Video Conference Tools
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Download Windows Live Messenger for Linux Ubuntu
Download windows live messenger for linux ubuntu But installing applications in Ubuntu that were originally made for I found emescene to be the best Msn Messenger for Ubuntu Linux so far. It really gives you the feel as if you are using Windows Live Messenger. Its builds are available for Archlinux, Debian, Ubuntu, Fedora, Mandriva and Windows. At first I found it quite difficult to use Pidgin Internet Messenger on Ubuntu Linux. Even though it allows signing into MSN, Yahoo! Messenger and Google Talk. While finding MSN Messenger for Linux / Ubuntu, I found different emesene is also available and could be downloaded and installed for. At first I found it quite difficult to use Pidgin Internet Messenger on Ubuntu Linux. Even though it allows signing into MSN, Yahoo! Messenger. A simple & beautiful app for Facebook Messenger. OS X, Windows & Linux By downloading Messenger for Desktop, you acknowledge that it is not an. An alternative MSN Messenger chat client for Linux. It allows Linux users to chat with friends who use MSN Messenger in Windows or Mac OS. The strength of. Windows Live Messenger is an instant messenger application that For more information on installing applications, see InstallingSoftware. sudo apt-get install chromium-browser. 2. After the installation is Windows Live Messenger running in LinuxMint / Ubuntu. You can close the. Linux / X LAN Messenger for Debian/Ubuntu LAN Messenger for Fedora/openSUSE Download LAN Messenger for Windows. Windows installer A MSN Messenger / Live Messenger client for Linux, aiming at integration with the KDE desktop Ubuntu: Ubuntu has KMess in its default repositories. -

Wiretapping End-To-End Encrypted Voip Calls Real-World Attacks on ZRTP
Institute of Operating Systems and Computer Networks Wiretapping End-to-End Encrypted VoIP Calls Real-World Attacks on ZRTP Dominik Schürmann, Fabian Kabus, Gregor Hildermeier, Lars Wolf, 2017-07-18 wiretapping difficulty End-to-End Encryption SIP + DTLS-SRTP (SIP + Datagram Transport Layer Security-SRTP) End-to-End Encryption & Authentication SIP + SRTP + ZRTP Introduction Man-in-the-Middle ZRTP Attacks Conclusion End-to-End Security for Voice Calls Institute of Operating Systems and Computer Networks No End-to-End Security PSTN (Public Switched Telephone Network) SIP + (S)RTP (Session Initiation Protocol + Secure Real-Time Transport Protocol) 2017-07-18 Dominik Schürmann Wiretapping End-to-End Encrypted VoIP Calls Page 2 of 13 wiretapping difficulty End-to-End Encryption & Authentication SIP + SRTP + ZRTP Introduction Man-in-the-Middle ZRTP Attacks Conclusion End-to-End Security for Voice Calls Institute of Operating Systems and Computer Networks No End-to-End Security PSTN (Public Switched Telephone Network) SIP + (S)RTP (Session Initiation Protocol + Secure Real-Time Transport Protocol) End-to-End Encryption SIP + DTLS-SRTP (SIP + Datagram Transport Layer Security-SRTP) 2017-07-18 Dominik Schürmann Wiretapping End-to-End Encrypted VoIP Calls Page 2 of 13 wiretapping difficulty Introduction Man-in-the-Middle ZRTP Attacks Conclusion End-to-End Security for Voice Calls Institute of Operating Systems and Computer Networks No End-to-End Security PSTN (Public Switched Telephone Network) SIP + (S)RTP (Session Initiation Protocol + Secure Real-Time -
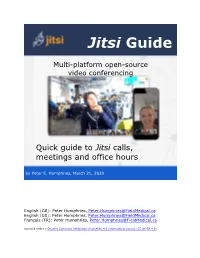
Jitsi User Guide
Jitsi Guide Multi-platform open-source video conferencing Quick guide to Jitsi calls, meetings and office hours by Peter E. Humphries, March 21, 2020 English (GB): Peter Humphries, [email protected] English (US): Peter Humphries, [email protected] Français (FR): Peter Humphries, [email protected] Licensed under a Creative Commons Attribution-ShareAlike 4.0 International Licence (CC BY-SA 4.0). Android Client: 1. Open the Jitsi application on your Android device. 2. Enter a new name for your meeting “room” to start a new meeting. You can enter the name of an existing meeting room to join a meeting already in progress. Figure 2 Jitsi Android client iOS Client: 1. Open the Jitsi application on your iOS device. 2. Enter a new name for your meeting “room” to start a new meeting. You can enter the name of an existing meeting room to join a meeting already in progress. Figure 3 Jitsi iOS client Getting Started You can host or attend Jitsi meetings from your browser or from the Jitsi client application on your mobile device. For more information about Jitsi meetings, go to the https://jitsi.org/ page. Click on START A CALL to open a Jitsi meeting room! Figure 4 Jitsi home page ( https://jitsi.org/ ) Jitsi can handle up to 75 participants in a “meeting room.” Practically, fewer should be active participants. For larger groups, Jitsi offers easy integration with YouTube’s live streaming service. Starting a Meeting Web Portal: 1. Go to https://meet.jit.si/ or click on START A CALL if you are on the Jitsi home page. -

