RYUK-EN-2.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tutorial for VCS
Tutorial for VCS STEP 1: login to the Linux system on Linuxlab server. Start a terminal (the shell prompt). Click here to open a shell window Fig. 1 The screen when you login to the Linuxlab through equeue STEP 2: In the terminal, execute the following command: module add ese461 You could perform “module avail” in the terminal to find the available modules on Linuxlab. Make sure ese461 is presented when you execute this command. 1.Find the available modules 2.Make sure ese461 is presented 3.This command will set up the work environment for class ESE461 Fig. 2 Build work environment for class ESE461 using module 1 STEP 3: Getting started with Verilog • Creating a new folder (better if you have all the files for a project in a specific folder). • Enter into this new folder and start writing your Verilog script in a new file (.v file). Example code for modeling an counter is here • In addition to model code, Test Bench script has to be given in order to verify the functionality of your model (.v file). Example code of test bench for counter is here. Use gedit to edit the .v files (gedit is a commonly used GUI editor on Linux ) Fig. 3 Open gedit through teminal STEP 4: Compiling and simulating your code • In the terminal, change the directory to where your model and test bench files (Counter.v and Counter_tb.v) are present by using this command: cd <path> For example: cd ~/ESE461/VcsTutorial/ (Remark: ‘~’ means home directory on Linux) • Compile the files by typing in the terminal: vcs <file>.v <file_tb>.v In the above example, it should be: vcs Counter.v Counter_tb.v There should be no error presented in the terminal. -

JAMS 7.X User Guide
User Guide JAMS Scheduler 7.3 Copyright Terms and Conditions Copyright Help/Systems LLC and its group of companies. The content in this document is protected by the Copyright Laws of the United States of America and other countries worldwide. The unauthorized use and/or duplication of this material without express and written permission from HelpSystems is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to HelpSystems with appropriate and specific direction to the original content. HelpSystems and its trademarks are properties of the HelpSystems group of companies. All other marks are property of their respective owners. 202108110755 JAMS 7.X User Guide Table of Contents JAMS 7.X Client Features 3 Jobs In JAMS 4 Working with Jobs 5-19 Scheduling Recurring Jobs 20-22 Execution Methods 23-27 Submitting Jobs Manually 28-29 Sequence Jobs 30-34 Managing Sequence Parameters 35-38 Sequence Tasks 39-47 Workflow Jobs 48-51 Workflow Activities 52-59 Migrating JAMS Objects 60-61 File Transfer Features 62-67 Variables 68 Working with Variables 69-71 Elements 72 Documentation Elements 73-74 EventHandler Elements 75-79 Prerequisite Elements 80-83 Result Elements 84-86 Trigger Elements 87-92 Folders 93 Working with Folders 94-104 Dates and Times 105 Date Properties 106-107 Creating Special Date Definitions 108-111 Specifying Dates Using Natural Language 112-114 Named Times in JAMS 115-118 Dashboards and Reports 119 Custom Dashboards 120-129 Creating New Report Templates and Customizing Existing Reports -

Toolkit Feature Interactive Debug Facility User's Guide
High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 High Level Assembler for z/OS & z/VM & z/VSE IBM Toolkit Feature Interactive Debug Facility User's Guide Version 1 Release 6 GC26-8709-09 Note Before using this information and the product it supports, be sure to read the general information under “Notices” on page 311. This edition applies to IBM High Level Assembler for z/OS & z/VM & z/VSE Toolkit Feature, Release 6, Program Number 5696-234 and to any subsequent releases until otherwise indicated in new editions. Make sure that you are using the correct edition for the level of the product. Order publications through your IBM representative or the IBM branch office serving your locality. IBM welcomes your comments. For information on how to send comments, see “How to send your comments to IBM” on page xv. © Copyright IBM Corporation 1992, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures ............... ix Building a module on z/OS ........ 17 Building a module on CMS ........ 17 About this book ........... xi Building a phase on z/VSE ........ 17 Running ASMLANGX ........... 18 Syntax notation ............. xi Extraction file allocation on z/OS ...... 18 Online language extraction on TSO ..... 19 How to send your comments to IBM .. xv Batch language extraction on z/OS ..... 19 If you have a technical problem ....... xv Online language extraction on CMS ..... 20 Batch language extraction on z/VSE .... -

