I847 Rugby Smart User Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2014 BT Compatibility List 20141030
Item Brand Name Model 1 Acer Acer beTouch E210 2 Acer acer E400 3 Acer acer P400 4 Acer DX650 5 Acer E200 6 Acer Liquid E 7 Acer Liquid Mini (E310) 8 Acer M900 9 Acer S110 10 Acer Smart handheld 11 Acer Smart handheld 12 Acer Smart handheld E100 13 Acer Smart handheld E101 14 Adec & Partner AG AG vegas 15 Alcatel Alcatel OneTouch Fierce 2 16 Alcatel MISS SIXTY MSX10 17 Alcatel OT-800/ OT-800A 18 Alcatel OT-802/ OT-802A 19 Alcatel OT-806/ OT-806A/ OT-806D/ OT-807/ OT-807A/ OT-807D 20 Alcatel OT-808/ OT-808A 21 Alcatel OT-880/ OT-880A 22 Alcatel OT-980/ OT-980A 23 Altek Altek A14 24 Amazon Amazon Fire Phone 25 Amgoo Telecom Co LTD AM83 26 Apple Apple iPhone 4S 27 Apple Apple iPhone 5 28 Apple Apple iPhone 6 29 Apple Apple iPhone 6 Plus 30 Apple iPhone 2G 31 Apple iPhone 3G 32 Apple iPhone 3Gs 33 Apple iPhone 4 34 Apple iPhone 5C 35 Apple iPHone 5S 36 Aramasmobile.com ZX021 37 Ascom Sweden AB 3749 38 Asustek 1000846 39 Asustek A10 40 Asustek G60 41 Asustek Galaxy3_L and Galaxy3_S 42 Asustek Garmin-ASUS M10E 43 Asustek P320 44 Asustek P565c 45 BlackBerry BlackBerry Passport 46 BlackBerry BlackBerry Q10 47 Broadcom Corporation BTL-A 48 Casio Hitachi C721 49 Cellnet 7 Inc. DG-805 Cellon Communications 50 C2052, Technology(Shenzhen) Co., Ltd. Cellon Communications 51 C2053, Technology(Shenzhen) Co., Ltd. Cellon Communications 52 C3031 Technology(Shenzhen) Co., Ltd. Cellon Communications 53 C5030, Technology(Shenzhen) Co., Ltd. -

Device Eligibility and Deductible Schedule for Mobile Insurance* (Standalone Or As Part of Mobile Protection Pack)
Device Eligibility and Deductible Schedule For Mobile Insurance* (standalone or as part of Mobile Protection Pack) 11/1/2015 Update The Equipment Tier List is updated regularly to include new models. Devices introduced under Equipment Tier 2 or Equipment Tier 3 may be moved to a lower tier during their lifecycle. The non- refundable deductible is based on the device in use and the equipment tier assigned on the date of loss. If you are not certain of the model of your device, refer to your original receipt or you may be able to determine the model by following these steps (if applicable): Turn the power off. Carefully remove the battery cover and the battery. The model is typically printed on the white label located under the battery. This list is changed from time to time. Please check this list any time your equipment changes. AT&T Mobile Insurance (standalone or as part of Mobile Protection Pack) is not available for and coverage does not apply to: Samsung Galaxy Camera™ (EK-GC100A) PlayStation® Vita Amazon Kindle™ Amazon Kindle™ Touch 3 BlackBerry® PlayBook™ Phones on GoPhone® accounts Tablets with prepaid data plans AT&T MicroCell™ Phone or device models not sold by AT&T Docks (such as for the Motorola ATRIX 4G) Eligibility is subject to change. Protect Plus app Please visit att.com/protectplus to view app device compatibility. *AT&T Mobile Insurance is underwritten by Continental Casualty Company, a CNA company (CNA), and administered by Asurion Protection Services, LLC (In California, Asurion Protection Services Insurance Agency, LLC, CA Lic. -
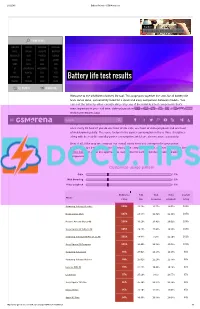
