to physics. 1 The three-body problem 1.1 A brief history The first thing Newton did, after proposing his law of gravity, is to calculate the orbits of two mass points, M1;M2 moving under the gravity of each other. It is a basic exercise in mechanics to show that, relative to one of the bodies M1, the orbit of M2 is a conic section (line, ellipse, parabola, or hyperbola). The second thing he did was to calculate the orbit of three mass points, in order to study the sun-earth-moon system. Here immediately he encountered difficulty. And indeed, the three body problem is extremely difficult, and the n-body problem is even more so. -

Escape and Metastability in Deterministic and Random Dynamical Systems
ESCAPE AND METASTABILITY IN DETERMINISTIC AND RANDOM DYNAMICAL SYSTEMS by Ognjen Stanˇcevi´c a thesis submitted for the degree of Doctor of Philosophy at the University of New South Wales, July 2011 PLEASE TYPE THE UNIVERSITY OF NEW SOUTH WALES Thesis/Dissertation Sheet Surname or Family name: Stancevic First name: Ognjen Other name/s: Abbreviation for degree as given in the University calendar: PhD School: Mathematics and Statistics Faculty: Science Title: Escape and Metastability in Deterministic and Random Dynamical Systems Abstract 350 words maximum: (PLEASE TYPE) Dynamical systems that are close to non-ergodic are characterised by the existence of subdomains or regions whose trajectories remain confined for long periods of time. A well-known technique for detecting such metastable subdomains is by considering eigenfunctions corresponding to large real eigenvalues of the Perron-Frobenius transfer operator. The focus of this thesis is to investigate the asymptotic behaviour of trajectories exiting regions obtained using such techniques. We regard the complement of the metastable region to be a hole , and show in Chapter 2 that an upper bound on the escape rate into the hole is determined by the corresponding eigenvalue of the Perron-Frobenius operator. The results are illustrated via examples by showing applications to uniformly expanding maps of the unit interval. In Chapter 3 we investigate a non-uniformly expanding map of the interval to show the existence of a conditionally invariant measure, and determine asymptotic behaviour of the corresponding escape rate. Furthermore, perturbing the map slightly in the slowly expanding region creates a spectral gap. This is often observed numerically when approximating the operator with schemes such as Ulam s method. -
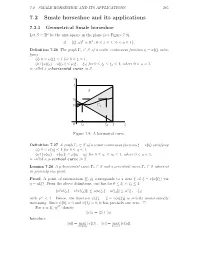
7.2 Smale Horseshoe and Its Applications
7.2. SMALE HORSESHOE AND ITS APPLICATIONS 285 7.2 Smale horseshoe and its applications 7.2.1 Geometrical Smale horseshoe Let S R2 be the unit square in the plane (see Figure 7.9). ⊂ S = (ξ, η)T R2 :0 ξ 1, 0 η 1 . { ∈ ≤ ≤ ≤ ≤ } Definition 7.26 The graph Γu S of a scalar continuous function η = u(ξ) satis- fying ⊂ (i) 0 u(ξ) 1 for 0 ξ 1, (ii) u≤(ξ ) ≤u(ξ ) µ≤ξ ≤ξ for 0 ξ ξ 1, where 0 <µ< 1, | 1 − 2 | ≤ | 1 − 2| ≤ 1 ≤ 2 ≤ is called a µ-horizontal curve in S. η 1 S η2 η1 Γu 0 ξ1 ξ2 1 ξ Figure 7.9: A horizontal curve. Definition 7.27 A graph Γv S of a scalar continuous function ξ = v(η) satisfying: (i) 0 v(η) 1 for 0 η⊂ 1; ≤ ≤ ≤ ≤ (ii) v(η1) v(η2) µ η1 η2 for 0 η1 η2 1, where 0 <µ< 1, is called| a µ-vertical− | ≤curve| −in S|. ≤ ≤ ≤ Lemma 7.28 A µ-horizontal curve Γh S and a µ-vertical curve Γv S intersect in precisely one point. ⊂ ⊂ Proof: A point of intersection (ξ, η) corresponds to a zero ξ of ξ v(u(ξ)) via − η = u(ξ). From the above definitions, one has for 0 ξ <ξ 1: ≤ 1 2 ≤ v(u(ξ ) v(u(ξ )) µ u(ξ ) u(ξ ) µ2 ξ ξ | 1 − 2 | ≤ | 1 − 2 | ≤ | 1 − 2| with µ2 < 1. Hence, the function ψ(ξ) = ξ v(u(ξ)) is strictly monotonically increasing. -

