Model Based Fuzzing of the WPA3 Dragonfly
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Driver Download Instructions
Download Instructions Foxconn Tbga01 Driver 8/13/2015 For Direct driver download: http://www.semantic.gs/foxconn_tbga01_driver_download#secure_download Important Notice: Foxconn Tbga01 often causes problems with other unrelated drivers, practically corrupting them and making the PC and internet connection slower. When updating Foxconn Tbga01 it is best to check these drivers and have them also updated. Examples for Foxconn Tbga01 corrupting other drivers are abundant. Here is a typical scenario: Most Common Driver Constellation Found: Scan performed on 8/12/2015, Computer: Sony SVE15136CNS Outdated or Corrupted drivers:9/21 Updated Device/Driver Status Status Description By Scanner Motherboards Synaptics Synaptics SMBus Driver Corrupted By Foxconn Tbga01 Mice And Touchpads Logitech Logitech USB First/Pilot Mouse+ Corrupted By Foxconn Tbga01 Microsoft HID mouse Corrupted By Foxconn Tbga01 Logitech HID-compliant mouse Corrupted By Foxconn Tbga01 Usb Devices Cypress USB Storage Up To Date and Functioning Logitech Logitech Microphone (Fusion) Corrupted By Foxconn Tbga01 Sound Cards And Media Devices NVIDIA NVIDIA GeForce GTX 675M Up To Date and Functioning Broadcom Audio Bluetooth. Up To Date and Functioning Network Cards Ralink 802.11n Wireless LAN Card Corrupted By Foxconn Tbga01 Keyboards Microsoft HID Keyboard Up To Date and Functioning Hard Disk Controller Intel(R) ICH10D/DO SATA AHCI Controller Up To Date and Functioning Others NEC Generic CardBus-kontroller Outdated Research In Motion BlackBerry Outdated Intel Port racine express PCI -
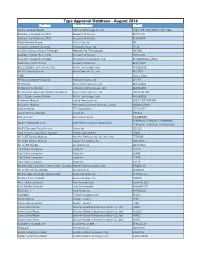
Type Approval Database - August 2014 Product Manufacturer Model Techno Mobile Phones Techno Technology Co
Type Approval Database - August 2014 Product Manufacturer Model Techno Mobile Phones Techno Technology Co. Ltd T331, T25, T501,T607, TV65, T28 Blackberry Smartphone 9520 Research In Motion RCP51UW Blackberry smartphone 9700 Research In Motion RCM71UW Fixed Wireless Phone I-Sirius Pte Ltd NA Personal Computer (Laptop) Panasonic Corp., Ltd CF-31 Unified Communications Exchange Network Eqt Technologies UX2000 BlackBerry SmartPhone 9700 Research In Motion RCN71UW Broadcom Bluetooth Module Broadcom Corporation, USA BCM92070MD_LENO Black Berry Smart Phone Research In Motion REM71UW 802.11a/b/g/n 2TR Combo Card Ralink Technology Corp RT3592BC8 WLAN Combo Module Micro-Star Int'l Co., Ltd MS-3871 PABX Aastra 2065 Personal Computer (Laptop) Panasonic Corp., Ltd CF-19T RF Module Barun Electronics Co., Ltd BM-LDS201 RF Remote Controller OHSUNG Electronics Co. Ltd. AKB732955 Blueconnect Handsfree Telephone Module Barun Electronics Co., Ltd CB2-BLUE11M 802.11b/g/n Combo Module Ralink Technology Corp RT5390BC8 Bluetooth Module Alpine Electronics Inc IAM2.1 BT PWB EU3 Bluetooth Module Panasonic Customer Services, Europe UGNZA/UGNZ4 Mobile Phone ZTE Corporation ZTE-G S217 Canon Wireless Module Canon Inc. WM223 WiFi Module LG Electronics Inc. LGSWF41 3160HMW, 3160NGW, 7260HMW, WLAN + Bluetooth Card Intel Mobile Communications SAS 7260NGW, 7260SDW, 6235ANNGW WLAN Compact Photo Printer Canon Inc. CD1112 Free To Air Terrestrial Set Top Box Vestel Electronik A.S T9300 Wi-Fi /BT Combo Module Hon Hai Precision Ind. Co. Ltd, India T77H506 Wi-Fi /BT Combo Module -