Battery Life Test Results HUAWEI TOSHIBA INTEX PLUM
2/12/2015 Battery life tests GSMArena.com Starborn SAMSUNG GALAXY S6 EDGE+ REVIEW PHONE FINDER SAMSUNG LENOVO VODAFONE VERYKOOL APPLE XIAOMI GIGABYTE MAXWEST MICROSOFT ACER PANTECH CELKON NOKIA ASUS XOLO GIONEE SONY OPPO LAVA VIVO LG BLACKBERRY MICROMAX NIU HTC ALCATEL BLU YEZZ MOTOROLA ZTE SPICE PARLA Battery life test results HUAWEI TOSHIBA INTEX PLUM ALL BRANDS RUMOR MILL Welcome to the GSMArena battery life tool. This page puts together the stats for all battery life tests we've done, conveniently listed for a quick and easy comparison between models. You can sort the table by either overall rating or by any of the individual test components that's most important to you call time, video playback or web browsing.TIP US 828K 100K You can find all about our84K 137K RSS LOG IN SIGN UP testing procedures here. SearchOur overall rating gives you an idea of how much battery backup you can get on a single charge. An overall rating of 40h means that you'll need to fully charge the device in question once every 40 hours if you do one hour of 3G calls, one hour of video playback and one hour of web browsing daily. The score factors in the power consumption in these three disciplines along with the reallife standby power consumption, which we also measure separately. Best of all, if the way we compute our overall rating does not correspond to your usage pattern, you are free to adjust the different usage components to get a closer match. Use the sliders below to adjust the approximate usage time for each of the three battery draining components. -

Apple Iphone Gen1 16GB 3.00 $ Iphone 4S 16GB (Verizon) 75.00
EcoPhones Fundraising Buy-Back Price List Price List Effective 05.01.14 CELL PHONES We pay up to $350.00 per cell phone! We pay something for every cell phone - listed or not, working or damaged! View program rules for details regarding qualifying and non-qualifying items as well as working and non-working definitions (Click Here) Apple iPhone Gen1 16GB $ 3.00 iPhone 4S 16GB (Verizon) $ 75.00 iPhone 5 64GB (Sprint) $ 250.00 iPhone Gen1 4GB $ 3.00 iPhone 4S 32GB (AT&T) $ 100.00 iPhone 5 64GB (T-Mobile) $ 250.00 iPhone Gen1 8GB $ 3.00 iPhone 4S 32GB (Other Carrier) $ 100.00 iPhone 5 64GB (Unlocked) $ 250.00 iPhone 3G 16GB (AT&T) $ 5.00 iPhone 4S 32GB (Sprint) $ 100.00 iPhone 5 64GB (Verizon) $ 250.00 iPhone 3G 16GB (Unlocked) $ 5.00 iPhone 4s 32GB (Unlocked) $ 100.00 iPhone 5c 16GB (AT&T) $ 200.00 iPhone 3G 8GB (AT&T) $ 5.00 iPhone 4S 32GB (Verizon) $ 100.00 iPhone 5c 16GB (Sprint) $ 200.00 iPhone 3G 8GB (Unlocked) $ 5.00 iPhone 4S 64GB (AT&T) $ 150.00 iPhone 5c 16GB (T-Mobile) $ 200.00 iPhone 3Gs 16GB (AT&T) $ 10.00 iPhone 4S 64GB (Other Carrier) $ 150.00 iPhone 5c 16GB (Unlocked) $ 200.00 iPhone 3Gs 16GB (Unlocked) $ 10.00 iPhone 4S 64GB (Sprint) $ 150.00 iPhone 5c 16GB (Verizon) $ 200.00 iPhone 3Gs 32GB (AT&T) $ 15.00 iPhone 4s 64GB (Unlocked) $ 150.00 iPhone 5c 32GB (AT&T) $ 225.00 iPhone 3Gs 32GB (Unlocked) $ 15.00 iPhone 4S 64GB (Verizon) $ 150.00 iPhone 5c 32GB (Sprint) $ 225.00 iPhone 3Gs 8GB (AT&T) $ 5.00 iPhone 4S 8GB (AT&T) $ 50.00 iPhone 5c 32GB (T-Mobile) $ 225.00 iPhone 3Gs 8GB (Unlocked) $ 5.00 iPhone 4S 8GB (Sprint) $ 50.00 -

Apple Apple Apple $44.00 $220.00 $335.00
