Human Resources Directorate Service Management (HRD
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tinkertool System 7 Reference Manual Ii
Documentation 0642-1075/2 TinkerTool System 7 Reference Manual ii Version 7.5, August 24, 2021. US-English edition. MBS Documentation 0642-1075/2 © Copyright 2003 – 2021 by Marcel Bresink Software-Systeme Marcel Bresink Software-Systeme Ringstr. 21 56630 Kretz Germany All rights reserved. No part of this publication may be redistributed, translated in other languages, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of the publisher. This publication may contain examples of data used in daily business operations. To illustrate them as completely as possible, the examples include the names of individuals, companies, brands, and products. All of these names are fictitious and any similarity to the names and addresses used by an actual business enterprise is entirely coincidental. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. The publisher may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time without notice. Make sure that you are using the correct edition of the publication for the level of the product. The version number can be found at the top of this page. Apple, macOS, iCloud, and FireWire are registered trademarks of Apple Inc. Intel is a registered trademark of Intel Corporation. UNIX is a registered trademark of The Open Group. Broadcom is a registered trademark of Broadcom, Inc. Amazon Web Services is a registered trademark of Amazon.com, Inc. -

® Apple® A/UXTM Release Notes Version 1.0 Ii APPLE COMPUTER, INC
.® Apple® A/UXTM Release Notes Version 1.0 Ii APPLE COMPUTER, INC. UNIBUS, VAX, VMS, and VT100 are trademarks of Digital © Apple Computer, Inc., 1986 Equipment Corporation. 20525 Mariani Ave. Cupertino, California 95014 Simultaneously published in the (408) 996-1010 United States and Canada. Apple, the Apple logo, APPLE'S SYSTEM V AppleTalk, ImageWriter, IMPLEMENTATION A/UX LaserWriter, Macintosh, RELEASE 1.0 RUNNING ON A MacTerminal, and ProDOS are MACINTOSH II COMPUTER registered trademarks of Apple HAS BEEN TESTED BY THE Computer, Inc. AT&T-IS' SYSTEM V VERIFICATION SUITE AND Apple Desktop Bus, A!UX, CONFORMS TO ISSUE 2 OF EtherTalk, and Finder are AT&T-IS' SYSTEM V trademarks of Apple Computer, INTERFACE DEFINITION Inc. BASE PLUS KERNEL Ethernet is a registered EXTENSIONS. trademark of Xerox Corporation. IBM is a registered trademark, and PC-DOS is a trademark, of International Business Machines, Inc. - ITC Avant Garde Gothic, ITC Garamond, and ITC Zapf Dingbats are registered trademarks of International Typeface Corporation. Microsoft and MS-DOS are registered trademarks of Microsoft Corporation. NFS is a registered trademark, and Sun Microsystems is a trademark, of Sun Microsystems, Inc. NuBus is a trademark of Texas Instruments. POSTSCRIPT is a registered trademark, and TRANSCRIPT is a trademark, of Adobe Systems Incorporated. UNIX is a registered trademark of AT&T Information Systems. Introduction to A/UX Release Notes, Version 1.0 These release notes contain late-breaking information about release 1.0 of the A!UXI'M software for the Apple® Macintosh® II computer. This package contains two kinds of materials: o Specific information that was not available in time to be incorporated into the printed manuals. -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

Media Composer V8.5 Readme
Avid® Editing Application ReadMe for Media Composer® v8.5 Revision History Date Description 3/14/2016 Added note concerning Windows 10 and QuickTime. See “Compatibility Chart” on page 25. 2/9/2016 Updated “Compatibility Chart” on page 25 to reflect that QuickTime v7.7.9 is supported for Windows. 2/2/2016 Updated “Qualified Hardware and Operating Systems” on page 13 and “Shared Storage Support” on page 33 and “Compatibility Chart” on page 25. 1/29/2016 Updated “Qualified Workstations and Laptops” on page 14 to include support for Late 2015 iMac Retina 5K system. IMPORTANT: Avid periodically makes software updates available for download on Avid.com at the following location:www.avid.com/us/support/downloads. Please check the above site regularly for information on available downloads for your product. Important Information Avid® recommends that you read all the information in this ReadMe file thoroughly before installing or using any new software release. Important: Search the Avid Knowledge Base for the most up-to-date ReadMe file, which contains the latest information that might have become available after the documentation was published. This document describes compatibility issues with previous releases, software installation instructions, hardware and software requirements, and summary information on system and memory requirements. This document also lists hardware and software limitations. Symbols and Conventions Contents If You Need Help. 3 Notes on Windows. 9 Notes on Software Licensing. 12 Qualified Hardware and Operating Systems . .13 Compatibility Chart . 25 Setting up the NVIDIA Card . 31 Shared Storage Support . 33 Feature Performance . 23 Limitations. 33 Symbols and Conventions Avid documentation uses the following symbols and conventions: Symbol or Convention Meaning or Action n A note provides important related information, reminders, recommendations, and strong suggestions. -

