Be a Video Producer – Using Smartphones and Tablets
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Step 1 - Check Current Ios and Device
My Erickson/Touchtown recently had an upgrade and (Apple) iPhone and iPad users have experienced log in issues. This guide can help you walk through the process of updating the iOS. Step 1 - Check Current iOS and Device Make sure resident is connected to Wi-Fi and has their Apple ID and password to Apple ID Available Connect to Wi-FI Tap Settings Tap About Me Look for the Software Version and Model Name. If the software version (iOS) is 12.4.8 the resident will need to update to 13.0. If it is any other version - even older Do Not Update. If the device is listed below the resident will need to update to 13 from 12.4.8. Please follow the directions in this guide. If the device is Not listed below and the resident is on 12.4.8, the resident will be unable to update to 13 and they can access My Erickson through their web browser (Safari) at myerickson.erickson.com until IT can resolve the issues. (Or from your web browser on a desktop / laptop computer) List of iOS 13 Compatible iPhones iOS 13 iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max iPhone XS and iPhone XS Max iPhone XR iPhone X iPhone 8 and iPhone 8 Plus iPhone 7 and iPhone 7 Plus iPhone 6s and iPhone 6s Plus iPhone SE iPod touch (7th generation) List of iOS 13 Compatible iPads iPadOS 12.9-inch iPad Pro 11-inch iPad Pro 10.5-inch iPad Pro 9.7-inch iPad Pro iPad (7th generation), iPad (6th generation), and iPad (5th generation) iPad mini (5th generation) iPad mini 4 iPad Air (3rd generation) iPad Air 2 If the device is on the list, the next step will be to Back up the device prior to updating. -
Sidecar Sidecar Lets You Expand Your Mac Workspace—And Your Creativity—With Ipad and Apple Pencil
Sidecar Sidecar lets you expand your Mac workspace—and your creativity—with iPad and Apple Pencil. October 2019 Contents Overview ...............................................................................................................3 Easy setup ............................................................................................................4 iPad as second display ......................................................................................... 5 iPad as tablet input device ....................................................................................6 Additional features ...............................................................................................8 Sidecar | October 2019 2 Overview Key Features Adding a second display has been a popular way for Mac users to extend their desktop and spread out their work. With Sidecar, Extended desktop Mac users can now do the same thing with their iPad. iPad makes Expand your Mac workspace using your iPad as a second display. Place one app a gorgeous second display that is perfect in the office or on on each screen, or put your main canvas the go. Plus Sidecar enables using Apple Pencil for tablet input on one display and your tools and on Mac apps for the very first time. Convenient sidebar and palettes on the other. Touch Bar controls let users create without taking their hands off iPad. And they can interact using familiar Multi-Touch gestures Apple Pencil to pinch, swipe, and zoom; as well as new iPadOS text editing Use Apple Pencil for tablet input with your favorite creative professional gestures like copy, cut, paste, and more. Sidecar works equally Mac apps. well over a wired or wireless connection, so users can create while sitting at their desk or relaxing on the sofa. Sidebar The handy sidebar puts essential modifier keys like Command, Control, Shift, and Option right at your fingertips. Touch Bar Touch Bar provides app-specific controls at the bottom of the iPad screen, even if your Mac does not have Touch Bar. -

Apple Ios 13 on Iphone and Apple Ipados 13 on Ipad Mobile Devices