Price valid on product shipped between November 1st and November 30th and is subject to approval. Find My iPhone/Find My iPad must be removed. Page 1 November 2014 Apple Apple Apple iPad 16GB $44.00 iPad 4th Gen 4G 32GB $220.00 iPad Air 4G 64GB $335.00 iPad 32GB $48.00 iPad 4th Gen 4G 64GB $240.00 iPad Air 4G 128GB $365.00 iPhone 4GB iPad 64GB iPad 4th Gen 4G 128GB $51.00 $260.00 1st Gen $2.00 iPhone 8GB iPad 16GB 3G iPad Mini 16GB $50.00 $110.00 1st Gen $3.00 iPhone 16GB iPad 32GB 3G iPad Mini 32GB $52.00 $140.00 1st Gen $5.00 iPad 64GB 3G $55.00 iPad Mini 64GB $175.00 iPhone 3G 8GB $5.00 iPad 2 16GB $100.00 iPad Mini 4G 16GB $130.00 iPhone 3G 16GB $6.00 iPad 2 32GB $110.00 iPad Mini 4G 32GB $150.00 iPhone 3G S 8GB $8.00 iPad 2 64GB $125.00 iPad Mini 4G 64GB $175.00 iPhone 3G S 16GB $11.00 iPad Mini 2nd Gen Retina iPad 2 16GB 3G iPhone 3G S 32GB $105.00 16GB $190.00 $13.00 iPad Mini 2nd Gen Retina iPad 2 32GB 3G iPhone 4 8GB GSM $115.00 32GB $220.00 $34.00 iPad Mini 2nd Gen Retina iPad 2 64GB 3G iPhone 4 8GB Sprint $130.00 64GB $250.00 $23.00 iPad Mini 2nd Gen Retina iPad 3rd Gen 16GB iPhone 4 8GB Verizon $130.00 128GB $290.00 $28.00 iPad Mini 2nd Gen Retina iPad 3rd Gen 32GB iPhone 4 16GB GSM $145.00 4G 16GB $200.00 $38.00 iPad Mini 2nd Gen Retina iPad 3rd Gen 64GB iPhone 4 16GB Verizon $175.00 4G 32GB $230.00 $40.00 iPad Mini 2nd Gen Retina iPad 3rd Gen 4G 16GB iPhone 4 32GB GSM $135.00 4G 64GB $260.00 $41.00 iPad Mini 2nd Gen Retina iPad 3rd Gen 4G 32GB iPhone 4 32GB Verizon $165.00 4G 128GB $310.00 $42.00 iPad 3rd Gen 4G 64GB $185.00 -

Factory Model Device Model
Factory Model Device Model Acer A1-713 acer_aprilia Acer A1-830 Avvio_753 Acer A1-830 X958E Acer A3-A20 8675 Acer Acer E320-orange C6 Acer Acer E320-orange Oysters T72MR 3G Acer AT390 QMobile i10 Acer AT390 T2 Acer AT390 Xiaomi Acer B1-723 oban Acer B1-730 a29 Acer B1-820 i-mobile2.8 Acer CloudMobile S500 a9 Acer DA220HQL gilda_p8081 Acer DA226HQ sm618_w_ztc_72lca Acer E120 K2 Acer E310 lava75_cu_jb Acer E330 A37 Acer E330 C7 Acer E330 G910 Acer E330 msm8x25q_d5 Acer E330 Z50_Nova Acer E350 C8n Acer G100W F13 Acer Iconia Tab 7 acer_apriliahd Acer Iconia Tab A211 g12refM805 Acer Iconia Tab A211 MYPHONE_AGUA_OCEAN_MINI Acer Iconia Tab A501 E353I Acer Iconia Tab A510 K235 Acer Iconia TalkTab 7 acer_a1_724 Acer Iconia TalkTab 7 d3268_ctp_q_mobile Acer Liquid a1 Acer Liquid C1 I1 Acer Liquid C1 s620_f_h1_trx_j401_ec Acer Liquid E1 C10 Acer Liquid E2 C11 Acer Liquid E3 acer_e3 Acer Liquid E3 acer_e3n Acer Liquid E3 D7.2 3G Acer Liquid E3 hedy89_we_jb2 Acer Liquid E3 SOLO Acer Liquid E600 e600 Acer Liquid E600 S5J Acer Liquid E600 z3368 Acer Liquid E700 acer_e39 Acer Liquid Gallant E350 C8 Acer Liquid Jade acer_S55 Acer Liquid Jade S acer_S56 Acer Liquid Jade Z ABCD Acer Liquid Jade Z acer_S57 Acer Liquid Jade Z k002_gfen Acer Liquid Jade Z mobiistar BUDDY Acer Liquid Mini Bmobile.AX800 Acer Liquid Mini C4R Acer Liquid S1 a10 Acer Liquid S2 a12 Acer Liquid S2 B706 Acer Liquid S3 FIREFLY_S10DUAL Acer Liquid S3 s3 Acer Liquid X2 acer_S59 Acer Liquid X2 g517_d1e_less26 Acer Liquid Z200 A1000s Acer Liquid Z200 acer_z200 Acer Liquid Z200 s9201b Acer -

Retail Packaging - Red
