Tech Report 2 V12 (Dragged)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Effect of Paclitaxel-Cisplatin Chemotherapy Towards Hemoglobin, Platelet, and Leukocyte Levels in Epithelial Ovarian Cancer Patients
Journal of Applied Pharmaceutical Science Vol. 9(01), pp 104-107, January, 2019 Available online at http://www.japsonline.com DOI: 10.7324/JAPS.2019.90115 ISSN 2231-3354 Effect of paclitaxel-cisplatin chemotherapy towards hemoglobin, platelet, and leukocyte levels in epithelial ovarian cancer patients Rini Noviyani1*, P. A. Indrayathi2, I. N. G Budiana3, Rasmaya Niruri4, K. Tunas5, N. M. Dhatu Dewi Adnyani1 1Department of Pharmacy, Faculty of Mathematics and Sciences, Udayana University, Bali, Indonesia. 2Department of Public Health, Faculty of Medicine, Udayana University, Bali, Indonesia. 3Department of Obstetrics and Gynecology, Faculty of Medicine, Udayana University, Bali, Indonesia. 4Department of Pharmacy, Faculty of Mathematics and Sciences, Sebelas Maret University, Central Java, Indonesia. 5Department of Public Health, Faculty of Health, Science and Technology, Dhyana Pura University, Bali, Indonesia. ARTICLE INFO ABSTRACT Received on: 04/06/2018 Paclitaxel-cisplatin combination chemotherapy as first-line treatment of epithelial ovarian cancer (EOC) is known to Accepted on: 14/10/2018 cause myelosuppression that leads to decreased hemoglobin, platelet and leukocyte levels. This study aims to evaluate Available online: 31/01/2019 the side effect of paclitaxel-cisplatin chemotherapy in EOC patients with hematologic status at Sanglah General Hospital, Denpasar. Observational retrospective research was conducted from February to May 2018. Samples were EOC patients who underwent six cycles of paclitaxel-cisplatin chemotherapy at Sanglah General Hospital, Bali- Key words: Indonesia from January 2015 to May 2018. Side effects of chemotherapy were seen from hemoglobin, platelet, and Chemotherapy, paclitaxel- leukocyte data before and after six cycles of chemotherapy. Hematologic data were analyzed and compared using cisplatin, epithelial ovarian Paired T-test with a level of confidence of 95% using the STATA version 14 software. -

How Project Based Learning Boost Learning Environment
Advances in Social Science, Education and Humanities Research (ASSEHR), volume 66 1st Yogyakarta International Conference on Educational Management/Administration and Pedagogy (YICEMAP 2017) How Project Based Learning Boost Learning Environment Pujiriyanto Mulyoto The Faculty of Teacher Training and Education The Faculty of Teacher Training and Education Sebelas Maret University Sebelas Maret University Surakarta, Indonesia Surakarta, Indonesia e-mail: [email protected] [email protected] Samsi Haryanto Dewi Rochsantiningsih The Faculty of Teacher Training and Education The Faculty of Teacher Training and Education Sebelas Maret University Sebelas Maret University Surakarta, Indonesia Surakarta, Indonesia e-mail: [email protected] [email protected] Abstract— Environment is one of the contributing factors to education is still taught teoritically and it is still focus on develop creativity. This study aimed to investigate the mastery of learning material so pedagogical aspect is performance of the project-based learning (PBL) model designed becoming imperative challenge. There are many debates to develop creative learning environments according to the which are still going on about the relevance, pedagogies, students’ perceptions. The method employed for the study is quasi experimental using one group pretest posttest design effectiveness, even about the sense of entrepreneurship inlvolved 42 students of an entrepreneurship class. A scale was education in general [2]. There are numerous challenges faced developed to measure the students’ perceptions of learning by entrepreneurship educators to enhance learning based on environment after the treatment. We also observed the students’ their experiences which offers many activities [3]. activities and responses during the project implementation. Paired sample t-test used to analyze the difference between two Creativity requires a condusive environment related to sets of observation. -