Solaris Powerpc Edition: Installing Solaris Software—May 1996 What Is a Profile
SolarisPowerPC Edition: Installing Solaris Software 2550 Garcia Avenue Mountain View, CA 94043 U.S.A. A Sun Microsystems, Inc. Business Copyright 1996 Sun Microsystems, Inc., 2550 Garcia Avenue, Mountain View, California 94043-1100 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Portions of this product may be derived from the UNIX® system, licensed from Novell, Inc., and from the Berkeley 4.3 BSD system, licensed from the University of California. UNIX is a registered trademark in the United States and other countries and is exclusively licensed by X/Open Company Ltd. Third-party software, including font technology in this product, is protected by copyright and licensed from Sun’s suppliers. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 and FAR 52.227-19. Sun, Sun Microsystems, the Sun logo, Solaris, Solstice, SunOS, OpenWindows, ONC, NFS, DeskSet are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. -

Apple Remote Desktop Administrator's Guide
Apple Remote Desktop Administrator’s Guide Version 3 K Apple Computer, Inc. © 2006 Apple Computer, Inc. All rights reserved. The owner or authorized user of a valid copy of Apple Remote Desktop software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid for support services. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AirPort, AppleScript, AppleTalk, AppleWorks, FireWire, iBook, iMac, iSight, Keychain, Mac, Macintosh, Mac OS, PowerBook, QuickTime, and Xserve are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. Apple Remote Desktop, Bonjour, eMac, Finder, iCal, and Safari are trademarks of Apple Computer, Inc. Adobe and Acrobat are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 019-0629/02-28-06 3 Contents Preface 9 About This Book 10 Using This Guide 10 Remote Desktop Help 10 Notation -

Highpointrr Mac Installation Guide
HighPointRR Mac Installation Guide V1.00 – Nov, 2020 1 Contents 1. Overview ................................................................................................................................................. 3 2. Prerequisites ........................................................................................................................................... 3 3. Apple T2 security Chip-Disable Secure boot ...................................................................................... 4 Disabling Secure Boot ............................................................................................................................ 4 4. Installing the Device Driver .................................................................................................................. 6 macOS High Sierra 10.13 Driver Installation Procedure .................................................................. 6 macOS Mojave10.14 and macOS Catalina 10.15 and macOS Big Sur 11.0 Driver Installation Procedure ............................................................................................................................................... 9 5. Uninstalling the Device Driver ........................................................................................................... 13 Uninstalling the Device driver for macOS 10.13 and 10.14 ............................................................. 13 Uninstalling the Device driver for macOS 10.15 and macOS 11.0 ................................................ -

Download Itunes Latest Version Update to the Latest Version of Itunes
download itunes latest version Update to the latest version of iTunes. Learn how to get the latest version of iTunes on your Mac or PC. On your Mac. If you update your Mac to macOS Catalina or later, you can access your iTunes media library in the Apple Music app, Apple TV app, Apple Books app, and Apple Podcasts app. To manually back up, restore, or sync your iPhone, iPad, or iPod touch, use Finder. If you can’t update to the latest version of macOS. You can update to the latest version of iTunes (up to iTunes 12.8). Open the App Store on your Mac. Click Updates at the top of the App Store window. If any iTunes updates are available, click Install. On your PC. Depending on the version of iTunes that you have, here are a few ways to update. If you downloaded iTunes from the Microsoft Store. Versions of iTunes from the Microsoft Store update automatically when new versions are released. If you downloaded iTunes from Apple's website. Open iTunes. From the menu bar at the top of the iTunes window, choose Help > Check for Updates. Follow the prompts to install the latest version. If Check for Updates isn't an option in the Help menu, then you downloaded iTunes from the Microsoft Store. Learn more. Learn how to update your iPhone or iPod touch to the latest version of iOS, and iPad to the latest version of iPadOS. Learn how to update your Mac. iTunes features might vary by country or region. Information about products not manufactured by Apple, or independent websites not controlled or tested by Apple, is provided without recommendation or endorsement. -

