Behavior-Based Spyware Detection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Administrator's Guide
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release notes, and/or the latest version of the applicable documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/scanmail-for-microsoft- exchange.aspx Trend Micro, the Trend Micro t-ball logo, Apex Central, eManager, and ScanMail are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2020. Trend Micro Incorporated. All rights reserved. Document Part No.: SMEM149028/200709 Release Date: November 2020 Protected by U.S. Patent No.: 5,951,698 This documentation introduces the main features of the product and/or provides installation instructions for a production environment. Read through the documentation before installing or using the product. Detailed information about how to use specific features within the product may be available at the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Evaluate this documentation on the following site: https://www.trendmicro.com/download/documentation/rating.asp Privacy and Personal Data Collection Disclosure Certain features available in Trend Micro products collect and send feedback regarding product usage and detection information to Trend Micro. Some of this data is considered personal in certain jurisdictions and under certain regulations. -

Clearing Commonly Used Browser's Internet Cache Desktops
Clearing Commonly Used Browser’s Internet Cache Clearing Commonly Used Browser’s Internet Cache For information on how to clear the cache of commonly used internet browsers, please see below. NOTE: If your browser is not listed, please refer to the documentation that came with your device or the browser software on how to clear its cache. REMINDER: To protect your privacy and prevent unauthorized use of your System ID, 1) sign out of the Self-Service application, 2) clear the browser’s cache, and 3) close all web browser windows. Desktops Internet Explorer 7 1. From the Tools menu, select Internet Options. 2. Under "Browsing history", click Delete. 3. To delete your cache, click Delete files. 4. Click Close, and then click OK to exit. 5. After the cache is cleared, click the X to close the browser window and confirm ALL browser windows are closed. Internet Explorer 9, 10, and 11 1. Select Tools (via the Gear icon) 2. Select Safety 3. Select Delete Browsing History… NOTE: You can also access this menu by holding Ctrl + Shift + Delete 4. Make sure to uncheck Preserve Favorites websites data and check both Temporary Internet Files and Cookies then click Delete. Microsoft Edge 1. Click the Hub icon. 2. Click the History icon. 3. Click the link labeled Clear all History. 4. Check the boxes for each item you want to clear. 5. Click the Clear button. The message “All Clear!” will appear. Android To clear cache: 1. Start your browser. 2. Tap Menu, and then tap More. 3. Select Settings. -

Taskstream Technical & System Faqs
Taskstream Technical & System FAQs 71 WEST 23RD STREET, NEW YORK, NY 10010 · T 1.800.311.5656 · e [email protected] Taskstream FAQs Taskstream FAQs Click the links in each question or description to navigate to the answer: System Requirements FAQs . What Internet browsers can I use to access Taskstream? . Can I use Taskstream on a Mac or a PC? on a desktop or laptop computer? . Does Taskstream work on iPad, iPhone or Android-based devices? . Do I need additional plugins or add-ons to use Taskstream? . Can I access Taskstream offline? . Does Taskstream require JavaScript to be enabled? . Does Taskstream require cookies to be enabled? . Does Taskstream use pop-ups? . How can I import and export data within Taskstream? Technical FAQs . Can I have Taskstream open in more than one window at a time? . Is Taskstream's site accessible to users with disabilities? . What is a Comma Separated Value (CSV) file? . How do I print my work? . How do I format my text? . How do I add special characters, such as math symbols or special punctuation, to my text? . What is WebMarker File Markup? . What is Turnitin® Originality Reporting? . Can I change the size of the Taskstream text/fonts? Troubleshooting . When I click on a button nothing occurs. Some of the features within the Taskstream site are missing. When I try to download/view a file attachment, nothing happens. I am not receiving emails from Taskstream. I uploaded a file on my Mac, but the attached file does not open. My file is too large to upload. Taskstream is reporting that I have entered unsafe text. -

