Resource Allocation Scheme for Dew Computing Paradigm Using Mobile Grid
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Totalmem),Form Factor,System on Chip,Screen Sizes,Screen Densities,Abis,Android SDK Versions,Opengl ES Versions
Manufacturer,Model Name,Model Code,RAM (TotalMem),Form Factor,System on Chip,Screen Sizes,Screen Densities,ABIs,Android SDK Versions,OpenGL ES Versions 10.or,E,E,2846MB,Phone,Qualcomm MSM8937,1080x1920,480,arm64-v8a 10.or,G,G,3603MB,Phone,Qualcomm MSM8953,1080x1920,480,arm64-v8a 10.or,D,10or_D,2874MB,Phone,Qualcomm MSM8917,720x1280,320,arm64-v8a 4good,A103,4GOOD_Light_A103,907MB,Phone,Mediatek MT6737M,540x960,240,armeabi- v7a 4good,4GOOD Light B100,4GOOD_Light_B100,907MB,Phone,Mediatek MT6737M,540x960,240,armeabi-v7a 7Eleven,IN265,IN265,466MB,Phone,Mediatek MT6572,540x960,240,armeabi-v7a 7mobile,DRENA,DRENA,925MB,Phone,Spreadtrum SC7731C,480x800,240,armeabi-v7a 7mobile,KAMBA,KAMBA,1957MB,Phone,Mediatek MT6580,720x1280,320,armeabi-v7a 7mobile,SWEGUE,SWEGUE,1836MB,Phone,Mediatek MT6737T,1080x1920,480,arm64-v8a A.O.I. ELECTRONICS FACTORY,A.O.I.,TR10CS1_11,965MB,Tablet,Intel Z2520,1280x800,160,x86 Aamra WE,E2,E2,964MB,Phone,Mediatek MT6580,480x854,240,armeabi-v7a Accent,Pearl_A4,Pearl_A4,955MB,Phone,Mediatek MT6580,720x1440,320,armeabi-v7a Accent,FAST7 3G,FAST7_3G,954MB,Tablet,Mediatek MT8321,720x1280,160,armeabi-v7a Accent,Pearl A4 PLUS,PEARL_A4_PLUS,1929MB,Phone,Mediatek MT6737,720x1440,320,armeabi-v7a Accent,SPEED S8,SPEED_S8,894MB,Phone,Mediatek MT6580,720x1280,320,armeabi-v7a Acegame S.A. -

Smart Probes Compatibility
Smart Probes compatibility There are more than 4.000 mobile devices on the market worldwide. The Smart Probes were tested with following mobile devices (see list below). Unfortunately it is impossible to test all of them. Please be aware that much more mobile devices are compatible. Basic system requirements: iOS 8.3 or higher / Android 4.3 or higher and Bluetooth 4.0 or higher. WHITE LIST (compatible) Brand name Version Comment Apple iPad iOS 8.3 or higher Apple iPhone iOS 8.3 or higher ASUS ZenFone 2 ZE551ML/ZE550ML/ZE500CL Android version: 5.0 Dell Venue 8 Android version: 4.4.2 Google Nexus 9 Andorid version: 5.1.1 Google Nexus 7 Android version: 6.0 Generation 2013 or newer Google Nexus 5 Android version: 6.0 HTC One Android version: 5.0.2 HTC One M8 Android version: 5.0.1 HTC One M8 Android version: 4.4.3 HTC One M9 Android version: 5.1 HTC One M9 Android version: 5.0.2 HTC One max Android version: 4.4.2 HTC One mini Android version: 4.4.2 Huawei P7-L10 Android version: 4.4.2 Huawei P6 Android version: 4.4.2 Huawei Y530 Android version: 4.3.0 Maximum 3 probes Huawei Mate7 Android version: 4.4.2 Huawei Ascend P7 mini Android version: 4.3.0 LGE LG G Flex Android version: 4.4.2 LGE LG G2 Android version: 4.4.2 LG G3 LG-D855 Android version: 5.0 LGE LG G4 Android version: 5.1 LGE LG G Pad 8.3 LTE Android version: 4.4.2 LGE LG Nexus 4 Andriod version: 5.1.1 Micromax Canvas A1 AQ4501 Android version: 5.1 Moto G (2nd) XT1068 Android version: 5.0.2 Moto G X1032 Android version: 5.0.2 Moto X (2nd) XT1092 Android version: 5.0 Moto X XT1052 Android version: 4.4.4 Motorola Droid RAZR M Android version: 4.4.2 Motorola Moto E XT1021 Android version: 4.4.4 Maximum 3 probes Motorola Moto E (2nd gen) XT1021 Android version: 5.0.2 Motorola Nexus 6 Android version: 5.1.0 Motorola Nexus 6 Android version: 5.1.1 Motorola RAZR HD XT925 Android version: 4.4.2 Motorola X8 Android version: 4.4.2 OnePlusOne A0001 Android version: 5.0. -