Cyber Monday LUXA2 LH0013-B H5- Premium Car Mount - Retail Packaging - Red Buy Cyber Monday LUXA2 LH0013-B H5- Premium Car Mount - Retail Packaging - Red top quality Smartphone and Accessory that you can purchase currently at affordable price. See Product Image | Check Cyber Monday Price Now | Customer Reviews Most of the consumer reviews recognize that this LUXA2 LH0013-B H5- Premium Car Mount - Retail Packaging - Red really are excellent quality Smartphone and Accessory and it is too priced reasonably. It can be find any testimony from users which can discover more about their own experience. The information will help you to understand a good indication with the benefits and dependability of these products. Total, It is the high quality item and we're surely suggest this item. When everyone searching for good quality Smartphone and Accessory at a less expensive, LUXA2 LH0013-B H5- Premium Car Mount - Retail Packaging - Red can be the one. Where to Purchase Cyber Monday Sale LUXA2 LH0013-B H5- Premium Car Mount - Retail Packaging - Red Quickly? Right now most affordable Phone and Accessory available for sale, find a item specifications that fits your needs and at a cost you may be completely satisfied. Best to order LUXA2 LH0013-B H5- Premium Car Mount - Retail Packaging - Red one of good quality product at this time with reasonable, low priced shipping and secure online payment system at Amazon.com the perfect online store. Following our check for low-priced product, we have discovered cheap price with save delivery. Generally really fast shipping for eligible product. Short Time Offers! Never miss to choose the great offers by authentic online stores. -

• 3 SKYPE • Phone WP-S1 • 3M • MP160 • MP180 • Mpro 110 Micro
3 SKYPE Liquid S110 mini PocketDV 8900 T483L One Touch 565A One Touch V212 OT-606C Phone WP-S1 N300 mini PocketDV M1 AITO One Touch 600 One Touch V270 OT-660 3M N310 MPVR Digital Media A-23002 One Touch 600A One Touch V570 OT-660A MP160 N311 MZ-DV ALCATEL One Touch 602 One Touch V570A OT-665 MP180 N320 Pocket DV-5700 890D One Touch 660 One Touch XTRA OT-665X MPro 110 Micro Projector N321 Pocket DV-8700 Crystal One Touch 660A OT-103 OT-706 Mpro 120 N500 Pocket DV-8800LE Elle No3 One Touch 665 OT-103A OT-706A Mpro 120 Micro Projector neoTouch P400 Pocket DV-H100 GYARI One Touch 706 OT-105 OT-708A Mpro 150 NeoTouch S110 PocketCam 8900 Miss Sixty One Touch 706A OT-105A OT-710 Mpro 150 Micro neoTouch S200 PocketDV AHD-100 M-tel E98 One Touch 710 OT-106 OT-710A Professional Projector Newtouch S200 PocketDV AHD-200 One Touc 908 One Touch 710A OT-108 OT-710D Mpro 150 Micro Projector S110 PocketDV AHD-300 One Touc 990 One Touch 710D OT-109 OT-799 3SKYPE S300 PocketDV AHD-C100 One Touch E227A One Touch 799 OT-111 OT-799A S2x Stream PocketDV AHD-Z500 One Touch V270A One Touch 799A OT-153 OT-800 4G SYSTEMS Tempo DX650 PocketDV AHD-Z500 Plus One Touch 103 One Touch 800 OT-155 OT-800A XSB6X G0 Tempo DX900 PocketDV C600 pro One Touch 103A One Touch 800A OT-203 OT-802 ACER Tempo M900 PocketDV DDV-V1 One Touch 105 One Touch 802 OT-203A OT-802A beTouch E100 ACOUSTIC RESEARCH PocketDV T200 One Touch 105A One Touch 802A OT-203E OT-802Y -
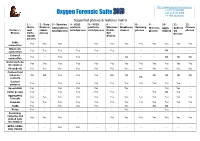
Oxygen Forensic Suite