Chapter 15 Stretch, Fold, Prune
Chapter 15 Stretch, fold, prune I.1. Introduction to conjugacy problems for diffeomor- phisms. This is a survey article on the area of global anal- ysis defined by differentiable dynamical systems or equiv- alently the action (differentiable) of a Lie group G on a manifold M. Here Diff(M) is the group of all diffeomor- phisms of M and a diffeomorphism is a differentiable map with a differentiable inverse. (::: ) Our problem is to study the global structure, i.e., all of the orbits of M. —Stephen Smale, Differentiable Dynamical Systems e have learned that the Rössler attractor is very thin, but otherwise the re- turn maps that we found were disquieting – figure 3.4 did not appear to W be a one-to-one map. This apparent loss of invertibility is an artifact of projection of higher-dimensional return maps onto their lower-dimensional sub- spaces. As the choice of a lower-dimensional subspace is arbitrary, the resulting snapshots of return maps look rather arbitrary, too. Such observations beg a ques- tion: Does there exist a natural, intrinsic coordinate system in which we should plot a return map? We shall argue in sect. 15.1 that the answer is yes: The intrinsic coordinates are given by the stable/unstable manifolds, and a return map should be plotted as a map from the unstable manifold back onto the immediate neighborhood of the unstable manifold. In chapter 5 we established that Floquet multipliers of periodic orbits are (local) dynamical invariants. Here we shall show that every equilibrium point and every periodic orbit carries with it stable and unstable manifolds which provide topologically invariant global foliation of the state space. -

HORSE SHOES and HOMOCLINIC TANGLE Math118, O. Knill HORSESHOE from HOMOCLINIC POINTS
HORSE SHOES AND HOMOCLINIC TANGLE Math118, O. Knill HORSESHOE FROM HOMOCLINIC POINTS. ABSTRACT. The horse shoe map is a map in the plane with complicated dynamics. The horse shoe construction THEOREM. A transverse homoclinic point leads to a horseshoe. applies also to conservative maps and occurs near homoclinic points. There exists then an invariant set, on which the map is conjugated to a shift on two symbols. THE HORSE SHOE MAP. We construct a map T on the plane which maps a rectangle into a horse-shoe-shaped Take a small rectangle A centered at the hyperbolic fixed point. Some iterate of T will have the property that set within the old rectangle. The following pictures show an actual implementation with an explicit map n m T (A) contains the homoclinic point. Some iterate of the inverse of T will have the property that B = T (A) contains the homoclinic point to. The map T n+m applied to B produces a horseshoe map. A better picture, which can be found in the book of Gleick shows a now rounded region which is first stretched MANY HYPERBOLIC PERIODIC POINTS. The conjugation shows that pe- out, then bent back into the same region. riodic points are dense in K and that it contains dense periodic orbits. The map T restricted to K is chaotic in the sense of Devaney. Actually, one can 0.2 0.1 show that each of the periodic points in K form hyperbolic points again. The -1 -0.5 0.5 1 stable and unstable manifolds of these hyperbolic points form again transverse -0.1 homoclinic points and the story repeats again. -

