Unlocking Encryption: Information Security and the Rule of Law
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2020 Sneak Peek Is Now Available
GISWatch 2020 GISW SNEAK PEEK SNEAK PEEK GLOBAL INFORMATION atch 2020 SOCIETY WATCH 2020 Technology, the environment and a sustainable world: Responses from the global South ASSOCIATION FOR PROGRESSIVE COMMUNICATIONS (APC) AND SWEDISH INTERNATIONAL DEVELOPMENT COOPERATION AGENCY (SIDA) GISWatch 2020 SNEAK PEEK Global Information Society Watch 2020 SNEAK PEEK Technology, the environment and a sustainable world: Responses from the global South APC would like to thank the Swedish International Development Cooperation Agency (Sida) for their support for Global Information Society Watch 2020. Published by APC 2021 Creative Commons Attribution 4.0 International (CC BY 4.0) https://creativecommons.org/licenses/by/4.0/ Some rights reserved. Disclaimer: The views expressed herein do not necessarily represent those of Sida, APC or its members. GISWatch 2020 SNEAK PEEK Table of contents Introduction: Returning to the river.... ............................................4 Alan Finlay The Sustainable Development Goals and the environment ............................9 David Souter Community networks: A people – and environment – centred approach to connectivity ................................................13 “Connecting the Unconnected” project team www.rhizomatica.org; www.apc.org Australia . 18 Queensland University of Technology and Deakin University marcus foth, monique mann, laura bedford, walter fieuw and reece walters Brazil . .23 Brazilian Association of Digital Radio (ABRADIG) anna orlova and adriana veloso Latin America . 28 Gato.Earth danae tapia and paz peña Uganda . .33 Space for Giants oliver poole GISWatch 2020 SNEAK PEEK Introduction: Returning to the river Alan Finlay do not have the same power as governments or the agribusiness, fossil fuel and extractive industries, and that to refer to them as “stakeholders” would The terrain of environmental sustainability involves make this power imbalance opaque. -

Controversy, Consensus, and Contradictions
Humour in Contemporary France Controversy, Consensus, and Contradictions Studies in Modern and Contemporary France 3 Studies in Modern and Contemporary France Series Editors Professor Gill Allwood, Nottingham Trent University Professor Denis M. Provencher, University of Arizona Professor Martin O’Shaughnessy, Nottingham Trent University The Studies in Modern and Contemporary France book series is a new collaboration between the Association for the Study of Modern and Contemporary France (ASMCF) and Liverpool University Press (LUP). Submissions are encouraged focusing on French politics, history, society, media and culture. The series will serve as an important focus for all those whose engagement with France is not restricted to the more classically literary, and can be seen as a long-form companion to the Association’s journal, Modern and Contemporary France, and to Contemporary French Civilization, published by Liverpool University Press. Humour in Contemporary France Controversy, Consensus, and Contradictions JONATH A N ERVIN E Humour in Contemporary France Liverpool University Press First published 2019 by Liverpool University Press 4 Cambridge Street Liverpool L69 7ZU Copyright © 2019 Jonathan Ervine The right of Jonathan Ervine to be identified as the author of this book has been asserted by him in accordance with the Copyright, Designs and Patents Act 1988. All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. British Library Cataloguing-in-Publication data A British Library CIP record is available ISBN 978-1-78962-051-1 cased eISBN 978-1-78962-464-9 Typeset by Carnegie Book Production, Lancaster Contents Contents Acknowledgements vii Introduction. -

The Order of Encryption and Authentication for Protecting Communications (Or: How Secure Is SSL?)?
The Order of Encryption and Authentication for Protecting Communications (Or: How Secure is SSL?)? Hugo Krawczyk?? Abstract. We study the question of how to generically compose sym- metric encryption and authentication when building \secure channels" for the protection of communications over insecure networks. We show that any secure channels protocol designed to work with any combina- tion of secure encryption (against chosen plaintext attacks) and secure MAC must use the encrypt-then-authenticate method. We demonstrate this by showing that the other common methods of composing encryp- tion and authentication, including the authenticate-then-encrypt method used in SSL, are not generically secure. We show an example of an en- cryption function that provides (Shannon's) perfect secrecy but when combined with any MAC function under the authenticate-then-encrypt method yields a totally insecure protocol (for example, ¯nding passwords or credit card numbers transmitted under the protection of such protocol becomes an easy task for an active attacker). The same applies to the encrypt-and-authenticate method used in SSH. On the positive side we show that the authenticate-then-encrypt method is secure if the encryption method in use is either CBC mode (with an underlying secure block cipher) or a stream cipher (that xor the data with a random or pseudorandom pad). Thus, while we show the generic security of SSL to be broken, the current practical implementations of the protocol that use the above modes of encryption are safe. 1 Introduction The most widespread application of cryptography in the Internet these days is for implementing a secure channel between two end points and then exchanging information over that channel. -