Apple Inc. Apple iOS 13 on iPhone and Apple iPadOS 13 on iPad Mobile Devices Security Target PP_MD_V3.1 with MOD_MDM_AGENT_V1.0, MOD_VPN_CLI_V2.1, PP_WLAN_CLI_EP_V1.0 Version 1.7 2020-11-10 VID: 11036 Prepared for: Prepared by: Apple Inc. atsec information security Corp. One Apple Park Way 9130 Jollyville Road, Suite 260 MS 927-1CPS Austin, TX 78759 Cupertino, CA 95014 www.atsec.com www.apple.com © 2020 Apple Inc. This document may be reproduced and distributed only in its original entirety without revision VID: 11036 Table of Contents Revision History ........................................................................................................................... 8 1 Security Target Introduction .............................................................................................. 10 1.1 Security Target Reference ........................................................................................... 10 1.2 TOE Reference ............................................................................................................. 10 1.3 TOE Overview ............................................................................................................... 10 1.4 TOE Description ............................................................................................................ 11 1.4.1 General information .......................................................................................... 11 1.4.2 Obtaining the mobile devices ......................................................................... -
Ios 13 Isnt Downloading If Your Iphone, Ipad Or Ipod Touch Won’T Update
ios 13 isnt downloading If your iPhone, iPad or iPod touch won’t update. You might be unable to update your iPhone, iPad, or iPod touch wirelessly — or over the air — for one of these reasons. Not enough available storage space on your device Downloading the update takes a long time Unable to reach the update server The update doesn't complete. If there's not enough space to update. If there isn't enough space to download and install an update, the software on your device will try to make space. It will remove only app data that it can download again and doesn't remove or relocate any of your data. If your device still doesn't have enough space, you can use your computer to update your device. If you can't connect your device to your computer, you can make room for the update by removing content and apps on your device that you don't use. Go to Settings > General > [Device name] Storage. If the download takes a long time. You need an Internet connection to update your device. The time it takes to download the update varies according to the size of the update and your Internet speed. You can use your device normally while downloading the update, and your device will notify you when you can install it. To improve the speed of the download, avoid downloading other content and use a Wi-Fi network if you can. If you can’t reach the update server or can’t verify the update. If you try to update your device, you might see one of these messages: "Unable to Check for Update. -
Ios 13 Upgrade Checklist
iOS 13 Upgrade Checklist Your step-by-step guide on how to upgrade your device to iOS 13 iOS 13 Upgrade Checklist Step 1: Eligibility The following devices are eligible to run iOS 13: iPhone: SE, 6S, 6S Plus, 7, 7 Plus, 8, 8 Plus, X, XR, XS, XS Max, 11, 11 Pro, 11 Pro Max iPad: Mini 4, Mini 5, Air 2, Air 3, 9.7-inch gen 5 & 6, 10.2-inch gen 7, all Pro models iPod Touch: 7th Gen Not sure which device you have? Then visit https://support.apple.com/HT201296 My device is eligible for the iOS 13 upgrade Step 2: Device backup As the saying goes, better be safe than sorry, so before upgrading to iOS 13, please perform at least 1 backup of your device, preferably 2. If you have a compatible computer, then perform an encrypted backup of your device via iTunes (Windows PC or macOS 10.14 or earlier) or Finder (macOS 10.15 or later): 1. If needed, update iTunes on your computer 2. Launch iTunes/Finder and connect your device to your computer via USB 1. If it’s the first time, you’ll need to click on « Trust » then enter your iOS device passcode 3. Access the panel with your device (device icon in iTunes or device name in Finder) 4. Tick the box “Encrypt local backup” and enter a password 5. Click on “Back Up Now” and wait until it’s finished 6. Archive the backup by right-clicking on the last one performed: 1. On Windows/macOS 10.14 and earlier, open iTunes preference pane, click on « Devices » 2. -

