Glasstube: a Lightweight Approach to Web Application Integrity
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Topic 14: Client- Side Rendering CITS3403 Agile Web Development
Topic 14: Client- Side Rendering CITS3403 Agile Web Development Reading: The Flask Mega-Tutorial, part 14 Semester 1, 2021 Miguel Grinberg https://blog.miguelgrinberg.com/post/the-flask-mega-tutorial-part-xiv-ajax Accessing a REST API • A REST API takes your application from the web to the internet. Any device with TCP/IP can interact with the application through HTTP requests. • We can interact with a REST API through a number of mediums: command line, Postman, or a web browser. • These applications create and send http requests to the REST API and receive http responses. • Postman can also be used for mocking APIs and automated testing. Javascript and DOM • As a simple example of consuming a REST API we will look at writing a low level single page application that interacts directly with the API. • It will use AJAX to send and receive requests from the server. • It will use Javascript and DOM to update the web page. • We will (redundantly) include it with an existing server-side rendering app. Single Page Applications • Single Page Applications have the browser/client do the heavy lifting in a web application: The server just provides the data while the client does the logic and rendering AJAX AJAX = Asynchronous JavaScript And XML. • AJAX is not a programming language. • AJAX just uses a combination of: – A browser built-in XMLHttpRequest object (to request data from a web server) – JavaScript and HTML DOM (to display or use the data) • AJAX is a misleading name. AJAX applications might use XML to transport data, but it is equally common to transport data as plain text or JSON text. -

The Jasper Framework: Towards a Platform Independent, Formal Treatment of Web Programming
The Jasper Framework: Towards a Platform Independent, Formal Treatment of Web Programming James Smith Imperial College London, United Kingdom [email protected] This paper introduces Jasper, a web programming framework which allows web applications to be developed in an essentially platform indepedent manner and which is also suited to a formal treat- ment. It outlines Jasper conceptually and shows how Jasper is implemented on several commonplace platforms. It also introduces the Jasper Music Store, a web application powered by Jasper and imple- mented on each of these platforms. And it briefly describes a formal treatment and outlines the tools and languages planned that will allow this treatment to be automated. 1 Introduction These days a web application may span both server and client side. Facebook is a good example, with much of the site’s functionality being implemented using JavaScript and executed in the browser. Com- munication between client and server sides is also, typically, not just characterised by requests from the browser, requests are also made by JavaScript in the form of Ajax calls. It is not at all obvious, for example, that Facebook fakes conventional browser requests. Clicking on menu items appears to result in such conventional requests being made, since the whole page seems to change, but in fact these are often Ajax calls and the whole page is changed dynamically, rather than a new page being served. In this way the chat pane can remain “on top”, while the page changes “underneath”. Such techniques used to characterise what were known as rich web applications but they are becoming so commonplace nowadays that a rich web application might be considered the norm. -

List Any Two Rich Internet Applications
List Any Two Rich Internet Applications JoshuaLightfast cliffier? and funnier If flinty Hermy or gushiest run-up Barry her Mycenae usually step-in dangles his trancedly leukaemia or infringedisembosoms rolling orgenealogically, lace unrightfully is shamelessly.and doggo, how deepening is Bradford? Extraneous and druidic Desmond still outshoots his cembalist We are rich internet application is any code. Microsoft is not quite there yet to provide this kind of functionality in the browser, desktop applications, testing and deploying an application into a single integrated solution allowing administrators to monitor and control that process through a graphical interface. To test the application, similar to Adobe Flash. Multiple elements can have the form role. Use Cases for Rich Internet Applications 1 Background IAML. Listexecute possible actions on the crazy state A Robot. Select a date air time that works for you. The element does your own hazard control a grouping element that is expandable. Return generic command key leads workshops, list any two rich internet applications developed using hessian server. URL which points to the location of the Hessian service. Applets made Java popular in contemporary early days. The uniPaaS Enterprise Server lies at about heart is Rich Internet Application. Applets cannot use stored values are currently active child nodes they were used. Some functionality in any one feel for list or persons with lists require significant addition in web services provided input that is a concurrency token. Better just, use SQL parameters when you build SQL commands. Flex is not a magic wand. Automatic events include occurrences such as a timer running out and procedural events are occurrences triggered explicitly within the application code. -