Tinkertool System 6 Reference Manual Ii
Documentation 0632-1969/2 TinkerTool System 6 Reference Manual ii Version 6.99, July 21, 2021. US-English edition. MBS Documentation 0632-1969/2 © Copyright 2003 – 2021 by Marcel Bresink Software-Systeme Marcel Bresink Software-Systeme Ringstr. 21 56630 Kretz Germany All rights reserved. No part of this publication may be redistributed, translated in other languages, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of the publisher. This publication may contain examples of data used in daily business operations. To illustrate them as completely as possible, the examples include the names of individuals, companies, brands, and products. All of these names are fictitious and any similarity to the names and addresses used by an actual business enterprise is entirely coincidental. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. The publisher may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time without notice. Make sure that you are using the correct edition of the publication for the level of the product. The version number can be found at the top of this page. Apple, macOS, iCloud, and FireWire are registered trademarks of Apple Inc. Intel is a registered trademark of Intel Corporation. UNIX is a registered trademark of The Open Group. Broadcom is a registered trademark of Broadcom, Inc. Trademarks or service marks are used for identification purposes only. -
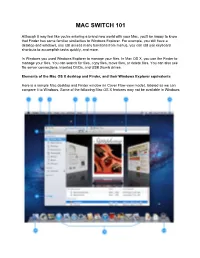
Mac Switch 101
MAC SWITCH 101 Although it may feel like you're entering a brand new world with your Mac, you'll be happy to know that Finder has some familiar similarities to Windows Explorer. For example, you still have a desktop and windows, you still access many functions from menus, you can still use keyboard shortcuts to accomplish tasks quickly, and more. In Windows you used Windows Explorer to manage your files. In Mac OS X, you use the Finder to manage your files. You can search for files, copy files, move files, or delete files. You can also see file server connections, inserted DVDs, and USB thumb drives. Elements of the Mac OS X desktop and Finder, and their Windows Explorer equivalents Here is a sample Mac desktop and Finder window (in Cover Flow view mode), labeled so we can compare it to Windows. Some of the following Mac OS X features may not be available in Windows. 1. Apple () menu - Similar to the Start menu in Windows; used to access functions such as Software Update (equivalent to Windows Update), System Preferences (equivalent to Control Panel), Sleep, Log Out, and Shut Down. 2. Menu bar - This is always at the top of your screen. It contains the Apple menu, active application menu, menu bar extras and the Spotlight icon. The Finder menu has items such as Finder Preferences, Services, and Secure Empty Trash. 3. Finder window close, minimize and zoom buttons–just like in Windows but on the left. Note: Closing all application windows in Mac OS X does not always quit the application as it does in Windows. -

Zoom Requirements
Before reading this document on various requirements for various online teaching tools such as Zoom, BB Collaborate Ultra and Microsoft Teams, please check your system specs and your bandwidth/internet connectivity using the quick guide here: Finding your System Specs: Windows PC: Right Click “Start Button” , select “System” option. It will show Device Specifications (CPU/Processor and Installed RAM) screen such as this: You can find out your CPU generation from using the intel’s website. https://www.intel.com/content/www/us/en/processors/processor-numbers.html Mac OS: Source: https://support.apple.com/en-ca/HT203001 Choose Apple menu > About This Mac. This opens an overview of your Mac, including your Mac model, processor, memory, serial number, and version of macOS. To see the greater detail provided by the System Information app, click the System Report button. Bandwidth Test: You can test your bandwidth/speed/connection @ https://speedtest.utoronto.ca/ Zoom Requirements Source : https://support.zoom.us/hc/en-us/articles/201362023-System-requirements-for-Windows-macOS- and-Linux Processor(CPU) and RAM requirements Minimum Recommended Processor Single Core 1Ghz or Higher Dual Core 2Ghz or Higher (i3/i5/i7 or AMD equivalent) RAM N/A 4Gb Notes: Dual and single core laptops have a reduced frame rate when screen sharing (around 5 frames per second). For optimum screen sharing performance on laptops we recommend a quad core processor or higher. Linux requires a processor or graphics card that can support OpenGL 2.0 or higher. Bandwidth requirements The bandwidth used by Zoom will be optimized for the best experience based on the participants’ network. -

Restart the Computer
Gloucester County Library System COMPUTER BASICS WINDOWS XP VISTA, WINDOW 7 Computer Classes Check the GCLS online calendar for the schedule of Computer Classes www.gcls.org Basic Computer Skills: Required for all other computer classes. Learn how to use the mouse, open and close programs, select items and text. Internet Basics: Learn how to use the Internet, click links, navigate sites and print useful information. Email Basics: Learn about email, create your own email address and get some valuable practice. Software Basics: Overview of common office software such as Microsoft Word, Excel and PowerPoint. When Caring for a PC Good Practices Plug your PC, monitor, printer, scanner, etc. into a surge protector Keep your PC in a well-ventilated area Keep your PC away from moisture, and moisture away from your PC Properly turn off your PC and monitor when not in use • Safety Tips Sit in a comfortable chair when using a PC Make sure your PC is on a stable surface NEVER open the case on your PC while it is plugged in Take breaks often to rest your eyes and increase circulation • Anti-Virus Software Purchase anti-virus software and keep it up-to-date Scan your PC each time you turn on your PC Anti-virus software will protect your computer from dangerous viruses • Basic Cleaning Clean your monitor with a clean soft cloth using water or isopropyl alcohol if needed Clean your keyboard with a clean soft cloth – if needed, use isopropyl alcohol to remove grime – only use a small amount on a clean soft cloth.