Ios and Ipados Deployment Overview Introduction Introduction
iOS and iPadOS Deployment Overview Introduction Introduction Contents iPhone and iPad can transform your business and how your Introduction employees work. They can significantly boost productivity and Ownership Models give your employees the freedom and flexibility to work in new Deployment Steps ways, whether in the office or on the go. Embracing this modern Support Options way of working leads to benefits across the entire organization. Summary Users have better access to information, so they feel empowered and are able to creatively solve problems. By supporting iOS and iPadOS, IT departments are viewed as shaping the business strategy and solving real-world problems, rather than just fixing technology and cutting costs. Ultimately everyone benefits, with an invigorated workforce and new business opportunities everywhere. Setting up and deploying iPhone and iPad throughout your business has never been easier. With Apple Business Manager and a third-party mobile device management (MDM) solution, your organization can easily deploy iOS and iPadOS devices and apps at scale. • Mobile device management allows you to configure and manage devices, and wirelessly distribute and manage apps. • Apple Business Manager automates enrollment of Apple devices into your MDM solution to streamline deployment with zero-touch configuration for IT. • Apple Business Manager lets you purchase apps and books in bulk and distribute them to users wirelessly. • Apple Business Manager also lets you create Managed Apple IDs for employees using federated authentication with Microsoft Azure AD. This document offers guidance on deploying iOS and iPadOS devices in your organization and helps you create a deployment plan that best suits your environment. -

What's New with Ios
What’s New with iOS 13? Jere Minich Program Chair, Lake Sumter Computer Society APCUG Advisor Region 5 [email protected] Scope of iOS 13. Sept 19, 2019 • Apple's newest operating system for iPhones and iPads. • Features: Systemwide Dark Mode; Revamped Photos App; New Photo editing interface; Sign in with Apple option; Location data limits; Look Around view in Maps; New Reminders App. • Faster and more efficient. (Apple’s claim) • 56 “How to” web pages with screenshots. (one site) • iOS 13; iOS 13.1; iOS 13.1.1; iOS 13.1.2; iOS 13.1.3; iOS 13.2 iOS 13 How To’s • How to Enable Dark Mode in iOS 13 • How to Silence Unknown Callers on Your iPhone in iOS 13 • How to Save or Share a Safari Web Page as a PDF in iOS 13 • How to Reduce Your iPhone or iPad Network Data Usage With iOS 13's Low Data Mode • How to Mute Email Threads in iOS 13 • How to Block People From Sending You Mail in iOS 13 • How to Search Your Messages in iOS 13 • How to Use Animoji and Memoji Stickers in iOS 13 • How to Create a Custom iMessage Profile in iOS 13 • How to See Links, Attachments, and Photos From a Messages Conversation • How to Change Who Sees Your Messages Profile in iOS 13 • Approx. 56 How To’s at this one (1) web site. • MacRumors How to’s. https://www.macrumors.com/roundup/ios-13/ • http://bit.ly/2Nr3udy iOS 13 How To’s • Open this page in the Power Point Presentation on the device. -

Resound Smart 3D App and Ios 13 Compatibility