Arguments for USPTO Error in Granting U.S. Patent 9,904,924 to Square, Inc
Arguments for USPTO Error in Granting U.S. Patent 9,904,924 to Square, Inc. Umar Ahmed Badami Annabel Guo [email protected] [email protected] Samantha Jackman Kathryn Ng Sharon Samuel [email protected] [email protected] [email protected] Brandon Theiss* [email protected] New Jersey’s Governor’s School of Engineering and Technology July 24, 2020 *Corresponding Author Abstract—The United States Patent and Trademark Office how their invention works. When the patent expires 2, the (USPTO) erred in granting U.S. Patent 9,904,924 to Square Inc. public is permitted to make, use, or sell the invention without U.S. Patent 9,904,924 claims a system for the transfer of funds the inventor’s permission. from a sender to a recipient via email. However, this system was disclosed prior to the U.S. Patent 9,904,924’s effective filing For an inventor to patent their invention, there are some date of March 15, 2013. Claims 1 and 9 were disclosed by U.S. requirements that must be fulfilled as per the U.S. Code. One 8,762,272 and U.S. Patent 8,725,635 while claim 20 was taught by requirement for patentability, as stated under 35 U.S.C. § 101 a combination of U.S. Pat. App. Publication 2009/0006233, U.S. Patent 10,395,223, and U.S. Patent 10,515,345, thereby rendering is that the invention must be useful, defined as having “a at least one of the claims of U.S. Patent 9,904,924 invalid. -

Application Number
Intellectual Property India· Application Number. 4302WHE/2014 0 Home (h ttp://i pin di a.gov. in/index. htm) Contact Us (hrtp :/I i pi ndia.gov. in/ contact-us. h tm) Feed back (http:/ I i pi nd ia .gov. in/feedback. h tm) FAQ s (http:// i pi nd i a .gov. i n/faq-patents .h tm) Si tem a p (http://i pi nd i a .gov. i n/sitemap. htm) ., v ~~i&l lnck; ,, P ..1renr Advat<r.~:d. Se.1rch System (http:/ I i pi ndia. gov. in/index. htm) (http:/ /ipin dia .gov.in/index.h t Application Number: 4302/CHE/2014 Bib/agraphic Data Complete Specification Application Status Invention Title PHARMACEUTICAL COMPOSITIONS COMPRISING GERANIAL AS ATPASE INHIBITORS "" Publication Number 27/2016 Publication Date 2016/07/01 Publication Type INA Application Number 4302/CHE/2014 Application Filing Date 2014/09/03 Priority Number Priority Country Priority Date Field Of Invention (F/11) PHARMACEUTICALS Classification (IPC) A61 K-31 /00 Inventor Name Address Country Nationality V SAISHA Department of Biotechnology, BMSCE, PB No. 1908, Bull Temple Road, Bangalore · 560019, Karnataka (India) IN IN http://i pi ndi aservi ces .g ov.1 nlpubli csearchlneltvpublicsearchlpatent_detail.php?UC ID= SGF6l.J Di1JN zJhSjJ KYkhZM jJGaF dzUG 1mSW1 NZ2F TaWCZ01\f\JRzkxRjF GST 0%30 L"'S~·il/5·31~2'0~13 ' lir~iiA~~~~=:"~ l~~&~f&;~g:~c,~;~(i) I #GS/4, N~G,A;Sf.\Em H,t.;Ciii) lNOfAN g, f>c, G. JYOf:IHI, #,3'6/:t7~B-.f0l Ofv1~RSAR®Vf4:AAI PAPW ·~OFr~G~; [email protected];Afi<APlaM•M#lN~R()AP, ~SklSM'ANAGWE>l, ·BA'NGJl;llQRE-560004'• IJIJDIAI'f . -