Cryptography with Chaos
Proceedings, 5th Chaotic Modeling and Simulation International Conference, 12 – 15 June 2012, Athens Greece Cryptography with Chaos George Makris , Ioannis Antoniou Mathematics Department, Aristotle University, 54124, Thessaloniki, Greece E-mail: [email protected] Mathematics Department, Aristotle University, 54124, Thessaloniki, Greece E-mail: [email protected] Abstract: We implement Cryptography with Chaos following and extending the original program of Shannon with 3 selected Torus Automorphisms, namely the Baker Map, the Horseshoe Map and the Cat Map. The corresponding algorithms and the software (chaos_cryptography) were developed and applied to the encryption of picture as well as text in real time. The maps and algorithms may be combined as desired, creating keys as complicated as desired. Decryption requires the reverse application of the algorithms. Keywords: Cryptography, Chaos, image encryption, text encryption, Cryptography with Chaos. 1. Chaotic Maps in Cryptography Chaotic maps are simple unstable dynamical systems with high sensitivity to initial conditions [Devaney 1992]. Small deviations in the initial conditions (due to approximations or numerical calculations) lead to large deviations of the corresponding orbits, rendering the long-term forecast for the chaotic systems intractable [Lighthill 1986]. This deterministic in principle, but not determinable in practice dynamical behavior is a local mechanism for entropy production. In fact Chaotic systems are distinguished as Entropy producing deterministic systems. In practice the required information for predictions after a (small) number of steps, called horizon of predictability, exceeds the available memory and the computation time grows superexponentially. [Prigogine 1980, Strogatz 1994, Katok, ea 1995, Lasota, ea 1994, Meyers 2009]. Shannon in his classic 1949 first mathematical paper on Cryptography proposed chaotic maps as models - mechanisms for symmetric key encryption, before the development of Chaos Theory. -

Dissertation Submitted in Partial Satisfaction of the Requirements for the Degree Of
UNIVERSITY OF CALIFORNIA Santa Barbara Development of Nonlinear and Coupled Microelectromechanical Oscillators for Sensing Applications A Dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Mechanical Engineering by Barry Ernest DeMartini Committee in Charge: Professor Kimberly L. Turner, Chair Professor Jeff Moehlis Professor Karl J. Astr¨om˚ Professor Noel C. MacDonald Professor Steven W. Shaw September 2008 The Dissertation of Barry Ernest DeMartini is approved: Professor Jeff Moehlis Professor Karl J. Astr¨om˚ Professor Noel C. MacDonald Professor Steven W. Shaw Professor Kimberly L. Turner, Committee Chairperson August 2008 Development of Nonlinear and Coupled Microelectromechanical Oscillators for Sensing Applications Copyright © 2008 by Barry Ernest DeMartini iii Acknowledgements First of all, I would like to dedicate this dissertation to my parents, Sharon and Ernie, my brothers, Kevin and Joel, and my girlfriend Michele for their un- conditional love and support over the past years. I would like to give special thanks to my advisors, Kimberly Turner and Jeff Moehlis, for giving me the opportunity to work in their research groups, for their guidance, and for all that they have taught me over the past five years. I would also like to thank Steve Shaw, Karl Astr¨om,˚ and Noel MacDonald for being on my committee and for their vital input on the various projects that I have worked on in graduate school. I would like to thank Jeff Rhoads and Nick Miller for the valuable collabora- -

Stretching and Folding Versus Cutting and Shuffling: an Illustrated
Stretching and folding versus cutting and shuffling: An illustrated perspective on mixing and deformations of continua Ivan C. Christov,1, a) Richard M. Lueptow,2, b) and Julio M. Ottino3, c) 1)Department of Engineering Sciences and Applied Mathematics, Northwestern University, Evanston, Illinois 60208, USA 2)Department of Mechanical Engineering, Northwestern University, Evanston, Illinois 60208, USA 3)Department of Chemical and Biological Engineering, Northwestern Institute on Complex Systems, and Department of Mechanical Engineering, Northwestern University, Evanston, Illinois 60208, USA We compare and contrast two types of deformations inspired by mixing applications – one from the mixing of fluids (stretching and folding), the other from the mixing of granular matter (cutting and shuffling). The connection between mechanics and dynamical systems is discussed in the context of the kinematics of deformation, emphasizing the equiv- alence between stretches and Lyapunov exponents. The stretching and folding motion exemplified by the baker’s map is shown to give rise to a dynamical system with a positive Lyapunov exponent, the hallmark of chaotic mixing. On the other hand, cutting and shuffling does not stretch. When an interval exchange transformation is used as the basis for cutting and shuffling, we establish that all of the map’s Lyapunov exponents are zero. Mixing, as quantified by the interfacial area per unit volume, is shown to be exponential when there is stretching and folding, but linear when there is only cutting and shuffling. We also discuss how a simple computational approach can discern stretching in discrete data. I. INTRODUCTION layer and the underlying static bed of granular material in an avalanche.5 This newaspect ofthe flow leads todifferent mod- The essence of mixing of a fluid with itself can be under- els for the kinematics. -