(12) United States Patent (10) Patent No.: US 7,921.461 B1 Golchikov Et Al
USOO7921461B1 (12) United States Patent (10) Patent No.: US 7,921.461 B1 Golchikov et al. (45) Date of Patent: Apr. 5, 2011 (54) SYSTEMAND METHOD FOR ROOTKIT S.8. 53 A. : SS Eyrdseter . et. al.. ............... 7 1. DETECTION AND CURE 2004/O181561 A1 9, 2004 Knox et al. 2005, 0021994 A1 1/2005 Barton et al. (75) Inventors: Andrey V. Golchikov, Moscow (RU); 2005/0278788 A1 12/2005. Jindal et al. Andrey V. Sobko, Moscow (RU) 2006/0031673 A1 2/2006 Becket al. .................... T13, 164 2006.0053270 A1* 3, 2006 Dunn et al. 712/13 (73) Assignee: Kaspersky Lab, ZAO, Moscow (RU) 2.99. A. : 29: RSU ca.tal. ... 2. (*) Notice: Subject to any disclaimer, the term of this 2008.0034429 A1 ck 2/2008 Schneider ....................... T26/23 patent is extended or adjusted under 35 OTHER PUBLICATIONS U.S.C. 154(b) by 1115 days. Simon Baker et al. "Checking Microsoft Windows(R) Systems for (21) Appl. No.: 11/623,364 Signs of Compromise', Oct. 28, 2005, version 1.3.4, pp. 1-18.* y x- - - 9 * cited by examiner (22) Filed: Jan. 16, 2007 Primary Examiner — Farid Homayoumehr (51) Int. Cl. Assistant Examiner — Michael Guirguis ge. 5.b4. 3:08: (74) Attorney, Agent, or Firm — Bardmesser Law Group GSB 23/00 (2006.01) (57) ABSTRACT (52) U.S. Cl. ................... 726/23: 726/24; 726/25; 713/2 ASVstem. method and computer program product for SVStem (58) Field of Classification Search .................... 726/26, ystem, computer program pr ySt. 726/23 25: 713/2 for detecting a rootkit on a computer having an operating S lication file f let h his s system, including a native application in ring 0 which, when ee appl1cauon Ille Ior complete searcn n1Story. -

Patent Application Publication (10) Pub. No.: US 2013/0091418 A1 Gonzalez (43) Pub
US 2013 009 1418A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0091418 A1 Gonzalez (43) Pub. Date: Apr. 11, 2013 (54) CROSS-BROWSER TOOLBAR AND METHOD Publication Classification THEREOF (51) Int. Cl. (71) Applicant: Visicom Media Inc., Brossard (CA) G06F 7/2 (2006.01) (52) U.S. Cl. (72) Inventor: Miguel Enrique Cepero Gonzalez, CPC .................................... G06F 17/218 (2013.01) Brossard (CA) USPC .......................................................... 71.5/234 (57) ABSTRACT (73) Assignee: VISICOMMEDIA INC., Brossard A tool configured to build a cross-browser toolbar is pro (CA) vided. The tool comprises a processor; and a memory coupled to the processor and configured to store at least instructions for execution of a wizard program by the processor, wherein (21) Appl. No.: 13/690,236 the wizard program causes to: receive an input identifying at least user interface elements and event handlers respective of the user interface elements, wherein the input further identi (22) Filed: Nov.30, 2012 fies at least two different types of a web browser on which the toolbar can be executed; generate respective of the received O O input a toolbar render object, a script file, and at least one Related U.S. Application Data toolbar library for each type of web browser; and compile the (63) Continuation of application No. 12/270,421, filed on toolbar render object, the script file, and the least one toolbar Nov. 13, 2008, now Pat. No. 8,341,608. library into an installer file. 120-1 Installer Web File BrOWSer TOOlbar Builder installer File TOOlbar BrOWSer Libraries Patent Application Publication Apr. -

Groove Gfs Browser Helper Grooveshellextensions.Dll
Groove gfs browser helper grooveshellextensions.dll Continue Equipment Info maakt gebruik van biscuits Equipment Information onderdeel van DPG Media. Onze sites en applications gebruiken cookies, JavaScript en vergelijkbare technologie onder andere om je een optimale gebruikerservaring te bieden. Ook kunnen we hierdoor het gedrag van bezoekers vastleggen en analyseren, en deze informatie toevoegen aan bezoekersprofielen. Biscuits kunnen worden gebruikt om Op Equipment Advertising information those Tonen en artikelen aan te bevelen die aansluiten op je interesses. Ook derden kunnen je internetgedrag volgen, zoals bijvoorbeeld het geval - is a bij built-in video van YouTube. Biscuits kunnen gebruikt worden om op sites van derden relevantenties te tonen. Dankzij cookies van derde partijen kun je daarnaast informatie delen via social media, zoals Twitter en Facebook. Meer informatie hierover vind je op hardware.info/extra/cookies. Om pagina's op Hardware Info te kunnen bekijken, moet je de cookies accepteren door op 'Ja, ik accepteer cookies' te klikken. The original GrooveShellExtensions.dll file is a software component of Microsoft Office 2007 at Microsoft. GrooveShellExtensions.dll is an addition to Microsoft Browser Helper Object (BHO) for Microsoft Internet Explorer. Known as Groove Folder Sync, this allowed Office 2007 users to access Groove files in the IE web browser window and helped synchronize updated files. It included a contextual menu. His location was C: Files of the Microsoft Office-Office12-GrooveShellExtensions.dll. No reference to Office14 or above can be found, indicating that it has not been installed since Office 2010 or later. The Groove in Office 2007 product allows users to collaborate by sharing workspaces synchronized through relay servers with any other user they're invited to join the workspace. -