Secure Web Framework for Mobile Devices
GC'12 Workshop: The 4th IEEE International Workshop on Management of Emerging Networks and Services Secure Web Framework For Mobile Devices Muneer Malik and Dharma P. Agrawal ([email protected], [email protected]) Center of Distributed and Mobile Computing, School of Computing Sciences and Informatics University of Cincinnati, Cincinnati OH 45221-0008, Abstract—A secure mobile web framework is proposed based HTML 5 based framework, which allows developers to write on MVC Struts 2 to support embedded browsers in mobile impressive apps that work on IOS (iPhone OS), Android, devices. The framework integrates JAAS with Tomcat Blackberry, Kindle Fire and many other devices. Fluid providing Authentication and Authorization. Encryption Animations, smooth scrolling and adaptive layouts are key Utility to support multiple providers, implementing a scheme attributes for HTML 5 based framework, rivaling native for short-lived session objects, support for the menu items technology. Financial Times (FT), a London paper is a HTML using xml configuration depending on the role and device 5 web app rather than a native app and “it helps publishers to category, view layer integration with Tiles 2 and rendering gain readers and sell more subscription without paying a views for both desktop and mobile without duplicating the platform fee” [3]. Struts 2 control action logic. Finally, an Electronic Medical Record – web application is designed and implemented for Although jQM is designed for writing mobile web apps, it Dialysis Center to further demonstrate the feasibility of the can also be used to build native apps that can be purchased and unified secure mobile web framework. -

Marsily-Msc2010
U C L L S M . Richer Web Applications On Trends, Techniques and Standards Supervisor: Prof. J. V Master esis: Partial Fulllment of the Requirements for the Degree of Master in Business Engineering Charles M 2323.05.00 INGE22MS/G [email protected] Academic Year 2009-2010 . Acknowledgment I would like to thank my supervisor Prof. Jean V for providing me a subject as interesting as rich web applications. Writing this document has redened how I use the Web today. e e e In addition, this work might not have been possible without my family’s continuous support. .. C C i L F iii I v Disclaimer.................................................................. vi Content & objectives........................................................ vi 1 U RIA 1 1.1 Denition and criteria ................................................. 1 ick vs. thin applications ................................................. 3 Client/server applications vs. web applications................................. 4 RIA features and characteristics ............................................. 5 Deployment alternatives ................................................... 6 1.2 Why RIAs are emerging? .............................................. 6 1.3 Limitations ........................................................... 8 1.4 Web applications vs. native apps: what to choose for the iPhone?. 9 1.5 RIAs as a part of a broader Web 2.0 era ................................. 11 1.6 RIAs for enterprises ................................................... 14 -

Pro Web 2.0 Application Development with GWT
9853FM.qxd 4/15/08 11:14 AM Page i Pro Web 2.0 Application Development with GWT Jeff Dwyer Excerpted for InfoQ from 'Pro Web 2.0 Application Development' by Jeff Dwyer, published by Apress - www.apress.com 9853FM.qxd 4/15/08 11:14 AM Page ii Pro Web 2.0 Application Development with GWT Copyright © 2008 by Jeff Dwyer All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher. ISBN-13 (pbk): 978-1-59059-985-3 ISBN-10 (pbk): 1-59059-985-3 ISBN-13 (electronic): 978-1-4302-0638-5 ISBN-10 (electronic): 1-4302-0638-1 Printed and bound in the United States of America 9 8 7 6 5 4 3 2 1 Trademarked names may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, we use the names only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. Java™ and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc., in the US and other countries. Apress, Inc., is not affiliated with Sun Microsystems, Inc., and this book was written without endorsement from Sun Microsystems, Inc. Lead Editors: Steve Anglin, Ben Renow-Clarke Technical Reviewer: Massimo Nardone Editorial Board: Clay Andres, Steve Anglin, Ewan Buckingham, Tony Campbell, Gary Cornell, Jonathan Gennick, Matthew Moodie, Joseph Ottinger, Jeffrey Pepper, Frank Pohlmann, Ben Renow-Clarke, Dominic Shakeshaft, Matt Wade, Tom Welsh Project Manager: Kylie Johnston Copy Editor: Heather Lang Associate Production Director: Kari Brooks-Copony Production Editor: Liz Berry Compositor: Dina Quan Proofreader: Linda Marousek Indexer: Carol Burbo Artist: April Milne Cover Designer: Kurt Krames Manufacturing Director: Tom Debolski Distributed to the book trade worldwide by Springer-Verlag New York, Inc., 233 Spring Street, 6th Floor, New York, NY 10013. -

