Administering Windows 10
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bitlocker Encryption for USB Drives Bitlocker Is a Security Feature. the Purpose of Bitlocker Is to Encrypt Your Data
BitLocker Encryption for USB Drives BitLocker is a security feature. The purpose of BitLocker is to encrypt your data. This is extremely necessary for any data that is not to be shared with other persons. This will prevent anyone from being able to access your files. In order to have access to your files, you will need to provide a secure password. This password should be unique only to you. More information is provided below on how to make a unique password in step 2. During this process, step 3 offers the option to save a recovery key. The recovery key is 48 characters long and consist of numbers and letters. This key will be saved to Active Directory and allow the IS Department to access your USB/External drive should you forget your password. To get started I would recommend encrypting the USB/External drive BEFORE adding any files. Once the drive is encrypted and you enter your password it will function as any other USB/External drive. So you may add, edit, or delete your files as you normally would. If you have any trouble following this guide or have any questions please do not hesitate to contact the IS department. You will need a USB or External drive in order to successfully complete this process. Multiple ways to navigate to BitLocker: 1. Control Panel System & Security BitLocker Drive Encryption 2. Search bar type in “BitLocker” Manage BitLocker Steps to encrypt your USB drive: Step 1: Click “Turn on BitLocker” Step 2: Check the “Use a password to unlock the drive” and enter your password. -
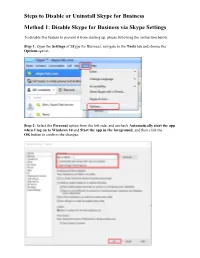
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -
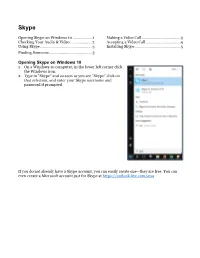
Opening Skype on Windows 10
Skype Opening Skype on Windows 10 ................... 1 Making a Video Call ..................................... 3 Checking Your Audio & Video .................... 2 Accepting a Video Call .................................4 Using Skype ................................................. 3 Installing Skype ........................................... 5 Finding Someone ........................................ 3 Opening Skype on Windows 10 1. On a Windows 10 computer, in the lower left corner click the Windows icon. 2. Type in “Skype” and as soon as you see “Skype” click on that selection, and enter your Skype username and password if prompted. If you do not already have a Skype account, you can easily create one—they are free. You can even create a Microsoft account just for Skype at https://outlook.live.com/owa Checking Your Audio & Video 1. Open Skype. 2. In the left pane, in the top right corner, click on the ellipse (…). 3. Your Settings open. 4. In the left pane, select Audio & Video. 5. In the Camera section your live picture should appear. If it does not, see if there is an option above your picture, and try selecting a different web camera. 6. Scroll down until you see the Audio section. Test your microphone and speakers and adjust the volume as needed. 7. Close the dialog box by clicking the X in the top left corner. Using Skype Once you open Skype, you will select someone to call from the left pane. You have some important options there: Search, Chats, Contacts The first couple times you use Skype you may need to search for your friends and family. You can search by name or email address associated with their Skype account. -

Chapter 2: Windows 7
Chapter 2: Windows 7 When you delete a file, a. A copy of the file will be sent to the desktop b. You send the file to the Recycle Bin. c. The file will not be affected. d. A copy of the file will be stored in your active folder. Which of the following statements is correct about arrange icon on desktop. a. Icons on desktop can be arranged by name. b. Icons on desktop can be arranged by type. c. Icons on desktop can be arranged by size. d. All of the above. Which of the following statements is correct about opening control panel. a. You can open control panel from windows explorer. b. You can open control panel from start menu. c. You can open control panel from my computer. d. All of the above. The documents that is located in start menu store. a. The last 15 files that you have open. b. The last 15 files that you have delete. c. The last 15 files that you have copy. d. None of the above. The desktop is: a. An example of a hardware device. b. A folder. c. A file d. A window. The Shutdown icon on start menu means: a. Close all windows. b. Close the current windows. c. Close your computer. d. None of the above. To open a minimized window, you can click on the:- a. window’s button on the body of the taskbar. b. maximized button on the title bar. c. restore button on the title bar. d. all of the above. -

