Scripting Basics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Configuring UNIX-Specific Settings: Creating Symbolic Links : Snap
Configuring UNIX-specific settings: Creating symbolic links Snap Creator Framework NetApp September 23, 2021 This PDF was generated from https://docs.netapp.com/us-en/snap-creator- framework/installation/task_creating_symbolic_links_for_domino_plug_in_on_linux_and_solaris_hosts.ht ml on September 23, 2021. Always check docs.netapp.com for the latest. Table of Contents Configuring UNIX-specific settings: Creating symbolic links . 1 Creating symbolic links for the Domino plug-in on Linux and Solaris hosts. 1 Creating symbolic links for the Domino plug-in on AIX hosts. 2 Configuring UNIX-specific settings: Creating symbolic links If you are going to install the Snap Creator Agent on a UNIX operating system (AIX, Linux, and Solaris), for the IBM Domino plug-in to work properly, three symbolic links (symlinks) must be created to link to Domino’s shared object files. Installation procedures vary slightly depending on the operating system. Refer to the appropriate procedure for your operating system. Domino does not support the HP-UX operating system. Creating symbolic links for the Domino plug-in on Linux and Solaris hosts You need to perform this procedure if you want to create symbolic links for the Domino plug-in on Linux and Solaris hosts. You should not copy and paste commands directly from this document; errors (such as incorrectly transferred characters caused by line breaks and hard returns) might result. Copy and paste the commands into a text editor, verify the commands, and then enter them in the CLI console. The paths provided in the following steps refer to the 32-bit systems; 64-bit systems must create simlinks to /usr/lib64 instead of /usr/lib. -
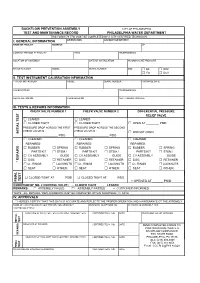
BFP Test Form
BACKFLOW PREVENTION ASSEMBLY CITY OF PHILADELPHIA TEST AND MAINTENANCE RECORD PHILADELPHIA WATER DEPARTMENT THIS FORM (79-770) MUST BE COMPLETED BY A CITY CERTIFIED TECHNICIAN I. GENERAL INFORMATION ORIENTATION ACCOUNT OR METER # NAME OF FACILITY ADDRESS ZIP CONTACT PERSON AT FACILITY TITLE TELEPHONE NO. LOCATION OF ASSEMBLY DATE OF INSTALLATION INCOMING LINE PRESSURE MANUFACTURER MODEL SERIAL NUMBER SIZE □ DS □ RPZ □ FS □ DCV II. TEST INSTRUMENT CALIBRATION INFORMATION TYPE OF INSTRUMENT MODEL SERIAL NUMBER PURCHASE DATE CALIBRATED BY TELEPHONE NO. REGISTRATION NO. CALIBRATED ON NEXT CALIBRATION DUE III. TESTS & REPAIRS INFORMATION CHECK VALVE NUMBER 1 CHECK VALVE NUMBER 2 DIFFERENTIAL PRESSURE RELIEF VALVE □ LEAKED □ LEAKED □ CLOSED TIGHT □ CLOSED TIGHT □ OPEN AT ________ PSID PRESSURE DROP ACROSS THE FIRST PRESSURE DROP ACROSS THE SECOND CHECK VALVE IS : CHECK VALVE IS : INITIAL TEST INITIAL □ DID NOT OPEN ______________________ PSID ______________________ PSID □ CLEANED □ CLEANED □ CLEANED REPAIRED: REPAIRED: REPAIRED: □ RUBBER □ SPRING □ RUBBER □ SPRING □ RUBBER □ SPRING PARTS KIT □ STEM / PARTS KIT □ STEM / PARTS KIT □ STEM / □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ DISC □ RETAINER □ DISC □ RETAINER □ DISC □ RETAINER * REPAIRS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ SEAT □ OTHER: □ SEAT □ OTHER: □ SEAT □ OTHER: □ CLOSED TIGHT AT ______ PSID □ CLOSED TIGHT AT ______ PSID TEST FINAL FINAL □ OPENED AT ______ PSID CONDITION OF NO. 2 CONTROL VALVE : □ CLOSED TIGHT □ LEAKED REMARKS : □ ASSEMBLY FAILED □ ASSEMBLY PASSED □ CUSTOMER INFORMED *NOTE : ALL REPAIRS / REPLACEMENTS MUST BE COMPLETED WITHIN FOURTEEN (14) DAYS IV. APPROVALS * I HEREBY CERTIFY THAT THIS DATA IS ACCURATE AND REFLECTS THE PROPER OPERATION AND MAINTENANCE OT THE ASSEMBLY NAME OF CERTIFIED BACKFLOW PREVENTION ASSEMBLY BUSINESS TELEPHONE NO. -