National Security Agency | Cybersecurity Information Selecting
National Security Agency | Cybersecurity Information Selecting and Safely Using Collaboration Services for Telework - UPDATE Summary During a global pandemic or other crisis contingency scenarios, many United States Government (USG) personnel must operate from home while continuing to perform critical national functions and support continuity of government services. With limited access to government furnished equipment (GFE) such as laptops and secure smartphones, the use of (not typically approved) commercial collaboration services on personal devices for limited government official use becomes necessary and unavoidable. We define collaboration services as those capabilities that allow the workforce to communicate via internet-enabled text, voice, and video, and can include the sharing of files and other mission content. Collaboration can occur between two people or widened to include a large group to support mission needs. This document provides a snapshot of best practices and criteria based on capabilities available at the time of publication and was coordinated with the Department of Homeland Security (DHS), which has released similar guidance: “Cybersecurity Recommendations for Federal Agencies Using Video Conferencing” [1] and “Guidance for Securing Video Conferencing” [2]. This NSA publication is designed to provide simple and actionable considerations for individual government users. The intent of this document is not meant to be exhaustive or based on formal testing, but rather be responsive to a growing demand amongst the federal government to allow its workforce to operate remotely using personal devices when deemed to be in the best interests of the health and welfare of its workforce and the nation. Recommendations in this document are likely to change as collaboration services evolve and also address known vulnerabilities and threats. -
Linphone a Good Working Skype Voice Over IP Alternative
Walking in Light with Christ - Faith, Computing, Diary Articles & tips and tricks on GNU/Linux, FreeBSD, Windows, mobile phone articles, religious related texts http://www.pc-freak.net/blog Linphone a good working Skype voice over IP alternative Author : admin If you never tried linphone I warmly recommend it. 2 days ago, with a friend of mine we tested a bunch of Linux softwares to find out what is the situation with possible alternatives to Skype to transmit Voice and Video. I've been interested into Skype Alternative programs since about 2 years, but so far I never found good and easy to set up working Linux alternative. We first tried Ekiga. Though it is said to be a good Linux SKype alternative, my ekiga client running on Debian Linux stable Squeeze ver. 3.2.7.2 failed to connect to SIP account I've created on ekiga.net. I've tried hard to make ekiga connect to account SIP created from ekiga.net but all time I was getting an error on connect: Ekiga did not manage to configure your network settings automatically. You can still use it, but you need to configure your network settings manually. Please see http://wiki.ekiga.org/index.php/Enable_port_forwarding_manually for instructions After continously trying to follow instructions from above pointed URL and making proper settings on my DL-524 Wireless Router and all time ending up with the annoying error, we decided to finally completely abondoned it and try some other voice over IP clients. We tried Jitsi and few others which prooved to be unworking. -

Virtual Excursions – Web Conferencing
Virtual excursions Create amazing STEM engagement programs online Technical set up | Best practice Partnering for impact | Engaging community Evaluate & Iterate ABOUT THE MANUAL About Inspiring Australia Inspiring Australia is the national strategy for public engagement with STEM and contributes to the Government’s vision to engage all Australians with science. Since 2009, the initiative supported by Commonwealth, State and Territory Governments facilitates science engagement programs and supports communities in diverse ways including through fostering influential networks to connect science to big audiences and delivering grant programs to organisations, groups and individuals. Inspiring Australia science engagement activities connect with people nationwide to: • build an awareness and appreciation of science • celebrate the excitement of science and scientific discovery • enhance capability and skills • improve science communication. In 2020, global events forced many organisations to adapt their large scale events and STEM engagement for online delivery modes. Inspiring Australia state programs have developed this online training opportunity to assist community partners to transition their programs to online delivery. This manual draws on the expertise of specialists in online education and STEM communication backed by research to deliver the tools, techniques and tips to help practitioners develop rich, deep and meaningful online STEM engagement. The Virtual Excursions training package has been coordinated for national delivery by Inspiring Australia NSW. It is produced and delivered by Fizzics Education, Sydney Science Education and Refraction Media with support from the Office of the NSW Chief Scientist & Engineer and state Inspiring Australia programs in NSW, ACT, QLD, WA and SA. © Inspiring Australia. Published by Refraction Media on 11 May 2020. -

