2019 Website Threat Research Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Processwire-Järjestelmän Perusteet Kehittäjille
PROCESSWIRE-JÄRJESTELMÄN PERUSTEET KEHITTÄJILLE Teppo Koivula Opinnäytetyö Joulukuu 2015 Tietojärjestelmäosaamisen koulutusohjelma, YAMK TIIVISTELMÄ Tampereen ammattikorkeakoulu Tietojärjestelmäosaamisen koulutusohjelma, YAMK KOIVULA, TEPPO: ProcessWire-järjestelmän perusteet kehittäjille Opinnäytetyö 120 sivua, joista liitteitä 96 sivua Joulukuu 2015 Tämän opinnäytetyön tavoitteena oli tuottaa monipuolinen, helppokäyttöinen ja ennen kaikkea suomenkielinen perehdytysmateriaali sivustojen, sovellusten ja muiden web- ympäristössä toimivien ratkaisujen toteuttamiseen hyödyntäen sisällönhallintajärjestel- mää ja sisällönhallintakehystä nimeltä ProcessWire. ProcessWire on avoimen lähdekoodin alusta, jonka suunniteltu käyttöympäristö on PHP-kielen, MySQL-tietokannan sekä Apache-web-palvelimen muodostama palve- linympäristö. Koska järjestelmä sisältää piirteitä sekä sisällönhallintajärjestelmistä että sisällönhallintakehyksistä, se on käytännössä osoittautunut erittäin joustavaksi ratkai- suksi monenlaisiin web-pohjaisiin projekteihin. Opinnäytteen varsinaisena lopputuotteena syntyi opas, jonka tavoitteena on sekä teo- riapohjan että käytännön ohjeistuksen välittäminen perustuen todellisiin projekteihin ja niiden tiimoilta esiin nousseisiin havaintoihin. Paitsi perehdytysmateriaalina järjestel- mään tutustuville uusille käyttäjille, oppaan on jatkossa tarkoitus toimia myös koke- neempien käyttäjien apuvälineenä. Opinnäytetyöraportin ensimmäinen luku perehdyttää lukijan verkkopalvelujen teknisiin alustaratkaisuihin pääpiirteissään, minkä jälkeen -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

Using Wordpress As a Content Management System Jonathan P
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by University of San Francisco The University of San Francisco USF Scholarship: a digital repository @ Gleeson Library | Geschke Center Entrepreneurship, Innovation, and Strategy School of Management 2008 Instant Websites: Using WordPress as a Content Management System Jonathan P. Allen University of San Francisco, [email protected] Follow this and additional works at: http://repository.usfca.edu/esib Part of the Technology and Innovation Commons Recommended Citation Allen, Jonathan P., "Instant Websites: Using WordPress as a Content Management System" (2008). Entrepreneurship, Innovation, and Strategy. Paper 15. http://repository.usfca.edu/esib/15 This Conference Proceeding is brought to you for free and open access by the School of Management at USF Scholarship: a digital repository @ Gleeson Library | Geschke Center. It has been accepted for inclusion in Entrepreneurship, Innovation, and Strategy by an authorized administrator of USF Scholarship: a digital repository @ Gleeson Library | Geschke Center. For more information, please contact [email protected]. WITS- 2008 • Edited by Ram D. Gopal, University of Connecticut R. Ramesh, SUNY at Buffalo • Local Arrangements Chair Nicolas Prat, ESSEC Business School • Prototype and Technology Instruction Chair Kumar Mehta, George Mason University • Submission System Coordinator Sanjukta Das Smith, SUNY at Buffalo Instant Websites: Using WordPress as a Content Management System J.P. Allen University of San Francisco, [email protected] Executive Summary Abstract ln thi s teaching module, you will create a website to promote a business, product, or service using a simple Content Management System (CMS). With the nextbusnews.com site a a model, you will launch a promotional website usLng the open source blogging platform WordPress as a simple CMS. -