MICROMAX Canvas A1
REVIEW SMARTPHONE SMARTPHONE Price: `6,499 MICROMAX CANvas A1 Price: `6,990 The enticing smartphone, though bundled with mediocre hardware, offers spectacular performance and promises latest updates INTEX AQUA Star — Ashok Pandey Intex Aqua Star is a well designed 5 inch smartphone in sub 8K category he enticing Micromax A1 Android One smartphone is bundled with — Rohit Arora mediocre hardware and runs over Android KitKat 4.4, yet promises qua Star is another budget offering form Intex which comes to offer better performance and latest updates. With its unique T with Android 4.4.2 Kitkat. The phone looks exactly like Aqua design elements like a large metal plate around the camera, the chunky Style which we reviewed last month; however it is just bigger phone boasts 4.5-inch display with 854X480p resolution, which is not A in size. The sleek iPhone 4 kind of look with metal finish edges gives impressive, though offers decent viewing angles and bright colors. The it a premium look. The back panel has a shiny dotted texture which 2 MP front camera can be used for selfie and video chats while the is made up of very light weight plastic that makes the phone quite rear 5 MP autofocus camera with a LED flash produces decent quality slippery. But overall the phone looks good. images in daylight, not so impressive, but one of the finest at this price The 5” IPS LCD screen is bright, offers a good touch response point. Shockingly, you can’t save images without adding a memory stick, particularly during typing, but has a poor resolution of 480x854p though about 2.27 GB space is available out of 4 GB internal storage. -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -
Ubity UC Mobile for Android I PRODUCT SHEET
Ubity UC Mobile for Android I PRODUCT SHEET OVERVIEW Take your favorite UC software in the palm of your hand with Ubity UC Mobile. Available on Android devices, Ubity UC is a dynamic unified communications application that makes it easy to stay connected anytime, anywhere. Use your device’s existing contact list to make and receive high-quality voice over IP (VoIP) business calls over a Wi-Fi or mobile data network connection. Ubity UC is a trusted and secure application that acts as an extension to your phone system. It’s the perfect solution for small and medium-sized enterprises battling the growing demands of a Bring-Your-Own-Device (BYOD) and mobile workforce. KEY FEATURES KEY BENEFITS Premium features include HD Take powerful office communication tools on the go video calling (H.264), messaging and presence Extended standard phone features such as call recording, transfering, merging and splitting calls, and many more Highly secure with signaling and media encryption built-in Consistent look and feel with other Ubity UC