Protocol Failure in the Escrowed Encryption Standard
Protocol Failure in the Escrowed Encryption Standard Matt Blaze AT&T Bell Laboratories [email protected] August 20, 1994 Abstract The proposal, called the Escrowed Encryption Stan- dard (EES) [NIST94], includes several unusual fea- The Escrowed Encryption Standard (EES) de¯nes tures that have been the subject of considerable de- a US Government family of cryptographic processors, bate and controversy. The EES cipher algorithm, popularly known as \Clipper" chips, intended to pro- called \Skipjack", is itself classi¯ed, and implemen- tect unclassi¯ed government and private-sector com- tations of the cipher are available to the private sec- munications and data. A basic feature of key setup be- tor only within tamper-resistant modules supplied by tween pairs of EES processors involves the exchange of government-approved vendors. Software implementa- a \Law Enforcement Access Field" (LEAF) that con- tions of the cipher will not be possible. Although Skip- tains an encrypted copy of the current session key. The jack, which was designed by the US National Security LEAF is intended to facilitate government access to Agency (NSA), was reviewed by a small panel of civil- the cleartext of data encrypted under the system. Sev- ian experts who were granted access to the algorithm, eral aspects of the design of the EES, which employs a the cipher cannot be subjected to the degree of civilian classi¯ed cipher algorithm and tamper-resistant hard- scrutiny ordinarily given to new encryption systems. ware, attempt to make it infeasible to deploy the sys- By far the most controversial aspect of the EES tem without transmitting the LEAF. -

Crypto Wars of the 1990S
Danielle Kehl, Andi Wilson, and Kevin Bankston DOOMED TO REPEAT HISTORY? LESSONS FROM THE CRYPTO WARS OF THE 1990S CYBERSECURITY June 2015 | INITIATIVE © 2015 NEW AMERICA This report carries a Creative Commons license, which permits non-commercial re-use of New America content when proper attribution is provided. This means you are free to copy, display and distribute New America’s work, or in- clude our content in derivative works, under the following conditions: ATTRIBUTION. NONCOMMERCIAL. SHARE ALIKE. You must clearly attribute the work You may not use this work for If you alter, transform, or build to New America, and provide a link commercial purposes without upon this work, you may distribute back to www.newamerica.org. explicit prior permission from the resulting work only under a New America. license identical to this one. For the full legal code of this Creative Commons license, please visit creativecommons.org. If you have any questions about citing or reusing New America content, please contact us. AUTHORS Danielle Kehl, Senior Policy Analyst, Open Technology Institute Andi Wilson, Program Associate, Open Technology Institute Kevin Bankston, Director, Open Technology Institute ABOUT THE OPEN TECHNOLOGY INSTITUTE ACKNOWLEDGEMENTS The Open Technology Institute at New America is committed to freedom The authors would like to thank and social justice in the digital age. To achieve these goals, it intervenes Hal Abelson, Steven Bellovin, Jerry in traditional policy debates, builds technology, and deploys tools with Berman, Matt Blaze, Alan David- communities. OTI brings together a unique mix of technologists, policy son, Joseph Hall, Lance Hoffman, experts, lawyers, community organizers, and urban planners to examine the Seth Schoen, and Danny Weitzner impacts of technology and policy on people, commerce, and communities. -

NSA's Efforts to Secure Private-Sector Telecommunications Infrastructure
Under the Radar: NSA’s Efforts to Secure Private-Sector Telecommunications Infrastructure Susan Landau* INTRODUCTION When Google discovered that intruders were accessing certain Gmail ac- counts and stealing intellectual property,1 the company turned to the National Security Agency (NSA) for help in securing its systems. For a company that had faced accusations of violating user privacy, to ask for help from the agency that had been wiretapping Americans without warrants appeared decidedly odd, and Google came under a great deal of criticism. Google had approached a number of federal agencies for help on its problem; press reports focused on the company’s approach to the NSA. Google’s was the sensible approach. Not only was NSA the sole government agency with the necessary expertise to aid the company after its systems had been exploited, it was also the right agency to be doing so. That seems especially ironic in light of the recent revelations by Edward Snowden over the extent of NSA surveillance, including, apparently, Google inter-data-center communications.2 The NSA has always had two functions: the well-known one of signals intelligence, known in the trade as SIGINT, and the lesser known one of communications security or COMSEC. The former became the subject of novels, histories of the agency, and legend. The latter has garnered much less attention. One example of the myriad one could pick is David Kahn’s seminal book on cryptography, The Codebreakers: The Comprehensive History of Secret Communication from Ancient Times to the Internet.3 It devotes fifty pages to NSA and SIGINT and only ten pages to NSA and COMSEC. -