Automatically Generated PDF from Existing Images
We would Like to Thank the Sponsors of the Event Melayani Negeri, Kebanggaan Bangsa A List of Internal and External Reviewers for Abstracts Submitted for The 61st International TEFLIN Conference The organizing committee of the 61st International TEFLIN Conference would like to acknowledge the following colleagues who served as anonymous reviewers for abstract/proposal submissions. Internal Reviewers Chair Joko Nurkamto (Sebelas Maret University, INDONESIA) Members Muhammad Asrori (Sebelas Maret University, INDONESIA) Abdul Asib (Sebelas Maret University, INDONESIA) Dewi Cahyaningrum (Sebelas Maret University, INDONESIA) Djatmiko (Sebelas Maret University, INDONESIA) Endang Fauziati (Muhammadiyah University of Surakarta, INDONESIA) Dwi Harjanti (Muhammadiyah University of Surakarta, INDONESIA) Diah Kristina (Sebelas Maret University, INDONESIA) Kristiyandi (Sebelas Maret University, INDONESIA) Martono (Sebelas Maret University, INDONESIA) Muammaroh (Muhammadiyah University of Surakarta, INDONESIA) Ngadiso (Sebelas Maret University, INDONESIA) Handoko Pujobroto (Sebelas Maret University, INDONESIA) Dahlan Rais (Sebelas Maret University, INDONESIA) Zita Rarastesa (Sebelas Maret University, INDONESIA) Dewi Rochsantiningsih (Sebelas Maret University, INDONESIA) Riyadi Santosa (Sebelas Maret University, INDONESIA) Teguh Sarosa (Sebelas Maret University, INDONESIA) Endang Setyaningsih (Sebelas Maret University, INDONESIA) Gunarso Susilohadi (Sebelas Maret University, INDONESIA) Hefy Sulistowati (Sebelas Maret University, INDONESIA) Sumardi (Sebelas -

A Study of the Association Between Selenium and Cardiovascular Disease in Lampung, Indonesia
ECOLOGICAL STUDY OF SELENIUM AND CARDIOVASCULAR DISEASE A STUDY OF THE ASSOCIATION BETWEEN SELENIUM AND CARDIOVASCULAR DISEASE IN LAMPUNG, INDONESIA Mutakin1,3, Ida F Rivai2, Andi Setiawan2, Rizky Abdulah3, 4, Kenji Kobayashi4, Chiho Yamazaki4, Satomi Kameo4, Minato Nakazawa4 and Hiroshi Koyama4 1Department of Pharmaceutical Analysis and Medicinal Chemistry, 3Department of Pharmacology and Clinical Pharmacy, Faculty of Pharmacy, Padjadjaran University, Jatinangor; 2Faculty of Mathematics and Natural Science, Lampung University, Lampung, Indonesia; 4Department of Public Health, Gunma University Graduate School of Medicine, Maebashi, Japan Abstract. Selenium deficient areas have been associated with a higher prevalence of cardiovascular disease in some countries. In this study, we investigated the cor- relation between cardiovascular disease prevalence and selenium concentration in paddy soil and rice grains, the main staple food in Lampung, Indonesia. Paddy soil and rice samples (ns = 35) from eight regencies (nd = 8) in Lampung were analyzed for selenium content. The prevalences of heart disease, stroke, and hypertension in those regencies were obtained from the Ministry of Health of Indonesia. The Shapiro-Wilk’s test was used to examine the data distribution. The Pearson’s correlation was used to examine the correlation between cardiovascular disease prevalence and selenium concentration in the paddy soil and rice grains. Heart disease prevalence was negatively correlated with the selenium concentration in the paddy soil (r = -0.77, p = 0.02) and rice grain (r = -0.71, p = 0.05). A negative correlation was seen for stroke prevalence and selenium concentration in paddy soil (r = -0.76, p = 0.02). Hypertension prevalence was negatively correlated with the selenium concentration in the rice grains (r = -0.83, p = 0.01). -
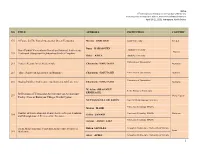
1 Reflections of Vernacular Architecture On
ISVS-6 6th International Seminar on Vernacular Settlements, Contemporary Vernaculars: Places, Processes and Manifestations April 19-21, 2012, Famagusta, North Cyprus NO TITLE AUTHOR/S INSTITUTION COUNTRY 375 A Future for The Past of Spectacular Desert Vernacular Marwa DABIAIEH Lund University Sweden Rana KARASOZEN From Turkish Vernacular to Formal and Informal Settlements: Anadolu University Turkey 203 Traditional OdunpazariNeighbourhood and its Periphery Guler KOCA Anadolu University University of Queensland 214 Tonga‟s Reason for its Western Fale Charmaine 'IIAIUTALEI Australia 215 Bure: Product of Spirituality and Romance Charmaine 'IIAIUTALEI University of Queensland Australia University of Queensland 216 Staging Pasifika Architecture: Auckland and Salt Lake City Australia Charmaine 'IIAIUTALEI M. Selen ABBASOĞLU Lefke European University ERMĠYAGĠL Reflections of Vernacular Architecture on Architecture 239 North Cyprus Today: Case of Koruçam Village, North Cyprus Nil PAġAOĞULLARI ġAHĠN Eastern Mediterranean University Universiti Teknologi MARA Mawar MASRI Conflict of Oenwership and Identity between Negeri Sembilan Universiti Teknologi MARA Malaysia 284 Zalina SAMADI and Minangkabau: A Review of the Literature Universiti Teknologi MARA Azlaini ABDUL AZIZ Focus Mediterraneum: Vernacular Architecture, Prelude of Ruben ALCOLEA School of Architecture, University of Navarre Spain 393 Modernity Aitor ACILU School of Architecture, University of Navarre 1 ISVS-6 6th International Seminar on Vernacular Settlements, Contemporary Vernaculars: -