IBM Tivoli Directory Server – Oracle Enterprise Gateway Integration Guide
Oracle Enterprise Gateway An Oracle White Paper June 2011 IBM Tivoli Directory Server – Oracle Enterprise Gateway Integration Guide 1 / 28 Oracle Enterprise Gateway Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. 2 / 28 Oracle Enterprise Gateway 1. Introduction ....................................................................................... 4 1.1. Purpose ...................................................................................... 4 1.2. LDAP Architecture ..................................................................... 5 1.3. Setup Used for this Guide: ......................................................... 5 2. Directory Details ................................................................................ 5 2.1. Directory Structure ..................................................................... 5 2.2. Connection Details ..................................................................... 5 3. Authenticate User with HTTP Basic HTTP Filter .............................. 6 3.1. Create a policy to authenticate a user in the LDAP directory .... 6 3.2. Create a new relative path for the Policy .................................. -

DWARF Debugging Information Format
DWARF Debugging Information Format UNIX International Programming Languages SIG Revision: 1.1.0 (October 6, 1992) Published by: UNIX International Waterview Corporate Center 20 Waterview Boulevard Parsippany, NJ 07054 for further information, contact: Vice President of Marketing Phone: +1 201-263-8400 Fax: +1 201-263-8401 International Offices: UNIX International UNIX International UNIX International UNIX International Asian/Pacific Office Australian Office European Office Pacific Basin Office Shinei Bldg. 1F 22/74 - 76 Monarch St. 25, Avenue de Beaulieu Cintech II Kameido Cremorne, NSW 2090 1160 Brussels 75 Science Park Drive Koto-ku, Tokyo 136 Australia Belgium Singapore Science Park Japan Singapore 0511 Singapore Phone:(81) 3-3636-1122 Phone:(61) 2-953-7838 Phone:(32) 2-672-3700 Phone:(65) 776-0313 Fax: (81) 3-3636-1121 Fax: (61) 2 953-3542 Fax: (32) 2-672-4415 Fax: (65) 776-0421 Copyright 1992 UNIX International, Inc. Permission to use, copy, modify, and distribute this documentation for any purpose and without fee is hereby granted, provided that the above copyright notice appears in all copies and that both that copyright notice and this permission notice appear in supporting documentation, and that the name UNIX International not be used in advertising or publicity pertaining to distribution of the software without specific, written prior permission. UNIX International makes no representations about the suitability of this documentation for any purpose. It is provided "as is" without express or implied warranty. UNIX INTERNATIONAL DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS DOCUMENTATION, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL UNIX INTERNATIONAL BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS DOCUMENTATION. -

Patching DOS 5 and up for the Pcjr
Patching DOS 5 and up for the PCjr November 29th, 2020 [email protected] Background Patching DOS 5+ Theory of operation Preparing a DOS 5 disk Patching the DOS 5+ disk Create FORMATJR.COM Hard drive installation Fdisk and create a DOS partition Format the hard drive partition Appendix A - Wiping out a boot sector Background The PCjr shipped in 1983 in two configurations: a 64KB machine with no floppy disk drive or a 128KB machine with a single floppy disk drive. The architecture of the machine has the video buffer “borrow” memory from the main memory of the machine. With the standard 16KB video buffer this makes the available RAM either 48KB or 112KB. IBM never offered a hard drive solution. Adding extra memory to a PCjr became possible, but it required a device driver to be loaded at boot time. Microsoft, Tecmar, and other vendors provided device drivers with their memory expansions. The best of the device drivers was a shareware program called jrConfig written by Larry Newcomb. jrConfig can be downloaded from http://www.brutman.com/PCjr/pcjr_downloads.html. The original version of DOS that shipped with the PCjr was PC DOS 2.1. DOS versions 2.1 through 3.3 work on the machine as is. To run DOS 5 or later two things are required: ● Extra memory is required. While extra memory is useful for DOS 2.1 - 3.3, DOS 5 won’t even boot on a small system. I BM formally states the requirement is 512KB and the PCjr is not supported. ● DOS 5 can be patched to work on a PCjr even though it is not supported. -
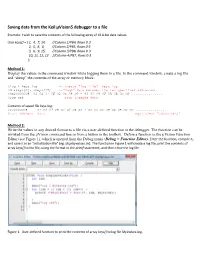
Saving Data from the Keil Μvision5 Debugger to a File
Saving data from the Keil µVision5 debugger to a file Example: I wish to save the contents of the following array of 16 8-bit data values. char keys[] = { 1, 4, 7, 14, //Column 1/PB4, Rows 0-3 2, 5, 8, 0, //Column 2/PB5, Rows 0-3 3, 6, 9, 15, //Column 3/PB6, Rows 0-3 10, 11, 12, 13 //Column 4/PB7, Rows 0-3 }; Method 1: Display the values in the command window while logging them to a file. In the command window, create a log file and “dump” the contents of the array or memory block: >log > keys.log -- create “log file” keys.log >d &keys[0], &keys[15] --“dump” data between the two specified addresses >0x20000008 01 04 07 0E 02 05 08 00 - 03 06 09 0F 0A 0B 0C 0D ................ >log off -- stop logging data Contents of saved file keys.log: 0x20000008 01 04 07 0E 02 05 08 00 - 03 06 09 0F 0A 0B 0C 0D ................ Start Address Data equivalent “characters” Method 2: Write the values in any desired format to a file via a user-defined function in the debugger. The function can be invoked from the µVision command line or from a button in the toolbox. Define a function in the µVision Function Editor (see Figure 1), which is opened from the Debug menu (Debug > Function Editor). Enter the function, compile it, and save it in an “initialization file” (eg. displayvalues.ini). The function in Figure 1 will create a log file, print the contents of array keys[] to the file, using the format in the printf statement, and then close the log file. -