Considerations for Deploying a Geographically Distributed Video Conferencing System
Considerations for deploying a geographically distributed video conferencing system Boris Grozev George Politis Emil Ivov Thomas Noel Atlassian and Atlassian and Atlassian University of Strasbourg University of Strasbourg University of Strasbourg [email protected] [email protected] [email protected] [email protected] Abstract—In this paper we report on our ongoing work to the user experience in video conferencing applications, and in improve the user experience of video conferencing by using geo- particular those based on WebRTC. location. We discuss the problem of selecting a media server for In this paper we describe a state-of-the-art multi-party video a video conference, introduce one state-of-the-art system which uses a simple method, and discuss a model for distributing conferencing system, which uses centralized media servers a conference among a set of media servers. We perform a with a basic form of geo-location. We analyze its performance measurement study of a production service, and find that in many and propose the first steps towards improving it. More specif- cases, contrary to common wisdom, connecting each participant ically, we explore the extent to which we can improve the to their closest server is not only costly, but counter-productive system if we introduce a distributed mode, in which a single in terms of decreasing the round-trip time. While, the approach may still seem viable in some use cases, more research is needed conference can be split to multiple servers. in order to understand when that may be, and define specific We structure the remainder of this paper as follows: section algorithms for server selection in the case of a distributed media II discusses other work related to our problem; section III conference. -

Automatically Generated PDF from Existing Images
STANDARD OPERATING PROCEDURES FOR HOLDING COURT PROCEEDINGS THROUGH VIDEO CONFERENCING 1. METHODS OF VIDEO CONFERENCING a) Offsite/Remote Location Video Conferencing - In this type of Video Conferencing the host Court is connected to the Advocates/Litigants present at a remote location i.e. their respective home or office. Such Video Conferencing is done through internet/cloud. ILLUSTRATION In GR Case Number 1/2020 pending before the Court of S.D.J.M. the Prosecution Counsel and the Defence counsel express desire to appear from remote location i.e. say from the office of the Public Prosecutor and private chamber respectively. A web link shall be created for VC with the Court of S.D.J.M. and shall be provided to the said Advocates. When the relevant proceeding commences, the Court and the Advocates mentioned above can remain connected to the Virtual Court Room through internet (by remaining at their respective remote locations) and participate therein by using the aforementioned link. b.) Onsite Video Conferencing - In this type of Video Conferencing all the participants are in the same premises (Court building) but in different rooms. We essentially have to provide this type of VC facility to those Advocates and litigants who cannot on their own arrange resources for Video Conferencing. Particular location/locations is/are to be earmarked for this purpose in the concerned Court building. We may call them Advocates Points for the sake of reference. There may be as many Advocate Points for the number of Court which shall function through Video Conferencing or there may be lesser number of such points with scheduling done to let more than one Court use the same Advocate Point by scheduling the proceeding time of their respective cases by way of mutual arrangement. -

Open Online Meeting
Open online meeting Project report 2021 1 Content Page ➢ Objectives and background ○ Background, current situation and future needs 3 ○ Purpose and aim of the project 4 ○ Implementation: Preliminary study 5 ○ Functionalities 6 ➢ Results of the study ○ Group 1: Web-conferencing and messaging solutions 7 ○ Group 2: Online file storage, management and collaboration platforms 21 ○ Group 3: Visual online collaboration and project management solutions 30 ○ Group 4: Online voting solutions 37 ➢ Solution example based on the study results ○ Selection criteria 42 ○ Description of the example solution 43 ➢ Next steps 44 2021 2 Background, current situation and future needs Municipalities in Finland have voiced a need to map out open source based alternatives for well-known proprietary online conferencing systems provided by e.g. Google and Microsoft for the following purposes: ➢ Online meeting (preferably web-based, no installation), ➢ Secure file-sharing and collaborative use of documents, ➢ Chat and messaging, ➢ Solution that enables online collaboration (easy to facilitate), ➢ Cloud services, ➢ Online voting (preferably integrated to the online meeting tool with strong identification method that would enable secret ballot voting). There are several open source based solutions and tools available for each category but a coherent whole is still missing. 2021 3 Purpose and aim of the project The purpose in the first phase of the project was to conduct a preliminary study on how single open source based solutions and tools could be combined to a comprehensive joint solution and research the technical compatibility between the different OS solutions. The project aims to create a comprehensive example solution that is based on open source components. -