ERNW Newsletter 31 / June 2010 Secure Configuration of Microsoft
ERNW Newsletter 31 / June 2010 Dear Partners, dear Colleagues, Welcome to the 31th edition of the ERNW Newsletter with the title: Secure Configuration of Microsoft Internet Explorer, Version 8 Version 1.0, 11th of June 2010 By: Enno Rey ([email protected]) Christopher Werny ([email protected]) Oliver Röschke ([email protected]) Abstract This newsletter evaluates configuration options, reflecting security and possible usability impact, incorporating typical large scale enterprise usage of browser based content. The evaluation was done for a globally operating enterprise. Note We provide some supporting files, namely: some regfiles containing the settings we recommended for the given environment. Use at your own risk and only if you fully understand the impact! an XLS with the recommended settings, based on the Microsoft XLS doc on GPO settings. miscellaneous stuff, e.g. an XLS with some documentation on potentially needed CLSIDs. A ZIP file with these can be found at http://www.ernw.de/download/ernw_nl_31_ie8config_supporting_docs.zip Disclaimer: the recommended settings are deployed in a sufficiently large global network. So they "work in production". Still, your mileage might vary. Please use the stuff cautiously. Any use is at your own risk. Definition – Umsetzung – Kontrolle 1 1 INTRODUCTION ............................................................................................. 5 1.1 Project Goals ............................................................................................................ 5 1.2 Technical goals ........................................................................................................ -

Building Anti-Phishing Browser Plug-Ins: an Experience Report
Building Anti-Phishing Browser Plug-Ins: An Experience Report Thomas Raffetseder, Engin Kirda, and Christopher Kruegel Secure Systems Lab, Technical University of Vienna {tr,ek,chris}@seclab.tuwien.ac.at Abstract stolen. These credentials are typically used to login into the online banking web site and to transfer money to the at- Phishing is an online identity theft that aims to steal tacker’s bank account. Although phishing is a simple social sensitive information such as user names, passwords, and engineeringattack, it has provento be surprisingly effective. credit card numbers. Although phishing is a simple social Hence, the number of phishing scams is continuing to grow, engineering attack, it has proven to be surprisingly effec- and the costs of the resulting damages is increasing. For tive. Hence, the number of phishing scams is continuing example, the Anti-Phishing Working Group received over to grow, and the costs of the resulting damages is increas- 35,000 unique phishing reports in November 2006, com- ing. Researchers as well as the IT industry have identified pared to around 7,000 in November of the year before [2]. the urgent need for anti-phishing solutions and recently, a Figure 1 shows a phishing email that targets the cus- number of solutions to mitigate phishing attacks have been tomers of a U.S. bank. The attackers have imitated the look proposed. Several of these approaches are browser plug- and feel of the Bank of America online banking web site ins. with the aim of fooling users into believing that the mail In 2005, we implemented a Firefox anti-phishing is authentic. -

Security Analysis of Browser Extension Concepts
Saarland University Faculty of Natural Sciences and Technology I Department of Computer Science Bachelor's thesis Security Analysis of Browser Extension Concepts A comparison of Internet Explorer 9, Safari 5, Firefox 8, and Chrome 14 submitted by Karsten Knuth submitted January 14, 2012 Supervisor Prof. Dr. Michael Backes Advisors Raphael Reischuk Sebastian Gerling Reviewers Prof. Dr. Michael Backes Dr. Matteo Maffei Statement in Lieu of an Oath I hereby confirm that I have written this thesis on my own and that I have not used any other media or materials than the ones referred to in this thesis. Saarbr¨ucken, January 14, 2012 Karsten Knuth Declaration of Consent I agree to make both versions of my thesis (with a passing grade) accessible to the public by having them added to the library of the Computer Science Department. Saarbr¨ucken, January 14, 2012 Karsten Knuth Acknowledgments First of all, I thank Professor Dr. Michael Backes for giving me the chance to write my bachelor's thesis at the Information Security & Cryptography chair. During the making of this thesis I have gotten a deeper look in a topic which I hope to be given the chance to follow up in my upcoming academic career. Furthermore, I thank my advisors Raphael Reischuk, Sebastian Gerling, and Philipp von Styp-Rekowsky for supporting me with words and deeds during the making of this thesis. In particular, I thank the first two for bearing with me since the release of my topic. My thanks also go to Lara Schneider and Michael Zeidler for offering me helpful advice. -