Chapter 23 Predicting Chaos
Chapter 23 Predicting Chaos We have discussed methods for diagnosing chaos, but what about predicting the existence of chaos in a dynamical system. This is a much harder problem, and it seems that the best that can be done is to predict the existence of “chaotic sets” that are not attractors but may perhaps “organize” the chaotic attractor. These methods rely on the understanding of the complicated structure that emerges in phase space when a homoclinic or heteroclinic orbit is perturbed. To introduce these ideas we first introduce a definition of chaos that is useful for sets that are not attractors, motivating the idea using the simplest of chaotic maps, the shift map. 23.1 The Shift Map and Symbolic Dynamics The map xn+1 = 2xn mod 1 (23.1) displays many of the features of chaos in an analytically accessible way. The tent map at a = 2 is equivalent to the shift map. To understand the dynamics write the initial point in binary representation x0 = 0.a1a2 ... equivalent to X −ν x0 = av2 (23.2) with each ai either 0 or 1. The action of the map is simply to shift the “binal” point to the right and discard the first digit x1 = f(x0) = 0.a2a3 ... (23.3) 1 CHAPTER 23. PREDICTING CHAOS 2 Many properties are now evident: 1. Sensitivity to initial conditions: two initial conditions differing by of order 2−m lead to orbits that differ by O(1) after m iterations. 2. The answer to the question whether the mth iteration from a random initial 1 condition is greater or less than 2 is as random as a coin toss. -

Generalized Attracting Horseshoe in the Rössler Attractor
S S symmetry Article Generalized Attracting Horseshoe in the Rössler Attractor Karthik Murthy 1, Ian Jordan 2, Parth Sojitra 3, Aminur Rahman 4,* and Denis Blackmore 5 1 Department of Computer Science, University of Illinois at Urbana-Champaign, Champaign, IL 61801, USA; [email protected] 2 Department of Applied Mathematics and Statistics, Stony Brook University, Stony Brook, NY 11794, USA; [email protected] 3 Department of Electrical and Computer Engineering, New Jersey Institute of Technology, Newark, NJ 07102, USA; [email protected] 4 Department of Applied Mathematics, University of Washington, Seattle, WA 98195, USA 5 Department of Mathematical Sciences, New Jersey Institute of Technology, Newark, NJ 07102, USA; [email protected] * Correspondence: [email protected] Abstract: We show that there is a mildly nonlinear three-dimensional system of ordinary differential equations—realizable by a rather simple electronic circuit—capable of producing a generalized attracting horseshoe map. A system specifically designed to have a Poincaré section yielding the desired map is described, but not pursued due to its complexity, which makes the construction of a circuit realization exceedingly difficult. Instead, the generalized attracting horseshoe and its trapping region is obtained by using a carefully chosen Poincaré map of the Rössler attractor. Novel numerical techniques are employed to iterate the map of the trapping region to approximate the chaotic strange attractor contained in the generalized attracting horseshoe, and an electronic circuit is constructed to produce the map. Several potential applications of the idea of a generalized attracting horseshoe and a physical electronic circuit realization are proposed. Keywords: generalized attracting horseshoe; strange attractors; poincaré map; electronic circuits Citation: Murthy, K.; Jordan, I.; 1.