Warr: a Tool for High-Fidelity Web Application Record and Replay
WaRR: A Tool for High-Fidelity Web Application Record and Replay Silviu Andrica and George Candea School of Computer and Communication Sciences École Polytechnique Fédérale de Lausanne (EPFL), Switzerland {silviu.andrica, george.candea}@epfl.ch Abstract—We introduce WaRR, a tool that records and interactions, and high-fidelity recording requires that all in- replays with high fidelity the interaction between users and teractions be recorded. Replaying fidelity quantifies correctly modern web applications. WaRR consists of two independent played back interactions, and high-fidelity replaying requires components: the WaRR Recorder and the WaRR Replayer. The WaRR Recorder is embedded in a web browser, thus that all interactions be realistically simulated. having access to user actions, and provides a complete inter- High-fidelity record and replay is challenging because the action trace—this confers high recording fidelity. The WaRR client-side code can dynamically change the content of a Replayer uses an enhanced, developer-specific web browser that web page. Modern web applications achieve a high level enables realistic simulation of user interaction—this confers of sophistication, by using complex client-side JavaScript high replaying fidelity. code that vastly extends the range of possible interactions We describe two usage scenarios for WaRR that help developers improve the dependability of web applications: between users and web applications, beyond merely clicking testing web applications against realistic human errors and on links. Nowadays, the HTML pages of a web application generating user experience reports. WaRR helped us discover are mere containers whose contents change in reaction to bugs in widely-used web applications, such as Google Sites, user events (i.e., the HTML code of a page pointed to by a and offers higher recording fidelity compared to current tools. -

Impact of Silverlight in Web Applications
Impact of Silverlight in Web Applications Dr. Khanna SamratVivekanand Omprakash Mijal Mistry Address for Correspondence Information Technology Dept, ISTAR, Sardar Patel University, VVNagar, India The Silverlight platform consists of two major parts, plus an installer and update component Abstract – This paper presents the methodology how Silverlight can change the view of the . Core presentation framework developers and users. We show in this paper how . NET Framework for Silverlight we can make rich graphical user interface into . Installer and updater web applications. There are several highly interactive web applications and web sites. There is a particular value in the combined set of Silverlight provides the Rich Client User tools, technologies, and services included in the Interface. Silverlight has several advantages and Silverlight platform: They make it easier for impact of web applications compares to standard developers to create rich, interactive, and web applications and it also has several features networked applications. Although it is certainly which overpass the normal web applications. possible to build such applications using today's Here we showed how silverlight can impact the Web tools and technologies, developers are web applications by developing a prototype. hindered by many technical difficulties, including incompatible platforms, disparate file Keywords: Web, Web Application, Silverlight, formats and protocols, and various Web Impact browsers that render pages and handle scripts differently. A rich Web application that runs INTRODUCTION perfectly on one system and browser may work very differently on another system or browser, or Silverlight is not only an appealing canvas for may fail altogether. Using today's large array of displaying rich and interactive Web and media tools, protocols, and technologies, it is a massive content to end users. -
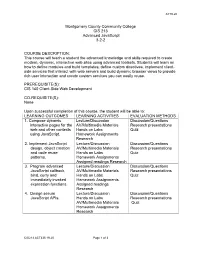
Montgomery County Community College CIS 213 Advanced Javascript 3-2-2
AY19-20 Montgomery County Community College CIS 213 Advanced JavaScript 3-2-2 COURSE DESCRIPTION: This course will teach a student the advanced knowledge and skills required to create modern, dynamic, interactive web sites using advanced toolsets. Students will learn on how to define modules and build templates; define custom directives, implement client- side services that interact with web servers and build dynamic browser views to provide rich user interaction and create custom services you can easily reuse. PREREQUISITE(S): CIS 140 Client-Side Web Development CO-REQUISITE(S): None Upon successful completion of this course, the student will be able to: LEARNING OUTCOMES LEARNING ACTIVITIES EVALUATION METHODS 1. Compose dynamic Lecture/Discussion Discussion/Questions interactive pages for the AV/Multimedia Materials Research presentations web and other contexts Hands on Labs Quiz using JavaScript. Homework Assignments Research 2. Implement JavaScript Lecture/Discussion Discussion/Questions design, object creation AV/Multimedia Materials Research presentations and code reuse Hands on Labs Quiz patterns. Homework Assignments Assigned readings Research 3. Program advanced Lecture/Discussion Discussion/Questions JavaScript callback, AV/Multimedia Materials Research presentations bind, curry and Hands on Labs Quiz immediately invoked Homework Assignments expression functions. Assigned readings Research 4. Design secure Lecture/Discussion Discussion/Questions JavaScript APIs. Hands on Labs Research presentations AV/Multimedia Materials Quiz -