How Do I Clear Partitions Using the Debug Script? WARNING
How do I clear partitions using the Debug script? WARNING - DELETING PARTITIONS WILL ALSO DELETE EVERYTHING ON YOUR COMPUTER, THAT MEANS EVERYTHING. PROGRAMS, DOCUMENTS, PICTURES, LETTERS, EMAIL, EVERYTHING. Make sure you have backup media before you continue like a Windows cd, driver cd, programs, and backup your data first*** If you have data on the drive and you can't stand to loose it (and your sure you don't have a virus) you may want to deltree the drive or delete the registry and reinstall. Here is the script: Boot to a Windows boot disk and use the following script. If debug can't be found on the Windows boot disk you may have to extract it. The computer will generate the text in red and you will type the text in white, where it says (ENTER) just hit the Enter key don't type the word. After the computer restarts you will need to run FDISK to repartition the hard drive then format and reinstall Windows. At A:> type ….. debug (ENTER) -F 220 L1000 0 (ENTER) -A CS:100 (ENTER) xxxx:0100 MOV AX,301 (ENTER) xxxx:0103 MOV BX,200 (ENTER) xxxx:0106 MOV CX,1 (ENTER) xxxx:0109 MOV DX,80 (ENTER) <---"80" for hd1, "81" for hd2 > xxxx:010C INT 13 (ENTER) xxxx:010E INT 20 (ENTER) xxxx:0110 (ENTER) <-------BLANK LINE "VERY IMPORTANT" > -G (ENTER) Program terminated normally (CTRL)-(ALT)-(DEL) to reboot system CLEAR CMOS using Debug If you think you may have a virus that infects the BIOS you may also want to clear that as well, otherwise it could infect your hard drive after you install Windows. -

Arm® Development Studio Heterogeneous System Debug with Arm DS Copyright © 2020 Arm Limited Or Its Affiliates
Arm® Development Studio Version 2020.1 Heterogeneous system debug with Arm DS Copyright © 2020 Arm Limited or its affiliates. All rights reserved. 102021_2010_00_en Arm® Development Studio Arm® Development Studio Heterogeneous system debug with Arm DS Copyright © 2020 Arm Limited or its affiliates. All rights reserved. Release Information Document History Issue Date Confidentiality Change 2000-01 3 July 2020 Non-Confidential New document for Arm® Development Studio 2020.0 documentation update 1 2010-00 28 October 2020 Non-Confidential Updated document for Arm® Development Studio 2020.1 Non-Confidential Proprietary Notice This document is protected by copyright and other related rights and the practice or implementation of the information contained in this document may be protected by one or more patents or pending patent applications. No part of this document may be reproduced in any form by any means without the express prior written permission of Arm. No license, express or implied, by estoppel or otherwise to any intellectual property rights is granted by this document unless specifically stated. Your access to the information in this document is conditional upon your acceptance that you will not use or permit others to use the information for the purposes of determining whether implementations infringe any third party patents. THIS DOCUMENT IS PROVIDED “AS IS”. ARM PROVIDES NO REPRESENTATIONS AND NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, SATISFACTORY QUALITY, NON-INFRINGEMENT OR FITNESS FOR A PARTICULAR PURPOSE WITH RESPECT TO THE DOCUMENT. For the avoidance of doubt, Arm makes no representation with respect to, and has undertaken no analysis to identify or understand the scope and content of, third party patents, copyrights, trade secrets, or other rights. -