Protecting Browsers from Extension Vulnerabilities
Protecting Browsers from Extension Vulnerabilities Adam Barth Adrienne Porter Felt Prateek Saxena Aaron Boodman Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2009-185 http://www.eecs.berkeley.edu/Pubs/TechRpts/2009/EECS-2009-185.html December 18, 2009 Copyright © 2009, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Acknowledgement We would like to thank Nick Baum, Erik Kay, Collin Jackson, Matt Perry, Dawn Song, David Wagner, and the Google Chrome Team. This work is partially supported by the Air Force Office of Scientific Research under MURI Grant No. 22178970-4170. Protecting Browsers from Extension Vulnerabilities Adam Barth, Adrienne Porter Felt, Prateek Saxena Aaron Boodman University of California, Berkeley Google, Inc. fabarth, afelt, [email protected] [email protected] Abstract browser’s full privileges. If an attacker can exploit an ex- tension vulnerability, the attacker can usurp the extension’s Browser extensions are remarkably popular, with one in broad privileges and install malware on the user’s machine. three Firefox users running at least one extension. Although At this year’s DEFCON, Liverani and Freeman presented well-intentioned, extension developers are often not security attacks against a number of popular Firefox extensions [23]. -

Netiq Securelogin 8.5 Service Pack 3 Release Notes September 2017
NetIQ SecureLogin 8.5 Service Pack 3 Release Notes September 2017 NetIQ SecureLogin 8.5 Service Pack 3 (SP3) enhances the product capability and resolves several previous issues. Many of these improvements were made in direct response to suggestions from our customers. We thank you for your time and valuable input. We hope you continue to help us ensure that our products meet all your needs. You can post feedback in the NetIQ SecureLogin forum on NetIQ Communities, our online community that also includes product information, blogs, and links to helpful resources. The documentation for this product and the latest Release Notes are available on the NetIQ website in HTML and PDF formats on a page that does not require you to log in. If you have suggestions for documentation improvements, click comment on this topic at the bottom of any page in the HTML version of the documentation posted at the NetIQ SecureLogin documentation page. To download this product, see the NetIQ Downloads website. Section 1, “What’s New?,” on page 1 Section 2, “System Requirements,” on page 3 Section 3, “Installing or Upgrading,” on page 3 Section 4, “Known Issues,” on page 3 Section 5, “Legal Notices,” on page 5 1 What’s New? This release includes the following: Section 1.1, “Software Fixes,” on page 1 1.1 Software Fixes This release includes the following software fixes: Section 1.1.1, “Smart Card Pin Auto-fill Does Not Work For Second Application,” on page 2 Section 1.1.2, “Performance Issue During Smart Card Pin Auto-fill While Using .Net Applications,” -
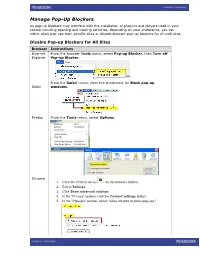
Manage Pop-Up Blockers
Manage Pop-Up Blockers As pop-up blockers may interfere with the installation of plug-ins and players used in your course including opening and viewing activities, depending on your preference, you can either allow pop-ups from specific sites or disable browser pop-up blockers for all web sites. Disable Pop-up Blockers for All Sites Browser Instructions Internet From the browser Tools menu, select Pop-up Blocker, then Turn off Explorer Pop-up Blocker. From the Safari menu, clear the checkmark for Block pop-up Safari windows. Firefox From the Tools menu, select Options Chrome 1. Click the Chrome menu on the browser toolbar. 2. Select Settings. 3. Click Show advanced settings. 4. in the "Privacy" section, click the Content settings button. 5. In the "Pop-ups" section, select "Allow all sites to show pop-ups." Allow Pop-ups from Specific Sites (Exceptions) Browser Instructions When you see the yellow “Information Bar” at the top of the web page Internet about a pop-up being blocked, click the bar and select Always allow Explorer pop-ups from this site, and click Yes to confirm. –or– 1. From the browser Tools menu, select Pop-up Blocker, then Pop-up Blocker Settings. 2. Add the following as allowed sites: • *.pearsoned.com, • *.pearsoncmg.com • *.mylanguagelabs.com , • *mylabs.px.pearsoned.com, • *pearsonvt.wimba.com 3. Click Close. Safari In Safari you can either enable or disable the pop-up blocker. There is no per-site control. See next section for details on how to disable pop-up blocker. Firefox 1.From the Tools menu, select Options 2.