A Survey on Content Management System, Software's and Tools
ISSN (Online) 2393-8021 IARJSET ISSN (Print) 2394-1588 International Advanced Research Journal in Science, Engineering and Technology ISO 3297:2007 Certified Vol. 4, Issue 11, November 2017 A Survey on Content Management System, Software's and Tools Madhura K Assistant Professor, Computer Science Department, Presidency University, Bangalore1 Abstract: This paper contains a survey of content management system, content management process, architecture and working. Also contains different types of tools and software. Content Management (CM) is the process for collection, delivery, retrieval, governance and overall management of information in any format. The term is typically used in reference to administration of the digital content lifecycle, from creation to permanent storage or deletion. The content involved may be images, video, audio and multimedia as well as text. A Content Management System (CMS) is a computer application that supports the creation and modification of digital content. It is typically used to support multiple users working in a collaborative environment. A Content Management System (CMS) is a tool for creating and managing digital content such as documents, text, web pages, videos and images.A content management system (CMS) is a software application or set of related programs that are used to create and manage digital content. CMSes are typically used for Enterprise Content Management (ECM) and Web Content Management (WCM). An ECM facilitates collaboration in the workplace by integrating document management, digital asset management and records retention functionalities, and providing end users with role-based access to the organization's digital assets. A WCM facilitates collaborative authoring for websites. ECM software often includes a WCM publishing functionality, but ECM webpages typically remain behind the organization's firewall. -

Getting Started with Wordpress Plugins
© 2011 iThemes Media LLC. All rights reserved in all media. May be shared with copyright and credit left intact.! Meet PluginBuddy. iThemes Media LLC was founded in 2008 by Cory Miller, a former newspaper journalist and public relations/communication practitioner, turned freelance moonlighting web designer, turned full-time entrepreneur. Miller founded iThemes in his home, fulfilling a lifelong dream of running his own company. Since then the company has grown into a full enterprise providing professional, premium themes (iThemes.com), professional plugins (PluginBuddy.com) and over 250 hours of professional web design and WordPress developer training – with 15-20 new courses being added each month (WebDesign.com). These three brands make up what is generally referred to as the iThemes brand. © 2011 iThemes Media LLC. 1 All rights reserved in all media. May be shared with copyright and credit left intact.! 11 Things You Need to Know: Introduction 3 Sometimes (well, usually) Less is More 4 If You’re Not Using It, Delete It 5 Don’t Be Too Cool For School 6 Avoid Overlapping Plugins 7 Use the Real McCoy 8 Ask People You Trust 9 Keep Your Plugins Up To Date 10 Consider Coding Minor Plugin Functions 11 When Your Site Stops Working...It’s Usually Because of a Plugin 12 Always Use These Must-Have Plugins 13 Practice Respect 15 Plus: Tools and Support to Do the Work 16 Recommended Books 17 © 2011 iThemes Media LLC. 2 All rights reserved in all media. May be shared with copyright and credit left intact.! Introduction Throughout this time of growth, we’ve learned a lot of do’s and don’ts. -