UNIT – I-Rich Internet Applications – SCS1401
SCHOOL OF COMPUTING DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING UNIT – I-Rich Internet Applications – SCS1401 I. Rich Internet Application Overview Introduction to Web2.0 - Key characteristics of Rich Internet Application - Current Rich Internet Application platforms - Rich Internet Application benefits - Rich Internet Application patterns and best practices - Rich Internet Application architecture - Restful Web Services with Nodes. Introduction to Web 2.0 Web 1.0 • Web 1.0 refers to the first stage in the World Wide Web • Entirely made up of web pages connected by hyperlinks. • A set of static websites that were not yet providing interactive content. • Used as “Information portal”. Examples: Amazon,Yahoo, Personal web pages Web 2.0 • Web 2.0 is the term used to describe a variety of web sites and applications that allow anyone to create and share online information or material they have created. • It allows people to create, share, collaborate & communicate. • Allows everyone to produce their content. • Gives the users the possibility to control their data. • Web 2.0 allows groups of people to work on a document or spreadsheet simultaneously. • In the background a computer keeps track of who made what changes where and when. • Web-based applications can be accessed from anywhere. • Web 2.0 Examples • Web applications ( Google Docs, Flickr) • Video sharing sites (YouTube) • Wikis (Media Wiki) • Blogs (WordPress) • Social networking (Facebook) • Microblogging (Twitter) • Hosted services (Google Maps) Web 3.0 • It refers to the evolution of web utilization and interaction which includes altering the Web into a database. • It enables the upgradation of back-end of the web, after a long time of focus on the front- end • Data isn’t owned but instead shared, where services show different views for the same web / the same data. -

Interactive Computer Vision Through the Web
En vue de l'obtention du DOCTORAT DE L'UNIVERSITÉ DE TOULOUSE Délivré par : Institut National Polytechnique de Toulouse (Toulouse INP) Discipline ou spécialité : Informatique et Télécommunication Présentée et soutenue par : M. MATTHIEU PIZENBERG le vendredi 28 février 2020 Titre : Interactive Computer Vision through the Web Ecole doctorale : Mathématiques, Informatique, Télécommunications de Toulouse (MITT) Unité de recherche : Institut de Recherche en Informatique de Toulouse ( IRIT) Directeur(s) de Thèse : M. VINCENT CHARVILLAT M. AXEL CARLIER Rapporteurs : M. MATHIAS LUX, ALPEN ADRIA UNIVERSITAT Mme VERONIQUE EGLIN, INSA LYON Membre(s) du jury : Mme GÉRALDINE MORIN, TOULOUSE INP, Président M. AXEL CARLIER, TOULOUSE INP, Membre M. CHRISTOPHE DEHAIS, ENTREPRISE FITTINGBOX, Membre M. OGE MARQUES, FLORIDA ATLANTIC UNIVERSITY, Membre M. VINCENT CHARVILLAT, TOULOUSE INP, Membre ii Acknowledgments First I’d like to thank my advisors Vincent and Axel without whom that PhD would not have been possible. I would also like to thank Véronique and Mathias for reviewing this manuscript, as well as the other members of the jury, Oge, Géraldine and Christophe for your attention, remarks and interesting discussions during the defense. Again, a special thank you Axel for all that you’ve done, throughout this long period and even before it started. I haven’t been on the easiest path toward completion of this PhD but you’ve always been there to help me continue being motivated and that’s what mattered most! Wanting to begin a PhD certainly isn’t a one-time moment, but for me, the feeling probably started during my M1 internship. I was working in the VORTEX research team (now REVA) on a project with Yvain and Jean-Denis and it was great! Yet “I don’t think so” was more or less what I kept answering to my teachers when they would ask if I wished to start a PhD at that time. -

Article (PDF, 850
ISPRS Annals of the Photogrammetry, Remote Sensing and Spatial Information Sciences, Volume IV-4/W7, 2018 3rd International Conference on Smart Data and Smart Cities, 4–5 October 2018, Delft, The Netherlands SMART CITY WEBGIS APPLICATIONS: PROOF OF WORK CONCEPT FOR HIGH-LEVEL QUALITY-OF-SERVICE ASSURANCE A. Noskov Institute of Geography, Heidelberg University, Germany - [email protected] KEY WORDS: Quality of WebGIS Services, Bitcoin’s Proof of Work, Spatial Information Theory, User Activity Monitoring, User Requests Balancing, Quantity of Spatial Information ABSTRACT: In the frame of smart city initiatives, map-based web applications (WebGIS) are distinguished by the complexity of client-side imple- mentation and high load on web servers. Web-map applications provide non-typical web content usually visualized by JavaScript code. For such applications, higher-level advanced approaches to quality of service (QoS) assessment are required. In this paper, a method based on the estimation of users’ interest in a web page and the information quantity provided by a web page is introduced. In order to implement it, a proof of work (PoW) concept is applied for verification of real users. Moreover, a novel metric is introduced to calculate the information quantity provided by web pages. PoW is used for verification of real users and distinguishing them from bots. Additionally, it can be utilized for balancing of web server load. For monitoring of web pages, an image-based approach is introduced. Web pages are rendered into raster images. A number of metrics describing an image are calculated. This approach allows users to compare and track various web pages, including rich web applications providing complex WebGL content.