Installation Guide LS Nav 2018 (11.0) Contents
LS Nav 2018 (11.0) Installation Guide © 2018 LS Retail ehf. All rights reserved. All trademarks belong to their respective holders. ii Installation Guide LS Nav 2018 (11.0) Contents Contents Installation Guide LS Nav 1 Files in This Version 1 LS Nav Setup File 1 Demonstration Database Backup 1 Documentation 1 Objects 2 Objects \ Uninstall 2 Objects \ Upgrade 2 Objects \ Auto Test 2 Online Help 2 Setup \ LS Nav Rapid Installer 2 Setup \ LS Nav Rapid Start 2 Setup \ LS Nav Toolbox 2 Setup \ LS Printing Station 2 Setup 2 Installation 2 Prerequisites 2 Microsoft Dynamics NAV Application Objects Added or Modified by LS Nav 3 Installing LS Nav in a New Database 4 Installing LS Nav in an Existing Database 4 Uninstall 5 Uninstall the LS Nav xx.x Client Components 5 Uninstall the LS Nav xx.x Service Components 5 Uninstall LS Nav from a Microsoft Dynamics NAV Database 5 Database Compilation 6 System Requirements 6 Security Hardening Guide for LS Nav 7 Clear Data Tables That Are Not Included in the Customer’s License 7 Online Help Installation 7 Installation Guide LS Nav 2018 (11.0) iii Contents Local Setup 8 Remote Setup 8 Older Documents 9 Toolbox Installation 10 See Also 10 Installing the Toolbox 10 Client Components Installer 11 Service Components Installer 12 Install Options (Silent Install) 13 Installing Into a Database (Control Add-Ins Table) 14 Web POS Installation 16 See Also (topics in LS Nav Online Help) 17 Installing Microsoft Dynamics NAV for Web POS 17 Importing Control Add-in for Web POS 17 Web POS in Full-Screen Mode 18 LS Nav Auto Tests 18 Prerequisites 18 Installation 19 Objects needed 19 Running 19 1. -

Getty Scholars' Workspace™ INSTALLATION INSTRUCTIONS
Getty Scholars’ Workspace™ INSTALLATION INSTRUCTIONS This document outlines methods to run the application locally on your personal computer or to do a full installation on a web server. Test Drive with Docker Getty Scholars' Workspace is a multi-tenant web application, so it is intended to be run on a web server. However, if you'd like to run it on your personal computer just to give it a test drive, you can use Docker to create a virtual server environment and run the Workspace locally. Follow the steps below to give it a spin. Scroll further for real deployment instructions. 1. Install Docker on your machine. Follow instructions on the Docker website: https://www.docker.com/ 2. If you are using Docker Machine (Mac or Windows), be sure to start it by using the Docker Quickstart Terminal. Docker is configured to use the default machine with IP 192.168.99.100. 3. At the command line, pull the Getty Scholars' Workspace image. $ docker pull thegetty/scholarsworkspace 4. Run the container. $ docker run -d -p 8080:80 --name=wkspc thegetty/scholarsworkspace supervisord -n 5. Point your browser to `<ip address>:8080/GettyScholarsWorkspace`. Use the IP address noted in Step 2. 6. The Drupal administrator login is `scholar` and the password is `workspace`. Be sure to change these in the Drupal admin interface. 7. To shut it down, stop the container: $ docker stop wkspc Web Server Installation These installation instructions assume you are installing Getty Scholars' Workspace on a server (virtual or physical) with a clean new instance of Ubuntu 14.04 as the operating system. -