Online Payment Fraud Prevention Using Cryptographic Algorithm TDES
S. Aishwarya et al, International Journal of Computer Science and Mobile Computing, Vol.4 Issue.4, April- 2015, pg. 317-323 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320–088X IJCSMC, Vol. 4, Issue. 4, April 2015, pg.317 – 323 RESEARCH ARTICLE Online Payment Fraud Prevention Using Cryptographic Algorithm TDES S. AISHWARYA1 K.DEVIKA RANI DHIVYA*2 III MSc (SS), Assistant Professor, Department of CA & SS, Department of CA & SS, Sri Krishna Arts and Science College, Sri Krishna Arts and Science College, Coimbatore, Tamil Nadu, Coimbatore, Tamil Nadu, India India ABSTRACT: Credit card is a small plastic card issued by a bank, building society, etc., allowing the holder to purchase goods or services on credit. Debit card is a card allowing the holder to transfer money electronically from their bank account when making a purchase. The use of credit cards and debit cards are increasing day by day. People are relying more on both cards nowadays than in the previous days. As credit cards and debit cards becomes the most popular mode of payment for both online as well as regular purchase, cases of fraud associated with it are also rising. In real life, fraudulent transactions are scattered with genuine transactions and simple pattern matching techniques are not often sufficient to detect those frauds accurately. In this project the process of Cryptography has been followed, it is one of the most important security technologies which used to secure the data transmission and the data itself. -

Ransomware Is Here: What You Can Do About It?
WHITEPAPER Ransomware is Here: What you can do about it? Overview Over the last few years, ransomware has emerged as one of the most devastating and costly attacks in the hacker arsenal. Cyber thieves are increasingly using this form of attack to target individuals, corporate entities and public sector organizations alike by holding your system or files for ransom. Unlike other forms of cyber theft that often involve stolen financial or healthcare information, ransomware cuts out the middleman. In cases where an attacker steals health or financial documents, they must sell them on to third parties to make money. As far as ransomware is concerned, the money comes directly from the victim. Ransomware is a quickly growing threat vector. According to the FBI’s Internet Crime Complaint center (IC3), infected users made complaints about ransomware 2,453 times in 2015—nearly double the figure for 2014. What’s more, these figures most likely represent only the tip of the iceberg, as many users pay their ransom without making a report to the authorities. A recent survey conducted by a Cyber Security Research Center at the University of Kent found that over 40% of those infected with CryptoLocker actually agreed to pay the ransom demanded, which is a big incentive for hackers to target more systems. Lastly, hackers are rapidly iterating both malware and distribution techniques. In early Q2 of 2016, a new variant of ransomware, known as CryptXXX, emerged on the scene. This program is packed in such a way that users and antivirus software may initially confuse it for a Windows DLL file. -
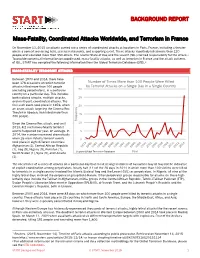
Mass-Fatality, Coordinated Attacks Worldwide, and Terrorism in France
BACKGROUND REPORT Mass-Fatality, Coordinated Attacks Worldwide, and Terrorism in France On November 13, 2015 assailants carried out a series of coordinated attacks at locations in Paris, France, including a theater where a concert was being held, several restaurants, and a sporting event. These attacks reportedly killed more than 120 people and wounded more than 350 others. The Islamic State of Iraq and the Levant (ISIL) claimed responsibility for the attack.1 To provide contextual information on coordinated, mass-fatality attacks, as well as terrorism in France and the attack patterns of ISIL, START has compiled the following information from the Global Terrorism Database (GTD).2 MASS-FATALITY TERRORIST ATTACKS Between 1970 and 2014, there have been 176 occasions on which terrorist Number of Times More than 100 People Were Killed attacks killed more than 100 people by Terrorist Attacks on a Single Day in a Single Country (excluding perpetrators), in a particular 30 country on a particular day. This includes both isolated attacks, multiple attacks, 25 and multi-part, coordinated attacks. The first such event took place in 1978, when 20 an arson attack targeting the Cinema Rex Theater in Abadan, Iran killed more than 15 400 people. Frequency Since the Cinema Rex attack, and until 10 2013, 4.2 such mass-fatality terrorist events happened per year, on average. In 5 2014, the number increased dramatically when 26 mass-fatality terrorist events 0 took place in eight different countries: Afghanistan (1), Central African Republic (1), Iraq (9), Nigeria (9), Pakistan (1), Source: Global Terrorism Database Year South Sudan (1), Syria (3), and Ukraine (1). -