Artificial Intelligence, Economics, and Industrial Organization Hal Varian1
Artificial Intelligence, Economics, and Industrial Organization Hal Varian1 Nov 2017 Revised June 2018 Introduction Machine learning overview What can machine learning do? What factors are scarce? Important characteristics of data Data ownership and data access Decreasing marginal returns Structure of ML-using industries Machine learning and vertical integration Firm size and boundaries Pricing Price differentiation Returns to scale Supply side returns to scale Demand side returns to scale Learning by doing Algorithmic collusion Structure of ML-provision industries Pricing of ML services Policy questions Security Privacy 1 I am a full time employee of Google, LLC, a private company. I am also an emeritus professor at UC Berkeley. Carl Shapiro and I started drafting this chapter with the goal of producing a joint work. Unfortunately, Carl became very busy and had to drop out of the project. I am grateful to him for the time he was able to put in. I also would like to thank Judy Chevalier and the participants of the NBER Economics of AI conference in Toronto, Fall 2017. Explanations Summary References Introduction Machine learning (ML) and artificial intelligence (AI) have been around for many years. However, in the last 5 years, remarkable progress has been made using multilayered neural networks in diverse areas such as image recognition, speech recognition, and machine translation. AI is a general purpose technology that is likely to impact many industries. In this chapter I consider how machine learning availability might affect the industrial organization of both firms that provide AI services and industries that adopt AI technology. My intent is not to provide an extensive overview of this rapidly-evolving area, but instead to provide a short summary of some of the forces at work and to describe some possible areas for future research. -

Data Analytics: the Future of Legal JEREMIAH CHAN1
International In-house Counsel Journal Vol. 9, No. 34, Winter 2016, 1 Data Analytics: The Future of Legal JEREMIAH CHAN1 Legal Director, Google Inc., USA & JAY YONAMINE Senior Data Scientist, Google Inc., USA & NIGEL HSU Head of Patent Operations, Verily Life Sciences LLC, USA INTRODUCTION During the 2002 season of Major League Baseball (MLB), the Oakland Athletics and New York Yankees both won an astounding 103 games, a feat only topped three times by any team in the last 24 years. Despite identical records, the New York Yankees payroll on opening day was $125,928,583 compared to only $39,679,746 for the Oakland Athletics. On a per win basis, the Oakland Athletics paid $385,240 per win compared to the New York Yankee’s $1,222,608. The New York Yankees were not an outlier. All other MLB teams (excluding Oakland) paid on average $853,252 per win in 2002. So how were the Oakland Athletics able to generate wins with over two to three times the cost efficiency of other teams in the league? By now, the answer has been well documented by Michael Lewis in the book and subsequent movie Moneyball, in which Lewis recounts how Oakland Athletics’ General Manager Billy Beane replaced traditional approaches to scouting and roster management with a rigorous use of data and statistical models. This is often referred to as “data analytics.” The quest for increased efficiency is certainly not unique to MLB. Be it a widget factory, technology company, or legal department, the desire to maximize the quality of outcomes while maintaining or reducing costs is ubiquitous. -

Improving Google Patents with European Patent Office Patents And
Improving Google Patents with European Patent Office patents and the Prior Art Finder Tuesday, August 14, 2012 at 10:23 AM ET Posted by Jon Orwant, Engineering Manager Cross-posted from the Google Research blog At Google, we're constantly trying to make important collections of information more useful to the world. Since 2006, we’ve let people discover, search, and read United States patents online. Starting this week, you can do the same for the millions of ideas that have been submitted to the European Patent Office, such as this one. [An example Moisture-tight edible film dispenser and method thereof EP 1692064 B1Abstract (text from WO2005051822A1]. Typically, patents are granted only if an invention is new and not obvious. To explain why an invention is new, inventors will usually cite prior art such as earlier patent applications or journal articles. Determining the novelty of a patent can be difficult, requiring a laborious search through many sources, and so we’ve built a Prior Art Finder to make this process easier. With a single click, it searches multiple sources for related content that existed at the time the patent was filed. From googlepublicpolicy.blogspot.com/2012/08/improving-google-patents-with-european.html 21 April 2013 Patent pages now feature a “Find prior art” button that instantly pulls together information relevant to the patent application. The Prior Art Finder identifies key phrases from the text of the patent, combines them into a search query, and displays relevant results from Google Patents, Google Scholar, Google Books, and the rest of the web. -