Telkom University
FACT SHEET 2018-2019 INSTITUTIONAL DETAILS Name Telkom University City, Country Bandung, Indonesia Website https://io.telkomuniversity.ac.id/ About the university Telkom University (Tel-U) is a modern, high-quality private university that was founded in 2013. It focuses on the knowledge areas of the information and communication technologies, business management, applied science, and creative industries. It has 29,000 enrolled students in 26 undergraduate studies and 4 Masters. Tel-U welcomes more than 300 international mobility students per year, and 30% of their undergraduate students have done an exchange abroad. Tel-U is the best private university in reputable scientific publications ranked in SINTA by the Indonesian ministry of higher education in 2018. Tel-U is the 2nd best private university in Indonesia based on UI Green Metric ranking of World Universities 2017 result. Tel-U is also among the top ten private university in Indonesia webometrics based on the ranking web of universities 2018. INTERNATIONAL RELATIONS SERVICE Website https://io.telkomuniversity.ac.id/research/about-international- office-tel-u/ Manager Indah Fajarwati [email protected] Staff responsible for Indah Fajarwati Erasmus+ ICM [email protected] projects Incoming and Lia Marlia outgoing students [email protected] Incoming and Indah Fajarwati outgoing PhD [email protected] students and staff Mobility and Lia Marlia Reception Offices International Office Telkom University (OMA) Bangkit building R118, Bandung technoplex Jl. Telekomunikasi no.1, Dayeuhkolot, Bandung 40257 Phones: +62 81321123 400|+62 22 7564108 ext. 2400 Email: [email protected] or [email protected] This office assists students attending: • Faculty of Electrical Engineering • Faculty of Industrial Engineering • Faculty of Informatics Engineering • Faculty of Economic and Business • Faculty of Communication and Business • Faculty of Creative Industry • Faculty of Applied Science Office hours: Mondays to Fridays: 09.00 a.m. -

World Higher Education Database Whed Iau Unesco
WORLD HIGHER EDUCATION DATABASE WHED IAU UNESCO Página 1 de 438 WORLD HIGHER EDUCATION DATABASE WHED IAU UNESCO Education Worldwide // Published by UNESCO "UNION NACIONAL DE EDUCACION SUPERIOR CONTINUA ORGANIZADA" "NATIONAL UNION OF CONTINUOUS ORGANIZED HIGHER EDUCATION" IAU International Alliance of Universities // International Handbook of Universities © UNESCO UNION NACIONAL DE EDUCACION SUPERIOR CONTINUA ORGANIZADA 2017 www.unesco.vg No paragraph of this publication may be reproduced, copied or transmitted without written permission. While every care has been taken in compiling the information contained in this publication, neither the publishers nor the editor can accept any responsibility for any errors or omissions therein. Edited by the UNESCO Information Centre on Higher Education, International Alliance of Universities Division [email protected] Director: Prof. Daniel Odin (Ph.D.) Manager, Reference Publications: Jeremié Anotoine 90 Main Street, P.O. Box 3099 Road Town, Tortola // British Virgin Islands Published 2017 by UNESCO CENTRE and Companies and representatives throughout the world. Contains the names of all Universities and University level institutions, as provided to IAU (International Alliance of Universities Division [email protected] ) by National authorities and competent bodies from 196 countries around the world. The list contains over 18.000 University level institutions from 196 countries and territories. Página 2 de 438 WORLD HIGHER EDUCATION DATABASE WHED IAU UNESCO World Higher Education Database Division [email protected] -