File Permissions Do Not Restrict Root
Filesystem Security 1 General Principles • Files and folders are managed • A file handle provides an by the operating system opaque identifier for a • Applications, including shells, file/folder access files through an API • File operations • Access control entry (ACE) – Open file: returns file handle – Allow/deny a certain type of – Read/write/execute file access to a file/folder by – Close file: invalidates file user/group handle • Access control list (ACL) • Hierarchical file organization – Collection of ACEs for a – Tree (Windows) file/folder – DAG (Linux) 2 Discretionary Access Control (DAC) • Users can protect what they own – The owner may grant access to others – The owner may define the type of access (read/write/execute) given to others • DAC is the standard model used in operating systems • Mandatory Access Control (MAC) – Alternative model not covered in this lecture – Multiple levels of security for users and documents – Read down and write up principles 3 Closed vs. Open Policy Closed policy Open Policy – Also called “default secure” • Deny Tom read access to “foo” • Give Tom read access to “foo” • Deny Bob r/w access to “bar” • Give Bob r/w access to “bar • Tom: I would like to read “foo” • Tom: I would like to read “foo” – Access denied – Access allowed • Tom: I would like to read “bar” • Tom: I would like to read “bar” – Access allowed – Access denied 4 Closed Policy with Negative Authorizations and Deny Priority • Give Tom r/w access to “bar” • Deny Tom write access to “bar” • Tom: I would like to read “bar” – Access -

Instructions for Pwd Candidates Regarding Typing Skill Test
INSTRUCTIONS FOR PWD CANDIDATES REGARDING TYPING SKILL TEST (ON COMPUTER) AND STENOGRAPHY SKILL TEST The following guidelines are applicable to PwD Candidates shortlisted for Typing test or stenography test. 1. Typing test will be conducted on computer. 2. Persons with benchmark disability in the category of Visually impaired, orthopedically handicapped (afflicted by cerebral palsy), orthopedically handicapped (both arm affected), orthopedically handicapped candidates who has a locomotor disability wherein the dominant writing extremity is affected to the extent of slowing down the performance of the candidate (such deficiency to be indicated in the certificate, issued by competent authority, submitted by the candidate) will be allowed compensatory time of 05 minutes. 3. VI Candidates are eligible for scribe/passage dictator. 4. The Scribe/ Passage dictator is identified by the candidate at own cost and as per own choice. 5. The scribe/Passage dictator will read out the passage to VI candidates only within the allotted time. 6. Passage will not be provided in Brail for the VI candidates. 7. A person acting as a Scribe/Passage dictator for one candidate cannot be a Scribe /Passage dictator for another candidate. 8. The scribe/Passage dictator arranged by the candidate should not be a candidate for the same examination. 9. The candidate shall be responsible for any misconduct on the part of the scribe/Passage dictator brought by him during typing test. 10.Persons with Disabilities candidates who claim to be permanently unfit to take the Typing test because of a physical disability may, with the prior approval of the CEPTAM, DRDO be exempted from the requirement of appearing and qualifying at such test, provided such a candidate submits in the attached format (Appendix-I) to the CEPTAM, DRDO from the competent Medical Authority, i.e. -