Important notes about the iOS 13, 13.1 and 13.1.2 The ReSound Smart 3D and Smart app platforms, and all compatible hearing aids, are now verified compatible with iOS 13.1.2. But there are still some iOS and iPhone related defects as well as changes to iOS behavior which may impact our users: 1. iOS 13 was released with several defects, which caused issues for ReSound apps and hearing aids (including connectivity issues): Make sure iOS users are upgraded to iOS 13.1.2 to minimize issues with hearing devices 2. iOS 13 and later have moved the accessibility menu, where you pair MFi hearing aids: from Settings / General / Accessibility / MFi Hearing Devices to Settings / Accessibility / Hearing Devices The pairing flow and MFi settings are the same as on iOS 12, find more info here: https://support.apple.com/HT201466 3. iOS 13 and later will ask users for permission to find and connect to Bluetooth Devices on first launch of the app after upgrading iOS version. The app can only connect to the hearing instruments if the user selects “OK”. If the user selects “Don’t Allow”, the app will not connect but show a red exclamation mark with the text “Please turn on Bluetooth”: Bluetooth permission on first launch: Message in app if ‘Don’t User must select OK Allow’ is selected Follow these steps to allow the app to use Bluetooth again: a. Go to Settings / [name of the app] b. Turn on Bluetooth Go to Settings / [app name] to allow the app to use Bluetooth again 4. -
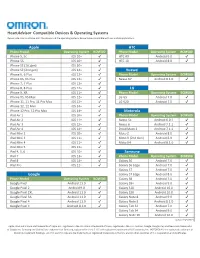
OMRON App Compatibility Matrix 172021.Xlsx
HeartAdvisor Compatible Devices & Operating Systems Please note: You must have both the device and the operating systems below to be compatible with our mobile applications. Apple HTC Phone Model Operating System BCM500 Phone Model Operating System BCM500 iPhone 5, 5c iOS 10+ ✔ HTC A9 Android 6.0 ✔ iPhone 5S iOS 10+ ✔ HTC 10 Android 8.0 ✔ iPhone SE (1st gen) iOS 10+ ✔ iPhone SE (2nd gen) iOS 14+ ✔ Huawei iPhone 6, 6 Plus iOS 12+ ✔ Phone Model Operating System BCM500 iPhone 6S, 6S Plus iOS 12+ ✔ Nexus 6P Android 8.1.0 ✔ iPhone 7, 7 Plus iOS 12+ ✔ iPhone 8, 8 Plus iOS 12+ ✔ LG iPhone X, XR iOS 11+ ✔ Phone Model Operating System BCM500 iPhone XS, XS Max iOS 12+ ✔ LG G5 Android 7.0 ✔ iPhone 11, 11 Pro, 11 Pro Max iOS 13+ ✔ LG V20 Android 7.0 ✔ iPhone 12, 12 Mini iOS 14+ ✔ iPhone 12 Pro, 12 Pro Max iOS 14+ ✔ Motorola iPad Air 1 iOS 10+ ✔ Phone Model Operating System BCM500 iPad Air 2 iOS 11+ ✔ Nexus 5x Android 6.0.1 ✔ iPad Air 3 iOS 12+ ✔ Nexus 6 Android 7.1.1 ✔ iPad Air 4 iOS 14+ ✔ Droid Maxx 2 Android 7.1.1 ✔ iPad Mini 2 iOS 10+ ✔ Moto Z Android 8.0 ✔ iPad Mini 3 iOS 11+ ✔ Moto X (2nd Gen) Android 6.0 ✔ iPad Mini 4 iOS 11+ ✔ Moto X4 Android 8.1.0 ✔ iPad Mini 5 iOS 12+ ✔ iPad 4, 5, 6 iOS 10+ ✔ Samsung iPad 7 iOS 13+ ✔ Phone Model Operating System BCM500 iPad 8 iOS 14+ ✔ Galaxy S6 Android 7.0 ✔ iPad Pro iOS 11+ ✔ Galaxy S6 Edge Android 7.0 ✔ Galaxy S7 Android 7.0 ✔ Google Galaxy S7 Edge Android 8.0 ✔ Phone Model Operating System BCM500 Galaxy S8 Android 7.0 ✔ Google Pixel Android 11.0 ✔ Galaxy S9+ Android 9.0 ✔ Google Pixel 2 Android 9.0 ✔ Galaxy S10 Android 10.0 ✔ Google Pixel 2XL Android 11.0 ✔ Galaxy S20 Android 10.0 ✔ Google Pixel 3A Android 11.0 ✔ Galaxy Note 8 Android 9.0 ✔ Google Pixel 4 Android 11.0 ✔ Galaxy Note 9 Android 8.1.0 ✔ Google Pixel C Android 8.1.0 ✔ Galaxy Tab S2 Android 7.0 ✔ Galaxy Tab S4 Android 9.0 ✔ Galaxy Note 10 Android 10.0 ✔ updated 3/5/2021 Apple, iPad and iPhone are trademarks of Apple Inc., registered in the U.S. -

Story of Jailbreaking Ios 13
Black Hat Europe 2020 London, United Kingdom Story of Jailbreaking iOS 13 Author: 08tc3wbb ([email protected]) Revision by Zuk Avaraham, Raz Mashat Outlines - Review iOS Sandbox weaknesses - Exploit Userland vulnerability CVE-????-???? (iOS 12.0 - iOS 14.1) - Looking for similar bugs - Attack AVEVideoEncoder component - Exploit Kernel vulnerability CVE-2019-8795 (iOS 12.0 - iOS 13.1.3) - Exploit Kernel vulnerability CVE-2020-9907 (iOS 13.2 - iOS 13.5.1) - Exploit Kernel vulnerability CVE-????