Development and Evaluation of the Blended Learning Courses at Sam Ratulangi University in Indonesia
International Journal of e-Education, e-Business, e-Management and e-Learning, Vol. 2, No. 3, June 2012 Development and Evaluation of the Blended Learning Courses at Sam Ratulangi University in Indonesia. Sary. D. E. Paturusi, Yoshifumi Chisaki, and Tsuyoshi Usagawa examinations given at specified dates and times. On the Abstract—The advancement in educational technology other hand, electronic learning (e-learning) refers to the precipitated by the dissemination of Internet in recent years emergent phenomenon in which teaching and learning occur has a potential to improve the quality of education by via the Internet. Blended learning is the learning paradigm encouraging participation and collaboration between that attempts to optimize both traditional learning and instructors and students. Educational institutions use information and communication technology (ICT) as a tool for distance learning advantages, potentials and benefits while teaching and learning in a number of ways including but not eliminating both learning paradigms shortages and limited to Internet-based content delivery and visualization. challenges [2]. One notable difference in this new approach This research involves the development and evaluation of toward learning is that an instructor acts as a facilitator or a blended learning courses at University of Sam Ratulangi guide to the students. E-learning has the potential to (UNSRAT), Manado, North Sulawesi, Indonesia. The current maximize chance of a students to interact with instructors work was aimed to redesign two courses of the existing curriculum based on the ADDIE instructional design model to and other students by online via the Internet, regardless of support student-centered learning and develop e-learning time and place. -

Protection of the Rights of Indigenous Peoples Study of Communal Land in the Management of Oil Palm Plantation in Indonesia by : Firdaus1
Protection of the Rights of Indigenous Peoples Study of Communal Land In The Management of Oil Palm Plantation in Indonesia By : Firdaus1 I. Preliminary A. Background One century of palm journey2 has demonstrated its role as a contributor to foreign exchange. Riau Provincial Secretariat, noted oil palm plantations in Riau province in 2010 and 2011 has contributed Rp16, 65 trillion from CPO exports of palm oil and its derivatives.3 Palm oil industry contributed to the enhancement of the national economy, employment, improved quality of life of local communities. In addition, palm oil is also a negative impact on society and the environment. Often the respect and protection of the rights of indigenous peoples especially communal land neglected oil palm plantations (PPKS). Palm plantation is a product of forest modernization by the state. Agricultural societies transformed into urban industrial society. Social rules, customs, habits that have been collected and characterized the life of a village or hamlet is replaced by the rhythm of the factory and the city.4 The difference in modern and traditional paradigms cause conflict (gaps) between the corporation with indigenous peoples (traditional), and 1 Lecturer of Faculty of Law, University of Riau, doctoral candidate in law at Islamic University of Indonesia. 2 M. Badrun, Milestones Change Through PIR Program, Directorate General of Plantations Ministry of Agriculture of the Republic of Indonesia, Jakarta, 2010, p 3. 3 http://birokeuangan.riau.go.id/k4/gallery/arsip-berita/37-demo4/102-ekspor-cpo-sawit-riau- capai-rp-1665-triliun.html, accessed on May 4, 2012. 4 Francis Fukuyama, The Great Discruption: Human Nature and the reconstitution of Social Order, translated by Masri Maris, Great Disruption of Human Nature and the New Social Administration, U.S. -