In This Tutorial, We'll Discuss How to Use the IDE Debugger to Examine And
Tutorial Introduction PURPOSE: – To explain how to use the CodeWarrior Debugger to examine and modify data. OBJECTIVES: – Describe how to examine data variables. – Describe how to modify variable values. – Describe how to examine and modify memory and processor registers. CONTENT: – 16 pages – 2 questions LEARNING TIME: – 20 minutes In this tutorial, we’ll discuss how to use the IDE Debugger to examine and modify data. CodeWarrior enables you to manipulate your source code to display and change the contents of variables, arrays, and data structures. You can also use the Debugger to work at the hardware level if necessary. Upon completion of this tutorial, you’ll be able to describe how to examine data variables and how to modify variable values. You’ll also be able to describe the low-level operations supported by the Debugger to view and modify sections of memory and the processor registers. 1 Data Basics • Among other features, the Debugger can display -- – all variables, both local and global. – the contents of memory. – the processor registers. • Data appears in panes and separate windows. • Variables have a name and a value. – Select the name or value to initiate actions. – Drag separating line to resize name/value columns. • Values are almost always editable. • Use hierarchy control for structures and pointers. Let’s begin with a look at data and variables. You can use the Debugger to display a large amount of data. This data is organized into separate windows and then into panes for easy viewing and access. Typically, a glance at the Variables pane in the Thread Window will reveal the status of code execution. -

Debug Command Synopsis This Handout Is Intended As a Handy Reference Guide for Performing the More Common Operations in DEBUG
Debug Command Synopsis This handout is intended as a handy reference guide for performing the more common operations in DEBUG. Not all commands are covered. Debug understands only hex. Neither decimal or binary numbers are accepted. Consequently, a trailing "H" to denote base 16 is not accepted. 1. Help. Type -? at the - prompt to get a complete list of DEBUG commands and syntax. 2. Specifying addresses. Many debug commands allow an address to specified. Addresses can be specified as offsets or segment:offset combinations. The segment and offset can be specified with either numeric addresses or segment registers. Examples: U ffff:0000 starts disassembly at address FFFF:0000 U 121 starts disassembly at offset 121 from the CS register. U DS:3F00 starts disassembly at offset 3F00 from the DS register. 3. Specifying ranges. Many debug commands (for example the D command) allow an optional range to be specified. Ranges can be specified as either startAddr endAddr or as StartAddr L Length. Examples: D 100 displays 128 bytes (the default value) from DS:100 on D 100 200 displays 257 bytes between DS:100 and DS:200 inclusive D 100 L 100 displays 256 bytes starting at DS:100 D 503 L 2 displays 2 bytes starting at DS:503 4. Flags. T is not displayed. ODISZA PC Set: OV UP EI NG ZR AC PE CY Clear: NV DN DI PL NZ NA PO NC 5. Starting DEBUG. A. To start DEBUG without loading a program into memory, just type DEBUG at the command prompt and press Enter. DEBUG assumes that you want to assemble a .COM program and will start with all segment registers having the same value, IP = 0100, and SP = FFFE. -

DEBUG Manual STARTING DEBUG
DEBUG Manual This tutorial is made to present an overview of the DEBUG.COM program for the IBM PC. This utility can be extremely useful, when used correctly. It is almost a must for Assembler Language programmers, and can also provide an insight into the operation of the machine at the bit level. It has several nice features, including the ability to display and change any of the registers in the IBMPC, start and stop program execution at any time, change the program, and look at iskettes, sector by sector. DEBUG works at the machine code level, ut it does also have the ability to disassemble machine code, and (at dos 2.0), assemble instructions directly into machine code. The rocedure for starting DEBUG and command syntax will not be covered here, as they are well documented in the DOS manual. What we ill do s show some examples of the various commands and the response hich is expected. Note that the segment registers will probably not be xactly what is shown. This is normal, and should be expected. For the examples, I will be using the demo program CLOCK.COM in the XA4 atabase. For those of you with the IBM assembler (MASM), the source can be down loaded. If you do not have the assembler, or have another assembler, the file CLOCK.HEX has been up loaded. It can be converted to a .COM file using any of the existing HEX conversion rograms on the SIG. See the file CLOCK.DOC for more information. STARTING DEBUG There are two ways to start DEBUG with a file.