Debian's Role in Establishing an Alternative to Skype
Debian’s role in establishing an alternative to Skype Motivation, Challenges and Tactics Daniel Pocock [email protected] http://www.OpenTelecoms.org mini-DebConf, Paris, November 2012 Daniel Pocock [email protected] Debian’s role in establishing an alternative to Skype Introduction Motivation – why do we need to do something? What happens if we do nothing? Challenges – why hasn’t it been done already? Tactics – what can we do over the next 12 months? Daniel Pocock [email protected] Debian’s role in establishing an alternative to Skype Motivation Some background Yes, you’ve seen me before – in Managua. Slides and video are available and highly recommended. Is there something new? – yes. Daniel Pocock [email protected] Debian’s role in establishing an alternative to Skype Motivation Why mention Skype? Widely deployed – hundreds of millions of users Interdependency – unlike other types of software, interoperability is a critical factor in the success of real-time communications software Viber – another proprietary solution that has quickly gained traction thanks to ease of use. The free software community missed the boat in the desktop VoIP arena, now the same may be happening for mobile. Daniel Pocock [email protected] Debian’s role in establishing an alternative to Skype Motivation How bad is it? Marketing – Skype allows Microsoft to study your thoughts and emotions in real time. Feedback to advertisers. Privacy – Microsoft has patented a technique for monitoring Skype. Call records, friend lists, etc. Statistical techniques for identifying who is pregnant, who is a homosexual, have all been exposed recently. -

Guidelines for Appearing Through Video Conferencing from Remote Locations)
(Guidelines for appearing through Video Conferencing from Remote Locations) If the learned Counsel intend to appear through Video Conferencing from their respective Homes/Offices/Any other Remote Location, they may please follow the procedure laid down below :- 1. “Jitsi Meet” Application shall be used for Video Conferencing. It works both on Mobile (Android/iPhone) and Laptops/Desktops. 2. Learned Advocates / Parties-in-person are requested to install “Jitsi Meet” Application in their Mobile Phones from Android Play Store or Apple Store. If someone wants to use the application from Laptop/Desktop, URL – https://meet.jit.si/ may be opened in the web browser. The users are not required to open any account in this application. 3. Advocates who intend to appear through Video Conferencing from their homes/offices are requested to submit intimation in this regard through email ID [email protected] or [email protected] not later than 8.30 AM on the date of hearing. The e-mail may be sent to both the above IDs. 4. In such e-mail, the concerned Advocates/Parties shall intimate their preference to appear through Video Conferencing and also state the following :- a. Case Number and Item Number in Cause List b. Name of Advocate / Party c. Party for whom appearance is sought d. E-mail ID where VC related intimation shall be sent e. Mobile Phone Number (preferably where whatsapp is installed) 5. The Advocates or Parties-in-person shall be ready with their Mobile Phones or Laptop/Desktop during the Hon’ble Court’s sitting timings. -

How to Encrypt Chat and Voip with Jitsi and XMPP
How To Encrypt Chat And VoIP With Jitsi and XMPP pillowfortress.wordpress.com /2013/08/01/how-to-encrypt-chat-and-voip-with-jitsi-and-xmpp/ Posted: 1 August 2013 | Author: Building20 | Filed under: | Tags: , , , , , , , , ,| Secure alternative to: Skype, Google Talk/Chat This guide will show how to set up encrypted off-the-record (OTR) chat and VoIP using ZRTP encryption in the following three sections: Section 1 will show how to register with an XMPP service, here dukgo.com. Section 2 will show how to set up XMPP with Jitsi. Section 3 will show how to find friends and initiate chat using end-to-end OTR encryption and secure VoIP calls using ZRTP, so no one but you and the receiver can read your messages or hear your conversations (and not a government or private company). Note that in my experience chat works great, whereas VoIP calls are inconsistent in terms of voice and video quality. Section 1: Register with dukgo.com Step 1: Register with an XMPP client (once called “Jabber”), in this example dukgo.com at https://dukgo.com/my/register. (There are many XMPP clients, not just dukgo.com; see the additional notes at the end for more information.) Step 2: Register an account (see Figure 1). Save your username and unique and long password somewhere safe (perhaps using KeePassX, for example). Figure 1: Registering at dukgo.com Section 2: Set up Jitsi Step 1: Download a stable release of Jitsi for your operating system: https://jitsi.org/Main/. (Gnu/Linux, Mac, and Windows are all supported, with Android coming soon.) Step 2: If opening Jitsi for the first time, skip the initial set up! Once the program is open, go to “File” and select “Add New Account.” Step 3: Under “select network,” scroll down to XMPP (see Figure 2).