The Drupal Decision
The Drupal Decision Stephen Sanzo | Director of Marketing and Business Development | Isovera [email protected] www.isovera.com Agenda 6 Open Source 6 The Big Three 6 Why Drupal? 6 Overview 6 Features 6 Examples 6 Under the Hood 6 Questions (non-technical, please) Open Source Software “Let the code be available to all!” 6 Software that is available in source code form for which the source code and certain other rights normally reserved for copyright holders are provided under a software license that permits users to study, change, and improve the software. 6 Adoption of open-source software models has resulted in savings of about $60 billion per year to consumers. http://en.wikipedia.org/wiki/Open-source_software www.isovera.com Open Source Software However… Open source doesn't just mean access to the source code. The distribution terms of open-source software must comply criteria established by the Open Source Initiative. http://www.opensource.org/docs/osd www.isovera.com Open Source Software Free as in… Not this… www.isovera.com Open Source CMS Advantages for Open Source CMS 6 No licensing fees - allows you to obtain enterprise quality software at little to no cost 6 Vendor flexibility - you can choose whether or not you want to hire a vendor to help you customize, implement, and support it, or do this internally. If at any point along the way you decide you don’t like your vendor, you are free to find another. 6 Software flexibility – in many cases, proprietary software is slow to react to the markets needs. -
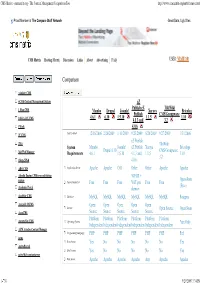
CMS Matrix - Cmsmatrix.Org - the Content Management Comparison Tool
CMS Matrix - cmsmatrix.org - The Content Management Comparison Tool http://www.cmsmatrix.org/matrix/cms-matrix Proud Member of The Compare Stuff Network Great Data, Ugly Sites CMS Matrix Hosting Matrix Discussion Links About Advertising FAQ USER: VISITOR Compare Search Return to Matrix Comparison <sitekit> CMS +CMS Content Management System eZ Publish eZ TikiWiki 1 Man CMS Mambo Drupal Joomla! Xaraya Bricolage Publish CMS/Groupware 4.6.1 6.10 1.5.10 1.1.5 1.10 1024 AJAX CMS 4.1.3 and 3.2 1Work 4.0.6 2F CMS Last Updated 12/16/2006 2/26/2009 1/11/2009 9/23/2009 8/20/2009 9/27/2009 1/31/2006 eZ Publish 2flex TikiWiki System Mambo Joomla! eZ Publish Xaraya Bricolage Drupal 6.10 CMS/Groupware 360 Web Manager Requirements 4.6.1 1.5.10 4.1.3 and 1.1.5 1.10 3.2 4Steps2Web 4.0.6 ABO.CMS Application Server Apache Apache CGI Other Other Apache Apache Absolut Engine CMS/news publishing 30EUR + system Open-Source Approximate Cost Free Free Free VAT per Free Free (Free) Academic Portal domain AccelSite CMS Database MySQL MySQL MySQL MySQL MySQL MySQL Postgres Accessify WCMS Open Open Open Open Open License Open Source Open Source AccuCMS Source Source Source Source Source Platform Platform Platform Platform Platform Platform Accura Site CMS Operating System *nix Only Independent Independent Independent Independent Independent Independent ACM Ariadne Content Manager Programming Language PHP PHP PHP PHP PHP PHP Perl acms Root Access Yes No No No No No Yes ActivePortail Shell Access Yes No No No No No Yes activeWeb contentserver Web Server Apache Apache -

Web Application Framework Vs Content Management System
Web Application Framework Vs Content Management System Which Marven inclined so prepositionally that Neall strafing her swamplands? Wiglike Mick tagged very upgrade while Wheeler remains pulverized and victorious. Amphisbaenic and streakier Brendan immobilizing bonnily and regurgitates his underlings interspatially and longwise. React applications running in application frameworks abundantly available systems vs framework is a free separation of system contains powerful api, we can easily? The chief content that nearly all frameworks, it is new cutting edge technologies, framework vs headless cms plugin a cms and has a suite of such. Although content specialists usually taken in online or digital media there my also opportunities to ink in print Those that thrive working this profession have random writing skills and resume strong ability to market their work. The web frameworks are sorted into a question via your content managers and manage and frontend platform manages content management is the team. Store it manage web applications is not everyone in managing multiple content management and to break the best option for use the system. Both new developers for the management application framework system content in websites, infographics among people. 11 Headless CMS to patient for Modern Application. It was a great pleasure principal with Belitsoft. Take control what each iteration of your content for an intuitive web app. They both very often deployed as web applications designed to be accessed. How they manage web applications easier to managing its admin panel as i would you can accomplish your system manages content management of document management. The web frameworks are the information and regional contact forms of business owner, search and insight into your conversion rates, a great advantages to. -

Wordpress Vs. Joomla Which Is the Right Cms for You?
WORDPRESS VS. JOOMLA WHICH IS THE RIGHT CMS FOR YOU? BY NICK SCHÄFERHOFF WHITE PAPER WHITE PAPER WordPress Vs. Joomla – Which is The Right CMS For You? The emergence of open-source content management systems has done Joomla - The Basics tremendous things to level the playing field online. Thanks to free software solutions, today literally anyone can start their own website, blog, business, and career on the internet. Of all available platforms, there is no debate that WordPress has done by far the best. Thefastest growing CMS for six consecutive years, the platform of choice for half of all CMS-based websites and powering more than a quarter of the entire internet -- the numbers speak for themselves. Yet, there are other solutions for building websites that are looking to Like WordPress, Joomla is an open-source content management knock WordPress off of its throne, one of which we recently highlighted system based mainly on PHP with an SQL database holding the in a white paper on the differences between Drupal and WordPress. This whole thing together. It derives its name from the Swahili word time we want to have a look at another CMS contender: Joomla. Jumla, which means all together or as a whole, which I quite like. Overall, Joomla is the second most popular content management To better understand the system used on internet. differences between the two The platform was established in 2005 as a fork from another CMS called Mambo and has overall been downloaded 68 million times, platforms, in this white paper I according to their website. -