http://www.oxygen-forensic.com +1 877 9 OXYGEN Oxygen Forensic Suite +44 20 8133 8450 +7 495 222 9278 Supported phones & features matrix 1 – 2 - Sony 3 – Symbian 4 - UIQ2 5 – UIQ3 6 - 7 - 8- 9- 10- 11- 12- Nokia Ericsson S60 platform platform platform Windows Blackberry Samsung Motorola Apple Android Chinese Feature \ and classic smartphones smartphones smartphones Mobile devices phones phones devices OS phones Phones Vertu phones 5/6 devices classic devices phones Cable Yes Yes Yes - Yes Yes Yes Yes Yes Yes Yes Yes connection Bluetooth Yes Yes Yes Yes Yes Yes - - - NA - - connection Infrared Yes - Yes Yes - - NA - - NA NA NA connection General phone Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes information Phonebook Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Custom field labels for NA NA Yes Yes Yes NA NA NA NA NA NA contacts NA Contact Yes - Yes Yes Yes Yes Yes Yes Yes Yes Yes - pictures Speed dials Yes - Yes Yes Yes - Yes - - Yes Yes - Caller groups Yes - Yes Yes Yes Yes - - Yes NA Yes - Aggregated Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Contacts Calendar Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Tasks Yes - Yes Yes Yes - Yes - NA NA - - Notes Yes - - - - - Yes - - Yes - - Incoming, outgoing and Yes Yes Yes - - Yes Yes Yes Yes Yes Yes Yes missed calls information GPRS, EDGE, - - Yes Yes - - - - - - - CSD, HSCSD - and Wi-Fi traffic and sessions log Sent and received SMS, - Sent SMS - Yes Yes Yes(2) - - - - - - MMS, E-mail messages log Deleted - messages - - Yes(1) - Yes(1) - - - Yes(8) - - information Flash SMS -

Multi-Device Insurance (Part of Multi-Device Protection Pack) Device Eligibility and Deductible Schedule
Multi-Device Insurance (part of Multi-Device Protection Pack) Device Eligibility and Deductible Schedule 3/1/2015 Update Devices connected to the AT&T network: The Equipment Tier list is updated regularly to include new models. This list applies to only the devices connected to the AT&T network. Devices introduced under Equipment Tier 2 or Equipment Tier 3 may be moved to a lower Tier during their lifecycle. The non-refundable deductible is based on the date of loss. If you are not certain of the model of your device, refer to your original receipt or you may be able to determine the model by following these steps (if applicable): Turn the power off. Carefully remove the battery cover and the battery. The model is typically printed on the white label located under the battery. This list is changed from time to time. Please check this list any time your equipment changes. Multi-Device Insurance for devices connected to the AT&T network is not available for and coverage does not apply to: Galaxy Camera (EK-GC100A) Blackberry Playbook ® Phones on GoPhone accounts Tablets with pre-paid data plans PlayStation® Vita AT&T 3G MicroCell Phone or device models not sold by AT&T (e.g., Dell Streak, Google Nexus One, TerreStar Genus) Docks (such as for the Motorola ATRIX 4G) Amazon Kindle Eligibility is subject to change. Devices not connected to the AT&T network (wi-fi): Multi-Device Insurance for Non-Connected Eligible Devices are not included in the Equipment Tier list below, but are charged a non-refundable deductible at the time of a repair ($89) or replacement ($199) as set forth in the Deductible Schedule directly below. -

New Logical Extraction Support for Android Apps Data Exclusive!