After Upgrade and Reboot with Install Configuration Set to Yes, the BIG-IP
K33233632: After upgrade and reboot with Install Configuration set to Yes, the BIG-IP appears to have hung or lost all configuration and mcpd, gtmd, named and others are in a restart loop Support Solution Original Publication Date: Jan 28, 2020 Update Date: Mar 25, 2021 Details Description After you upgrade the BIG-IP system to BIG-IP 14.1.2 and later, certain daemons (e.g. mcpd, gtmd, and named) may be in a restart loop and the BIG-IP appears to have hung or lost all configuration. Additionally, the device may exhibit the following symptoms: You observe error messages similar to the following in /var/log/ltm (below is an example of an mcpd restart loop): err mcpd[8710]: 01070734:3: Configuration error: MCPProcessor::initializeDB: can't chmod for directory (/config/filestore/files_d/<directory_names>) err (Permission denied). err mcpd[8710]: 01070596:3: An unexpected failure has occurred, can't chmod for directory (/config /filestore/files_d/<directory_names>) err (Permission denied). - sys/validation/FileObject.cpp, line 612, exiting... You observe error messages similar to the following in /var/log/ltm: 01420006:3: Loading configuration process failed. You observe error messages similar to the following in /var/log/auditd/audit.log (below is an example for an mcpd restart loop): Note: The message contains denied and unlabeled_t shown in bold below. type=AVC msg=audit(day_time): avc: denied { setattr } for pid=13624 comm="mcpd" name=" external_monitor_d" dev="dm-11" ino=307 scontext=system_u:system_r:mcpd_t:s0 tcontext=system_u:object_r:unlabeled_t:s0 tclass=dir The Configuration utility displays the following: The configuration has not yet loaded. -

Install and Run External Command Line Softwares
job monitor and control top: similar to windows task manager (space to refresh, q to exit) w: who is there ps: all running processes, PID, status, type ps -ef | grep yyin bg: move current process to background fg: move current process to foreground jobs: list running and suspended processes kill: kill processes kill pid (could find out using top or ps) 1 sort, cut, uniq, join, paste, sed, grep, awk, wc, diff, comm, cat All types of bioinformatics sequence analyses are essentially text processing. Unix Shell has the above commands that are very useful for processing texts and also allows the output from one command to be passed to another command as input using pipe (“|”). less cosmicRaw.txt | cut -f2,3,4,5,8,13 | awk '$5==22' | cut -f1 | sort -u | wc This makes the processing of files using Shell very convenient and very powerful: you do not need to write output to intermediate files or load all data into the memory. For example, combining different Unix commands for text processing is like passing an item through a manufacturing pipeline when you only care about the final product 2 Hands on example 1: cosmic mutation data - Go to UCSC genome browser website: http://genome.ucsc.edu/ - On the left, find the Downloads link - Click on Human - Click on Annotation database - Ctrl+f and then search “cosmic” - On “cosmic.txt.gz” right-click -> copy link address - Go to the terminal and wget the above link (middle click or Shift+Insert to paste what you copied) - Similarly, download the “cosmicRaw.txt.gz” file - Under your home, create a folder -

Install Guide - UNIX Oracle CSE
Information Engineering Technology Install Guide - UNIX Oracle CSE Release 8.7.3 © Information Engineering Technology Ltd 2020 www.iet.uk Table Of Contents Introduction ............................................................................................................................................................................... 3 Architecture .................................................................................................................................................................................... 3 Communications ............................................................................................................................................................................. 3 About The Installation Guides .................................................................................................................................................... 4 Software for Download .............................................................................................................................................................. 4 Server Install – UNIX / Oracle CSE ............................................................................................................................................... 5 Pre-Requisites ................................................................................................................................................................................. 5 Who Should Perform this Installation? .......................................................................................................................................... -

Regression Testing and Conformance Testing Interactive Programs
RegressionTesting and Conformance TestingInteractive Programs Don Libes- NationalInstitute of Standardsand Technology ABSTRACT _ Testinginteractive programs, by its nature,requires interaction - usuallyby real people. Such testing is an expensiveprocess and hencerarely done. Some interactivetools can ¡e used non-interactivelyto a limited extent, and are often tested only this way. Purely interactiveprograms are rarely testedin any systematicway. _ This paper describestesting of interactive line and character-orientedprograms via Expect. An immediate use of this is to build a test suite for automatingstandards conformanceof all of the interactiveprograms in POSH t003.2a (interactiveshells and tools),something which hasnot yet beenaccomplished by any means. Introduction does not produceoutput that is immediatelycon- sumed by another process, Dennis Ritchie said that "A program but may for example, tl] write designedfor inputs from people is usually stressed to a disk or display.) This is the environment beyond the breaking point by computer-generated in which Ritchie'sremark arose. inputs." I would add the following: Any program In practice,there are forms of input that pro- useful to people- interactively- is likely to be use- duction programsdo not generate.For example, ful to programs- non-interactively.A corollary of programsdo not make typing errorsand thereforedo Ritchie's statementis that conect softwarefunction not (press the backspaceor delete key to) delete during normalhuman use is not a very goodtest of a charactersjust produced.Similarly, programs do not program'stotal correctness. enter control characters,such as might be used to process. I claim that even when humansare explicitly interrupt a This suggeststhat Ritchie was too - teqtinginteractive software, the resultsare still quite optimistic even computergenerated inputs still unreliable. -