Lethal Legacies: Illicit Firearms and Terrorism in France
169 Lethal legacies: Illicit firearms and terrorism in France FRANCE Nicolas Florquin and André DesmaraisI This chapter analyses the illicit firearms market in France, the ways in which terror- ist networks have been able to access firearms, and the national policies that have been developed to combat (terrorist access to) the illicit gun market. Particularly since 2015, France has by far been the European country most affected by terrorist attacks involving the use of firearms. The use of fully automatic rifles in the January and November 2015 Paris attacks took an unprecedented human toll, with 147 deaths in those events alone.1 In 2015 the French authorities made 424 terrorism- related arrests, compared to 238 in 2014 and 225 in 2013.2 The recent attacks have created a push to reform the country’s intelligence and secu- rity forces in order to adapt to, anticipate and better respond to these threats.3 The gov- ernment has also identified a series of measures to tackle the issue of illicitly held fire- arms: the Ministry of the Interior’s National Action Plan was launched on 13 November 2015, just hours before the attack on the Bataclan theatre started.4 Yet these efforts can only rely on limited information on and analysis of the extent and nature of the illicit arms market in France, owing principally to the fact that levels of gun violence in France were previously moderate, if not low by international standards. This study constitutes an unprecedented effort to present and analyse data and information on illicit firearms and their acquisition by terrorist actors in France. -

Mining Your Ps and Qs: Detection of Widespread Weak Keys in Network Devices
Mining Your Ps and Qs: Detection of Widespread Weak Keys in Network Devices † ‡ ‡ ‡ Nadia Heninger ∗ Zakir Durumeric ∗ Eric Wustrow J. Alex Halderman † University of California, San Diego ‡ The University of Michigan [email protected] {zakir, ewust, jhalderm}@umich.edu Abstract expect that today’s widely used operating systems and RSA and DSA can fail catastrophically when used with server software generate random numbers securely. In this malfunctioning random number generators, but the extent paper, we test that proposition empirically by examining to which these problems arise in practice has never been the public keys in use on the Internet. comprehensively studied at Internet scale. We perform The first component of our study is the most compre- the largest ever network survey of TLS and SSH servers hensive Internet-wide survey to date of two of the most and present evidence that vulnerable keys are surprisingly important cryptographic protocols, TLS and SSH (Sec- widespread. We find that 0.75% of TLS certificates share tion 3.1). By scanning the public IPv4 address space, keys due to insufficient entropy during key generation, we collected 5.8 million unique TLS certificates from and we suspect that another 1.70% come from the same 12.8 million hosts and 6.2 million unique SSH host keys faulty implementations and may be susceptible to com- from 10.2 million hosts. This is 67% more TLS hosts promise. Even more alarmingly, we are able to obtain than the latest released EFF SSL Observatory dataset [18]. RSA private keys for 0.50% of TLS hosts and 0.03% of Our techniques take less than 24 hours to scan the entire SSH hosts, because their public keys shared nontrivial address space for listening hosts and less than 96 hours common factors due to entropy problems, and DSA pri- to retrieve keys from them. -

Battle of the Clipper Chip - the New York Times
Battle of the Clipper Chip - The New York Times https://www.nytimes.com/1994/06/12/magazine/battle-of-the-clipp... https://nyti.ms/298zenN Battle of the Clipper Chip By Steven Levy June 12, 1994 See the article in its original context from June 12, 1994, Section 6, Page 46 Buy Reprints VIEW ON TIMESMACHINE TimesMachine is an exclusive benefit for home delivery and digital subscribers. About the Archive This is a digitized version of an article from The Times’s print archive, before the start of online publication in 1996. To preserve these articles as they originally appeared, The Times does not alter, edit or update them. Occasionally the digitization process introduces transcription errors or other problems; we are continuing to work to improve these archived versions. On a sunny spring day in Mountain View, Calif., 50 angry activists are plotting against the United States Government. They may not look subversive sitting around a conference table dressed in T-shirts and jeans and eating burritos, but they are self-proclaimed saboteurs. They are the Cypherpunks, a loose confederation of computer hackers, hardware engineers and high-tech rabble-rousers. The precise object of their rage is the Clipper chip, offically known as the MYK-78 and not much bigger than a tooth. Just another tiny square of plastic covering a silicon thicket. A computer chip, from the outside indistinguishable from thousands of others. It seems 1 of 19 11/29/20, 6:16 PM Battle of the Clipper Chip - The New York Times https://www.nytimes.com/1994/06/12/magazine/battle-of-the-clipp..