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -
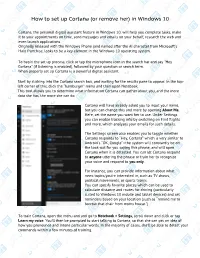
How to Set up Cortana (Or Remove Her) in Windows 10
How to set up Cortana (or remove her) in Windows 10 Cortana, the personal digital assistant feature in Windows 10, will help you complete tasks, make it to your appointments on time, send messages and emails on your behalf, research the web and even launch applications. Orignally released with the Windows Phone (and named after the AI character from Microsoft's Halo franchise, looks to be a key element in the Windows 10 operating system. To begin the set up process, click or tap the microphone icon in the search bar and say "Hey Cortana" (if listening is enabled), followed by your question or search term. When properly set up Cortana is a powerful digital assistant. Start by clicking into the Cortana search box, and waiting for the results pane to appear. In the top- left corner of this, click the “hamburger” menu and then open Notebook. This tool allows you to determine what information Cortana can gather about you, and the more data she has, the more she can do. Cortana will have already asked you to input your name, but you can change this and more by opening About Me. Here, set the name you want her to use. Under Settings you can enable tracking info by switching on Find flights and more, which analyses your emails for such details. The Settings screen also enables you to toggle whether Cortana responds to “Hey, Cortana” which is very similar to Android’s “OK, Google“–the system will constantly be on the look-out for you saying this phrase, and will open Cortana when it is detected. -
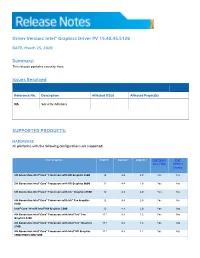
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Active@ NTFS Reader for DOS User Guide
Active Data Recovery Software Active@ NTFS Reader for DOS User Guide Version 1.0 Contents PRODUCT OVERVIEW SYSTEM REQUIREMENTS PRODUCT FEATURES OPERATING PROCEDURES 4.1 Bootable Floppy Disk (Startup Disk) Preparation..............................................................................4 4.2 Program Start and Information Display...............................................................................................5 4.3. Scan and Search for Files and Folders..................................................................................................5 4.4. Previewing Files.......................................................................................................................................6 4.5. Copying Files and Folders......................................................................................................................7 4.6. Using Disk Viewer ..................................................................................................................................8 4.7. Localized File Names Display ...............................................................................................................8 4.8. Long File Names Display.......................................................................................................................9 4.9. Command Line Parameters ...................................................................................................................9 1 PRODUCT OVERVIEW Active@ NTFS Reader is a compact and powerful DOS utility that -
Quick Guide Page | 1
Quick Guide Page | 1 Contents Welcome to Windows 10 ................................................................................................................................................................................................... 3 Key innovations ...................................................................................................................................................................................................................... 3 Cortana ................................................................................................................................................................................................................................. 3 Microsoft Edge .................................................................................................................................................................................................................. 4 Gaming & Xbox ................................................................................................................................................................................................................ 5 Built-in apps ....................................................................................................................................................................................................................... 7 Enterprise-grade secure and fast ................................................................................................................................................................................... -

Getting Started with Windows Speech Recognition
Getting Started with Windows™ Speech Recognition (WSR) A. OVERVIEW After reading Part One, the first time user will dictate an E-mail or document quickly with high accuracy. The instructions allow you to create, dictate, and send an E-mail without touching the keyboard. The second part discusses steps to attain highest accuracy. The final part has suggestions for increasing productivity when using Windows™ Speech Recognition. II. PART ONE A. WHY USE SPEECH RECOGNITION? Most people will be able to dictate faster and more accurately than they type. My experience with Windows™ Speech Recognition is the ability to dictate over 80 words a minute with accuracy of about 99%. If you truly can type at 80 words a minute with accuracy approaching 99%, you do not need speech recognition. However, even a good keyboarder will benefit from reduced strain on the hands and arms by using Windows™ Speech Recognition. It takes time to become comfortable with dictation into a computer. There will be moments of frustration as you go through the learning curve. If you are impatient or are a perfectionist, DO NOT read on and do not use Windows™ Speech Recognition. If you have reasonable patience, you will learn to dictate accurately and comfortably. The best strategy is to keep things simple for first several days of using Windows™ Speech Recognition. When you are comfortable with the basics, move to part two of this document. B. THE MICROPHONE A good microphone makes dictation into a computer a pleasure instead of a battle. Good microphones reproduce your voice accurately and block out background noise that distorts the audio signal. -

Feature Description
NTLM Feature Description UPDATED: 19 March 2021 NTLM Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM Table of Contents 1 Introduction 4 1.1 Document Purpose 6 1.2 Intended Audience 6 1.3 Related Firmware Version 6 2 Configure NTLM Authentication 7 2.1 Configure Internet Options on the Client Machine 7 2.2 Configure the LoadMaster 11 2.2.1 Enable NTLM Proxy Mode 13 2.2.2 Configure the Server Side SSO Domain 13 2.2.3 Configure the Client Side SSO Domain 15 2.2.4 Configure the Virtual Service 15 2.3 Configure Firefox to Allow NTLM (if needed) 17 2.4 Troubleshooting 18 References 19 Last Updated Date 20 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM 1 Introduction 1 Introduction NT LAN Manager (NTLM) is a Windows Challenge/Response authentication protocol that is often used on networks that include systems running the Windows operating system and Active Directory. Kerberos authentication adds greater security than NTLM systems on a network and provides Windows-based systems with an integrated single sign-on (SSO) mechanism.