Proceedings the Second International Conference
PROCEEDINGS THE SECOND INTERNATIONAL CONFERENCE ON EDUCATION AND LANGUAGE 2nd ICEL 2014 20 -22 MAY 2013 Organized by: Faculty of Teacher Training and Education (FKIP), English Education Study Program of Bandar Lampung University Zainal Abidin Pagar Alam street No.89 Labuhan Ratu, Bandar Lampung, Indonesia Phone: +62 721 36 666 25, Fax: +62 721 701 467 www.ubl.ac.id The Second International Conference on Education and Language (2nd ICEL) 2014 ISSN 2303-1417 Bandar Lampung University (UBL), Indonesia PREFACE The activities of the International Conference are in line and very appropriate with the vision and mission of Bandar Lampung University (UBL) to promote training and education as well as research in these areas. nd On behalf of the Second International Conference of Education and Language (2 ICEL 2014) organizing committee, we are very pleased with the very good responses especially from the keynote speakers and from the participants. It is noteworthy to point out that about 80 technical papers were received for this conference The participants of the conference come from many well known universities, among others: University of Wollongong, NSW Australia, International Islamic University Malaysia, Kyoto University (Temple University (Osaka), Japan - Jawaharlal Nehru University, New Delhi, India - West Visayas State University College of Agriculture and Forestry, Lambunao, Iloilo, Philipine - Bahcesehir University, Istanbul, Turkey - The Higher Institute of Modern Languages, Tunisia - University of Baku, Azerbaijan - Sarhad University, -

The 3Rd ICOR 2018
i IORA International Conference on Operations Research Manado, Indonesia, September 20-21, 2018 rd The 3 ICOR 2018 Operations Research (OR) had become powerful decision making tools worldwide. In its use, Management Science (MS) is used as another term for OR. Concept of OR is borderless as it can be derived from various discipline such as Mathematics, Statistics, Economics, Engineering, Marine Science, Social, etc. to make a new set of knowledge for decision making. Today, OR has become a professional discipline which deals with the application of scientific methods in decision making theory. The scope of OR can be used to find best solution for both simple and complex problem. It is beneficial in every aspect of human life regarding resources optimization. OR is widely used in important and main fields such as national planning and budgeting, transportation, education, agriculture, and marine management. Therefore, research and study involving OR are inevitable. Number of research and study about OR or using OR as tools is high these years. This is accommodated by Indonesian Operations Research Association (IORA) IORA as one of OR organisations in an annual international conference entitled International Conference on Operations Research (ICOR). ICOR 2018 is the third conference. This initiates to bring together OR/MS researchers, academicians and practitioners, whose collective work has sustained continuing OR/MS contribution to decision-making in many fields of application. It can be considered as good platforms for the OR/MS community, particularly in Indonesia, to meet each other and to exchange ideas. ii IORA International Conference on Operations Research Manado, Indonesia, September 20-21, 2018 COMMITTEE: Conference Chair: Dr. -

Download Article (PDF)
Advances in Social Science, Education and Humanities Research, volume 439 Tarumanagara International Conference on the Applications of Social Sciences and Humanities (TICASH 2019) Utilization of Peatland Technology for Food Availability in a Legal Perspective Jeane Neltje Saly Christine S.T. Kansil Adriel Michael Tirayo Faculty of Law Tarumanagara University Faculty of Law Tarumanagara University Faculty of Law Tarumanagara University Letjen S. Parman Street Number 1, West Letjen S. Parman Street Number 1, West Jakarta, Indonesia Letjen S. Parman Street Number 1, West Jakarta, Indonesia [email protected] Jakarta, Indonesia [email protected] [email protected] Abstract—The results of this research revealed that Law No. 18 of 2012 about Food [1], functions as a problematics with the use of peat technology due to the rate of guideline for the implementation of an orderly food, on the conversion of agricultural land, expansion of agricultural land, consideration that the most basic human needs and fulfillment are and increasing production of food crops is not optimal, despite part of human rights guaranteed in the Constitution of the long-term solutions to the crisis of fire and haze, therefore it is Republic of Indonesia in 1945. Therefore, the State is obliged important to implement Government Regulation of 2016 about to realize the availability, affordability, and fulfillment of the Protection and Management of Peat Ecosystems to meet the adequate, safe, quality, and nutritious food consumption that is basic needs of the community from local resources. The balanced, both at the national and regional levels to individuals problem is what is the government’s effort to improve the evenly throughout the territory of the Unitary Republic of realization of food sufficiency through the use of peatlands and Indonesia.