Aspire 4736G/4736Z Series Service Guide
Aspire 4736G/4736Z Series Service Guide Service guide files and updates are available on the ACER/CSD web; for more information, please refer to http://csd.acer.com.tw PRINTED IN TAIWAN Revision History Please refer to the table below for the updates made to this service guide. Date Chapter Updates II Copyright Copyright © 2009 by Acer Incorporated. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written permission of Acer Incorporated. Disclaimer The information in this guide is subject to change without notice. Acer Incorporated makes no representations or warranties, either expressed or implied, with respect to the contents hereof and specifically disclaims any warranties of merchantability or fitness for any particular purpose. Any Acer Incorporated software described in this manual is sold or licensed as is. Should the programs prove defective following their purchase, the buyer (and not Acer Incorporated, its distributor, or its dealer) assumes the entire cost of all necessary servicing, repair, and any incidental or consequential damages resulting from any defect in the software. Acer is a registered trademark of Acer Corporation. Intel is a registered trademark of Intel Corporation. Pentium and Pentium II/III are trademarks of Intel Corporation. Other brand and product names are trademarks and/or registered trademarks of their respective holders. III Conventions The following conventions are used in this manual: SCREEN MESSAGES Denotes actual messages that appear on screen. -

Google Patents
USPTO University Outreach: Patent Searching and Search Resources Presenter Date Objectives • Where can you search? • What are the benefits of searching? • When should you search? and most importantly: • How do you search using USPTO search tools? • What are some important strategies? Overview of IP: Why Get a Patent? • A patent can be – Used to gain entry to a market – Used to exclude others from a market – Used as a marketing tool to promote unique aspects of a product – Sold or licensed, like other property What is patentable? compositi on Manufact NEW, USEFUL, Machine ure NONOBVIOUS, ENABLED & CLEARLY DESCRIBED Method/ Improvements or process thereof Types of Patents • Utility - New and useful process, machine, article of manufacture, or composition of matter, or any new and useful improvement thereof Term – 20 years from earliest effective filing date • Design - Any new, original and ornamental design Term - 15 years from issue date • Plant - Whoever invents or discovers and asexually produces any distinct and new variety of plant... Term – 20 years from earliest effective filing date Overview of IP: What is a Patent? • A Property Right – Right to exclude others from making, using, selling, offering for sale or importing the claimed invention – Limited term – Territorial: protection only in territory that granted patent; NO world-wide patent • Government grants the property right in exchange for the disclosure of the invention What Type of Application? • Provisional – abandoned after one year, no claims required, written disclosure must meet same requirements as non- provisional, not allowed for design. • Non-Provisional - claims required, written disclosure must meet requirements of 35 USC 112(a). -

Machine Learning for Marketers
Machine Learning for Marketers A COMPREHENSIVE GUIDE TO MACHINE LEARNING CONTENTS pg 3 Introduction pg 4 CH 1 The Basics of Machine Learning pg 9 CH. 2 Supervised vs Unsupervised Learning and Other Essential Jargon pg 13 CH. 3 What Marketers can Accomplish with Machine Learning pg 18 CH. 4 Successful Machine Learning Use Cases pg 26 CH. 5 How Machine Learning Guides SEO pg 30 CH. 6 Chatbots: The Machine Learning you are Already Interacting with pg 36 CH. 7 How to Set Up a Chatbot pg 45 CH. 8 How Marketers Can Get Started with Machine Learning pg 58 CH. 9 Most Effective Machine Learning Models pg 65 CH. 10 How to Deploy Models Online pg 72 CH. 11 How Data Scientists Take Modeling to the Next Level pg 79 CH. 12 Common Problems with Machine Learning pg 84 CH. 13 Machine Learning Quick Start INTRODUCTION Machine learning is a term thrown around in technol- ogy circles with an ever-increasing intensity. Major technology companies have attached themselves to this buzzword to receive capital investments, and every major technology company is pushing its even shinier parentartificial intelligence (AI). The reality is that Machine Learning as a concept is as days that only lives and breathes data science? We cre- old as computing itself. As early as 1950, Alan Turing was ated this guide for the marketers among us whom we asking the question, “Can computers think?” In 1969, know and love by giving them simpler tools that don’t Arthur Samuel helped define machine learning specifi- require coding for machine learning. -