-???? (iOS 13.6 - iOS 13.7) iOS security consists of many layers, and hackers can find vulnerabilities in different layers to gain different levels of access, and it's also possible to link multiple vulnerabilities together to form an exploit chain. The unique aspect of this paper is to analyze the threat from userland vulnerabilities, and then use its advantages to attack the neglected kernel weaknesses, thereby completing the privilege escalation from the user to the kernel. It may not sound as cool as attacking the kernel directly. Still, it has been proven to be a practical method for jailbreaking. Also, such exploits are eligible for various bounty programs and are well hidden, which reduces the chance of bug collision. These are important factors that an independent researcher needs to consider before deciding to enter the field full-time. A general term "Sandbox" refers to similar security mechanisms for separating running programs by controlling the power and resources that a process may use. It's customizable and evolvable. Thus it lets Apple neutralize many kinds of vulnerabilities in a very short period of time, with almost no overhead added. -
Ios 13 & Ipados 13 Accessibility
iOS 13 & iPadOS 13 Accessibility Switch Control - The Missing User Guide Table of Contents New Switch Control Features In iOS 13 and iPadOS 13 ..........................................................................................2 Switch Interface Options ...............................................................................................................................................2 Configuring Switch Control - Auto Configuration ....................................................................................................3 Configuring Switch Control - Single Switch Auto Scanning ..................................................................................3 - 6 Configuring Switch Control - Single Switch Step Scanning..................................................................................6 - 9 Configuring Switch Control - Dual Switch Step Scanning ....................................................................................9 - 12 Switch Control App Developer Resources .................................................................................................................12 New Switch Control Features In iOS 13 and iPadOS 13 IPADOS AND IOS New this year is iPadOS 13. Previously iOS was the operating system for iPhone, iPad, and iPod touch devices. Now, iOS 13 is the operating system for all iPhone and iPod touch devices. iPadOS 13 is the operating system for all iPad devices. Accessibility settings in both iPadOS 13 and iOS 13 are almost identical. ACCESSIBILITY SETTINGS Accessibility -

Authenticating Ios 12, 13, and 14 Videos Using Metadata and Hex Code
AUTHENTICATING IOS 12, 13, AND 14 VIDEOS USING METADATA AND HEX CODE by ANDREW ELLIS WEST B.S, Utah Valley University, 2018 A thesis submitted to the Faculty of the Graduate School of the University of Colorado in partial fulfillment of the requirements for the degree of Master of Science Recording Arts Program 2020 © 2020 ANDREW ELLIS WEST ALL RIGHTS RESERVED ii This thesis for the Master of Science degree by Andrew Ellis West has been approved for the Recording Arts Program by Catalin Grigoras, Chair Cole M. Whitecotton Gregory S. Wales Date: December 12, 2020 iii West, Andrew Ellis (M.S., Recording Arts Program) Authenticating iOS 12, 13, and 14 Videos Using Metadata and Hex Code Thesis directed by Associate Professor Catalin Grigoras ABSTRACT The ability to record, edit, and share videos using the same device has created the culture behind the phrase, “pics or it didn’t happen”. This new shift in culture has allowed consumers to record and share as much as they can with their friends and family. Leading the way for this way of communicating is the popular Apple smartphone line. Its popularity stems from its impressive line of smartphone and tablet products, making iOS one of the main operating systems for consumer technology. The prevalence of this lifestyle change has also increased the number of videos taken by bystanders or suspects while crimes are taking place. With the ability to natively edit videos introduced in iOS 12, this causes concern for forensic analysts who have to authenticate these videos. In order to prove that we know a video has been edited using the native “Photo” application, we must create an approach on how to authenticate the video metadata found within the file.