CS2043 - Unix Tools & Scripting Cornell University, Spring 20141
CS2043 - Unix Tools & Scripting Cornell University, Spring 20141 Instructor: Bruno Abrahao January 31, 2014 1 Slides evolved from previous versions by Hussam Abu-Libdeh and David Slater Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Vim: Tip of the day! Line numbers Displays line number in Vim: :set nu Hides line number in Vim: :set nonu Goes to line number: :line number Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Counting wc How many lines of code are in my new awesome program? How many words are in this document? Good for bragging rights Word, Character, Line, and Byte count with wc wc -l : count the number of lines wc -w : count the number of words wc -m : count the number of characters wc -c : count the number of bytes Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Sorting sort Sorts the lines of a text file alphabetically. sort -ru file sorts the file in reverse order and deletes duplicate lines. sort -n -k 2 -t : file sorts the file numerically by using the second column, separated by a colon Example Consider a file (numbers.txt) with the numbers 1, 5, 8, 11, 62 each on a separate line, then: $ sort numbers.txt $ sort numbers.txt -n 1 1 11 5 5 8 62 11 8 62 Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting uniq uniq uniq file - Discards all but one of successive identical lines uniq -c file - Prints the number of successive identical lines next to each line Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Character manipulation! The Translate Command tr [options] <char_list1> [char_list2] Translate or delete characters char lists are strings of characters By default, searches for characters in char list1 and replaces them with the ones that occupy the same position in char list2 Example: tr 'AEIOU' 'aeiou' - changes all capital vowels to lower case vowels Instructor: Bruno Abrahao CS2043 - Unix Tools & Scripting Pipes and redirection tr only receives input from standard input (stdin) i.e. -

File Security and Permissions
File Security and Permissions File Permissions (1) u With respect to a particular file, Unix divides the set of all users on a system into three categories: – user vThe owner of the file. – group users vMost of you are in the group 2ndyr vUsed for easier administration of access control. vNormally only the superuser can set up groups. vUsers can be in more than one group. – others vEveryone else. File Permissions (2) u Permissions can be viewed with the ls -l command obelix[1] > ls -l total 1247 -rw------- 1 csnow 1117 Jul 23 15:49 bad.cpp drwx--x--x 2 csnow 2048 Jul 17 10:13 bibd/ drwxr-xr-x 2 csnow 512 Aug 27 23:18 cache/ -rw------- 1 csnow 2081 Jul 23 15:49 tst2.s -rw-r-xr-- 1 csnow 1275 Jul 23 15:49 vecexpr.cpp r read permission -rw-r-xr-- w write permission x execute permission File type - = file d = directory User Group Other l=symbolic link Permissions Permissions Permissions File Permissions (3) u Permissions are changed with the chmod command. u There are two syntaxes you can use: chmod DDD file [file ...] – DDD are 3 octal digits representing bits of protection – rwx rwx rwx can be thought of as 111 111 111 in binary rw- r-- r-- 110 100 100 6 4 4 chmod 644 file File Permissions (4) u chmod [ugoa][+-=][rwx] file [...] – This is the “symbolic” method. – chmod u+rwx file gives the User Read, Write, and eXecute – chmod g+rx file gives the Group Read and eXecute – chmod o-rwx file removes R, W, and X from Others – chmod a+x file gives All eXecute permission – chmod g=r file gives Group Read permission and makes sure it has nothing