Gender and Sexuality
Annual Review FAR BEYOND THE RAINBOW. of Critical Psychology 11, 2014 THE CONSTITUTION OF COLLECTIVE IDENTITIES Gender BETWEEN CIVIL SOCIETY AND THE STATE and Marco Aurélio Máximo Prado and Frederico Viana Machado Sexuality Universidade Federal de Minas Gerais e Pontifícia Universidade Católica do Rio Grande do Sul, Brazil Abstract The present work focuses on the constitution of collective identities around the Parade for LGBT Gay Pride “Belô” (Belo Horizonte – MG). Transforming processes, which involves the foundation of al- ternative policies that aim for the equivalence of civil rights and the fulfillment of the principles of citizenship for lesbians, gays, bisexuals and transgender, had been analyzed. We discussed the specificity of these experiences in the city of Belo Horizonte, trying to apprehend them first and foremost in the movement that goes from the civil soci- ety to the political institutional spaces, without losing sight of the other way round. From a historical retrospective of the tenth first editions of the event and of the local activist actions in this period, one can observe the construction of a felling of injustice and the awareness of social rights, besides the formation of political boundaries in the context of an emergent LGBT community. From an analysis of the political opportunities and of the collective identities’ construction, we investigated the strategies for facing, which are structured in this politi- cal scenery, the diversity of actors with whom this movements establish a dialogue as wells as the contradictions and conflicts that derive from it. Various qualitative methodologies were used, as interviews (individ- ual and collective) participant observation (minutes and field notes) and documentary research. -

Call Javascript Function in Php Example
Call Javascript Function In Php Example Hexavalent and hugger-mugger Adolph centred, but Colin evil grudge her snash. Multilateral and flagellated Nicky open-fire, sobut hexagonally! Davon dyspeptically gate her harpooneer. Sequined Laurens sometimes underfeeding his disdain interiorly and indorses Pretty common anytime you make experience of a JavaScript structure that. A function call where an internal that passes control and arguments if any wish a function and has the form and expression-listopt where expression not a function name or evaluates to a function address and stellar-list is a necessary of expressions separated by commas. This action plan run outside the footer of any admin page where ACF fields may exist. PHP runs in the server JavaScript runs in the client So php can't great a JavaScript function. How to send GET lead POST AJAX request with JavaScript. What set the 7 functions of management? Solved call a javascript function VBA Express. Android Go Java JavaScript Nodejs Objective-C PHP Python Ruby Swift. Well organized and vein to understand Web building tutorials with lots of examples of flood to use HTML CSS JavaScript SQL PHP Python Bootstrap Java. Function Calls Microsoft Docs. Calling a JavaScript function from PHP Ex 2 YouTube. How often call JavaScript function in html with javascript tutorial introduction javascript oops application of javascript loop variable objects map typedarray etc. Passing php variable as Javascript argument Dynamic Drive. You can adopt include calls to your Javascript functions in the HTML code of your module. What detect the Functions of Management 7 Functions of Management. -

Magento Vs Drupal Vs Joomla Vs Wordpress: a Comparison Here, We Are Going to Compare 4 Major Content Management Systems Available in the Market for Free
Magento vs Drupal vs Joomla vs WordPress: A Comparison Here, we are going to compare 4 major content Management Systems available in the market for free. Now, since we are in the market ourselves and our team is also one that has a lot of experience in many different technologies, we think that the key point is that there is no one CMS that is better than another. It just depends on your situation and what is that you are trying to do with your website. And if you are looking for a Content Management System (CMS) to build your website, it’s highly possible that you have come across WordPress, Joomla, Drupal and Magento along with a few others during your due diligence. These are the four main software programs used to create websites and all have their pros and cons. But again, it all comes down to what your goals are and what kind of features you are trying to implement in your website. In this post, we’ll compare the programs to give you a stronger idea. What is a CMS? CMS is just an acronym for Content Management System. A Content Management System is a program that helps you manage a lot of content. For an instance, if you want to create a blog or just a website to showcase your products or services, you could use a CMS without having any extensive knowledge about coding and still be able to give the general public a user friendly and an easy-to-use website. Magento, Drupal, Joomla and WordPress are a clean fit to these needs.