applications (SIP-TLS and SRTP) for a unified experience from desktop to mobile Save money by using Wi-Fi or mobile data instead of Utilizes the G.722 codec for paying by the minute, and eliminate long distance charges optimized, high-definition audio Seamless connectivity – employees can get in touch Advanced and intuitive user with team members and clients using the same number interface with multitasking support they would at their desk Let’s start talking ! For more information or to purchase our product, visit studio.ubity.com or contact your Ubity sales representative. -
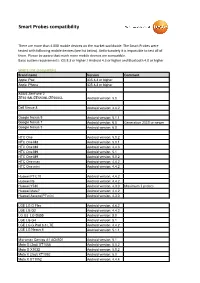
Smart Probes Compatibility
Smart Probes compatibility There are more than 4.000 mobile devices on the market worldwide. The Smart Probes were tested with following mobile devices (see list below). Unfortunately it is impossible to test all of them. Please be aware that much more mobile devices are compatible. Basic system requirements: iOS 8.3 or higher / Android 4.3 or higher and Bluetooth 4.0 or higher. WHITE LIST (compatible) Brand name Version Comment Apple iPad iOS 8.3 or higher Apple iPhone iOS 8.3 or higher ASUS ZenFone 2 ZE551ML/ZE550ML/ZE500CL Android version: 5.0 Dell Venue 8 Android version: 4.4.2 Google Nexus 9 Andorid version: 5.1.1 Google Nexus 7 Android version: 6.0 Generation 2013 or newer Google Nexus 5 Android version: 6.0 HTC One Android version: 5.0.2 HTC One M8 Android version: 5.0.1 HTC One M8 Android version: 4.4.3 HTC One M9 Android version: 5.1 HTC One M9 Android version: 5.0.2 HTC One max Android version: 4.4.2 HTC One mini Android version: 4.4.2 Huawei P7-L10 Android version: 4.4.2 Huawei P6 Android version: 4.4.2 Huawei Y530 Android version: 4.3.0 Maximum 3 probes Huawei Mate7 Android version: 4.4.2 Huawei Ascend P7 mini Android version: 4.3.0 LGE LG G Flex Android version: 4.4.2 LGE LG G2 Android version: 4.4.2 LG G3 LG-D855 Android version: 5.0 LGE LG G4 Android version: 5.1 LGE LG G Pad 8.3 LTE Android version: 4.4.2 LGE LG Nexus 4 Andriod version: 5.1.1 Micromax Canvas A1 AQ4501 Android version: 5.1 Moto G (2nd) XT1068 Android version: 5.0.2 Moto G X1032 Android version: 5.0.2 Moto X (2nd) XT1092 Android version: 5.0 Moto X XT1052 Android version: 4.4.4 Motorola Droid RAZR M Android version: 4.4.2 Motorola Moto E XT1021 Android version: 4.4.4 Maximum 3 probes Motorola Moto E (2nd gen) XT1021 Android version: 5.0.2 Motorola Nexus 6 Android version: 5.1.0 Motorola Nexus 6 Android version: 5.1.1 Motorola RAZR HD XT925 Android version: 4.4.2 Motorola X8 Android version: 4.4.2 OnePlusOne A0001 Android version: 5.0. -

Supported Devices Epihunter Companion App
Supported devices epihunter companion app Manufacturer Model Name RAM (TotalMem) Ascom Wireless Solutions Ascom Myco 3 1000-3838MB Ascom Wireless Solutions Ascom Myco 3 1000-3838MB Lanix ilium Pad E7 1000MB RCA RLTP5573 1000MB Clementoni Clempad HR Plus 1001MB Clementoni My First Clempad HR Plus 1001MB Clementoni Clempad 5.0 XL 1001MB Auchan S3T10IN 1002MB Auchan QILIVE 1002MB Danew Dslide1014 1002MB Dragontouch Y88X Plus 1002MB Ematic PBS Kids PlayPad 1002MB Ematic EGQ347 1002MB Ematic EGQ223 1002MB Ematic EGQ178 