DECEMBER, 2012 TING SUPPOR 6 4 S 9 FILE , RO 9 E P IC DEV New logical extraction support for Android Forensic method New Total Logical extraction 217 4827 apps data Physical extraction* 363 2216 Apps data such as contacts, chats, calls and locations are often important File system extraction 249 1858 information sources in an investigation. UFED users can now acquire apps data Password extraction 186 1045 from Android devices via logical extraction. UFED Physical/Logical Analyzer is Total device profiles 1015 9946 required to analyze the apps data. *Including GPS devices Supported Apps: Facebook, Facebook UFED Messenger, Google+, PingChat! (aka Touch), Skype, Twitter, Viber, Yahoo Samsung Galaxy SIII Family – Messenger, Whatsapp, TigerText, Dropbox, Physical and file system QIP, Kik Messenger, Evernote, Kakao Talk, extraction, and decoding ICQ, Vkontakte and more Android 4.2.x – Logical, file Note: The apps data will not be part of the UFED system, and physical extraction HTML and XML reports. support Nokia BB5 – Physical extraction from an additional 21 locked and unlocked devices iPad 4 and iPad mini - Logical extraction support Nokia DCT4, DCT4+ and BB5 – Password extraction on selected devices Mass storage devices – Physical extraction is also supported via UFED Touch in addition to UFED Physical Analyzer Remaining time display in UFED Touch while performing physical Exclusive! Disable phone lock on selected and file system extraction New tool for releasing Samsung Samsung Android devices Android devices in ODIN mode is now available under device tools UFED can now disable pattern, PIN or password locks on selected Samsung Android devices using cable 130, to perform any type of extraction – logical, file system and physical. -

Summary of Compatible Phones
Summary of Compatible Phones The summary on this page and the next includes recently released phones that support hands-free calls, Bluetooth audio streaming, and EntuneTM applications. Some phones also support additional features. Please refer to the following pages for a Complete List of Phones Tested to Date and their detailed compatibility test results. Head Unit Compatible Phones Display Audio with Navigation and EntuneTM Carrier Manufacturer Model Operating System iPhone 3Gs iOS 6.0 (10A403) Apple iPhone 4S iOS 6.0 (10A403) PD98120 (Inspire 4G) Android 2.3.3 HTC PH39100 (Vivid) Android 4.0.3 PM63100 (One X Plus) Android 4.1.1 Vehicles Huawei U8800-51 (Impulse 4G) Android 2.2.2 4Runner 2012. 2013 Highlander Hybrid 2013 LG-E970 (Optimus G) Android 4.0.4 Avalon 2013 Prius 2012, 2013 LG AT&T Wireless Avalon Hybrid 2013 Prius c 2012, 2013 LG-P930 (Nitro HD) Android 2.3.5 Camry 2012, 2013 Prius Plug-in Hybrid 2012, 2013 MB865 (Atrix 2) Android 2.3.6 Motorola Camry Hybrid 2012, 2013 Prius v 2012, 2013 MB886 (Atrix HD) Android 4.0.4 RAV4 2012, 2013 Corolla 2012, 2013 Tacoma 2012, 2013 Highlander 2013 SGH-i317 (Galaxy Note II) Android 4.1.2 Venza 2013 SGH-i547 (Galaxy Rugby Pro) Android 4.0.4 Samsung SGH-i717 (Galaxy Note) Android 4.0.4 Features SGH-i747 (Galaxy S III) Android 4.0.4 Vehicle (Bluetooth)** Hands-Free, Audio Streaming SGH-I897 (Captivate) Android 2.1-update1 iPhone 4 iOS 6.0 (10A403) EntuneTM Apple iPhone 4S iOS 6.0 (10A403) Sprint Fuel, Sports, Stocks, Traffic, Weather iPhone 5 iOS 6.0 (10A405) HTC PJ75100 (EVO 4G LTE) Android 4.0.3 Toyota vehicles equipped with the Display Audio multimedia systemContinued require all iPhone on Next users Page to connect using an Apple connector cable to the vehicle's Universal Serial Bus (USB) port ** For Message Alert compatiblity test results, please refer to the Complete List of Phones Tested to Date Continued on Next Page An updated list will be available mid-June Page 1 of 15 Summary of Compatible Phones - cont.