Linux from Scratch 版本 R11.0-36-中⽂翻译版 发布于 2021 年 9 ⽉ 21 ⽇
Linux From Scratch 版本 r11.0-36-中⽂翻译版 发布于 2021 年 9 ⽉ 21 ⽇ 由 Gerard Beekmans 原著 总编辑:Bruce Dubbs Linux From Scratch: 版本 r11.0-36-中⽂翻译版 : 发布于 2021 年 9 ⽉ 21 ⽇ 由 由 Gerard Beekmans 原著和总编辑:Bruce Dubbs 版权所有 © 1999-2021 Gerard Beekmans 版权所有 © 1999-2021, Gerard Beekmans 保留所有权利。 本书依照 Creative Commons License 许可证发布。 从本书中提取的计算机命令依照 MIT License 许可证发布。 Linux® 是Linus Torvalds 的注册商标。 Linux From Scratch - 版本 r11.0-36-中⽂翻译版 ⽬录 序⾔ .................................................................................................................................... viii i. 前⾔ ............................................................................................................................ viii ii. 本书⾯向的读者 ............................................................................................................ viii iii. LFS 的⽬标架构 ............................................................................................................ ix iv. 阅读本书需要的背景知识 ................................................................................................. ix v. LFS 和标准 ..................................................................................................................... x vi. 本书选择软件包的逻辑 .................................................................................................... xi vii. 排版约定 .................................................................................................................... xvi viii. 本书结构 ................................................................................................................. -

COMPLAINT for PATENT INFRINGEMENT Against Asustek Computer Inc., Asus Computer International, Inc., Atheros Communications, Inc
MOSAID Technologies Incorporated v. Dell, Inc. et al Doc. 1 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF TEXAS MARSHALL DIVISION MOSAID Technologies Incorporated, § § Plaintiff, § Case No. 2:11-cv-179 § v. § § Dell, Inc., § Jury Trial Demanded Research in Motion Corporation, § Research in Motion, Ltd., § Datalogic S.p.A., § Informatics Holdings, Inc., § Wasp Barcode Technologies, Ltd., § Venture Research, Inc., § Huawei Technologies Co., Ltd., § Huawei Technologies USA Inc., § Huawei Device USA Inc., § Futurewei Technologies, Inc., § Murata Electronics North America, Inc., § Murata Manufacturing Co., Ltd., § Murata Wireless Solutions, § Sychip, Inc., § Wistron Corporation, § Wistron LLC, § SMS Infocomm Corporation, § Wistron Infocomm (Texas) Corporation, § Wistron Infocomm Technology (America) § Corporation, § Wistron NeWeb Corporation, § ASUSTeK Computer Inc., § Asus Computer International, Inc., § Lexmark International, Inc., § Canon Inc., § Canon U.S.A., Inc., § Digi International Inc., § Intel Corporation, § Atheros Communications, Inc., § Marvell Semiconductor, Inc., § Realtek Semiconductor, § Ralink Technology Corporation, § CSR plc, § § Defendants. § Dallas 320181v1 Dockets.Justia.com ORIGINAL COMPLAINT FOR PATENT INFRINGEMENT Plaintiff MOSAID Technologies Incorporated (“MOSAID”) files this Original Complaint for patent infringement against Defendants Dell, Inc. (“Dell”); Research in Motion Corporation and Research in Motion, Ltd. (collectively, “RIM”); Datalogic S.p.A., Informatics Holdings, Inc., and Wasp Barcode