1002MB Ematic FunTab 3 1002MB ESI Enterprises Trinity T101 1002MB ESI Enterprises Trinity T900 1002MB ESI Enterprises DT101Bv51 1002MB iGet S100 1002MB iRulu X40 1002MB iRulu X37 1002MB iRulu X47 1002MB Klipad SMART_I745 1002MB Lexibook LexiTab 10'' 1002MB Logicom LEMENTTAB1042 1002MB Logicom M bot tab 100 1002MB Logicom L-EMENTTAB1042 1002MB Logicom M bot tab 70 1002MB Logicom M bot tab 101 1002MB Logicom L-EMENT TAB 744P 1002MB Memorex MTAB-07530A 1002MB Plaisio Turbo-X Twister 1002MB Plaisio Coral II 1002MB Positivo BGH 7Di-A 1002MB Positivo BGH BGH Y210 1002MB Prestigio MULTIPAD WIZE 3027 1002MB Prestigio MULTIPAD WIZE 3111 1002MB Spectralink 8744 1002MB USA111 IRULU X11 1002MB Vaxcare VAX114 1002MB Vestel V Tab 7010 1002MB Visual Land Prestige Elite9QL 1002MB Visual Land Prestige Elite8QL 1002MB Visual Land Prestige Elite10QS 1002MB Visual Land Prestige Elite10QL 1002MB Visual Land Prestige Elite7QS 1002MB Dragontouch X10 1003MB Visual Land Prestige Prime10ES 1003MB iRulu X67 1020MB TuCEL TC504B 1020MB Blackview A60 1023MB -
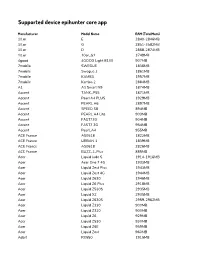
Supported Device Epihunter Core App
Supported device epihunter core app Manufacturer Model Name RAM (TotalMem) 10.or E 2840-2846MB 10.or G 2851-3582MB 10.or D 2868-2874MB 10.or 10or_G2 3749MB 4good 4GOOD Light B100 907MB 7mobile SWEGUE 1836MB 7mobile Swegue 2 1861MB 7mobile KAMBA 1957MB 7mobile Kamba 2 2884MB A1 A1 Smart N9 1874MB Accent TANK_P55 1871MB Accent Pearl A4 PLUS 1929MB Accent PEARL A6 2897MB Accent SPEED S8 894MB Accent PEARL A4 Lite 903MB Accent FAST73G 904MB Accent FAST7 3G 954MB Accent Pearl_A4 955MB ACE France AS0518 1822MB ACE France URBAN 1 1839MB ACE France AS0618 2826MB ACE France BUZZ_1_Plus 885MB Acer Liquid Jade S 1914-1916MB Acer Acer One 7 4G 1933MB Acer Liquid Zest Plus 1943MB Acer Liquid Zest 4G 1944MB Acer Liquid Z630 1946MB Acer Liquid Z6 Plus 2918MB Acer Liquid Z530S 2935MB Acer Liquid X2 2935MB Acer Liquid Z630S 2959-2962MB Acer Liquid Z330 900MB Acer Liquid Z320 900MB Acer Liquid Z6 929MB Acer Liquid Z530 930MB Acer Liquid Z6E 959MB Acer Liquid Zest 960MB Adart RX550 1915MB Adart ALIGATOR RX510 900MB Adart ALIGATOR S5510 Duo 957MB Adart ALIGATOR S5062 Duo 963MB Adart S5060 Duo 967MB Adart ALIGATOR S4080 Duo 967MB Admiral Overseas Corporation O7 1944MB Advan digital i6c 1803MB Advan digital G-Tab 1803MB Advan digital I5E 1814MB Advan digital 5061 1817MB Advan digital i6A 1839MB Advan digital i55K 1884MB Advan digital i10 1900MB Advan digital I Tab 1901MB Advan digital i5C plus 1918MB Advan digital I5E 1944MB Advan digital G2 2807MB Advan digital ADVAN G2 plus 2857MB Advan digital A8 3818MB Advan digital G3 3830MB Advan digital S5E_NXT 703-964MB -

Offer Terms & Conditions • This Promotional Offer Is Only Available
Offer Terms & Conditions This promotional offer is only available to customers purchasing select models of smartphones (list available below) from Amazon.in between Aug 10th, 2015 and Aug 12th, 2015. In addition, this offer is only available to Amazon.in customers (i) located in India, (ii) that have set India as their country of record in their Amazon.in account settings, (iii) with a billing address in India and (iv) who have accepted the Amazon.in Kindle Store Terms of Use. Any customer attempting to redeem this promotion from outside of India (or from a device with a non-India IP address) are not eligible for this offer. By August 15, 2015 eligible participants will receive the promotion code to buy eBooks worth Rs.300 This is a limited time offer and the promotional credit will expire on September 9th, 2015 The promotional credit may only be applied to Kindle eBook titles sold and delivered by be Amazon Digital South Asia Inc. Offer limited to one promotional credit per qualifying device purchase. Promotional supplies are limited. Promotional credit will be allocated proportionally among all qualifying items in your order. If any of the products or content related to this offer are returned, your refund will equal the amount you paid for the product or content, subject to applicable refund policies. Standard terms and conditions, including the Amazon.in Conditions of Use and Sale and Privacy Notice, apply to this promotion, use of the Amazon.in website and the Kindle reading apps. The promotional credit is non-transferable, not exchangeable or redeemable for cash or other goods or services and may not be combined with other credits or special offers. -

Mobile Mcode 3D Cover Mold Apple Iphone 4-EM02 EM01 Yes 0 Apple Iphone 4S-EM01 EM02 Yes 0 Apple Iphone 5/5S/SE-EM04 EM03 Yes
ExclusiveBay Solutions More than 500 models of 3D Sublimation Mobile Covers, Molds, Silicon Whatsapp or Call +91-8199993691, +91-8587095427 Mobile Mcode 3D Cover Mold Apple Iphone 4-EM02 EM01 Yes 0 Apple Iphone 4S-EM01 EM02 Yes 0 Apple Iphone 5/5s/SE-EM04 EM03 Yes 0 Apple Iphone 5S/5/SE-EM03 EM04 Yes 0 Apple Iphone 6-EM06 EM05 Yes 0 Apple Iphone 6S-EM05 EM06 Yes 0 Samsung Galaxy J7 (2015) EM08 Yes 0 Samsung Galaxy J1 (2015) EM09 Yes Yes Samsung Galaxy J5 (2016) EM10 Yes Yes Samsung Galaxy J5 (2015) EM11 Yes 0 Samsung Galaxy J2 (2016)-EM96 EM12 Yes 0 Samsung Galaxy J2 (2015) EM13 Yes 0 Xiaomi Redmi Note 3 EM14 Yes 0 Samsung Galaxy J7 (2016) EM15 Yes 0 Xiaomi Mi 5 EM16 Yes 0 Xiaomi Mi 4 EM17 Yes Yes Xiaomi Mi 4i EM18 Yes 0 Samsung Galaxy E5(E500) (2016) EM19 Yes 0 Samsung Galaxy E7(E700) (2016) EM20 Yes 0 Motorola Moto X Play EM21 Yes 0 Motorola Moto G Turbo-EM24-EM29 EM22 Yes 0 Motorola Moto X Style EM23 Yes 0 Motorola Moto Turbo-EM22-EM29 EM24 Yes 0 Motorola Moto X Force-EM563 EM25 Yes 0 Motorola Moto X 2nd Gen EM26 Yes 0 Motorola Moto G 1st Gen EM27 Yes 0 Motorola Moto G 2nd Gen EM28 Yes Yes Motorola Moto G 3rd Gen-EM22 EM29 Yes 0 Motorola Moto E 1st Gen EM30 Yes Yes Lenovo Vibe K5-EM45 EM31 Yes Yes Lenovo Vibe K4 Note/A7010-EM272 EM32 Yes 0 Lenovo A2010 4G-EM606/441 EM34 Yes 0 Lenovo A7000/K3 Note-EM342 EM35 Yes 0 Huawei P9 EM36 Yes Yes LeEco (LeTV) Le 2 Pro-EM600 EM41 Yes Yes Lenovo K5 Note EM42 Yes 0 Lenovo Vibe K5 Plus-EM31 EM45 Yes 0 Lenovo Vibe P1 Turbo-EM343 EM46 Yes 0 LG G5 EM47 Yes 0 LG Stylus 2 Plus-EM577 EM48 Yes 0 Micromax -
Device Catalogue
Acer Liquid Jade 2 Archos 133 Oxygen BUSH SPIRA E4X Asus ZenFone 2 Laser ZenPad 8.0 (Z380M) ZenFone Selfie Zenpad 8 LTE (ZE550KL) (ZD551KL) Zenfone 3 ZenFone 2 Laser ZenFone 3 Max ZenPad 10 (Z301MFL) (ZE600KL) (ZC553KL) ZenFone 2 Laser Zenfone 3 Deluxe ASUS ZenPad Z8 ZenPad S 8.0 (Z580C) (ZE601KL) (ZS570KL) ZenPad 3S 10 LTE Zenfone 3 Laser Zenfone3 Ultra ZenPad 3 8.0 (Z500KL) ZenFone 2 Laser ZenFone 2 (ZE550ML) Fonepad 7 LTE ZenFone 2 (ZE551ML) (ZE551KL) (FE375CL) Zenfone AR ZenFone 3 Zoom ZenPad S 8.0 ZenFone 3 Deluxe (ZE553KL) (Z580CA) (ZS550KL) Zenfone MAX Zenbo ZenPad 10 ZenPad 10 (Z300M) (ZC550KL) ASUS_ Zenfone Max ZenPad Z10 ZenFone Zoom ASUS ZenPad 3S 10 (ZX551ML) ZenPad 10 (Z301ML) BlackBerry PRIV by BlackBerry Coolpad Cool C1 i3-M1 3600i ivvi i3P-02 C103 ivvi i3-01 FLY Cirrus 13 Swift 2 Cirrus 14 Storm Foxconn International Holdings Limited brown 1 Cat S60 TDC800 Handheld LS-5002 UP Prime Blackview BV6000 ARK Bebefit M551 Lava iris 880 NUU X5 Beeline Pro 6 Spectra Ranger 5 LIFE ONE X2 MINI M1092R SMART Race2 4G C-eight A3_mini LIFE ONE X2 TDC500 Handheld TurboTab E1 DG-A97QT LS-5201 NUU M2 SMART 4G Octa 5.5 NUU M3 Fujitsu F-02H F-04H F-04G F-04J F-01J Gionee GM 6 s GM 6 d Google Nexus 5X Nexus 6 Pixel Pixel XL Pixel C Nexus 9 Nexus 9 LTE Nexus 6P Google Cros Chromebook Plus AOpen RK3288 10" Asus Chromebook Flip Chromebase C100PA Hisense C30 PERLA Iron Pro C20S L636 F22 HMD Global Nokia 3 Nokia 5 Nokia 6 HTC Butterfly 3 One A9 U11 One M9 U Ultra HTV31 HTV33 10 evo Bolt M10 Huawei HUAWEI nova Mate 9 HUAWEI Y7 P8max HUAWEI G9 Plus P10 -
UFED, UFED Physical Analyzer, UFED Logical Analyzer, and Cellebrite Reader V7.27
RELEASE NOTES UFED, UFED Physical Analyzer, UFED Logical Analyzer, and Cellebrite Reader v7.27 December 2019 Now supporting: 30,391 device profiles App versions: 10,002 Forensic methods v. 7.27 Total Logical extraction 143 11,815 Physical extraction* 130 7,475 File system extraction 139 7,478 Extract/disable user lock 39 3,623 Total 451 30,391 *Including GPS devices The number of unique mobile devices with passcode capabilities is 5,501 App support • Updated applications - support for 128 new app versions for iOS and Android devices UFED 4PC/ UFED Touch2 Perform iOS full file system extractions from devices after jailbreak iOS extraction is a tough nut to crack, and a key challenge faced by forensic practitioners on a daily basis. To overcome this challenge, we are excited to announce Cellebrite’s support for the most comprehensive extraction of an iOS device. With the newly introduced ‘checkm8’ exploit, forensic examiners can now gain lawful access to iOS devices to extract more digital evidence. This includes access to 3rd party application data, locations, health data, passwords, keys, and tokens stored in the Keychain. This support is relevant to unlocked iPhones from iPhone 5S through to iPhone X. UFED, UFED Physical Analyzer, UFED Logical Analyzer, and Cellebrite Reader v7.27 | December 2019 | www.cellebrite.com Our support of checkm8 and checkra1n is in two phases: • This version (7.27) includes full extraction support for devices after ‘checkra1n’ has been applied externally (using the downloadable jailbreaking tool available at https://checkra.in). You do not need to install Cydia or the AFC2 package, just connect the device after applying ‘checkra1n’.